Method, equipment and system for processing active detection response
A technology of active detection and processing methods, applied in the field of communication technology and security, it can solve problems such as security risks, insecurity, information leakage, etc., and achieve the effect of preventing attack behavior, curbing attack behavior, and avoiding security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
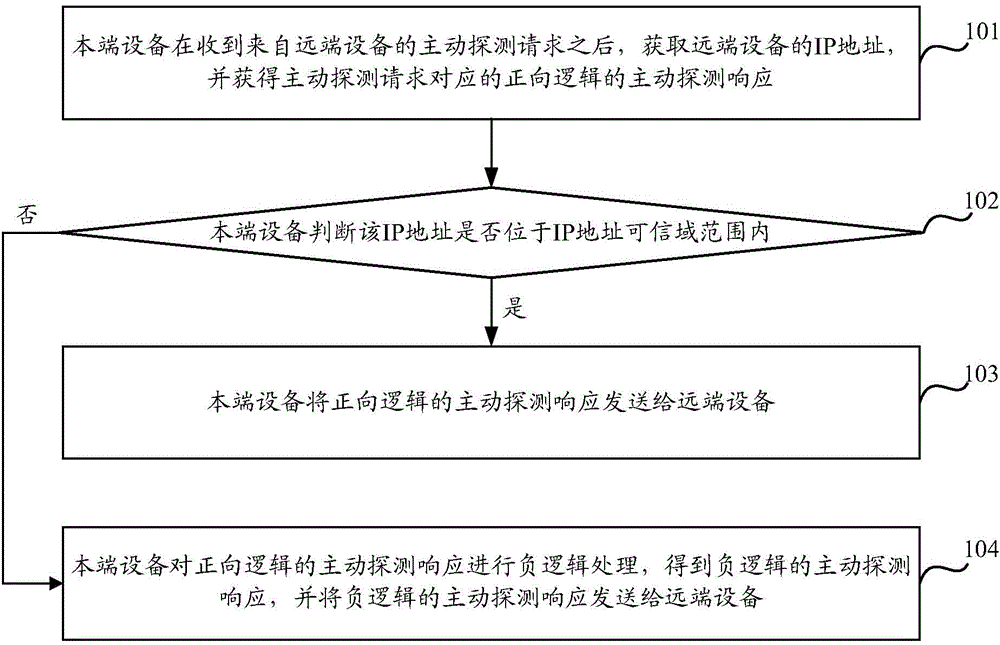
[0032] Embodiment 1 of the present invention provides a method for processing active detection responses. By expressing the status of active detection responses in negative logic based on NLS (Negative Logic System), attackers cannot obtain active detection responses. The effective attack exploit information is obtained in the response, such as figure 1 As shown, the processing method of the active probe response includes at least the following steps:
[0033] Step 101 , after receiving an active detection request from a remote device, the local device obtains the IP address of the remote device, and obtains a positive logic active detection response corresponding to the active detection request.
[0034] Wherein, the IP address of the remote device can be obtained from the active detection request, the active detection request is Msg_Request, the active detection response of the forward logic is Msg_Respond_PLS, and the active detection response of the forward logic is based ...
Embodiment 2
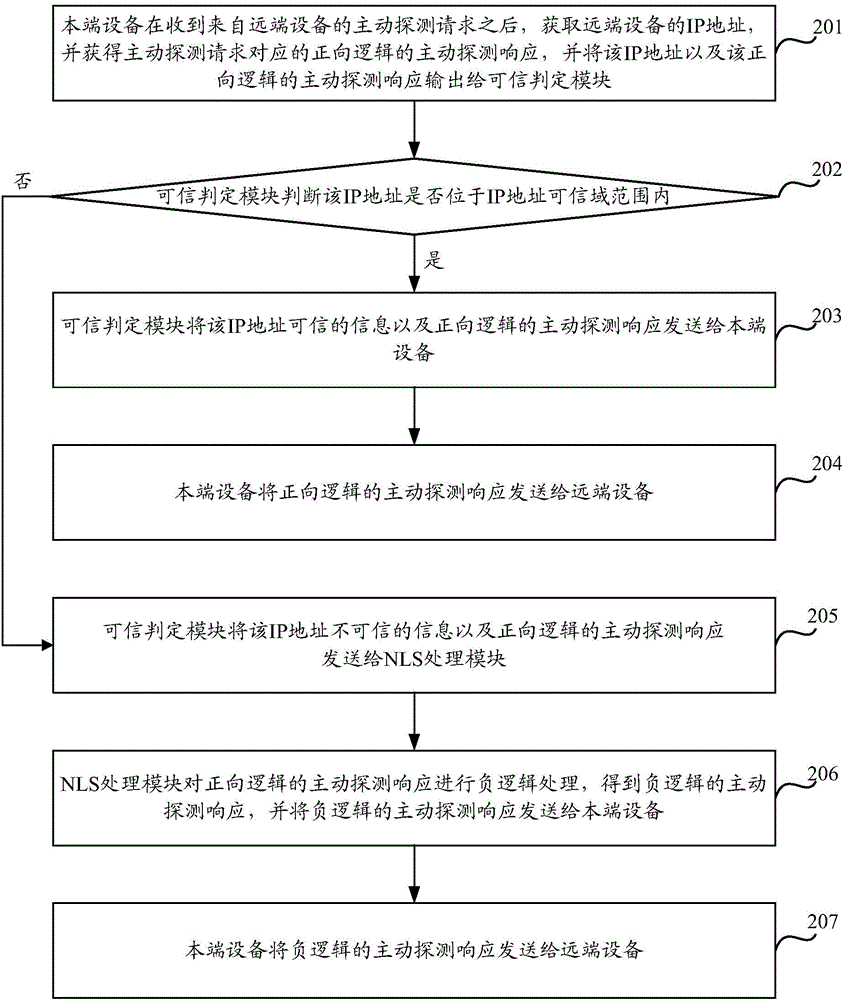
[0043] Embodiment 2 of the present invention provides a method for processing active detection responses. By negatively expressing the state of active detection responses based on negative logical thinking NLS (negative logic system), attackers cannot obtain active detection responses. The effective attack exploit information is obtained in the response, such as figure 2 As shown, the processing method of the active probe response includes at least the following steps:
[0044] Step 201, after receiving the active detection request from the remote device, the local device obtains the IP address of the remote device, and obtains a positive logic active detection response corresponding to the active detection request, and sends the IP address and the positive Active probe responses to the logic are output to the trusted decision module.
[0045] Wherein, the IP address of the remote device can be obtained from the active detection request, the active detection request is Msg_R...
Embodiment 3
[0064] Based on the same inventive concept as the above method, an embodiment of the present invention also provides a processing device for an active detection response, such as Figure 4 As shown, the equipment includes:
[0065] The obtaining module 11 is configured to obtain the IP address of the remote device after receiving the active detection request from the remote device, and obtain a positive logic active detection response corresponding to the active detection request;
[0066] A judging module 12, configured to judge whether the IP address is within the IP address trusted domain range;
[0067] The processing module 13 is configured to perform negative logic processing on the active detection response of the positive logic to obtain the active detection response of negative logic when the judgment result is negative;
[0068] The sending module 14 is configured to send the active detection response of the negative logic to the remote device when the judgment resu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com