Intelligent Anti-SQL Injection Method Based on Semantic Analysis
A semantic analysis and intelligent technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve hidden dangers and other problems, achieve high security, good implementation effect, and prevent attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
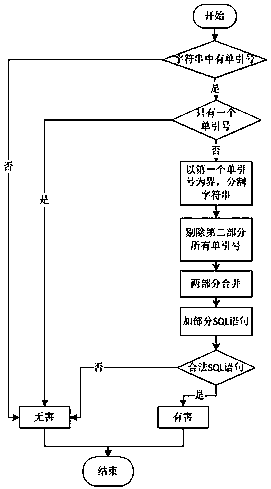
[0037] Such as figure 1The shown intelligent anti-SQL injection method based on semantic analysis is different in that the following steps are adopted: firstly, data interception or data extraction is performed on all requests from web pages, and the data appears as character strings. Afterwards, send the extracted data to the Security Center for processing and return the result. If the data is harmful, it will jump to the ShowErr page. If the data is harmless, it will continue to make normal requests.
[0038] Specifically, the data interception adopted is to intercept all requests through Global.asax. And the data extraction is to extract the data in querystring, form, and cookie. In other words, in .net, the querystring form is the object obtained by two kinds of requests. After that, replace the escape characters in it, and check one by one according to the preset judgment rules to determine whether the data is harmful. Moreover, there is no need to process the request ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com