Method, device and system for detecting distributed malicious codes on basis of textures
A malicious code, distributed technology, applied in the field of network security, can solve problems such as insufficient scalability, low detection performance, and inaccurate detection results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
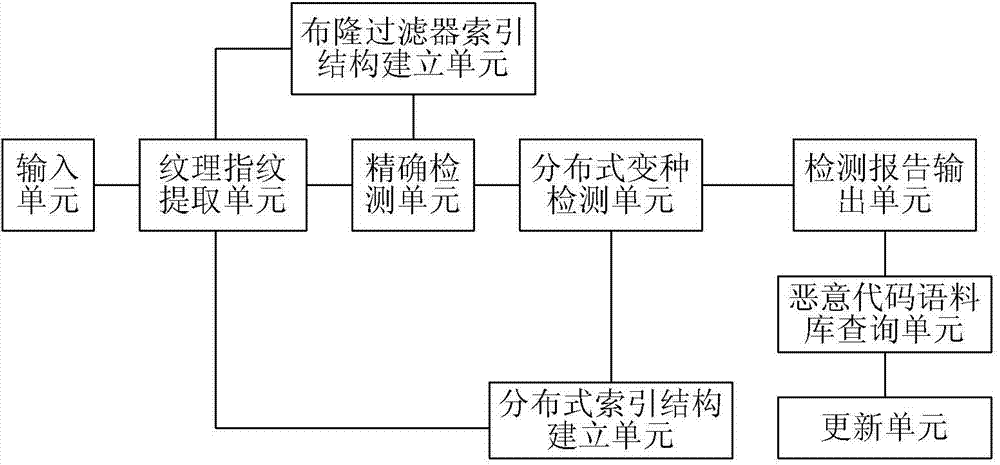
[0098] Embodiment 1. A texture-based distributed malicious code detection device, such as figure 1 As shown, including: distributed variant detection unit;
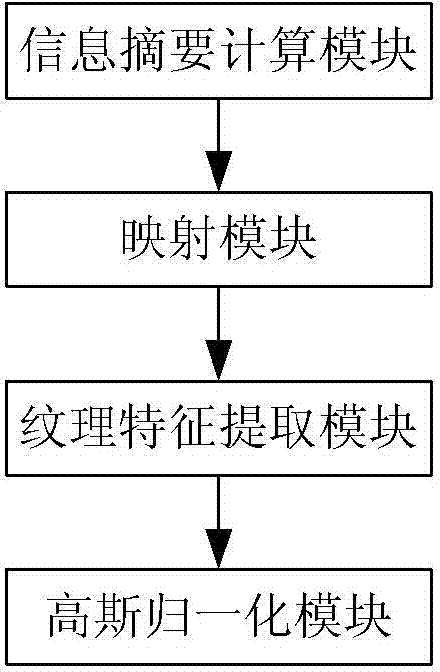
[0099] The texture fingerprint extraction unit is used to generate a malicious code texture fingerprint vector set according to the malicious code PE (portable executable) file in the malicious code corpus, and extract the texture fingerprint vector of the sample to be detected;
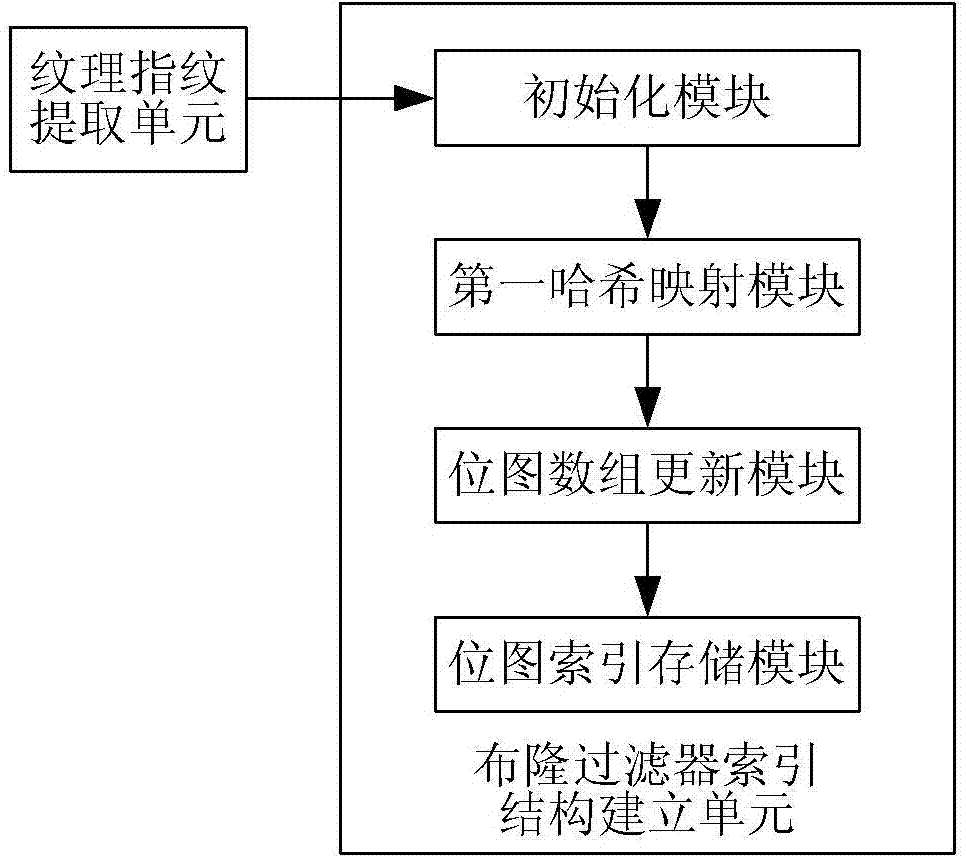
[0100] A Bloom-Filter (Bloom filter) index structure establishment unit, configured to map the malicious code texture fingerprint vector set into the Bloom-Filter index structure;
[0101] A distributed LSH (Location Sensitive Hash) index structure building unit, used to calculate the location-sensitive hash value of each malicious code texture fingerprint vector, calculate the machine ID and hash bucket ID of each location-sensitive hash value, and establish a distribution Formula LSH index structure;
[0102] The accurate detection unit is u...
Embodiment 2
[0190] Embodiment 2. A texture-based distributed malicious code detection method, such as Figure 7 shown, including:
[0191] S201. Generate a malicious code texture fingerprint vector set according to the malicious code PE file in the malicious code corpus;
[0192] S202. Map the malicious code texture fingerprint vector set into a Bloom-Filter index structure;
[0193] S203. Calculate the location-sensitive hash value of each malicious code texture fingerprint vector, calculate the machine ID and hash bucket ID of each location-sensitive hash value, and establish a distributed LSH index structure;
[0194] S204. Extract the texture fingerprint vector of the sample to be detected;
[0195] S205. Based on the Bloom-Filter index structure, detect the texture fingerprint vector of the sample to be detected; if hit, use the information of the hit malicious code PE file as the detection result;
[0196] S206. If there is no hit, perform distributed variant detection, including...
Embodiment 3
[0251] Embodiment three, as Figure 10 As shown, a texture-based distributed malicious code detection system includes: an upload server, a malicious code corpus, a malicious code detection front-end server, an accurate detection server, a variant detection cluster, and a third-party detection voting cluster (optional). Among the above functional devices, the malicious code corpus, the precise detection server and the variant detection cluster share the texture fingerprint extraction component.
[0252] For the upload server, the upload user uploads the confirmed malicious code to be stored to the upload server (the voting result of the third-party detection software), and the upload server uses a message digest algorithm (such as MD5 algorithm, SHA-1 algorithm, etc.) to calculate the malicious code The message summary accesses the malicious code corpus, and judges whether the malicious code of the message summary already exists, and if so, abandons the processing of the malici...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com