A SIM card and its anti-cloning method and device
A card locking and threshold technology, applied in the field of communication, can solve problems such as SIM card cloning, and achieve the effects of improving security, minimizing resources, and improving accurate judgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
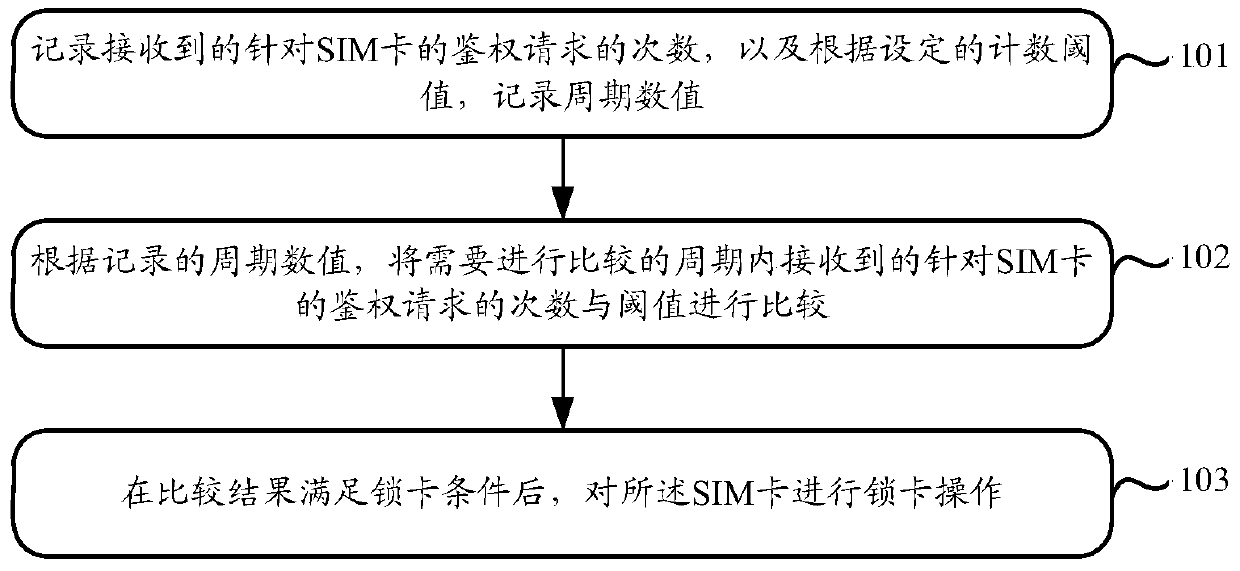
[0064] Such as figure 1 As shown, the flow chart of the steps of the SIM card anti-cloning method provided by Embodiment 1 of the present invention specifically includes the following steps:
[0065] Step 101: Record the number of received authentication requests for the SIM card, and record the period value according to the set counting threshold.
[0066] In this step 101, when it is monitored that there is an authentication request to access the SIM card, the authentication request needs to be recorded once; at the same time, the period value will also be recorded according to the set counting threshold.
[0067] Preferably, counting may be performed by using the frequency-divided clock signal, and when the counted value reaches a set counting threshold once, the recorded cycle value is increased. Wherein, frequency division processing can be performed on the input clock signal according to the frequency of the required clock signal and the set counting threshold.
[0068...
Embodiment 2
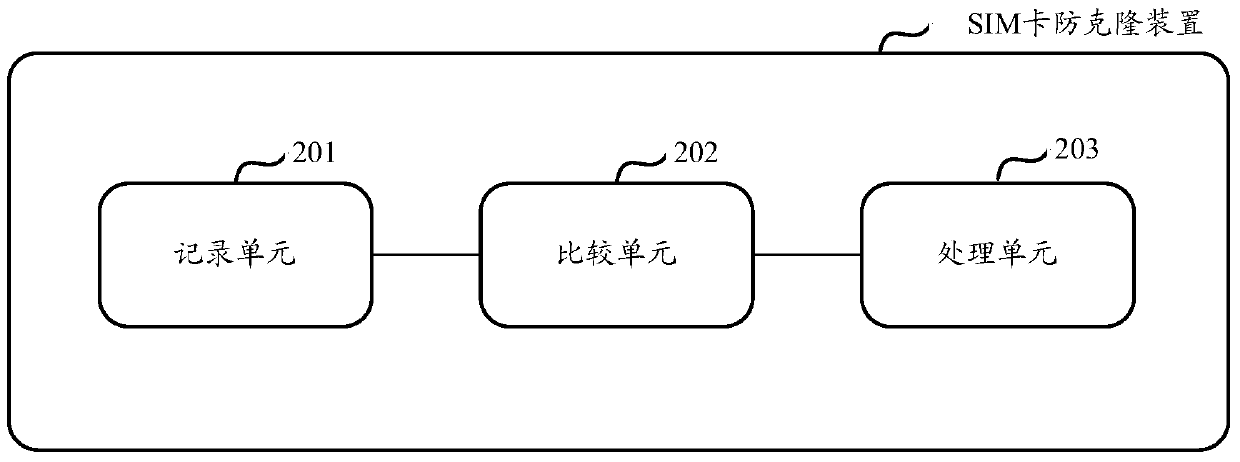
[0082] Such as figure 2 As shown, it is a schematic structural view of the SIM card anti-cloning device provided by Embodiment 2 of the present invention, which mainly includes the following structural units:
[0083] The recording unit 201 is configured to record the number of received authentication requests for the SIM card, and record the period value according to the set counting threshold.
[0084] Preferably, the recording unit is specifically configured to count by the frequency-divided clock signal, and increase the recorded period value every time the counted value reaches a set counting threshold.
[0085] In the embodiment of the present invention, the SIM card anti-cloning device further includes: a selection unit, configured to select a frequency divider for the clock signal to perform frequency division according to the frequency of the clock signal and a set counting threshold.
[0086] The comparison unit 202 is configured to compare the number of authentica...
Embodiment 3
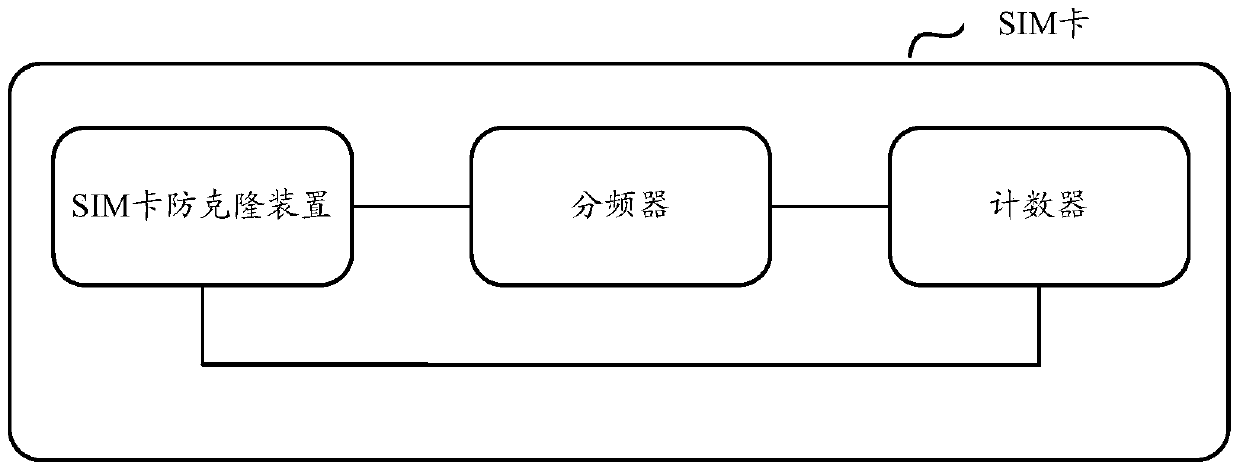
[0094] Such as image 3 As shown, it is a SIM card introduced in Embodiment 3 of the present invention, including the SIM card anti-cloning device, frequency divider, and counter in Embodiment 2.
[0095] The above-mentioned anti-cloning process of the SIM card will be described in detail below in conjunction with specific examples.
[0096] When the SIM card is powered on, the external clock will provide a clock signal. If the SIM card anti-cloning device will determine that the frequency of the clock signal received by the SIM card is 10MHz, select a 64 frequency divider according to the preset standard signal frequency of 0.15MHz, and trigger the frequency divider to divide the frequency of the clock signal 0.15MHz. The frequency divider outputs the standard clock signal after frequency division, and activates the counter for counting. The frequency division process described above is very short and can be ignored. When the count of the counter reaches FFFFFFFF, the SIM...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com