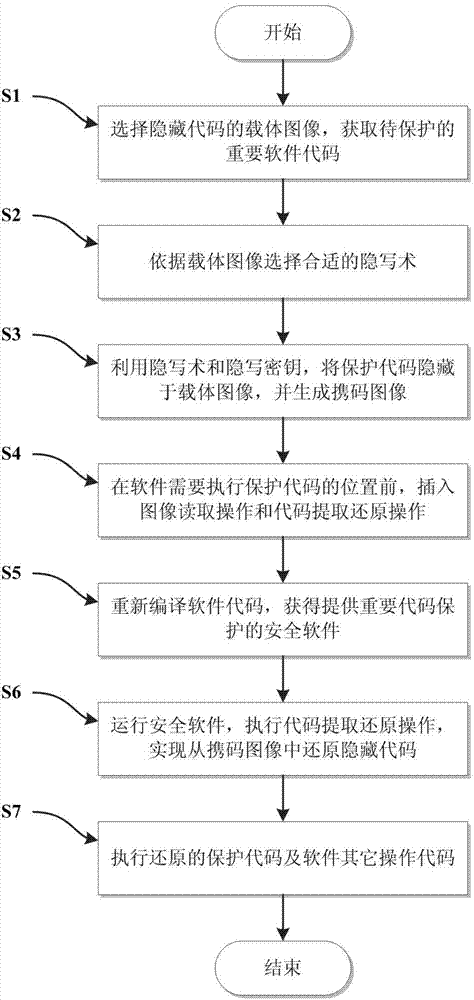
Steganography-based code protecting and restoring method
A steganography and code technology, applied in the field of information hiding, can solve the problem of low concealment of extraction operations, and achieve high security, good code concealment, and high concealment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be described in further detail below in conjunction with the accompanying drawings.
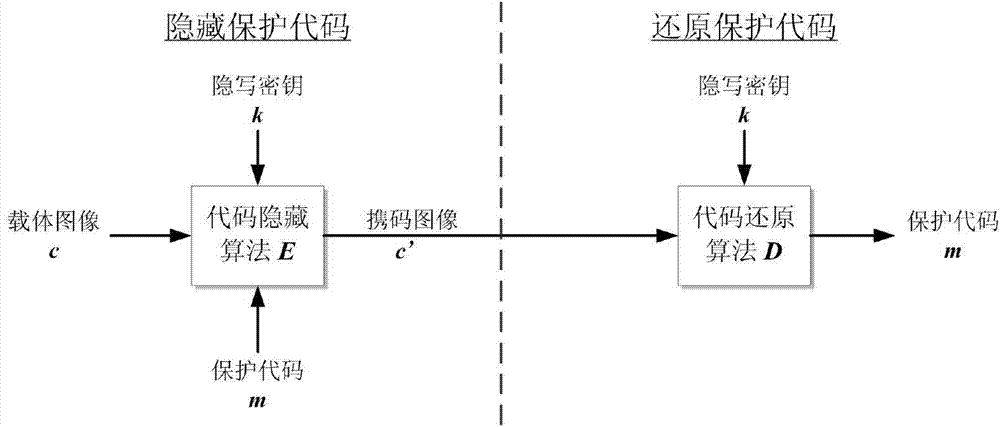
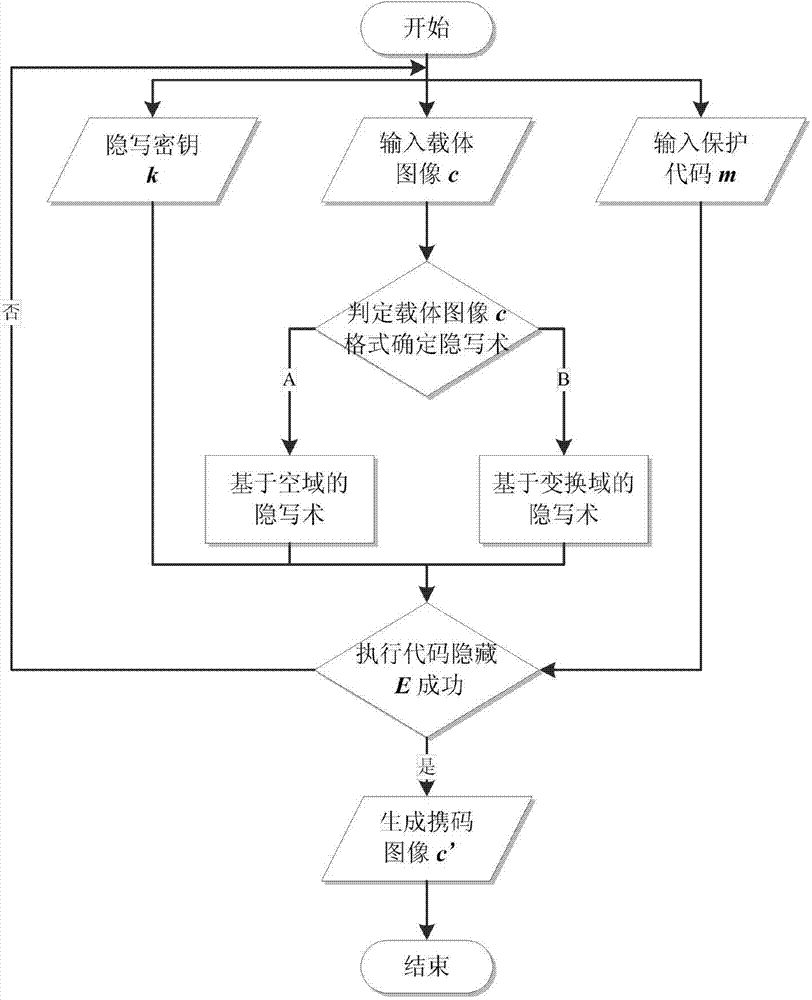
[0036] Such as figure 2 As shown, it is a schematic diagram of the realization function module of the method of the present invention, and the code protection method can be expressed as a five-tuple, that is, Σ=k ,D k 〉, where C is the carrier image set, M is the protection code set, C′ is the code-carrying image set obtained after the carrier image hides the protection code, E k is the code-behind algorithm, D k Restore the algorithm for the code. In the code protection method Σ, there are two main algorithm modules: a code hiding algorithm module and a code restoration algorithm module. The functional requirements of each module are as follows:
[0037] 1. Code-behind algorithm module
[0038] Under the control of the steganography key k, the module embeds the code M to be protected into the carrier image C, and outputs the code-carrying image C′. Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com