Webpage tamper-resistant method based on file-driven watermark comparison
A file-driven, anti-tampering technology, applied in the direction of digital data protection, etc., can solve the problems of inability to prevent database attacks, increase publishing servers, single inspection timing, etc., and achieve the goal of reducing external environment requirements, system resource requirements, and configuration volume Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
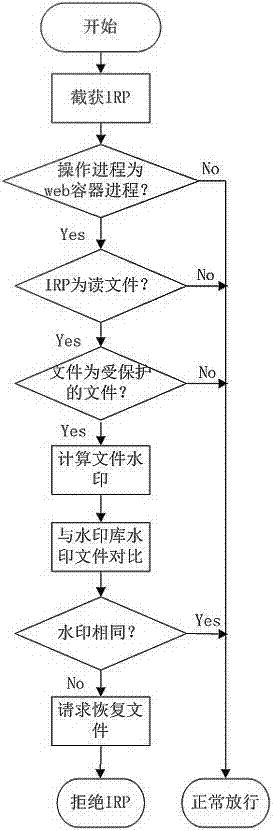
[0029] The present invention is based on the webpage anti-tampering method of file-driven watermark comparison, such as figure 1 shown, including the following steps:
[0030] (1) When the driver installed on the server monitors that the webpage file is accessed, the kernel layer intercepts the IRP request.
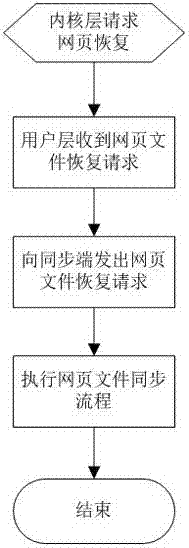
[0031] (2) Analyze the intercepted IRP request to determine whether it is satisfied at the same time: the process that initiates the IRP request is a specified Web container process, and the purpose of the IRP request is to read a file, and the file read by the IRP request is a user For files that need to be protected, if the above three conditions are met at the same time, the watermark comparison will be started, and the next step will be turned. As long as one of the conditions is not satisfied, the IRP request will be releas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com