Method and device for data packet feature extraction
A feature extraction and data packet technology, applied in the computer field, can solve the problems of cumbersome process and low efficiency, and achieve the effect of simple identification process, high identification efficiency, and low efficiency in solving cumbersome process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
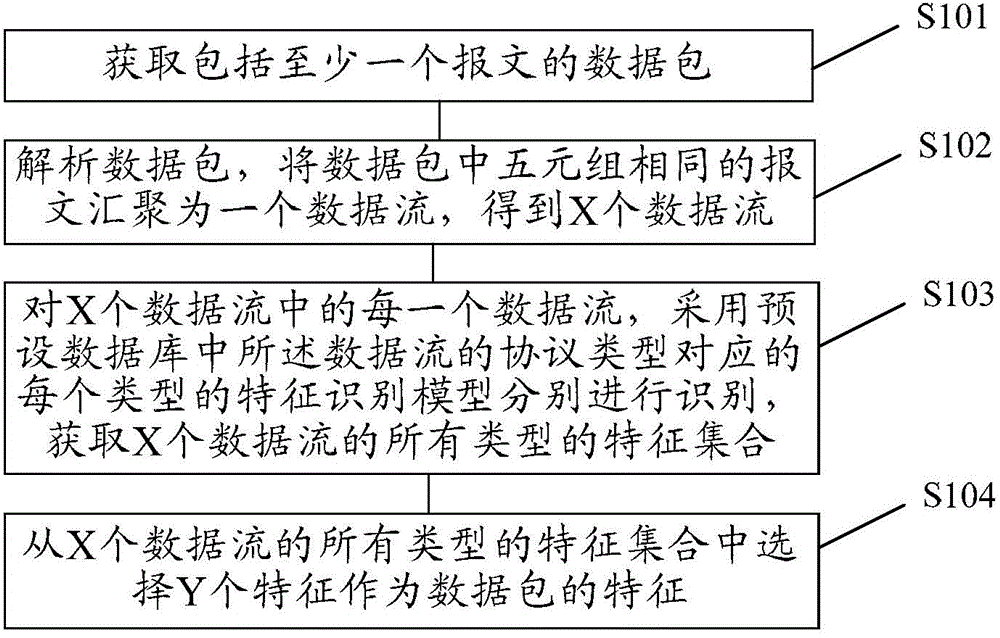
[0067] Embodiment 1 of the present invention provides a data packet feature extraction method, such as figure 1 As shown, the method may include:
[0068] S101. Obtain a data packet including at least one packet.
[0069] Wherein, the data packet is a data packet transmitted during network operation, and the data packet includes at least one message.
[0070] Specifically, the methods for obtaining data packets may include but not limited to the following two methods:
[0071] Method 1. Obtain the data packet by capturing the data packet through the real-time network card.
[0072] Exemplary, if the execution subject of this embodiment is to obtain data packets by means of real-time network card capture data packets, in the process of network operation, the data packets captured in real time can be saved as packet capture (packet capture) under the INPUT directory. , referred to as pcap) file, when executing S101, the data packet is obtained by sequentially reading all the ...
example 1
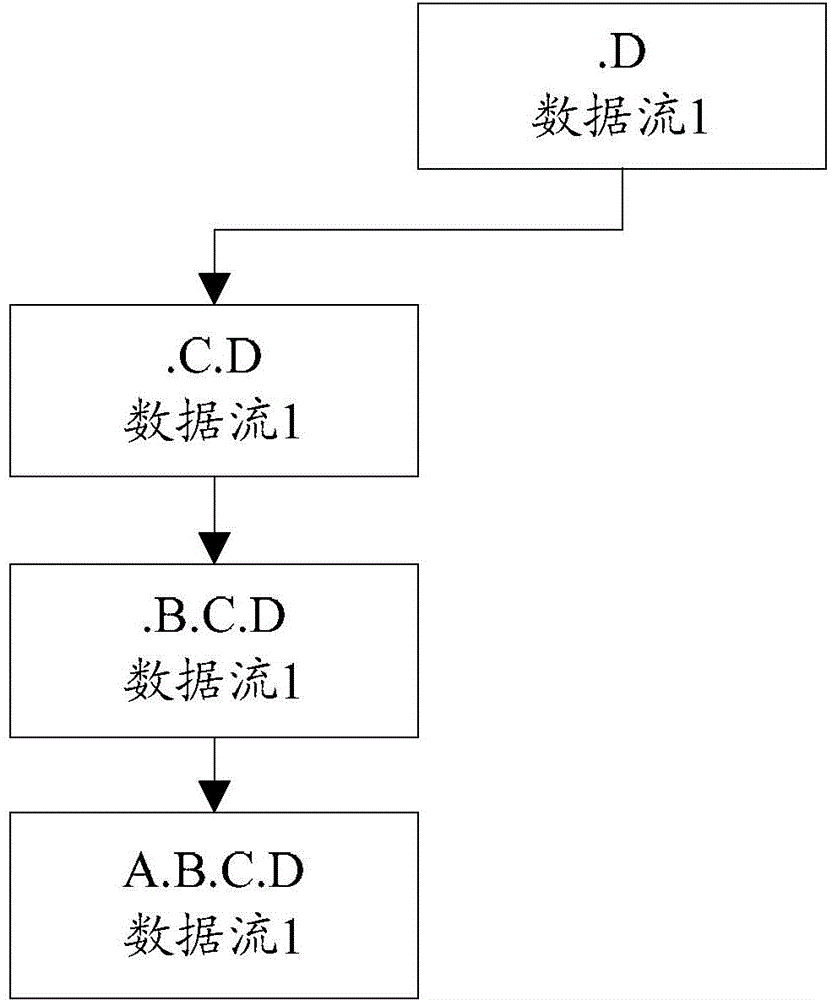
[0132] Example 1, assuming that the host of data stream 1 is identified according to the protocol type of data stream 1, and the host in the application layer protocol metadata of data stream 1 is A.B.C.D.
[0133] Then, before performing feature recognition, A.B.C.D is divided into multiple recognition contents step by step, namely: (.D), (.C.D), (.B.C.D), (A.B.C.D).
[0134] Assume that data flow 1 is the first data flow for host identification in the data packets to which it belongs, and therefore, the feature set for host identification is empty.
[0135] The process of host identification for data stream 1 is described in detail below:
[0136] First, match the recognition content.D with the features of each feature node in the feature set recognized by the host. Since the feature set recognized by the host is empty, there is no feature matching the recognition content, and then in the feature set recognized by the host Add a feature node (including feature: .D) that mat...
Embodiment 2
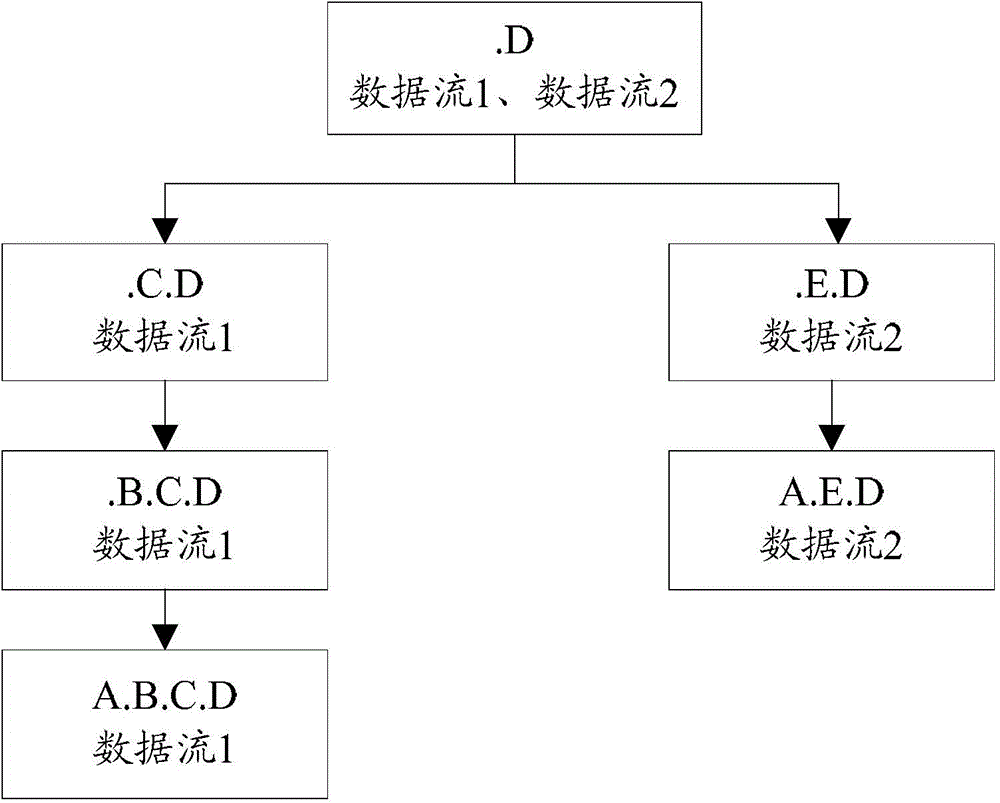
[0220] Embodiment 2 of the present invention provides another data packet feature extraction method, which takes the feature set as a tree structure, and uses specific examples to figure 1 The method for extracting the feature of the data packet shown is described in detail.
[0221] see Figure 4 , the method can include:
[0222] S401. Read the pcap file in the INPUT directory to obtain a data packet.
[0223] S402. Parse the data packet, and aggregate the packets with the same quintuple in the data packet into one data stream, and obtain 6 data streams.
[0224] Specifically, the six data streams are shown in Table 11:
[0225] Table 11
[0226]
[0227]
[0228] S403. For each data stream in the 6 data streams, use each feature recognition model corresponding to the protocol type of the data stream in the preset database to identify, and obtain feature sets of all types of the 6 data streams.
[0229] Among them, the preset database is shown in Table 1.
[0230...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com