A method of operating system kernel integrity protection
An integrity protection, operating system technology, applied in the field of integrity monitoring and protection of the operating system kernel, can solve problems such as reduced practicability, and achieve the effect of protecting security and executing safely and efficiently
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described below in conjunction with the accompanying drawings.
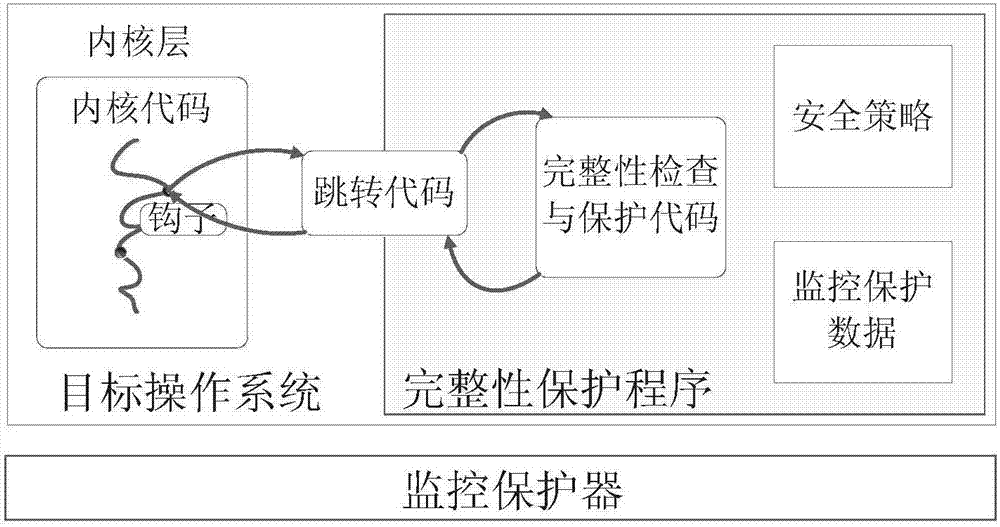
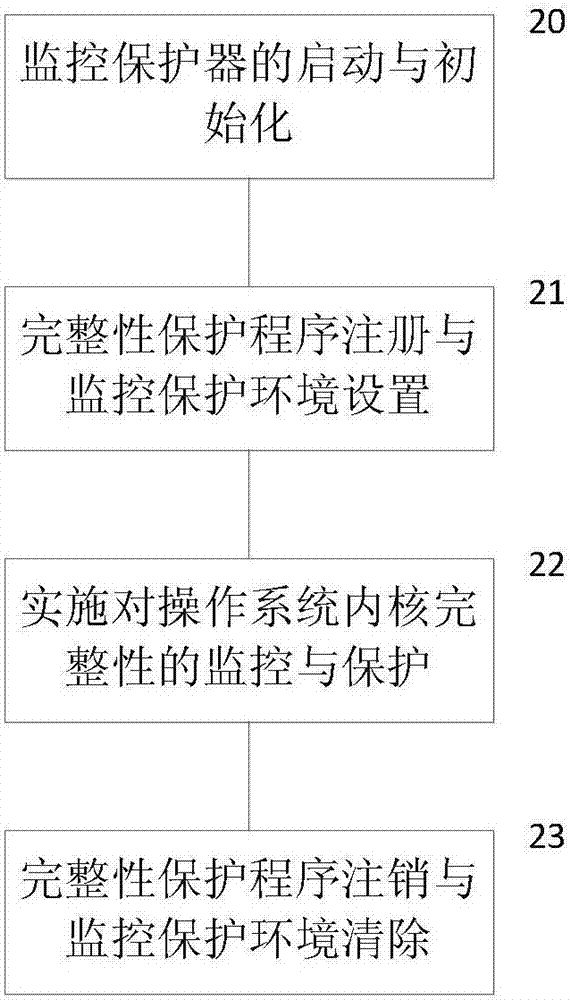
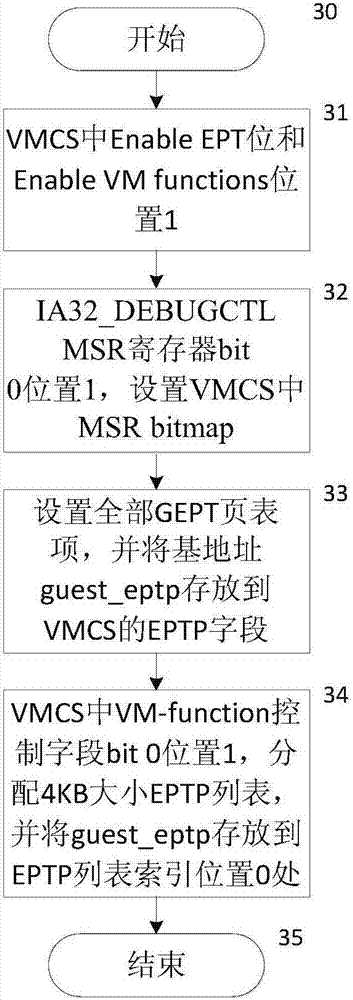
[0032] Such as figure 1As shown, an operating system kernel integrity protection system provided by the present invention includes components including an integrity protection program IPS, a kernel hook, a jump code, a target system Target OS, and a monitoring protector. When it is necessary to implement integrity monitoring and protection for the operating system kernel, the integrity protection program IPS is loaded into the Target OS address space of the target operating system through a kernel module, configures the monitoring protection environment, and registers with the monitoring protector , to build an isolated and protected operating environment. The integrity protection program IPS itself encapsulates the relevant codes for integrity checking and protection of the Target OS kernel, as well as the data segments and work stacks required at runtime, forming a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com