Identity verification method, apparatus and system
An identity verification method and identity verification technology, applied in user identity/authority verification, transmission systems, electrical components, etc., can solve problems such as illegal user identity, low security, and failed verification, so as to increase complexity, Effects of improving safety and increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] This embodiment will be described from the perspective of an identity verification device. The identity verification device may specifically be a device such as a terminal or a server, wherein the terminal may specifically be a device such as a mobile phone, a tablet computer, or a personal computer (PC, Personal Computer).
[0032] An identity verification method, comprising: obtaining a data processing request; obtaining identity verification information according to the data processing request, the identity verification information including image information, sound information, and associated information between the image information and sound information; judging the Whether the identity verification information matches the preset information sample; if yes, pass the data processing request; if not, reject the data processing request.
[0033] Such as Figure 1a As shown, the specific process of the authentication method can be as follows:
[0034] 101. Obtain a da...
Embodiment 2
[0079] In this embodiment, description will be made by taking that the identity verification device is specifically a server as an example.
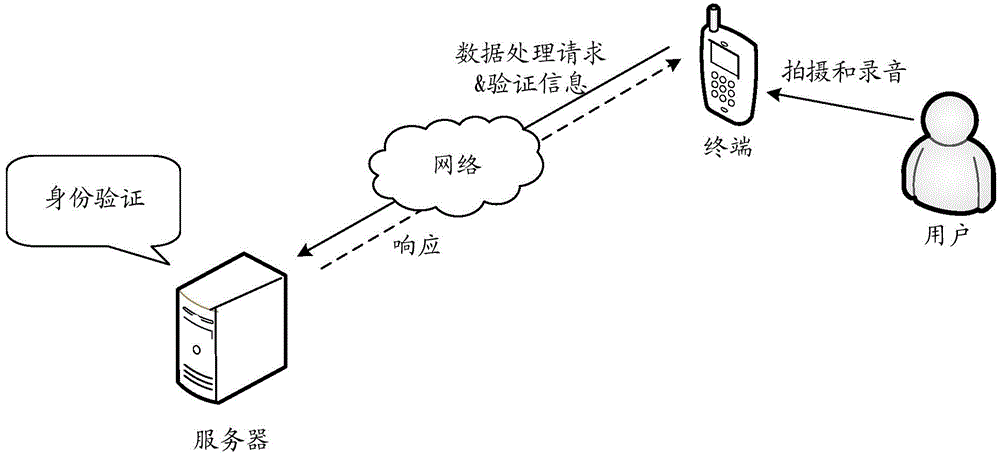
[0080] see Figure 2a , the communication system to which the identity verification method is applied may include a server and a terminal, specifically as follows:
[0081] (1) terminal;
[0082] The terminal is configured to send a data processing request to the server, and obtain identity verification information after receiving the identity information acquisition request sent by the server, and send the identity verification information to the server.
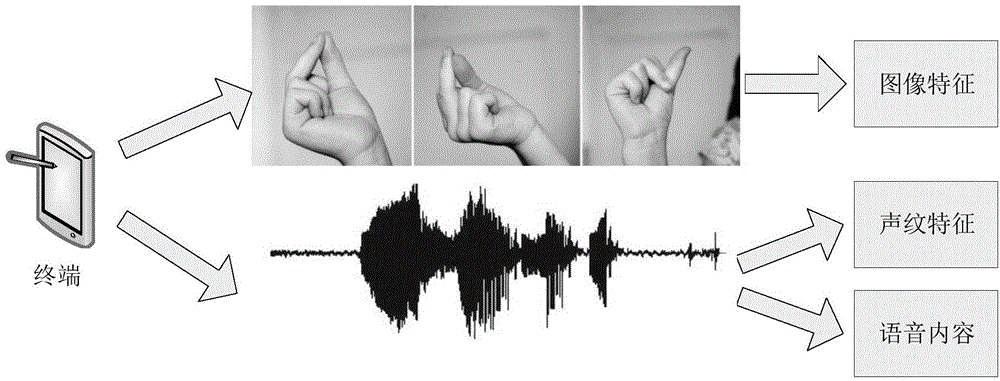
[0083] Wherein, the identity verification information includes information such as image information, sound information, and associated information between the image information and sound information.
[0084] Wherein, the association information between image information and sound information refers to the positional relationship and / or temporal relationship between the image in th...
Embodiment 3
[0112] In this embodiment, an example will be described in which the identity verification device is specifically a terminal, and the data processing request is specifically a terminal application start request.
[0113] Such as image 3 As shown, an authentication method, the specific process can be as follows:
[0114] 301. The terminal receives a terminal application launch request triggered by a user, for example, may instruct to open a certain terminal application, such as a photo album or a personal document, and so on.
[0115] 302. After receiving the terminal application startup request, the terminal generates and displays prompt information according to the terminal application startup request, wherein the prompt information instructs the user to take a video, or take a series of pictures and record a sound respectively, and receive the user's The prompt information indicates the recorded video, or pictures and information to obtain identity verification information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com