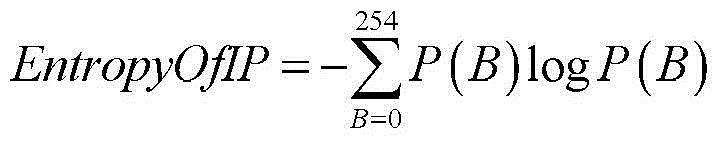Method and device for realizing malicious domain name identification
A domain name and malicious technology, applied in the field of information security, can solve problems such as unsatisfactory accuracy and recall rate, difficult physical location location of C&C server, and inability to identify malicious domain names
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
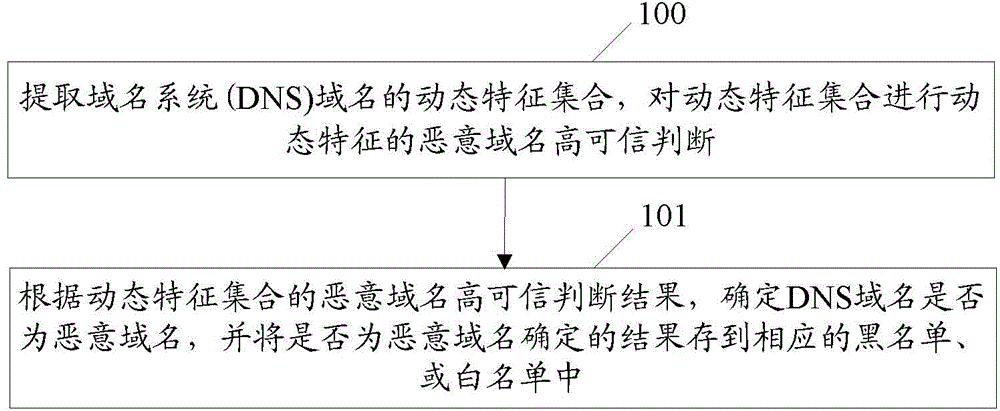
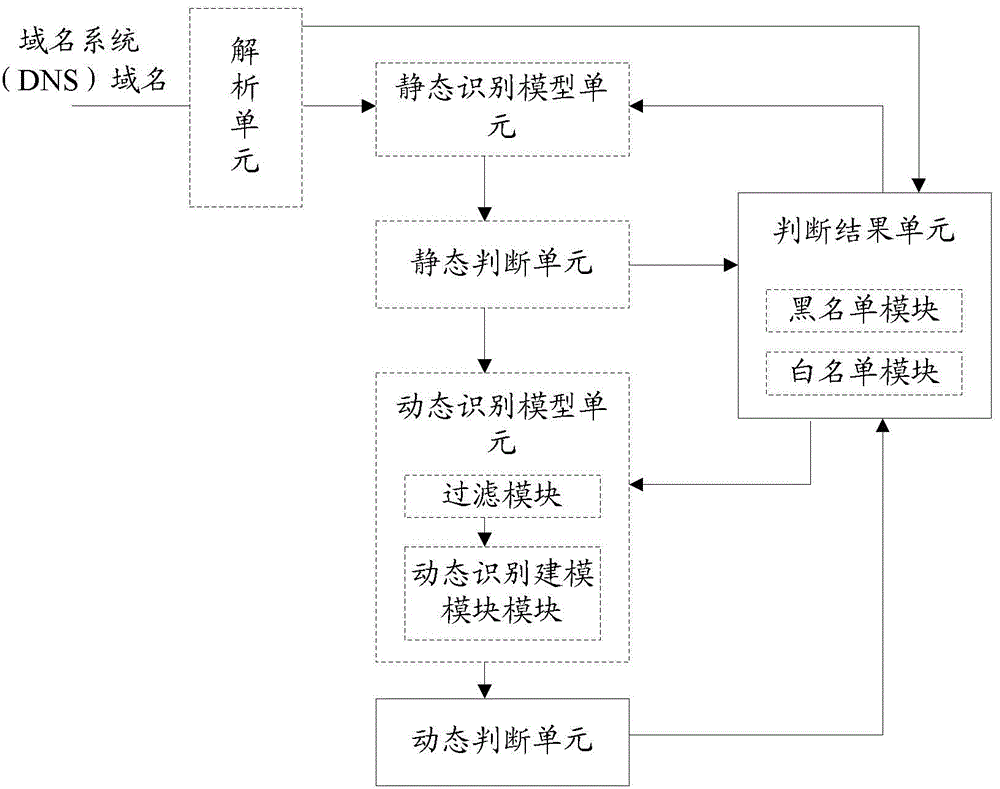
[0078] figure 1 A flow chart of the method for realizing malicious domain name identification in the present invention, such as figure 1 shown, including:
[0079] Step 100 , extracting a dynamic feature set of a domain name system (DNS) domain name, and performing a high-credibility judgment of a malicious domain name with dynamic features on the dynamic feature set through a credible judgment model of a malicious domain name with dynamic features.
[0080] Here, the dynamic feature set at least includes: features related to IP, and / or the consistency rate of the primary domain name of the authoritative DNS server.
[0081] It should be noted that the high-confidence judgment of the malicious domain name is judged by the SVM of the prior art,
[0082] For a domain name, its feature is a vector (or array), such as [1:0.1,2:0.4,3:0.1,…,8:0.9], which is used as the input of the support vector machine (SVM), and its output [MaliProbability:0.3,NormProbability:0.7], at this tim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com