FT-processor based trust management system and method
A management system and management method technology, applied in electrical digital data processing, instruments, digital data authentication, etc., can solve the problem of no operating system file verification, and achieve the effect of avoiding attacks, ensuring security, reliability, and flexible management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] A trusted management system based on Feiteng processor, said system comprising:
[0044] 1) Terminal management module: used to manage terminals and terminal security and trusted policies;
[0045] 2) TCM initialization module: used for TCM initialization and program whitelist initialization after the terminal deploys the trusted management system for the first time;
[0046] 3) Terminal trusted module: used for terminal program installation and operation control, and communicates with the terminal management module to update security and trusted policies;
[0047] 4) BIOS measurement module: used to measure the integrity of the operating system kernel and system key files;
[0048] 5) USBKey: used for operating system identity authentication and storing TCM keys;
[0049] 6) TCM module: Trusted cryptographic module, used to store keys, built-in cryptographic algorithms to provide cryptographic services such as hash calculations.
Embodiment 2
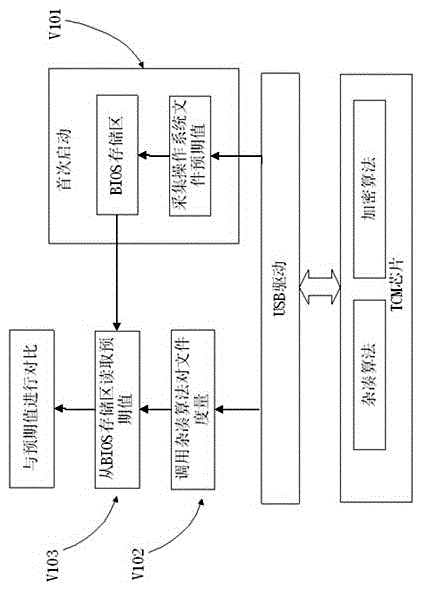
[0051] On the basis of embodiment 1, the BIOS measurement module operation steps described in the present embodiment are as follows:
[0052] Step I1: turn on the power, the BIOS calls the TCM cryptographic algorithm to calculate the hash value of the operating system kernel and system key files, and obtain the hash value;
[0053] Step 12: The BIOS compares the hash value with the expected value stored inside the BIOS, and if they are the same, proceed to the next step, otherwise prohibit the system from starting.
Embodiment 3
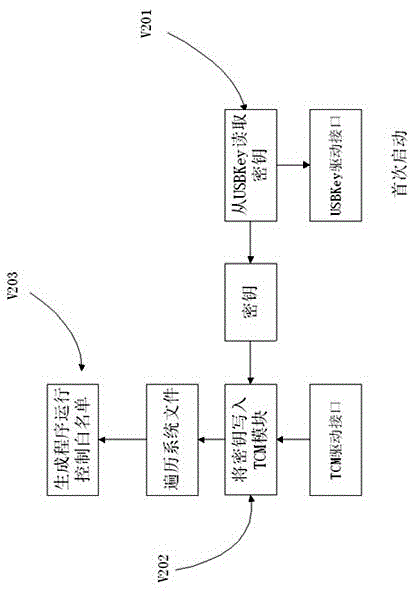
[0055] On the basis of Embodiment 1, the operation steps of the TCM initialization module described in this embodiment are as follows:
[0056] Step S1: Connect the user's USBKey device to the computer, and the USBKey stores the key;
[0057] Step S2: Log in to the operating system through the USBKey, the TCM initial module starts automatically, prompts to input basic user information, then calls the USBKey interface function to read the key from the USBkey, and imports the key into the TCM module through the TCM interface;
[0058] Step S3: Scan the operating system file, call the TCM cryptographic algorithm to generate a program operation control white list, and the program operation control white list is used for the terminal trusted module.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com