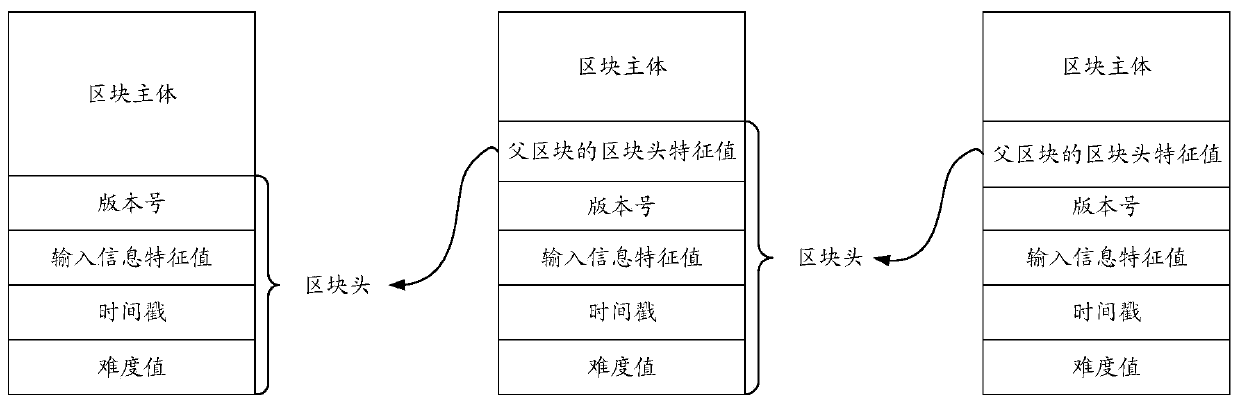
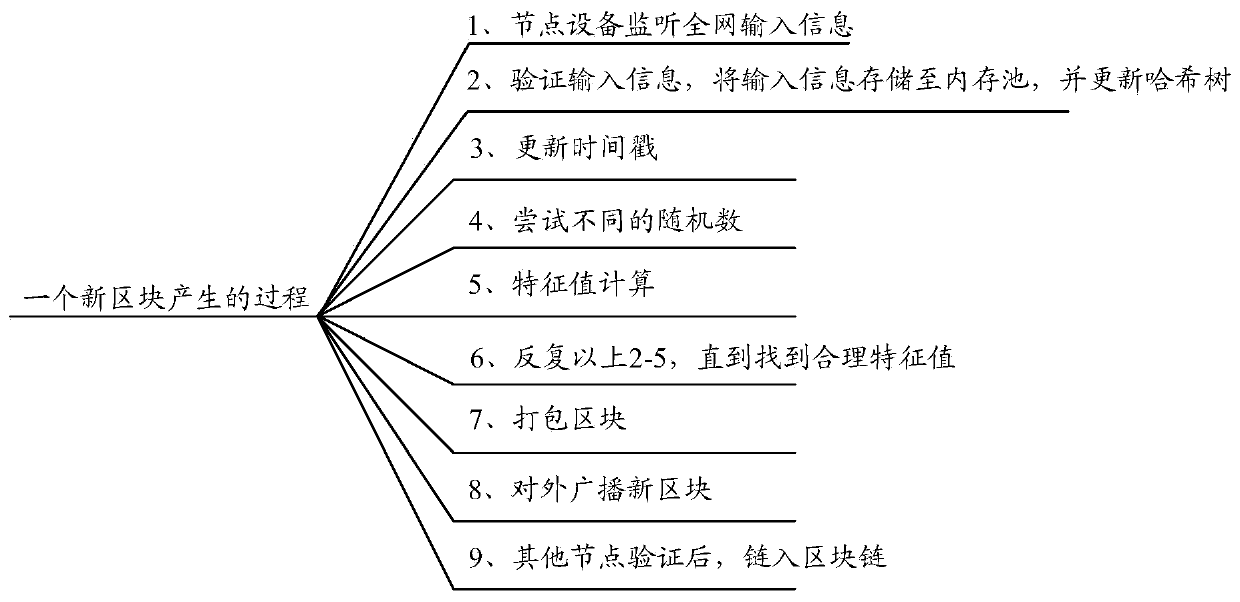
Patents
Literature
36results about How to "Guaranteed to be legal" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
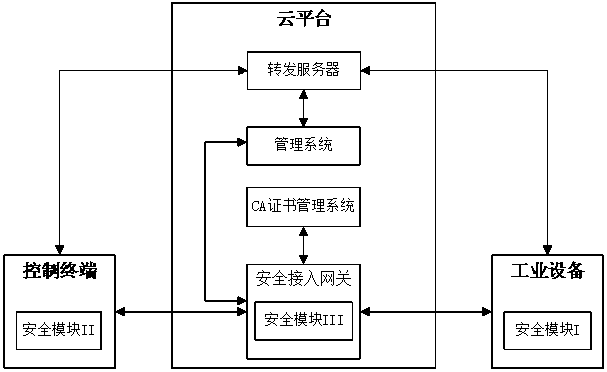
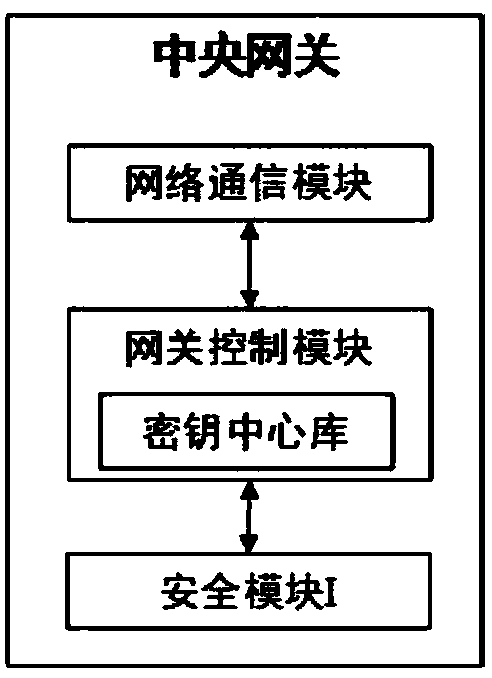
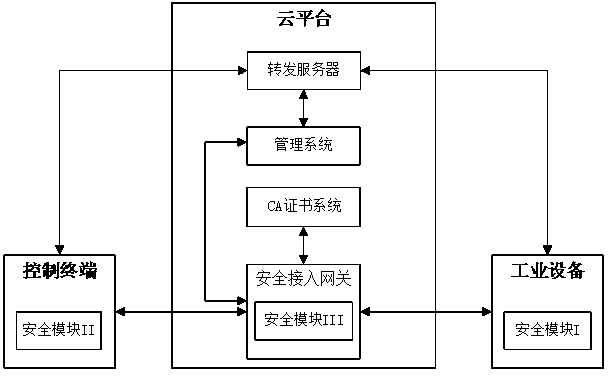
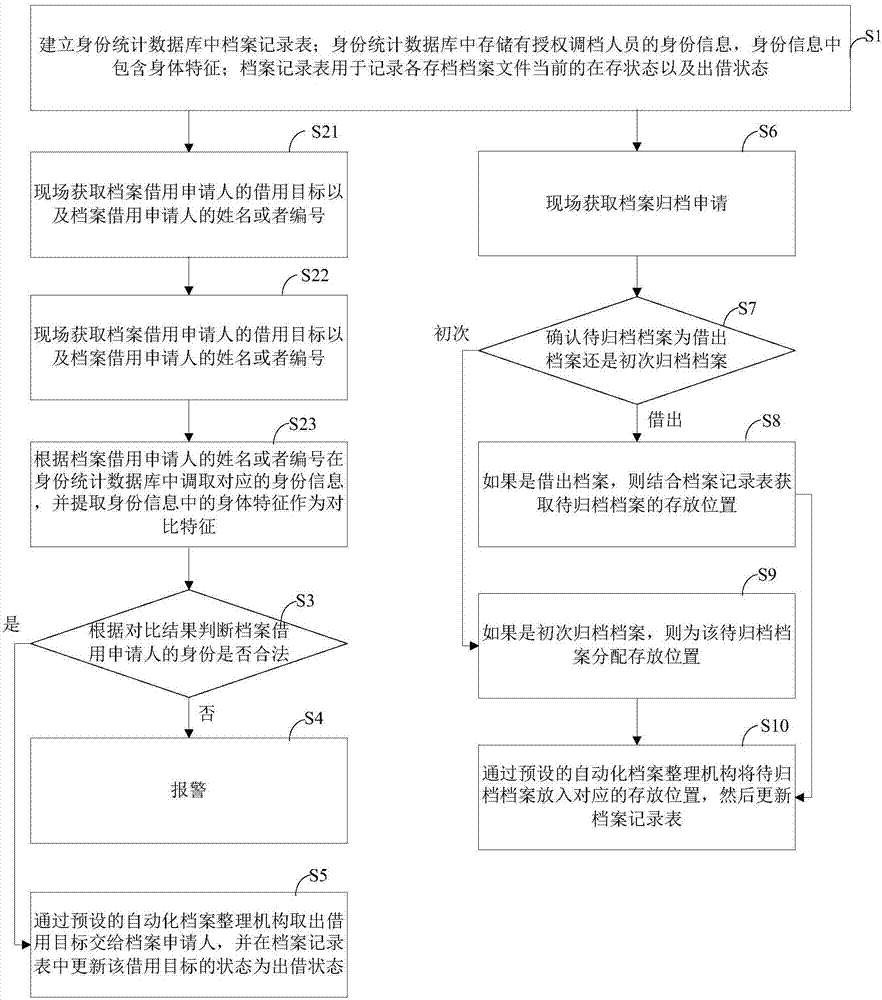
Security remote control system and method for industrial equipment
ActiveCN108390851AHighlight substantiveSignificant progressKey distribution for secure communicationUser identity/authority verificationRemote controlControl system
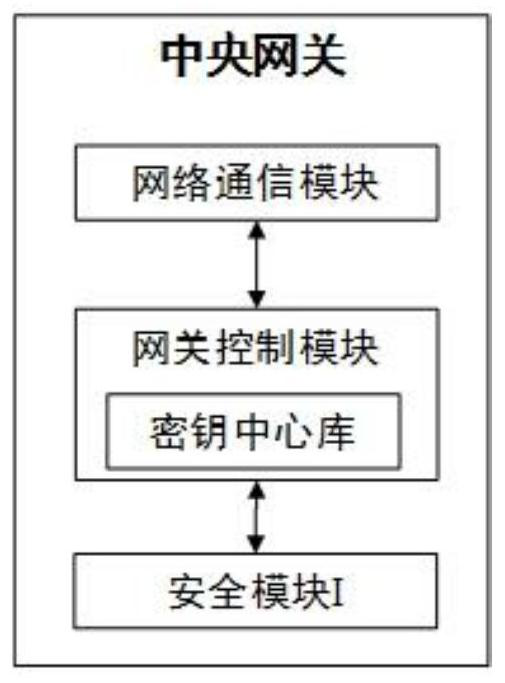
The invention provides a security remote control system and method for industrial equipment. The system comprises industrial equipment, a control terminal and a cloud platform, wherein a security module I is arranged in the industrial equipment, a security module II is inserted into or arranged in the control terminal, the cloud platform comprises a security access gateway, a management system, aCA certificate management system and a forwarding server, and a security module III is arranged in the security access gateway. In remote control, the industrial equipment and the security access gateway perform bidirectional identity authentication and key negotiation and create a first session key; the control terminal and the security access gateway perform bidirectional identity authenticationand key negotiation and create a second session key; the control terminal and the industrial equipment perform bidirectional identity authentication and key negotiation through the forwarding serverand then create a third session key; and the control terminal performs security remote control on the industrial equipment by using the third session key through the forwarding server.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
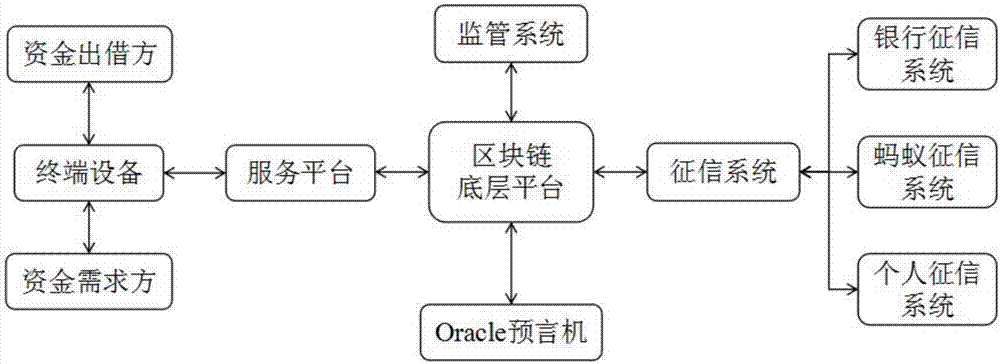
System and method for logistics financing management based on block chain technology
InactiveCN107977811AWith creditMarket-oriented lendingFinanceLogisticsLogistics managementTerminal equipment
The present invention discloses a system and a method for logistics financing management based on a block chain technology, and relates to the technical field of logistics financing management. The system comprises a block chain ground floor platform which is in information interaction with a credit reference system, a supervision system, a service platform and an Oracle prediction machine througha data transmission and storage module; the credit reference system is connected with a bank credit reference system, an ant credit reference system and an individual credit reporting system; and theservice platform performs data transmission with the terminal device through the data transmission module. The system and the method for logistics financing management based on the block chain technology utilize the effects of the block chain ground layer platform, the credit reference system, the supervision system and the service platform to solve the problems that current loan principal and interest recovery risk are high, the information of a loan market is not opaque, the information of the lower-cost and safer fund is difficult to obtain and a supervision means is lack to go against local economic development.
Owner:HEFEI WEITIANYUNTONG INFORMATION TECH CO LTD
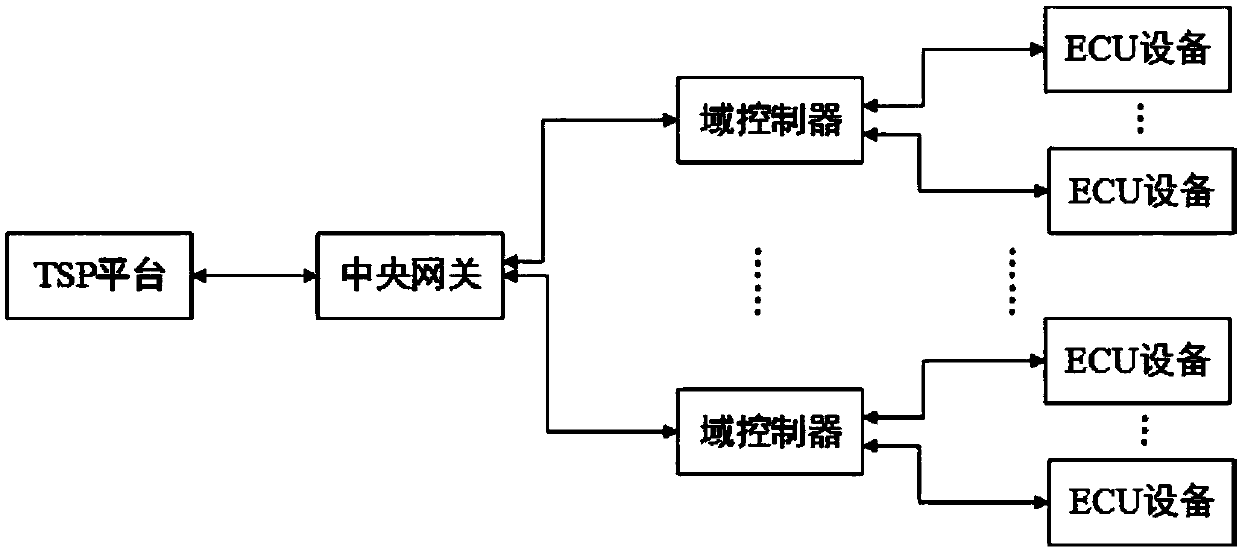
In-vehicle network safety communication system and method
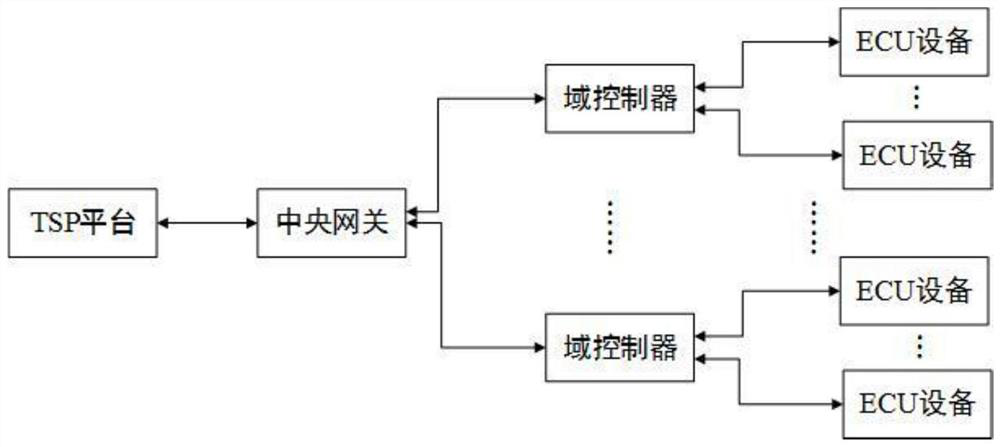
ActiveCN110943957AGuaranteed to be legalEnsure safetyKey distribution for secure communicationSecure communicationNetwork connection
The invention provides an in-vehicle network safety communication system and method. The in-vehicle network safety communication system comprises a TSP platform, a central gateway, a domain controllerand ECU equipment. The TSP platform is connected with the central gateway through a network, the central gateway is connected with the one or more domain controllers through a network, and the domaincontrollers are connected with the one or more ECU devices through vehicle buses. The method comprises: after first identity authentication and key negotiation are carried out between the TSP platform and the central gateway, constructing a first secure channel, and the TSP platform carrying out encrypted communication with the central gateway through the first secure channel; performing second identity authentication and key distribution between the central gateway and the domain controller, and then constructing a second secure channel, wherein the central gateway performs encrypted communication with the domain controller through the second secure channel; and after third identity authentication and key distribution are carried out between the domain controller and the ECU equipment, constructing a third secure channel, and the domain controller carrying out encrypted communication with the ECU equipment through the third secure channel.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
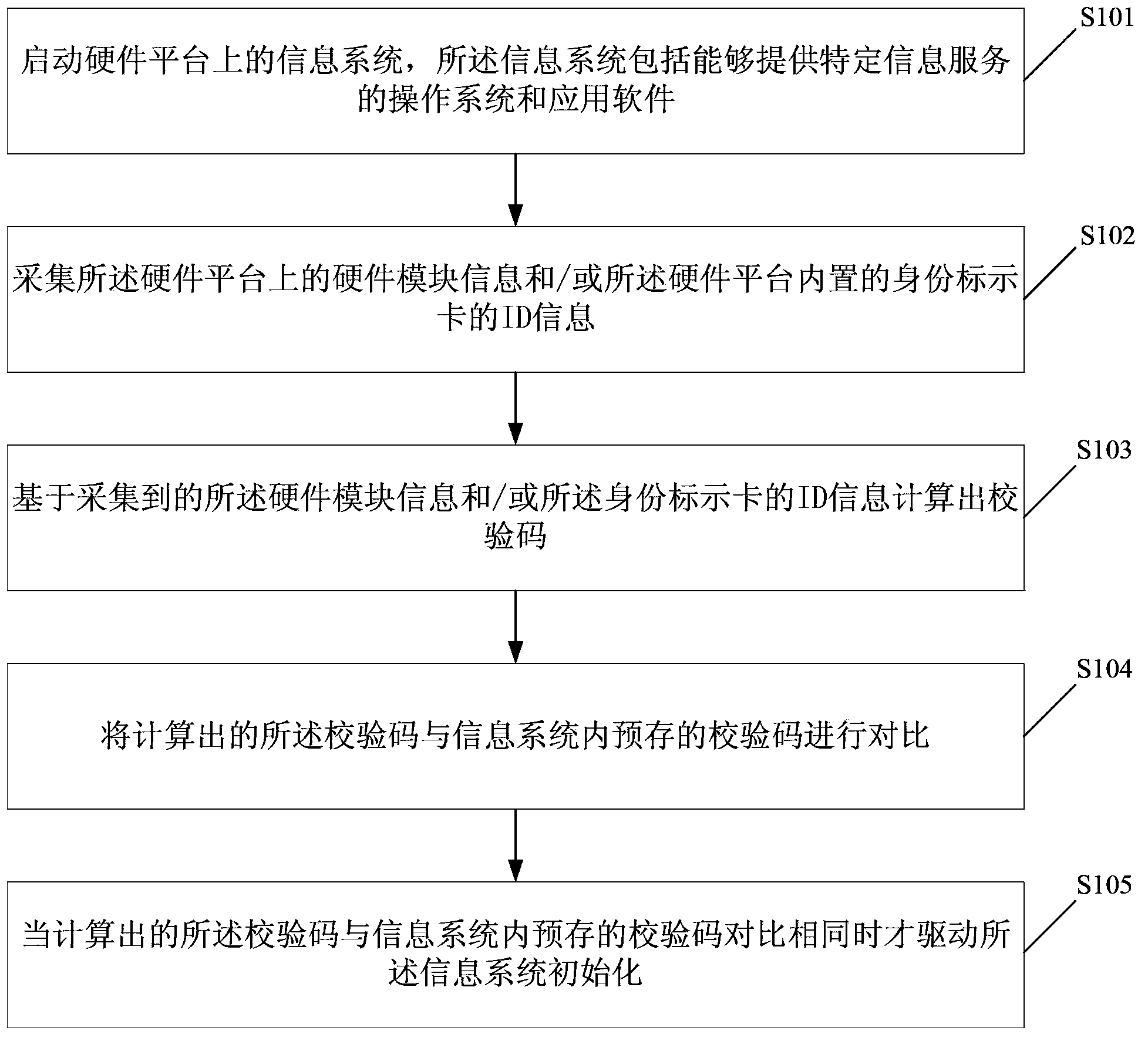
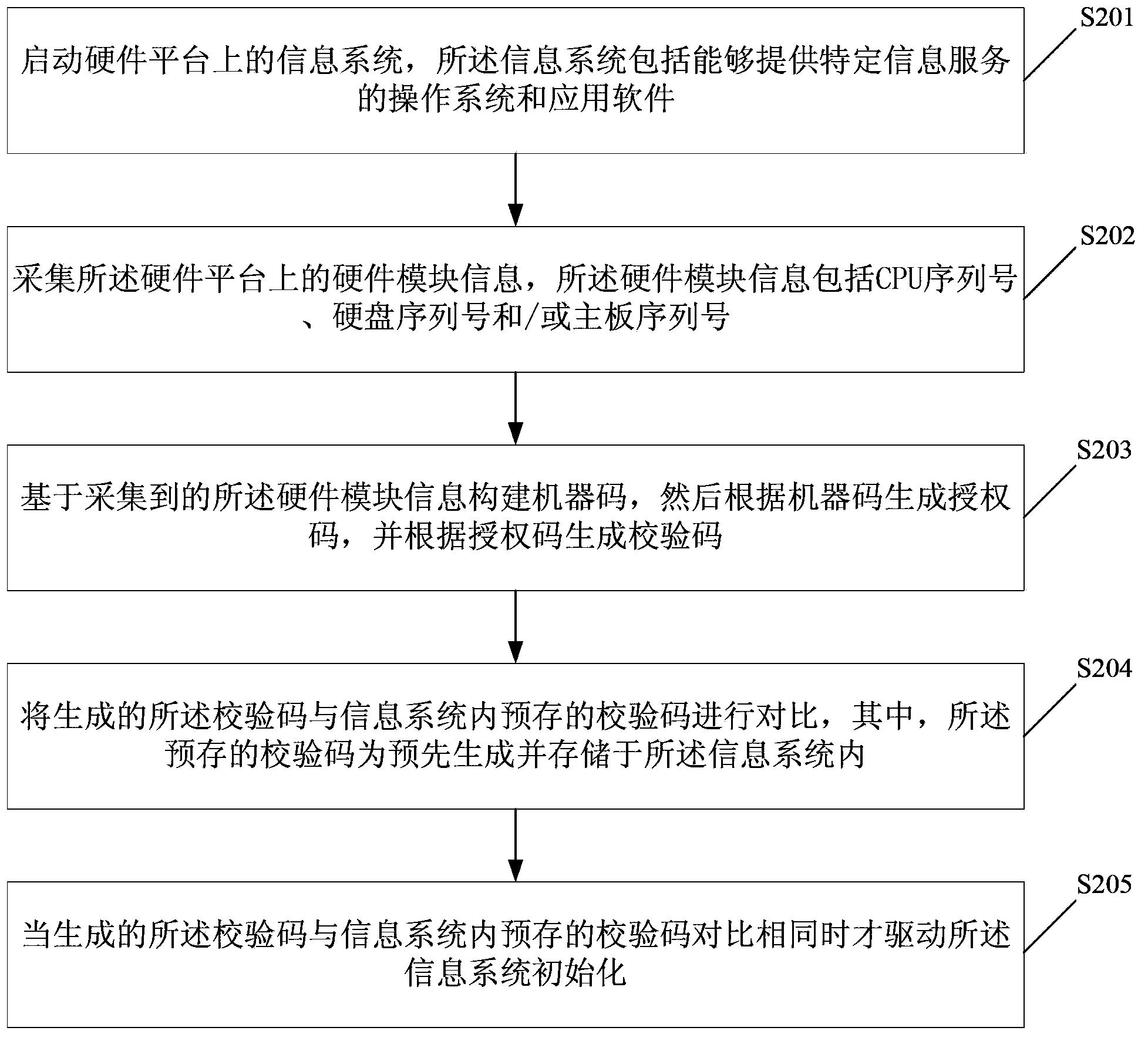
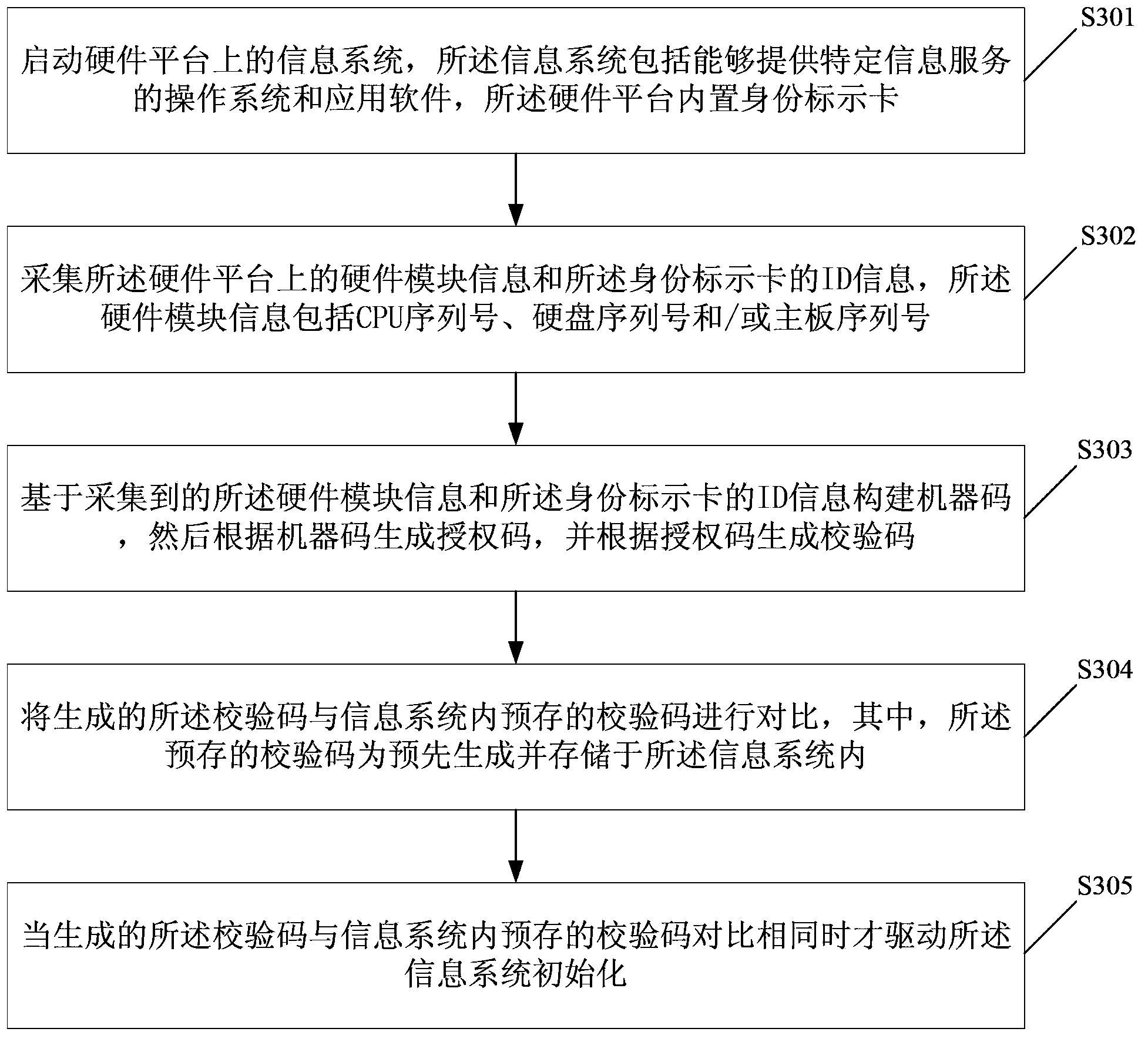
Control method and system for operating information system
ActiveCN104166809AGuaranteed to be legalEasy to useDigital data authenticationProgram/content distribution protectionComputer hardwareOperational system
The invention discloses a control method for operating an information system. The control method comprises the steps that the information system on a hardware platform is started, and the information system comprises application software and an operating system capable of providing a specific information service; hardware module information on the hardware platform and / or ID information of an identity marking card in the hardware platform are / is collected; a check code is worked out according to the collected hardware module information and / or the ID information of the identity marking card; the worked out check code is compared with a check code prestored in the information system; when the worked out check code is the same as the check code prestored in the information system, the information system is driven to be initialized. The invention further discloses a control system for operating the information system.
Owner:GCI SCI & TECH
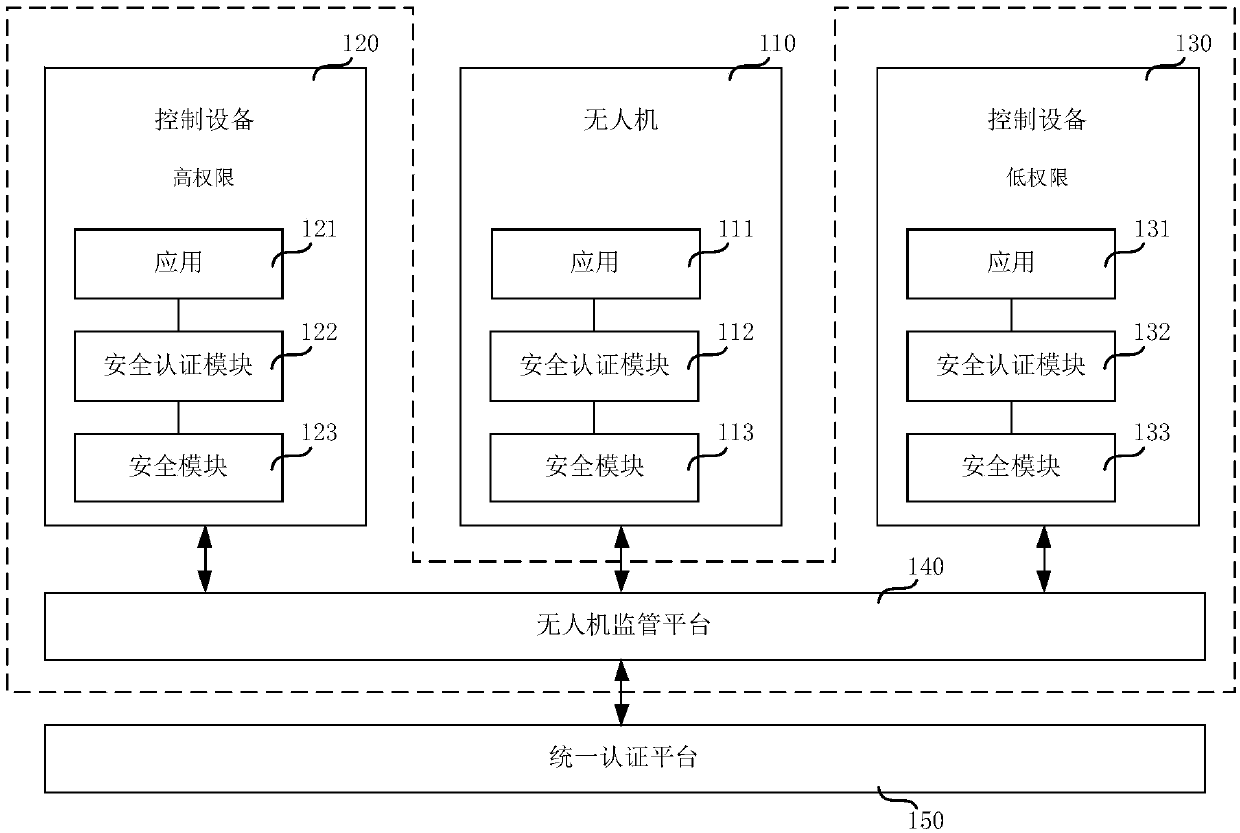
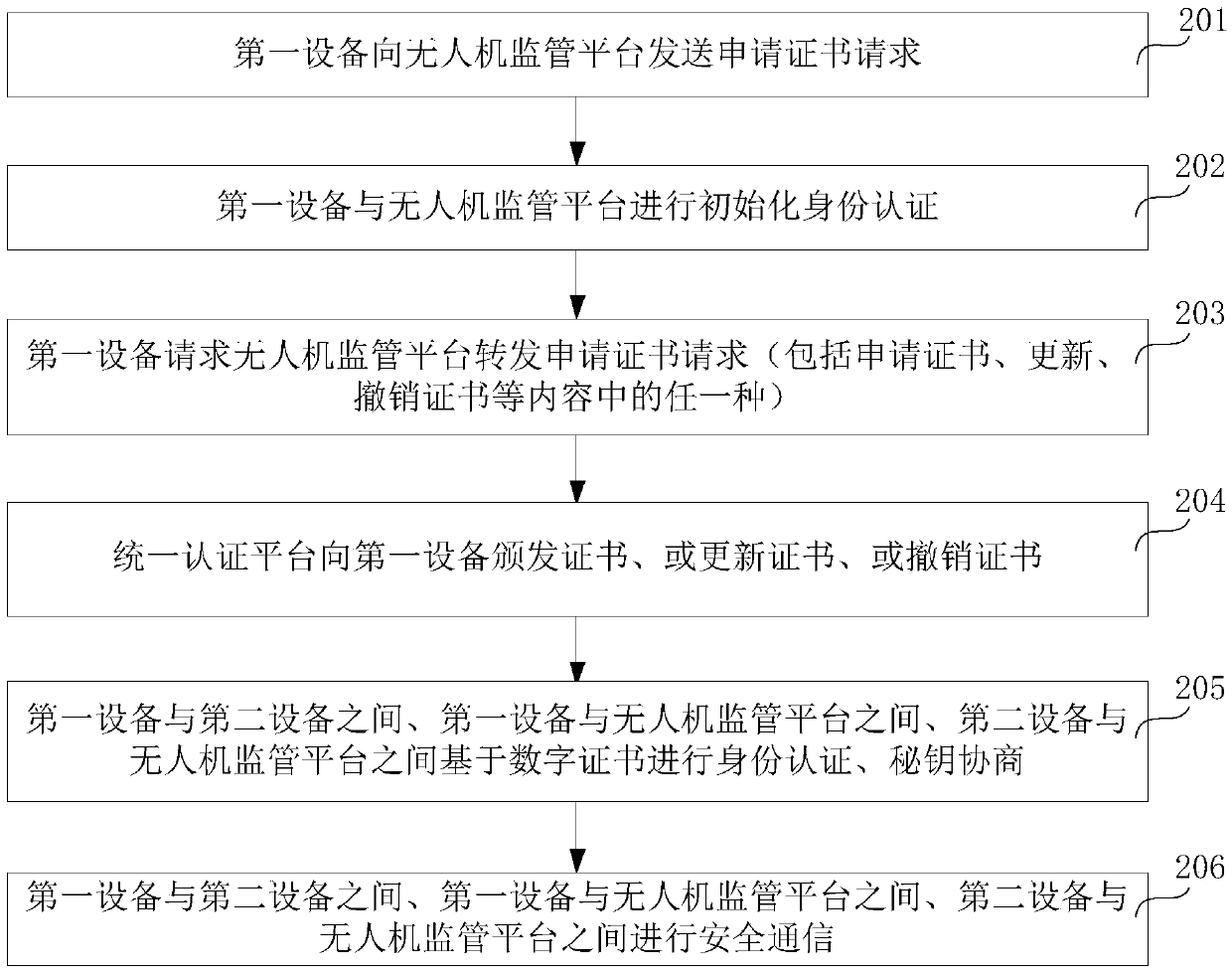
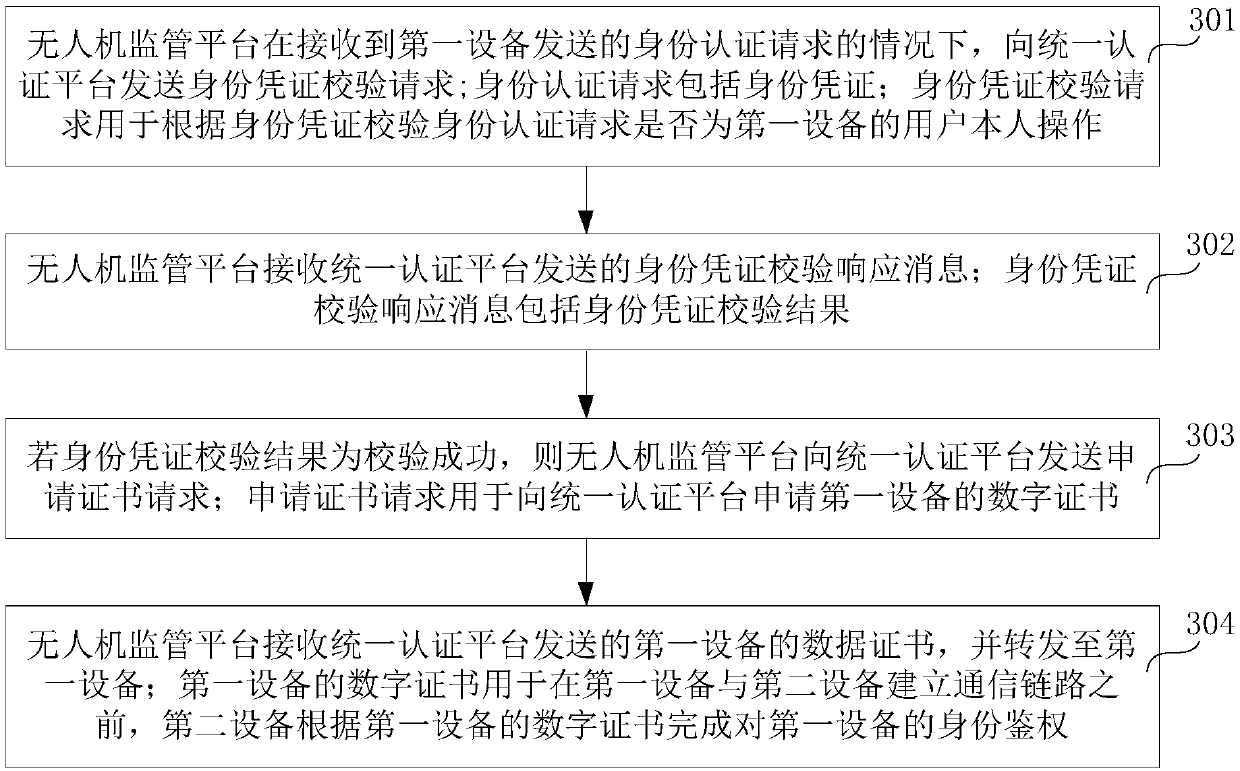
Unmanned aerial vehicle authentication method and system, unmanned aerial vehicle supervision platform and first equipment
InactiveCN109995719ARealize the bindingEnsure communication securityTransmissionTelecommunications linkCommunication link
The embodiment of the invention relates to the technical field of unmanned aerial vehicle authentication, in particular to an unmanned aerial vehicle authentication method and system, an unmanned aerial vehicle supervision platform and first equipment, and is used for confirming whether identities of two communication parties are legal. When receiving the identity authentication request sent by the first device, the unmanned aerial vehicle supervision platform sends an identity certificate verification request to the unified authentication platform and receives an identity certificate verification response message; if the identity certificate verification result is that the verification is successful, a certificate application request is sent to a unified authentication platform; a data certificate of the first device is received, and the data certificate is forwarded to the first device; wherein the digital certificate of the first device is used by the second device to complete identity authentication of the first device according to the digital certificate of the first device before the first device establishes a communication link with the second device. Therefore, before thefirst equipment and the second equipment establish the communication link, the binding between the user information and the first equipment and between the first equipment and the digital certificateis realized, so that the legitimacy of the identities of the two communication parties can be ensured.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +2
Voting processing method and device based on block chain
ActiveCN111369730AEnsure safetyGuaranteed reliabilityVoting apparatusDigital data protectionIdentity recognitionDatabase
The invention provides a voting processing method and device based on a block chain, node equipment and a storage medium, and belongs to the technical field of block chains. According to the voting processing method, decentralized and persistent block chain type storage of the voting related information is carried out for exiting the service by adopting the block chain, voters are identified through the biological characteristics, so identity legitimacy of voting participants can be ensured while security and reliability of the voting data are ensured, the condition that other people counterfeit the voters in the voting process is prevented, and credibility of the voting result can be ensured.
Owner:TENCENT TECH (SHENZHEN) CO LTD
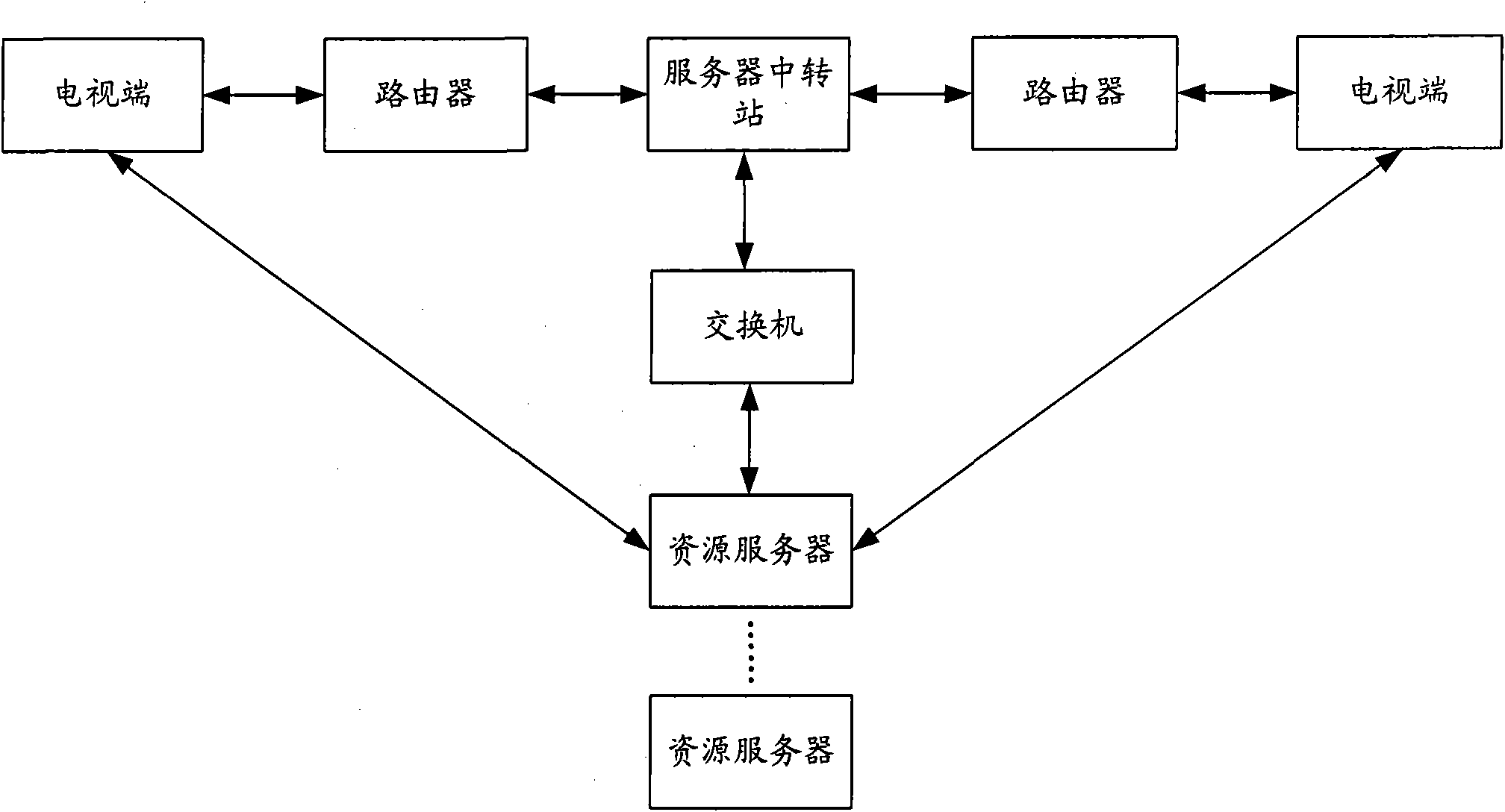
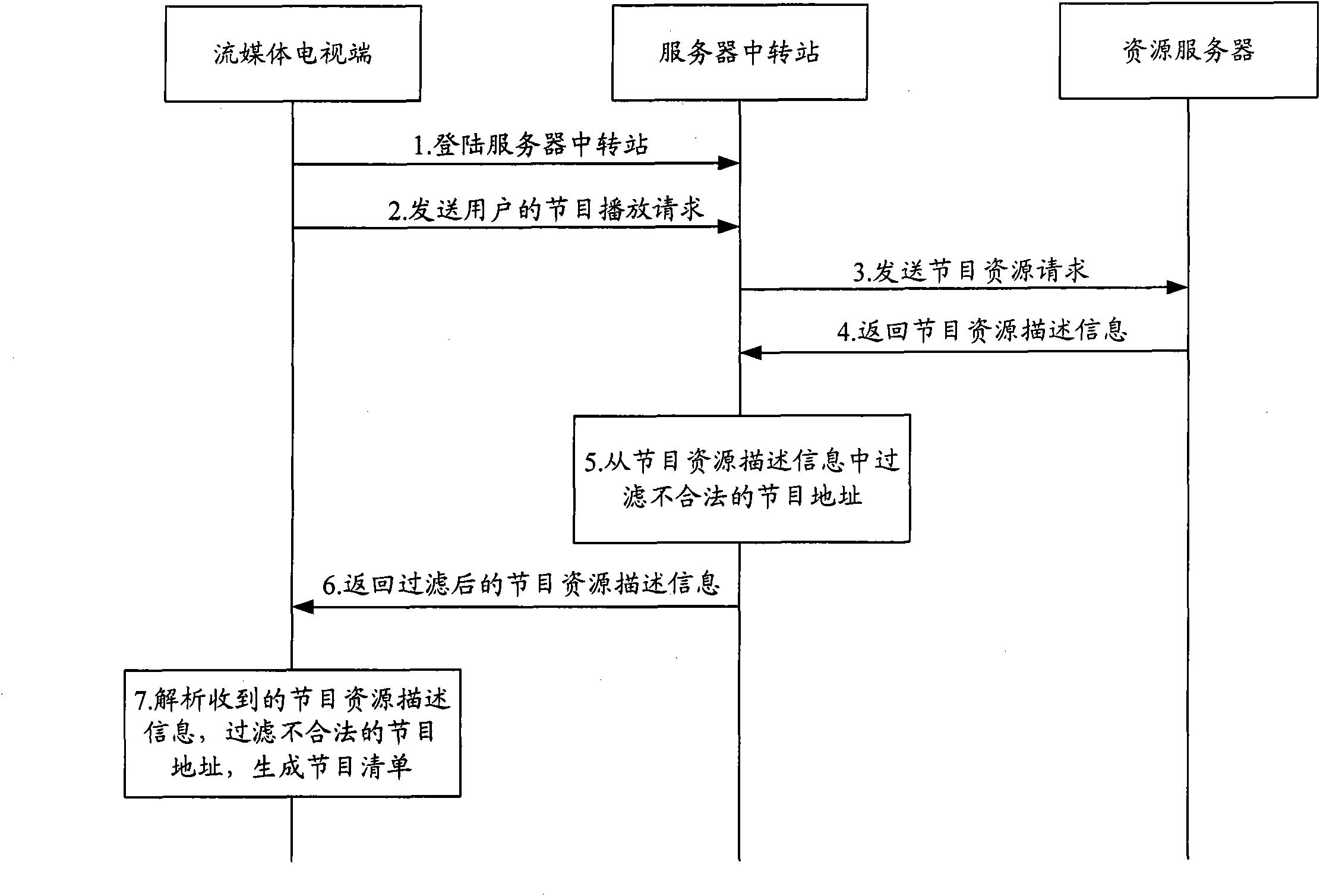
System, method, device and installation for filtering programs
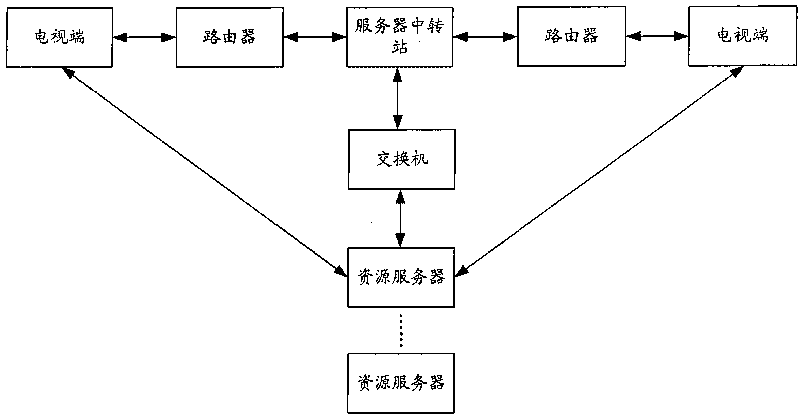
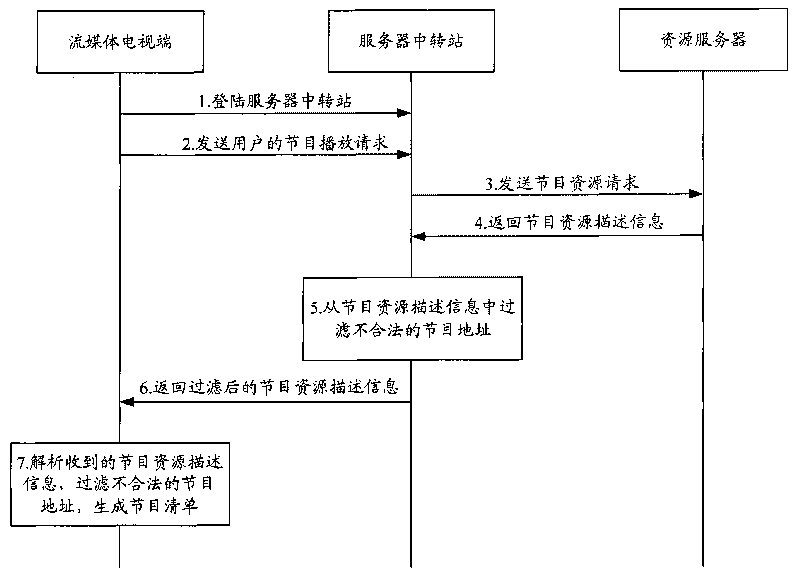
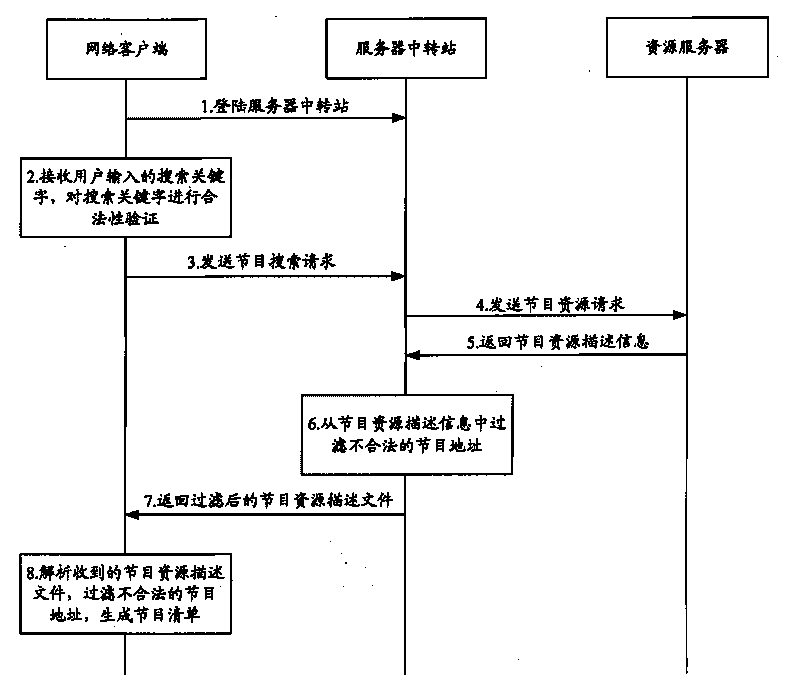
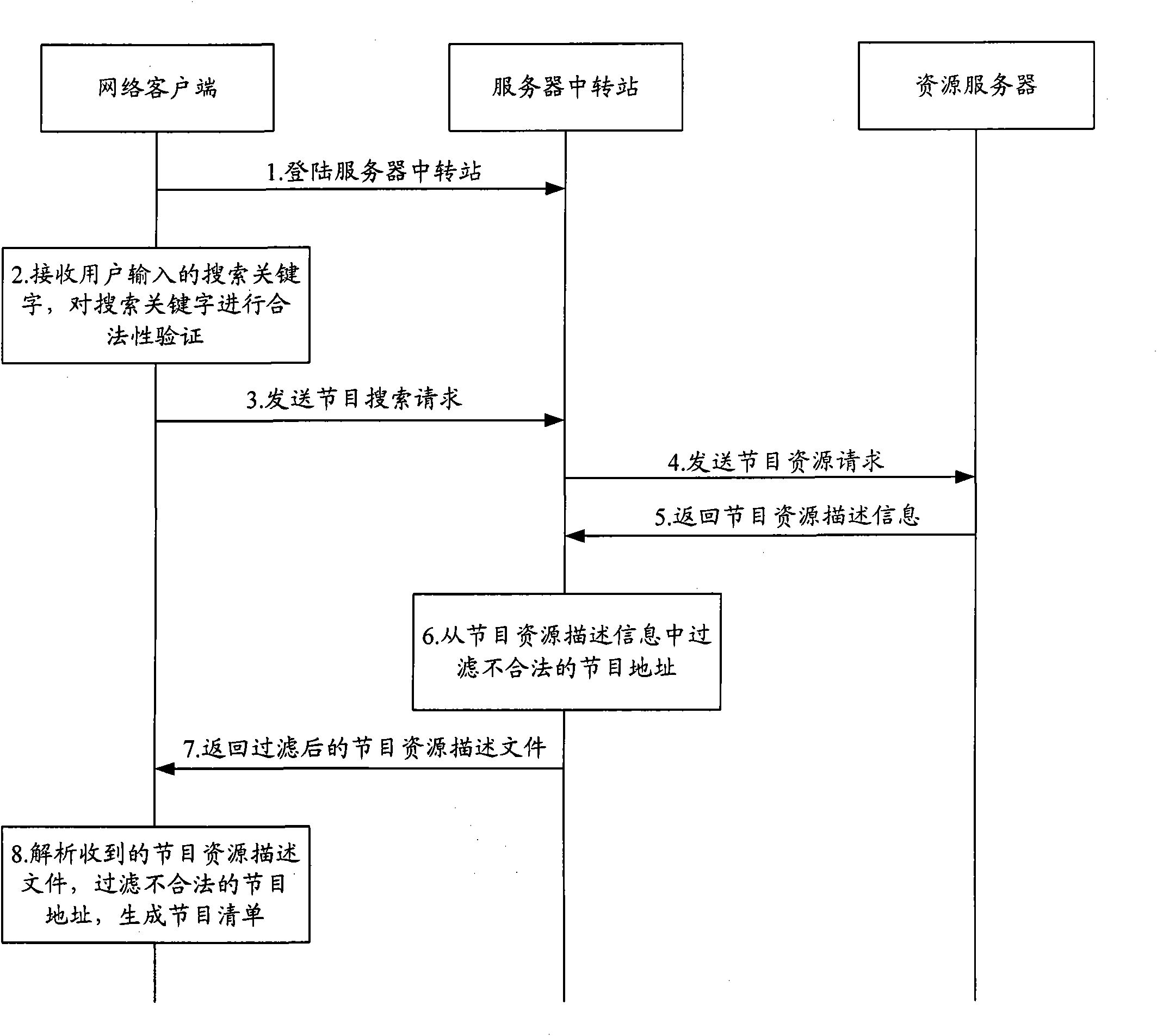
InactiveCN101729853AGuaranteed to be legalKeep healthyAnalogue secracy/subscription systemsTwo-way working systemsClient-sideResource description
The invention is suitable for the field of communication, and provides a system, a method, a device and an installation for filtering programs. The system comprises a plurality of network clients and at least a server transfer station in a network connection with the network clients and resource servers providing program contents. The server transfer station obtains the resource description information of the programs requested by the network client from the resource servers, and filters resources addresses of illegal programs in the resource description information. The network clients analyze the resource description information transmitted by the server transfer station after filtering the resources addresses of the illegal programs, further filter the illegal programs in the analyzed program information, and generate a program list allowed to be played. The embodiment of the invention carries out multi-stage filtration on the programs through the server transfer station and the network clients, ensures legal and health content of the programs, and is beneficial to reducing illegal incidents and incidents of violating discipline.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
PLC remote firmware upgrading system and method
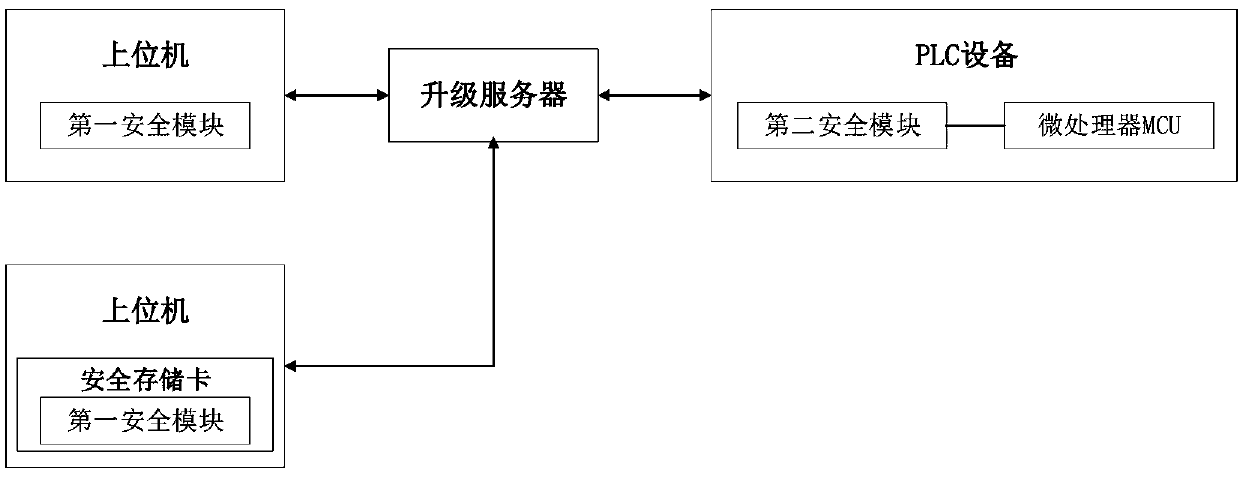
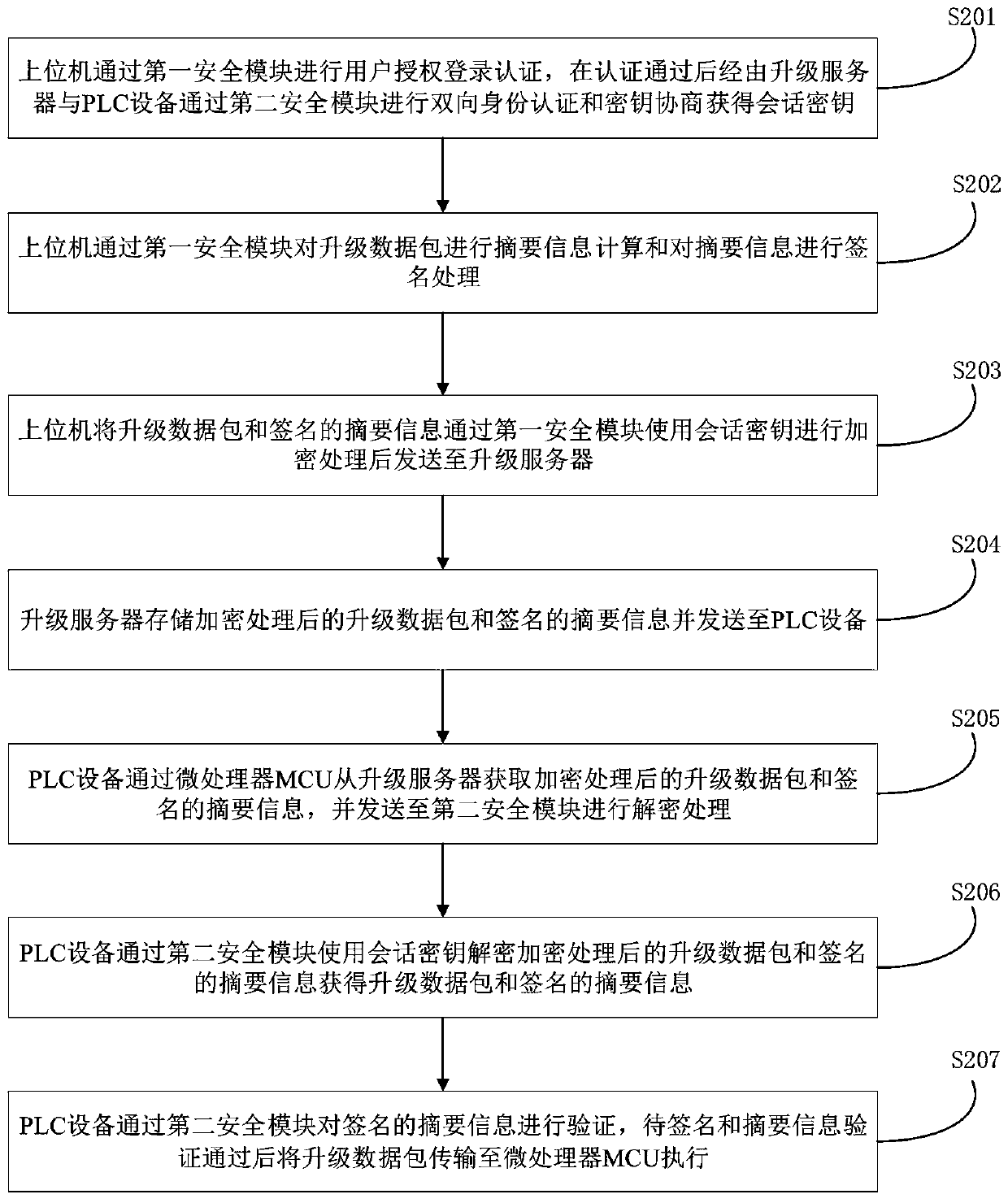
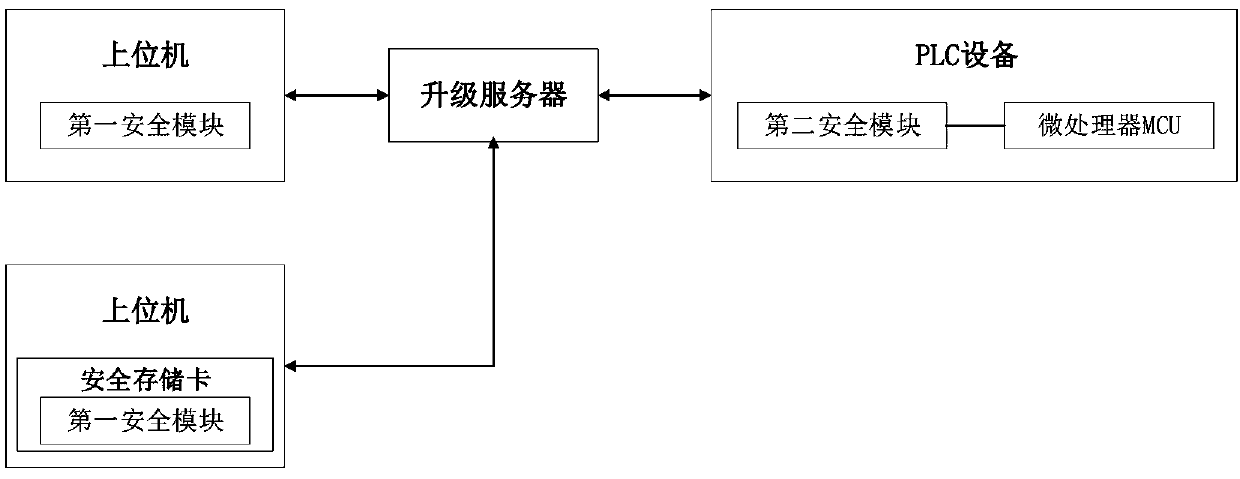
InactiveCN111143856AHighlight substantiveSignificant progressDigital data protectionDigital data authenticationData packConfidentiality
The invention provides a PLC (Programmable Logic Controller) remote firmware upgrading method, which comprises the following steps that: after an upper computer performs user authorization login authentication through a first security module, an upgrading server and PLC equipment perform bidirectional identity authentication and key negotiation through a second security module to obtain a sessionkey; the upper computer performs summary information calculation on the upgrading data packet and signs summary information through the first security module, and sends the summary information to theupgrading server after the summary information is encrypted by using a session key; the upgrade server sends the encrypted upgrade data packet and the signed abstract information to the PLC device; the PLC device decrypts the encrypted abstract information of the upgrade data packet and the signature by using the session key through the second security module to obtain the abstract information ofthe upgrade data packet and the signature; the PLC device verifies the signed abstract information through the second security module and then executes the upgrade data packet; according to the invention, the remote firmware upgrading of the PLC equipment and the confidentiality and integrity of the upgrading data packet are realized.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Method and system for controlling trusted root in BIOS
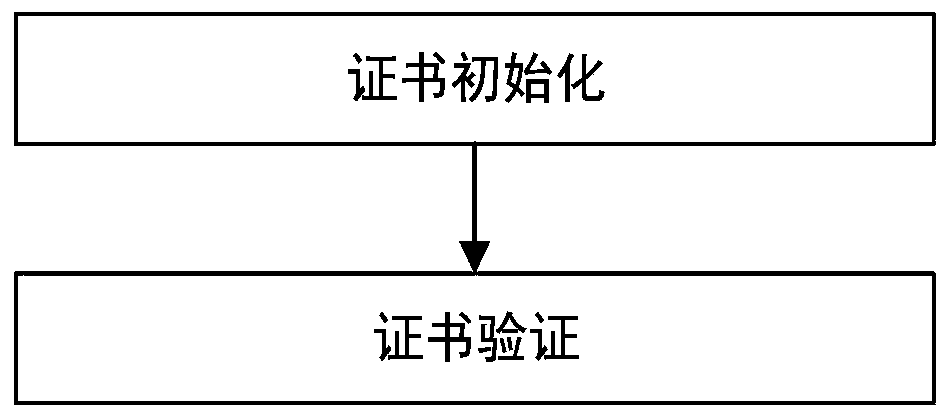
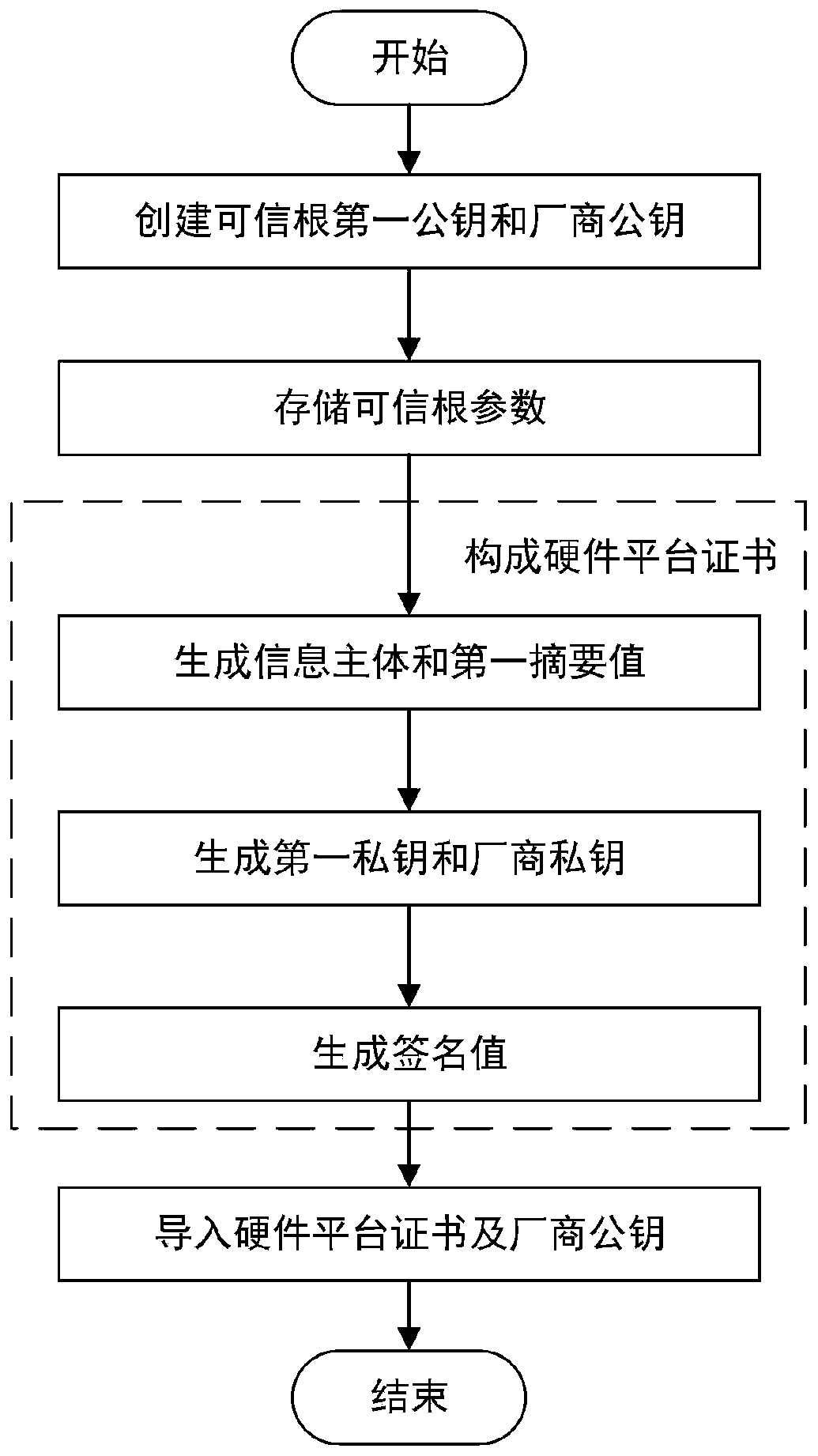
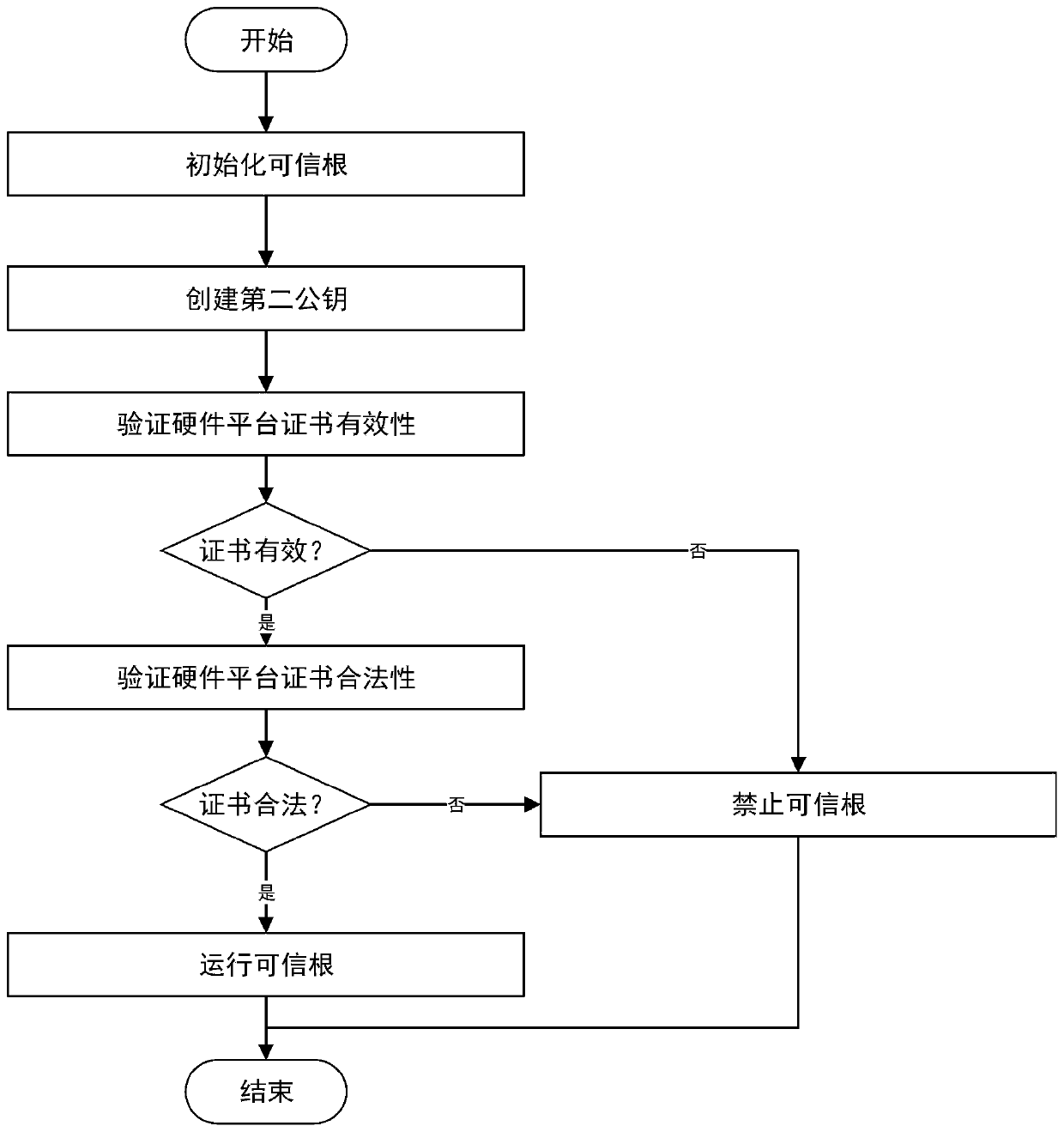
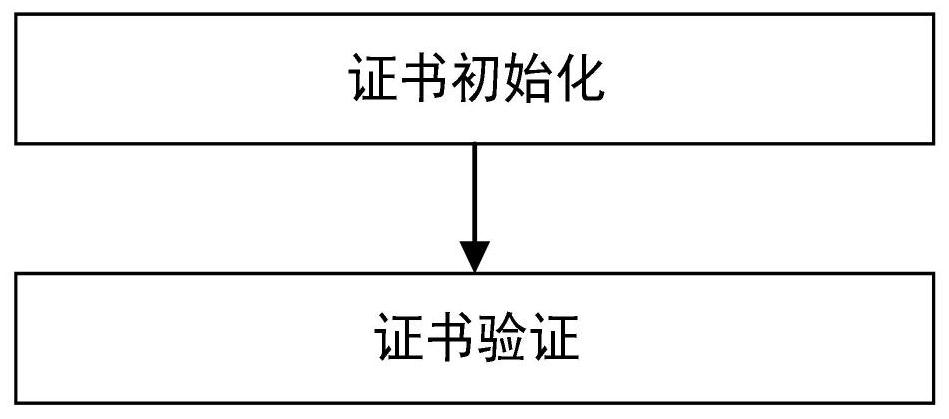
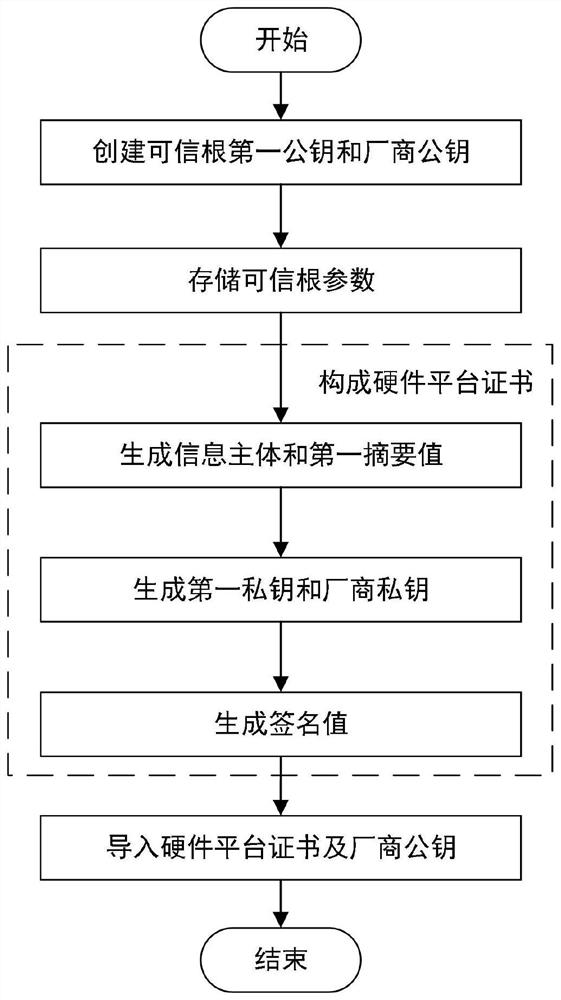
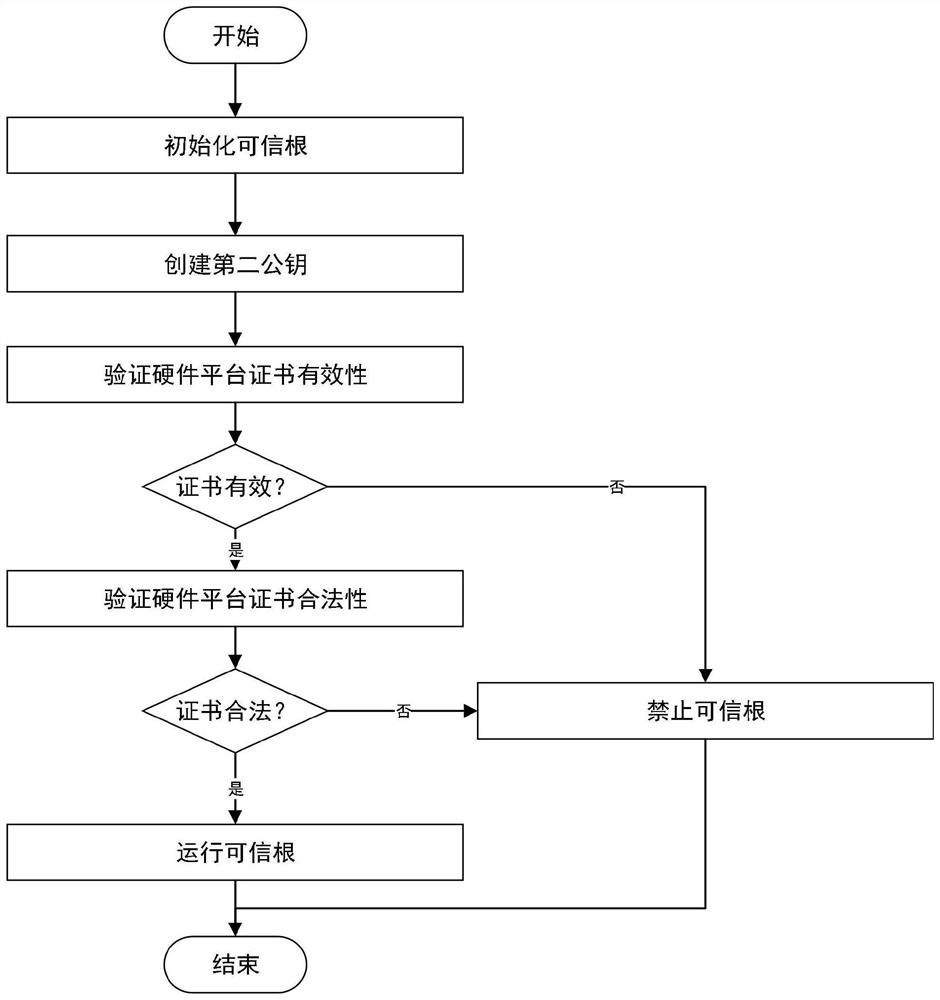
ActiveCN110543768AProtection securityGuaranteed to be legalKey distribution for secure communicationUser identity/authority verificationBIOSComputer security
The embodiments of the invention disclose a method and a system for controlling a trusted root in a BIOS, the method comprises certificate initialization and certificate verification, the certificateinitialization comprises the steps of generating a hardware platform certificate of the trusted root and importing the hardware platform certificate into the trusted root, and the hardware platform certificate comprises an information main body and a signature value. The method comprises the following steps: initializing a trusted root by a BIOS; and verifying that the information main body in thehardware platform certificate is valid, indicating that the hardware platform certificate is matched with the trusted root, ensuring that the hardware platform certificate is valid, verifying that the signature in the hardware platform certificate is valid, indicating that the hardware platform certificate is matched with the manufacturer public key solidified in the BIOS, and ensuring that the hardware platform certificate is legal. According to the invention, the BIOS verifies the identity of the trusted root after initializing the trusted root, and judges whether to provide a trusted rootfunction for a subsequent running program or not according to the verification result so as to protect the security of upper-layer application data of a computer.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
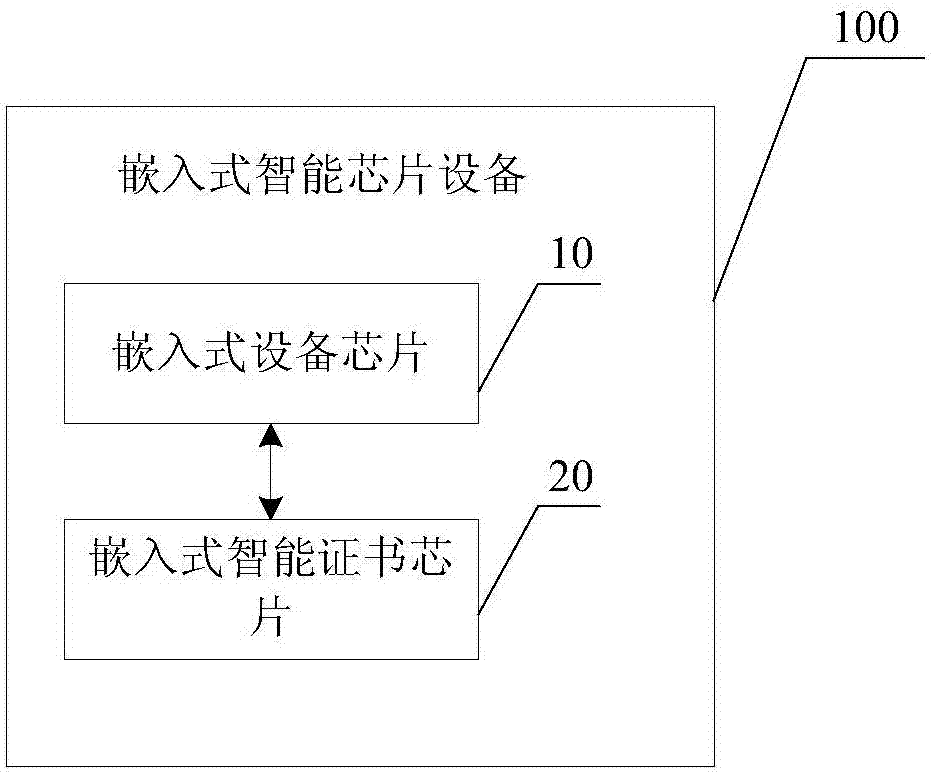
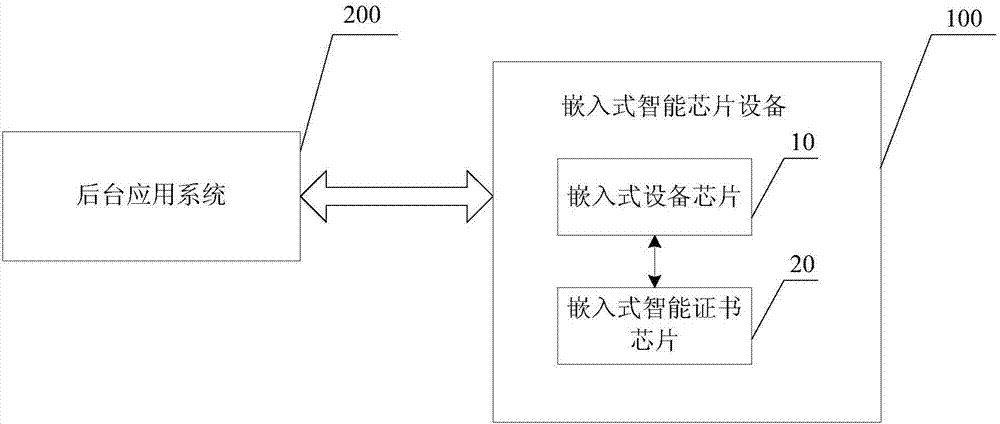
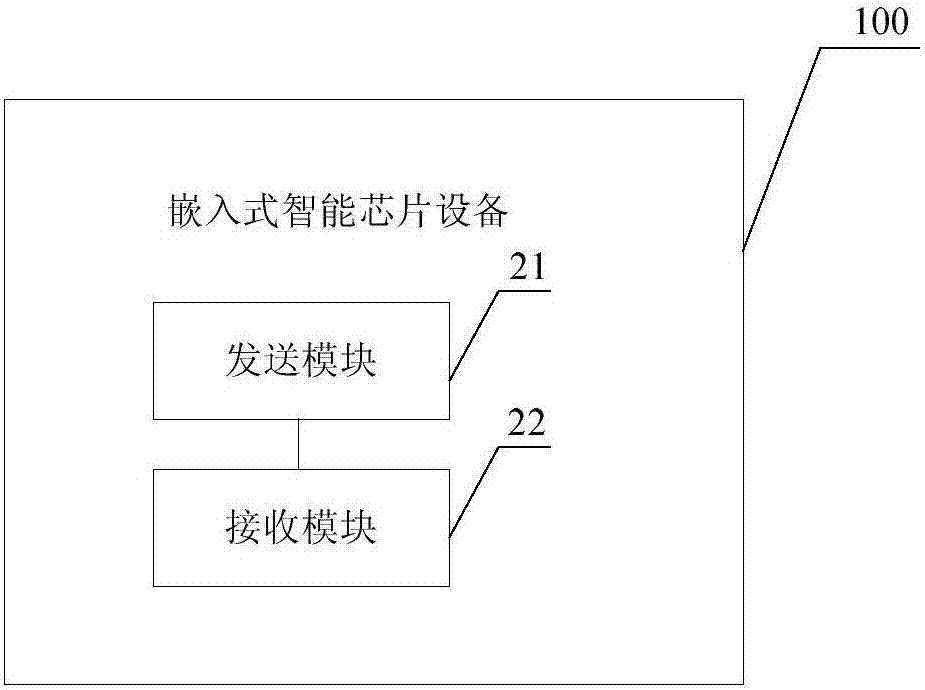
Embedded intelligent chip device and background application system
ActiveCN106855924AEasy to identifyPrevent intrusionUser identity/authority verificationDigital data authenticationPermission systemTransfer procedure
The invention discloses an embedded intelligent chip device and a background application system. The embedded intelligent chip device comprises an embedded device chip and an embedded intelligent certificate chip, wherein the embedded device chip is used for sending a control instruction to the embedded intelligent certificate chip, the embedded intelligent certificate chip is used for receiving the control instruction sent by the embedded device chip and conducting identity authentication on the embedded intelligent chip device and the background application system through the control instruction and encrypting and sending updated configuration data to the background application system through the embedded device chip after identity authentication is qualified, and meanwhile the embedded device chip begins to execute the functions of the embedded intelligent chip device after the authentication succeeds. By adopting the embedded intelligent chip device and the background application system, viruses or illegal permission systems are effectively prevented from invading the embedded intelligent chip device, and the data safety in the transmission process is ensured.
Owner:南方城墙信息安全科技有限公司
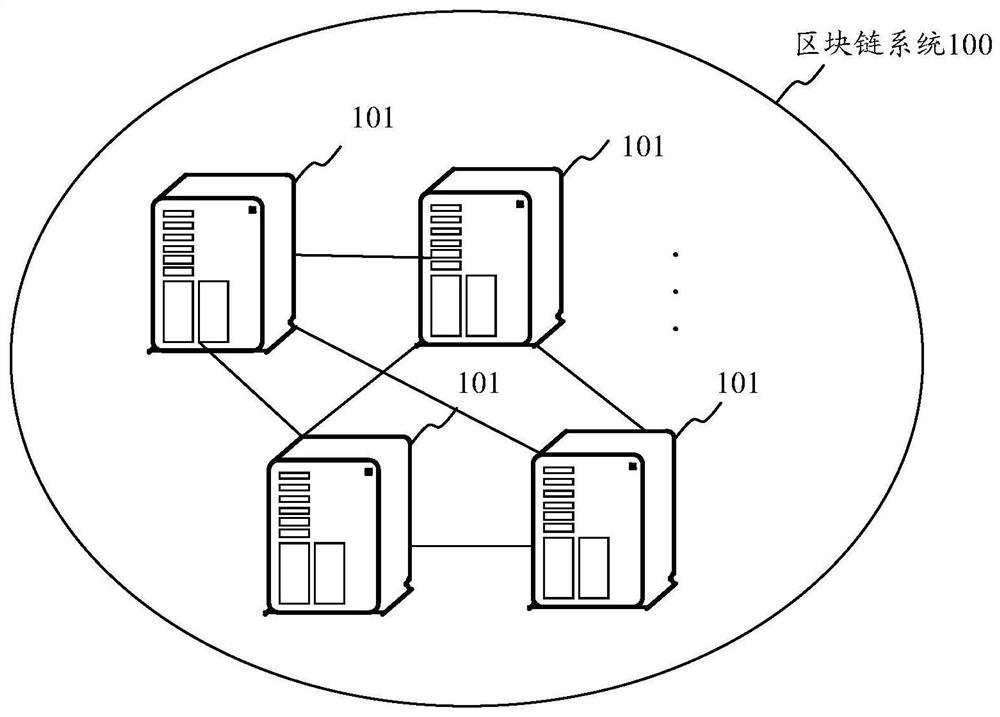
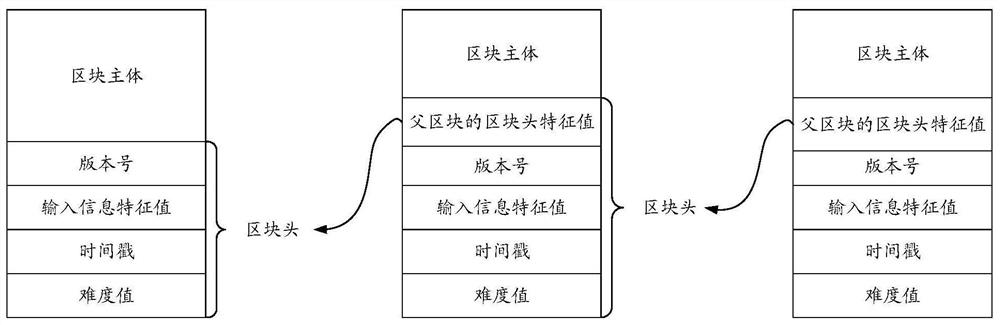
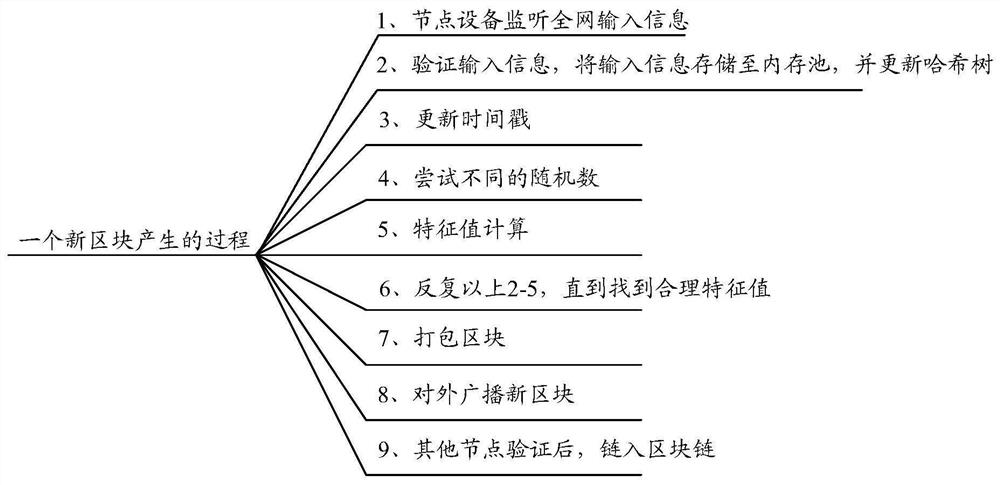
Edge intelligent calculation method based on block chain and edge intelligent system
ActiveCN112333187ATraceableTamper proofUser identity/authority verificationDatabase distribution/replicationSmart systemIntelligent computing
The invention discloses an edge intelligent calculation method based on a block chain and an edge intelligent system, belongs to edge intelligence, and aims to solve the technical problem of how to apply a block chain technology to edge intelligent calculation to ensure that data is correct and complete and ensure the legality of transmitted data. The calculation method comprises the following steps: configuring connection between a gateway and a main node and connection between the main node and a working node through the gateway; the main node generating a key pair, adding the block information to a locally stored block chain of the main node and publishing the block information to the outside, and each working node adding the verified block information to the locally stored block chain;and the main node sending the instruction data and the specified private key to a related working node, and the working node calling an artificial intelligence module to analyze the equipment acquisition data to obtain an analysis report and returning the analysis report to the gateway through the working node. The system comprises at least one gateway and at least one edge device, and the edge device comprises a main node and at least one working node.
Owner:QILU UNIV OF TECH
Security management and control method and system for logistics information, and computer storage medium
InactiveCN108717611AGuaranteed transmission efficiencyPrevent leakageMemory record carrier reading problemsCo-operative working arrangementsLogistics managementTimestamp
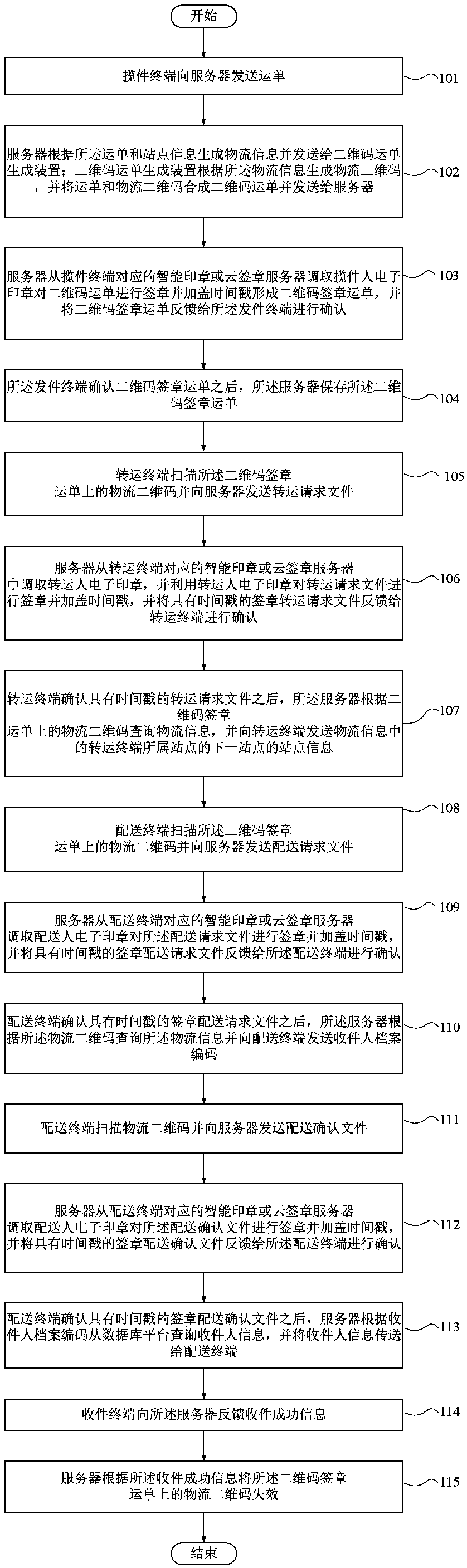
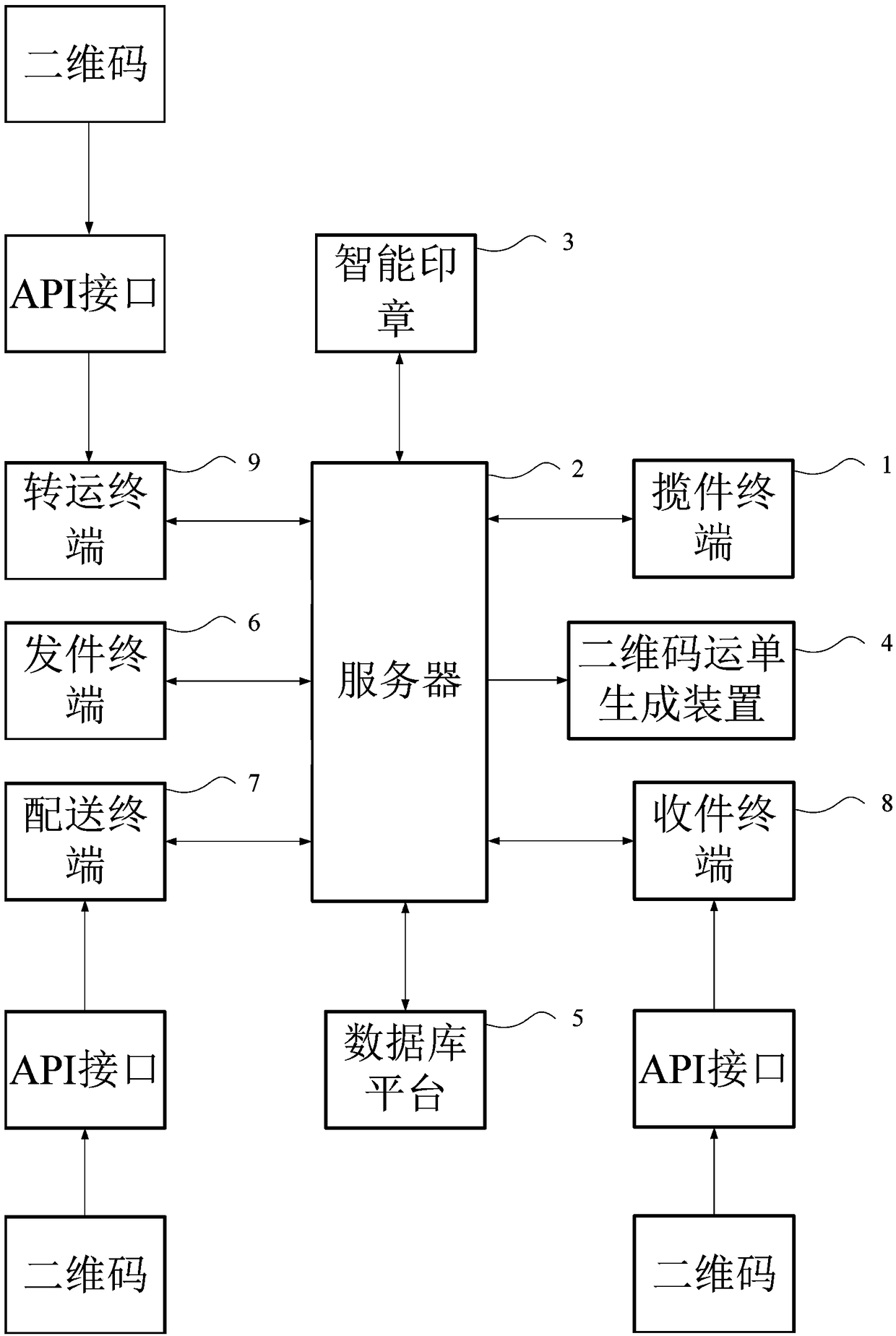
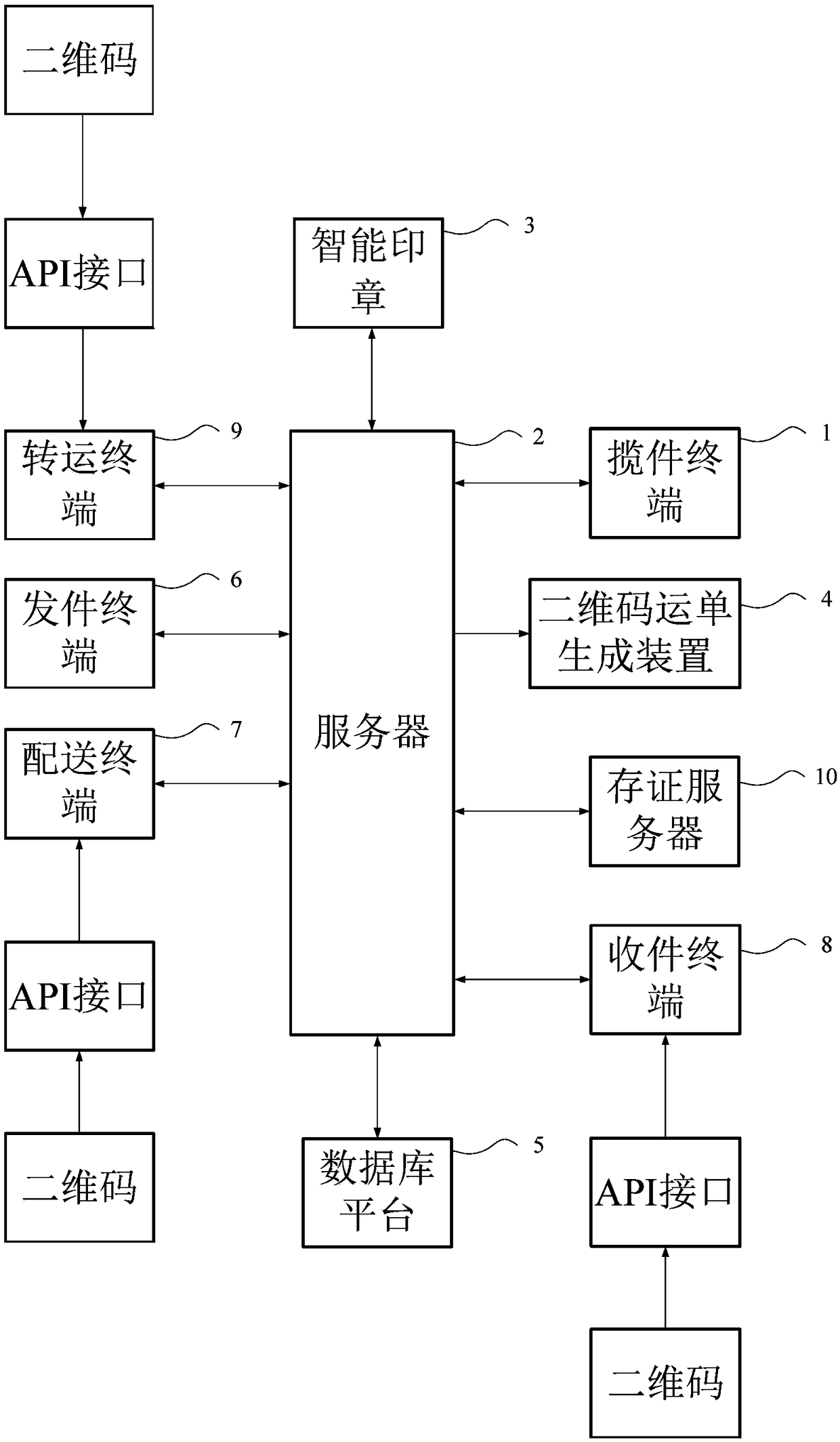
The invention provides a security management and control method and system for logistics information, and a computer storage medium. The method comprises the following steps that: an express deliverycollection terminal sends a waybill to a server; the server generates the logistics information according to the waybill and site information, and a two-dimensional code waybill generation device generates a logistics two-dimensional code according to the logistics information, and combines the waybill and the logistics two-dimensional code into a two-dimensional code waybill; the two-dimensionalcode waybill is signed and stamped with a timestamp to form a two-dimensional code signature waybill; a transfer terminal scans the logistics two-dimensional code on the two-dimensional code signaturewaybill to transfer articles; a distribution terminal scans the logistics two-dimensional code on the two-dimensional code signature waybill to distribute articles; after distribution is finished, anexpress delivery receiving terminal feeds back express delivery picking-up success information to the server; and the server causes the logistics two-dimensional code to fail. By use of the method, while the personal information of an addressee and an addresser is not leaked, logistics transfer efficiency is improved.
Owner:胡金钱
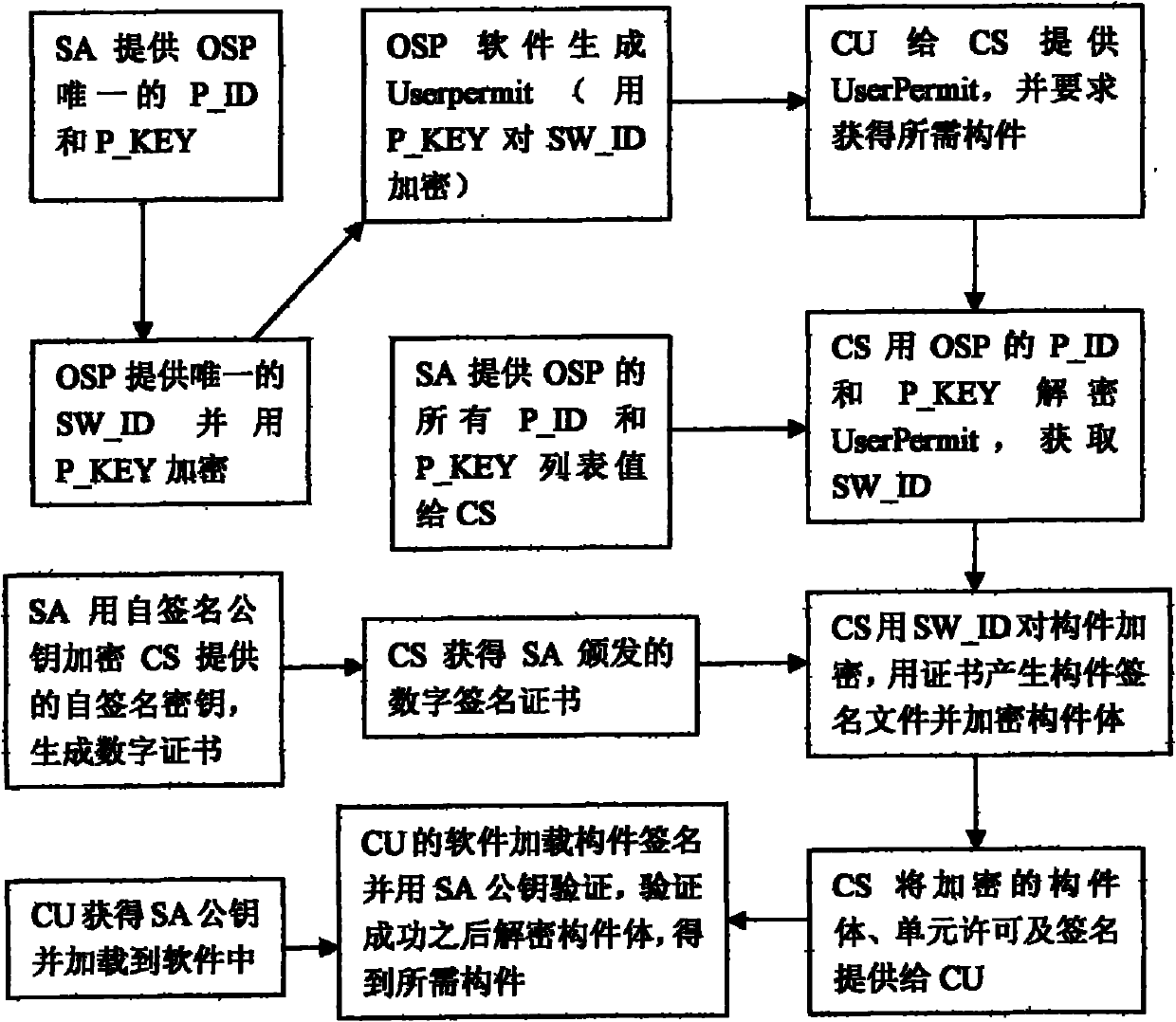
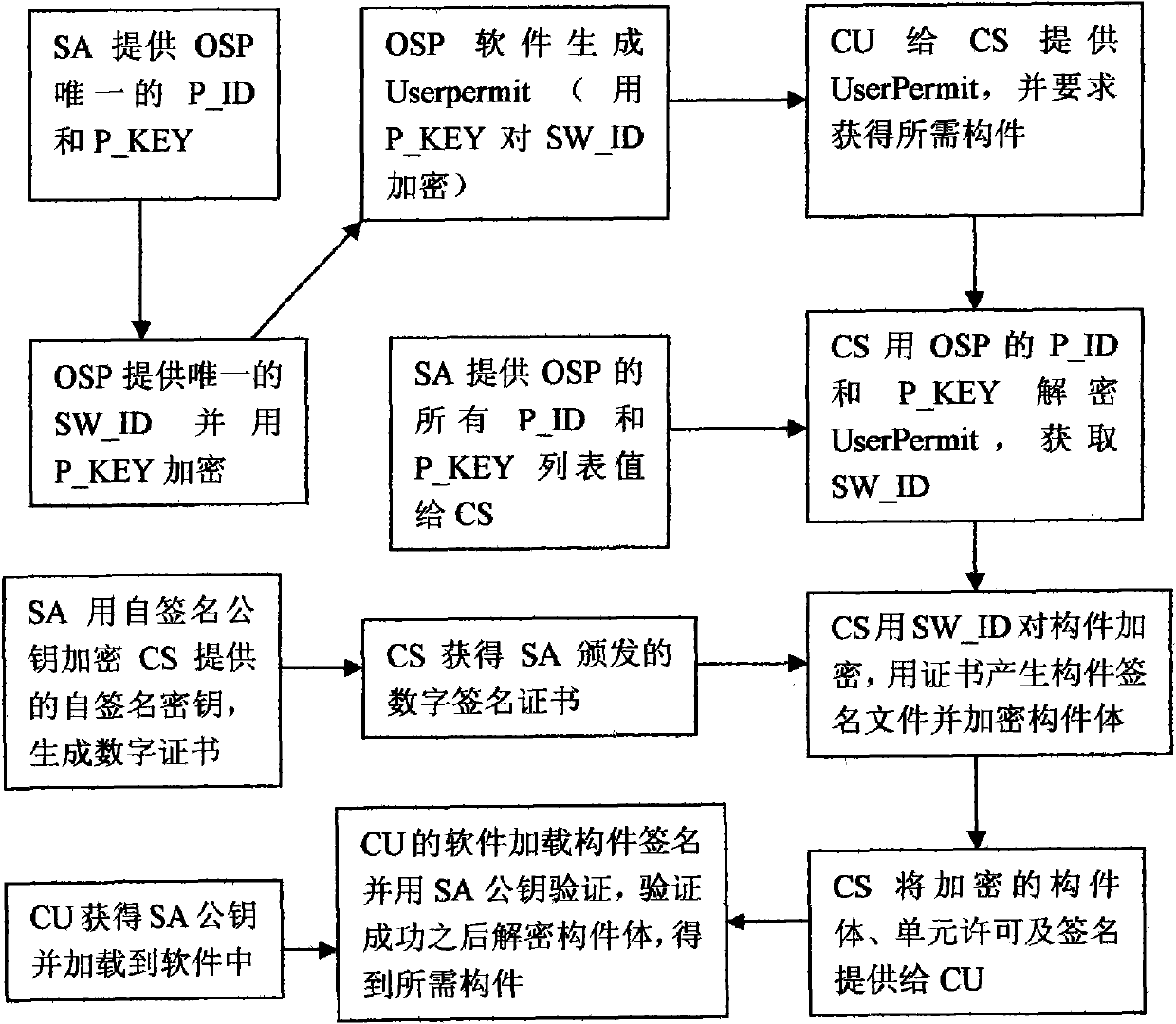
Method for issuing, using and protecting controllable component
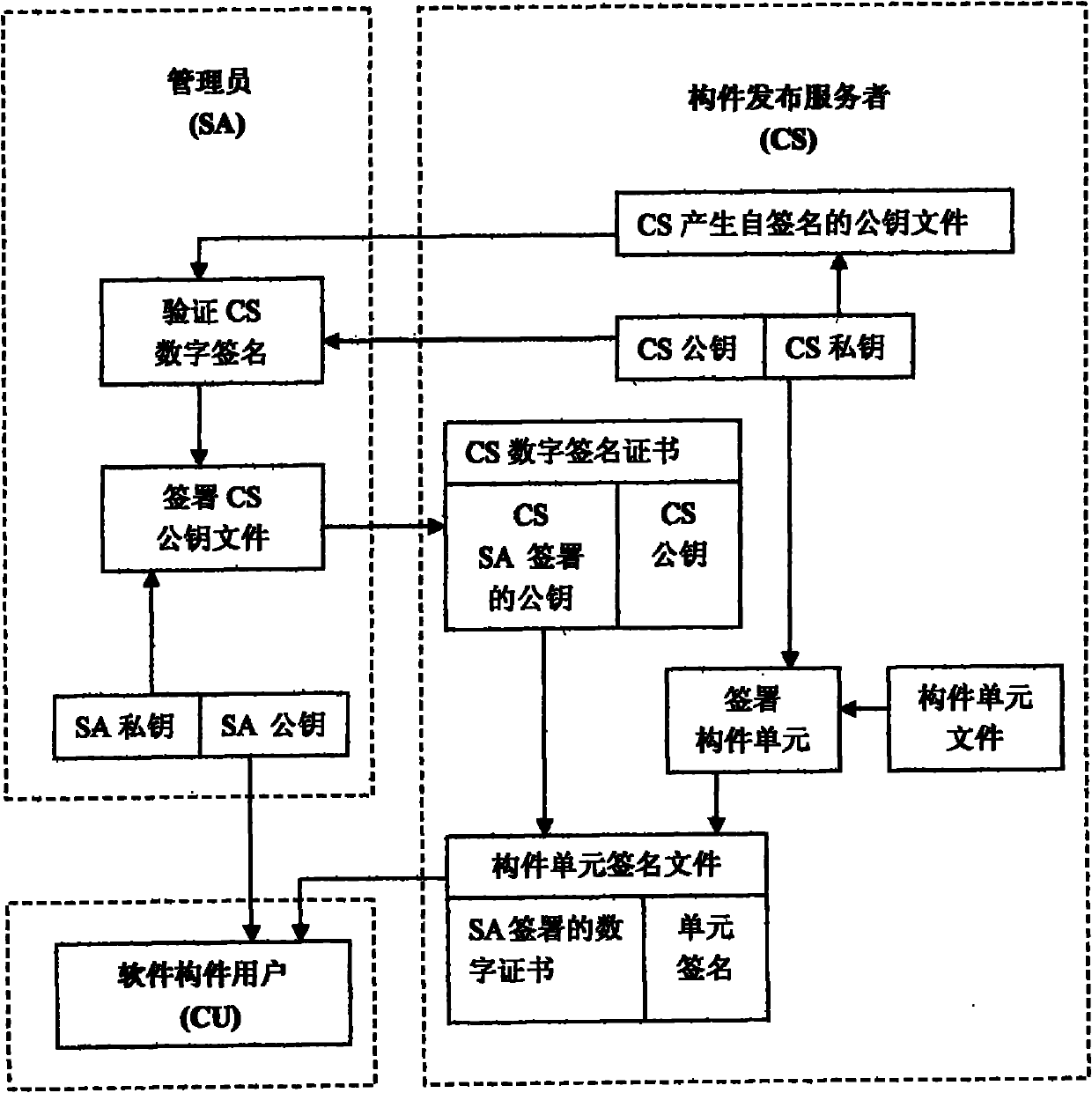
InactiveCN101908109AEasy to useGuaranteed legal originProgram/content distribution protectionSoftware engineeringEncryption
The invention relates to a method for issuing, using and protecting a controllable component. The method comprises the following steps that: five roles need to be established; all the roles are mutually authorized; the component is effectively controlled in the process of issuing and using the component in the ways of digital certificates, signatures and encryption; only software produced by a recognized original software producer OSP can use a legal component, and only a recognized component issuing server CS can issue the legal component to a software component user CU; and the software component user CU can apply for the legal software component only by acquiring the software from a legal original software producer OSP. The method has the advantages that the software producer can be qualified for producing the legal software by the scheme so as to ensure that the produced software can use the legal software component, and the component produced by the software component producer can be finally used by the user after being submitted to a component issuer and signed to ensure legal sources of the component.
Owner:NO 709 RES INST OF CHINA SHIPBUILDING IND CORP
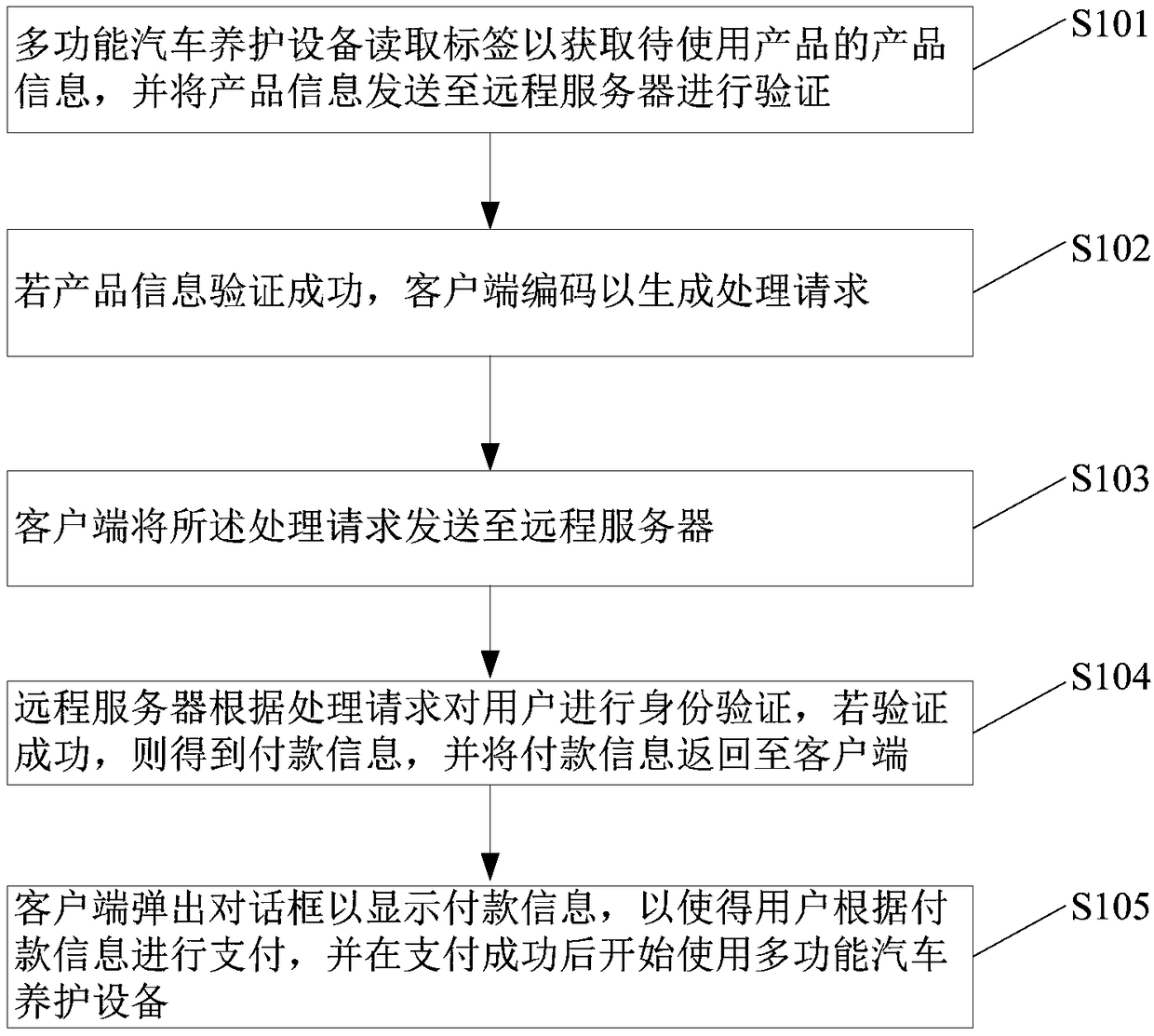
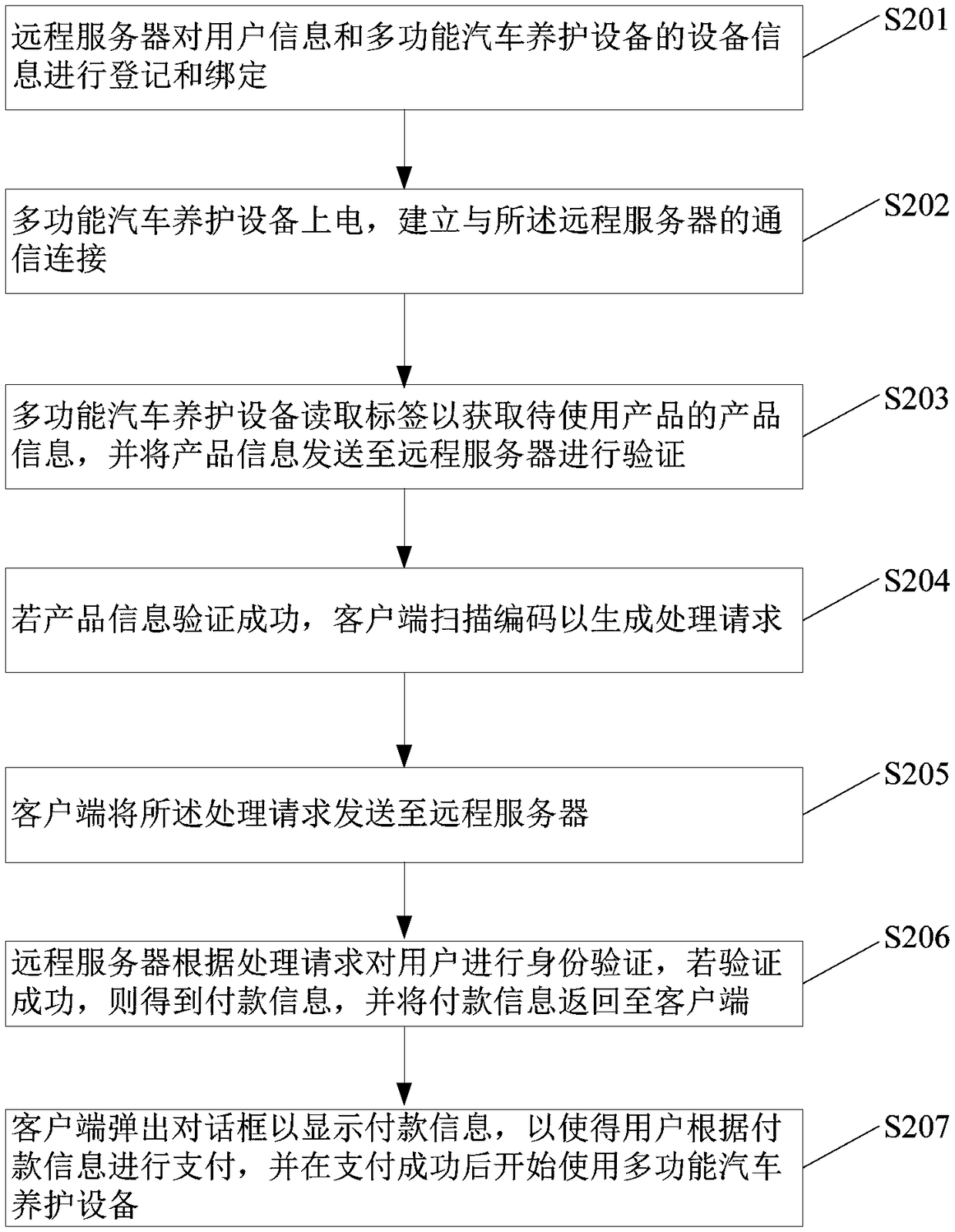
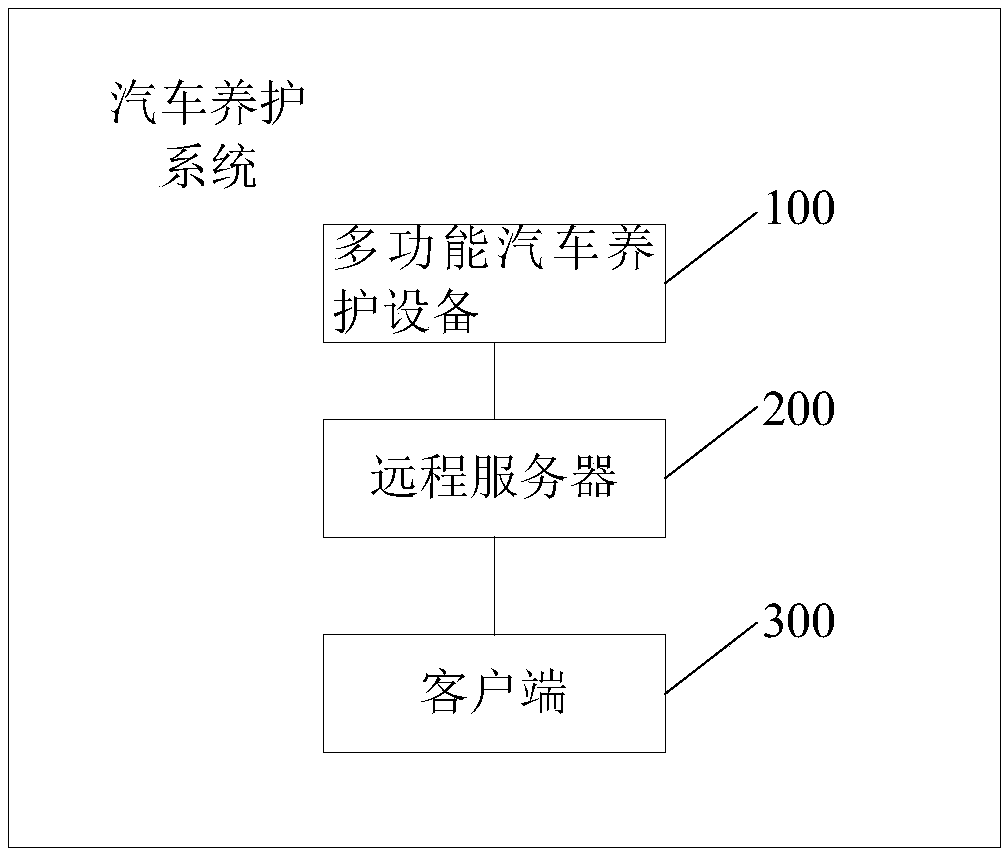
Automobile maintenance method and system based on internet of things
PendingCN109285013ARealize authenticity verificationVerification GuaranteeCo-operative working arrangementsPayment architectureClient-sideUser authentication
The embodiment of the invention discloses an automobile maintenance method and a system thereof based on the internet of things. The method comprises the following steps: a multi-functional automobilemaintenance equipment reads a label to obtain product information of a product to be used, and sends the product information to a remote server for verification; if the product information verification is successful, the client scans the encoding to generate a processing request; the client sends the processing request to the remote server; the remote server authenticates the user according to the processing request, and if the authentication is successful, the remote server obtains payment information and returns the payment information to the client; the client pops up a dialog box to display payment information so that the user can make payment based on the payment information and start using the multi-function vehicle maintenance equipment after the payment is successful. The embodiment of the invention effectively combines the authentication of the product to be used, the authentication of the user and the online payment, and provides convenience for the user on the premise of ensuring the authenticity of the product to be used and the legitimacy of the user identity.
Owner:重庆伯儒科技有限公司
Scheduling device and method for cooperative operation of video monitor equipment cluster
InactiveCN109640055AReal-time monitoring of instruction queue statusAvoiding Instruction Buffer Overflow ProblemsElectric signal transmission systemsSignal allocationVideo monitoringClosed loop
The invention discloses a device and method for cooperative operation of a video monitor equipment cluster. The method raises an instruction elimination mechanism, and an instruction queue state is monitored in real time, so that instruction cache overflow is prevented; the method raises a determining rule for instruction integrity and instruction group integrity, solving a problem of lack of integrity of the instruction and instruction group due to communication abnormality, guaranteeing instruction legal and correct, and making the system more stable and reliable; the method raises instruction classification and instruction prioritizing manner, solving a conflict problem of executing of multiple problems, ensuring that the instruction is executed correctly, and preventing abnormal equipment actions; the method adopts a Petri network, limited state machine and other technological models, so as to constrain and guide coordinate scheduling of multiple signal instructions; and the methodraises an instruction closed loop mechanism, schedules the monitor equipment accurately, further, reduces abnormal jitter amid frequency instructions, and prolongs service life of equipment effectively.
Owner:SHANDONG SYNTHESIS ELECTRONICS TECH
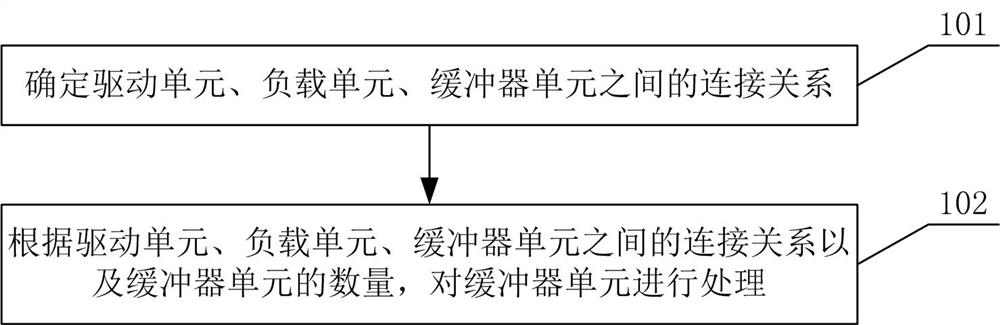
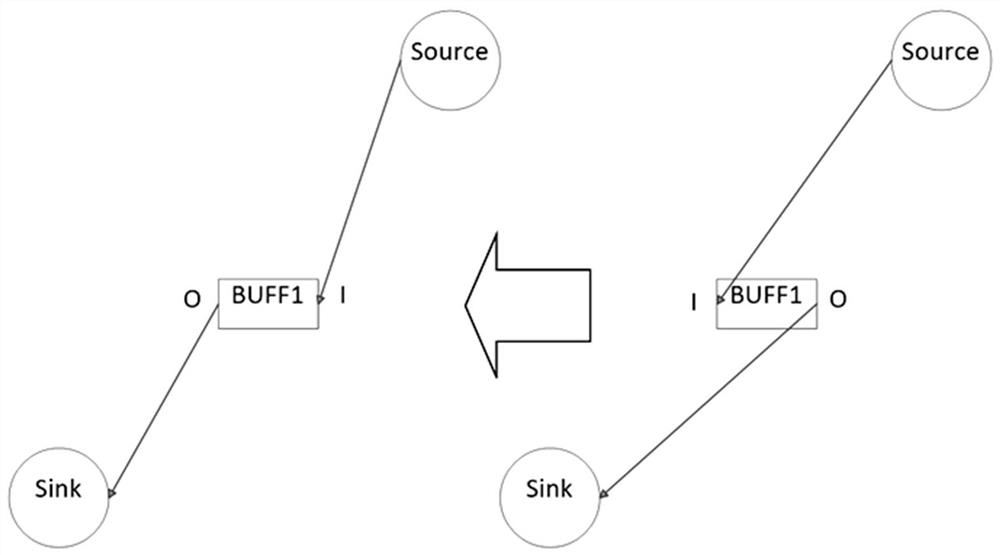
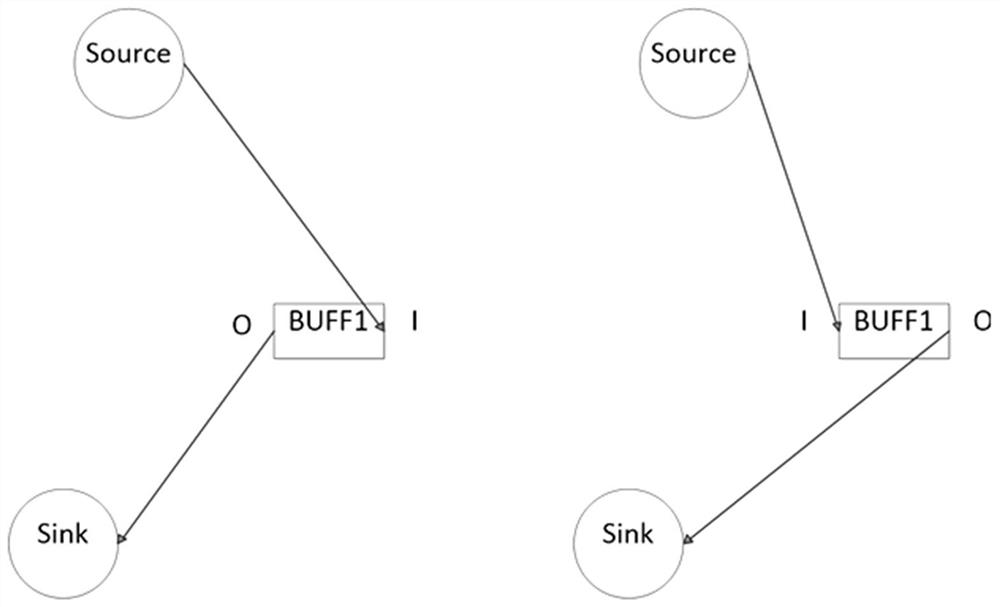
Method for reducing wire length, electronic equipment and computer readable storage medium
ActiveCN112417808AShorten the line lengthShorten the lengthComputer aided designSpecial data processing applicationsComputer hardwareEngineering
The invention discloses a method for reducing the wire length, which is characterized by comprising the steps of determining a connection relationship among a driving unit, a load unit and a buffer unit; and overturning and adjusting the buffer unit according to the position of the buffer unit. According to the method for reducing the wire length, when the buffer unit is inserted, the purposes ofreducing the wiring length and reducing the wiring difficulty are achieved by turning over the buffer unit and changing the positions of the unit pins according to the positions of the units in the chip and the actual condition of physical wiring, so that the influence of a timing sequence ECO optimization scheme on local wiring is smaller, and the accuracy and the consistency are better.
Owner:北京华大九天科技股份有限公司
A secure remote control system and method for industrial equipment
ActiveCN108390851BHighlight substantiveSignificant progressKey distribution for secure communicationUser identity/authority verificationAccess networkControl system
The invention provides a security remote control system and method for industrial equipment. The system comprises industrial equipment, a control terminal and a cloud platform, wherein a security module I is arranged in the industrial equipment, a security module II is inserted into or arranged in the control terminal, the cloud platform comprises a security access gateway, a management system, aCA certificate management system and a forwarding server, and a security module III is arranged in the security access gateway. In remote control, the industrial equipment and the security access gateway perform bidirectional identity authentication and key negotiation and create a first session key; the control terminal and the security access gateway perform bidirectional identity authenticationand key negotiation and create a second session key; the control terminal and the industrial equipment perform bidirectional identity authentication and key negotiation through the forwarding serverand then create a third session key; and the control terminal performs security remote control on the industrial equipment by using the third session key through the forwarding server.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
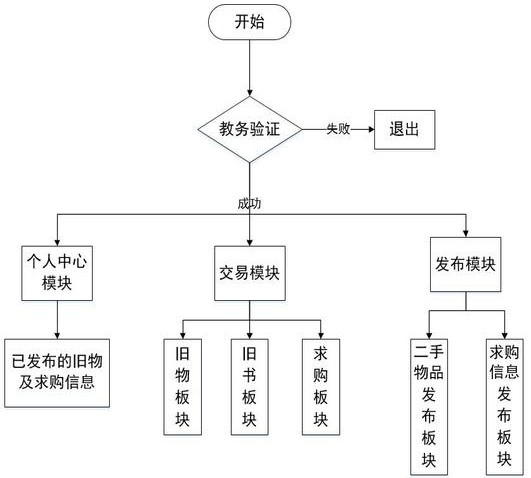
Campus second-hand article transaction management system based on WeChat applet
PendingCN112330425AGuaranteed to be legalGuaranteed legalityBuying/selling/leasing transactionsProgram loading/initiatingTransaction management systemUser Privilege
The invention provides a campus second-hand article transaction management system based on a WeChat applet. The campus second-hand article transaction management system comprises an applet end and a background management end; the applet end is provided with a transaction module for the user to browse and inquire the second-hand articles and the purchase information, a publishing module for the user to publish the second-hand articles and the purchase information, and a personal center module for the user to check the second-hand articles and the purchase information published by the user; thebackground management module is configured to be an auditing module for an administrator to auditing second-hand articles and purchase information, an announcement management module for the administrator to issue and delete announcements, and a member management module for the administrator to check user information and edit user permission. According to the campus second-hand article transactionmanagement system based on the WeChat applet, it can be ensured that the identities of buyers and sellers are legal, the problem that the logistics transportation cost is high is solved, through the campus second-hand article transaction management system, a user can conveniently browse and publish second-hand articles and purchase information at a mobile phone terminal, and convenience is improved.
Owner:WEIHAI OCEAN VOCATIONAL COLLEGE
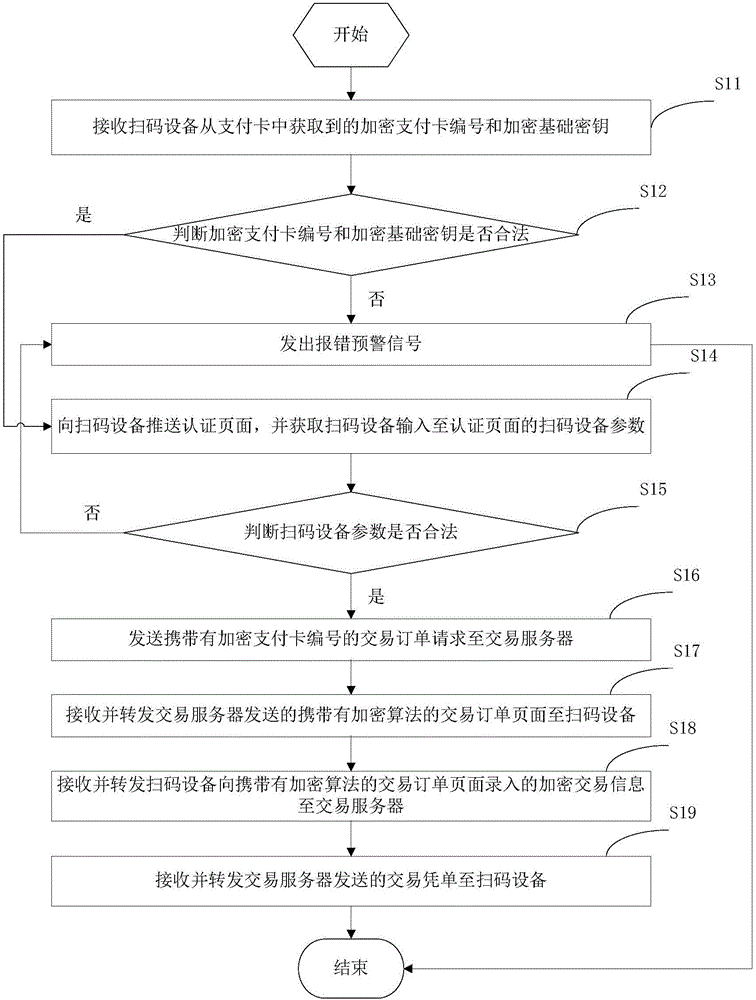
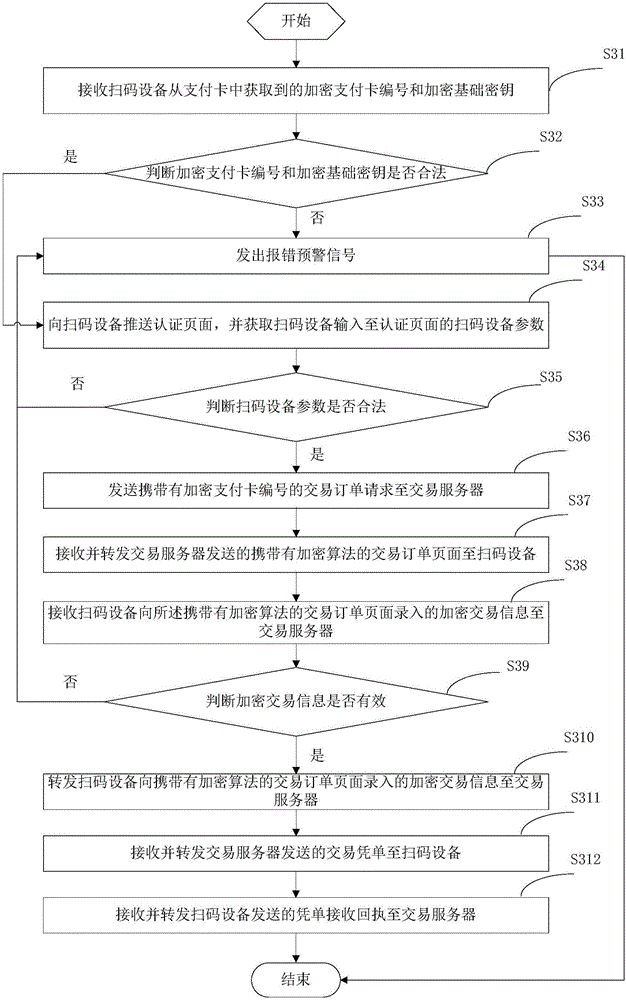
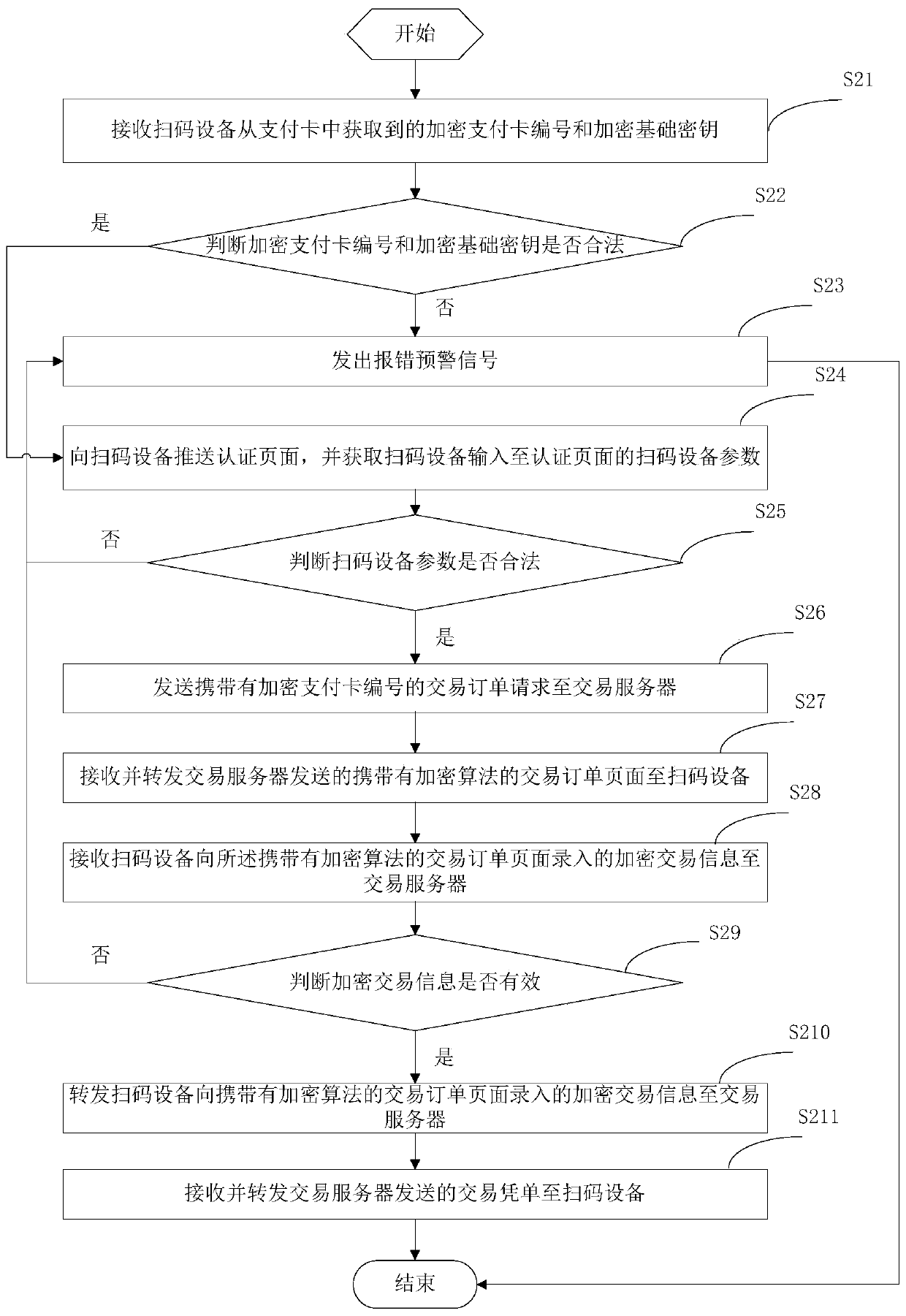
Payment method and payment device
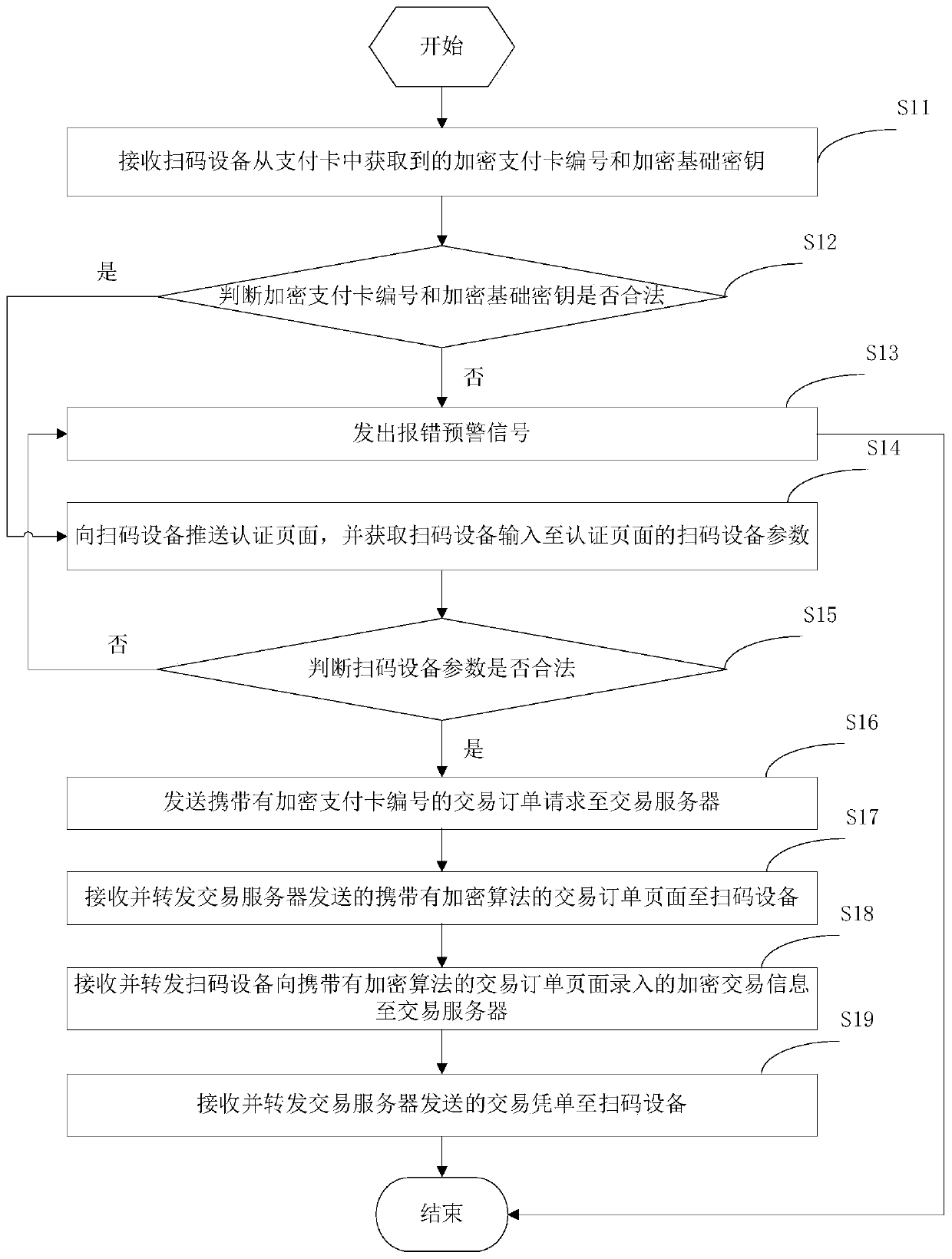
ActiveCN106251147APrevent interception and tamperingImprove securityPayment protocolsDevice parametersPayment card number
The invention provides a payment method and a payment device. The payment method comprises steps: an encrypted payment card number and an encrypted basic key acquired from the payment card by a code scanning device are received; whether the encrypted payment card number and the encrypted basic key are legal is judged; if not, an error early warning signal is given; if yes, an authentication page is pushed to the code scanning device, and code scanning device parameters inputted to the authentication page by the code scanning device are acquired; whether the code scanning device parameters are legal is judged; if not, an error early warning signal is given; if yes, a transaction order request carrying the encrypted payment card number is sent to a transaction server; a transaction order page carrying an encryption algorithm sent by the transaction server is received and forwarded to the code scanning device; encrypted transaction information inputted to the transaction order page carrying the encryption algorithm by the code scanning device is received and forwarded to the transaction server; and a transaction voucher sent by the transaction server is received and forwarded to the code scanning device. Thus, through the above mode, the payment process security is improved.
Owner:随行付支付有限公司
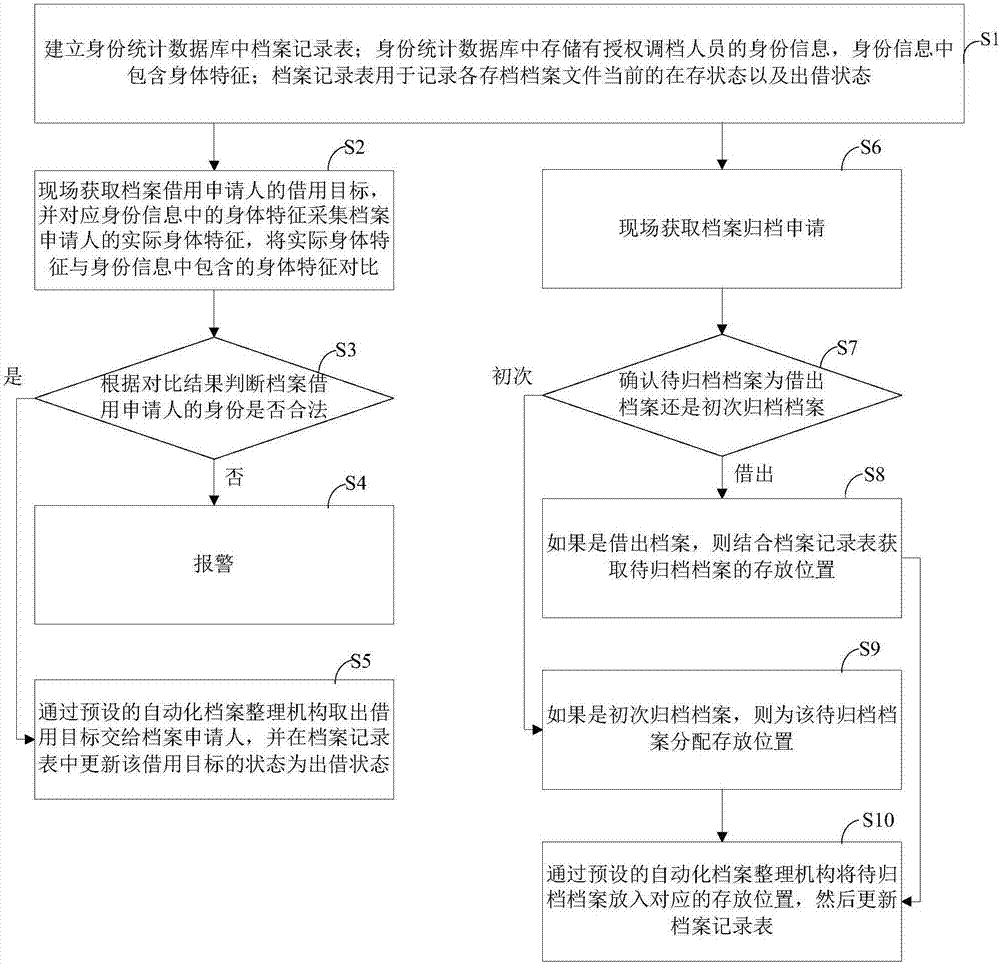
Archive immediate calling trace management method
InactiveCN107463650AImprove targetingAvoid direct contactDigital data protectionFile access structuresArchive file
Owner:合肥泓泉档案信息科技有限公司
Blockchain-based voting processing method and device
ActiveCN111369730BEnsure safetyGuaranteed reliabilityVoting apparatusDigital data protectionIdentity recognitionDatabase
The application provides a blockchain-based voting processing method, device, node equipment and storage medium, which belong to the technical field of blockchain. This technical solution adopts blockchain for decentralized and persistent storage of voting-related information about exiting services, and identifies voters through biometric features, which can ensure the security and reliability of voting data. At the same time, it can ensure that the identities of voting participants are legal, prevent others from impersonating others during the voting process, and ensure the credibility of voting results.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for realizing data tampering detection of nonvolatile memory by adopting hybrid encryption algorithm
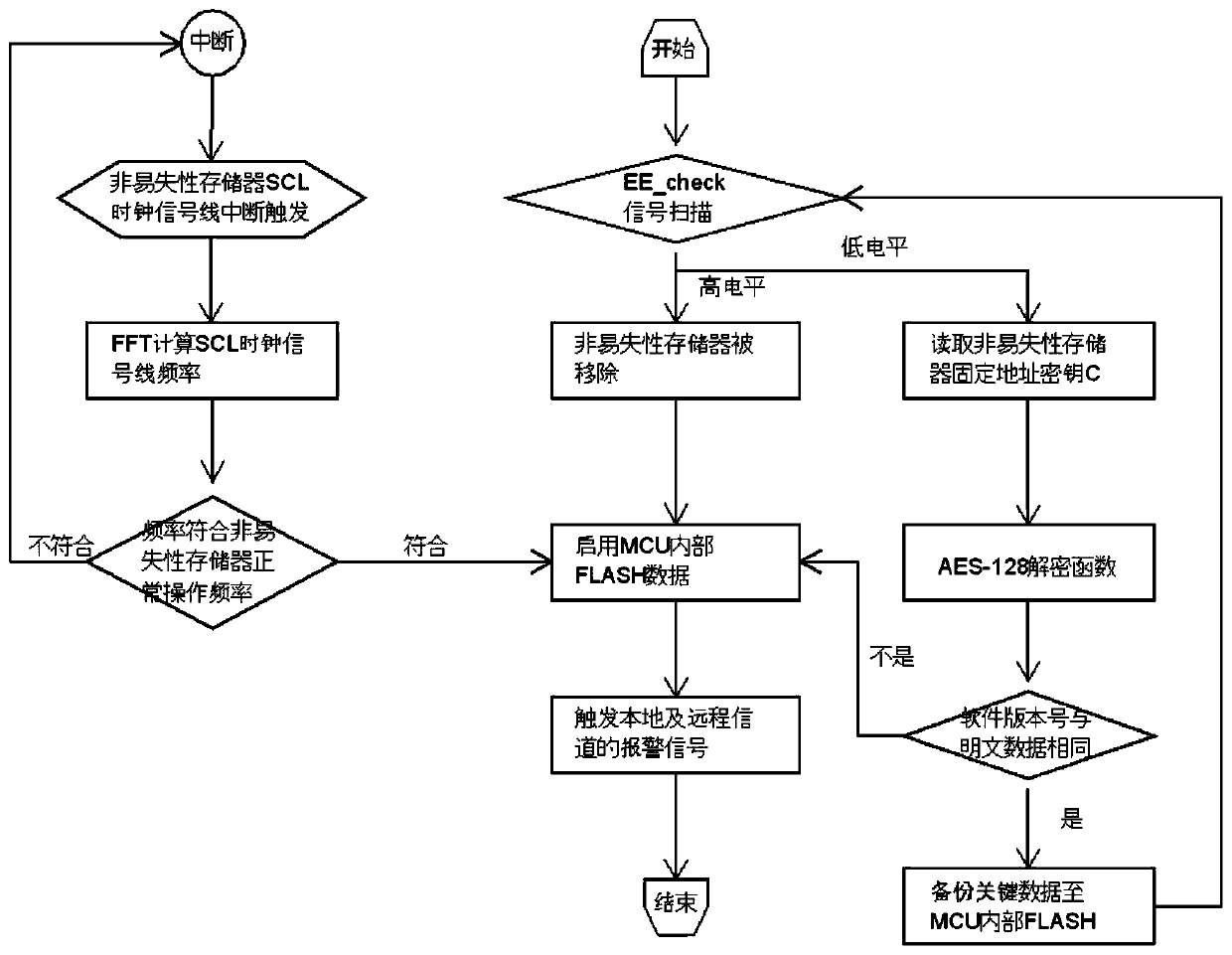
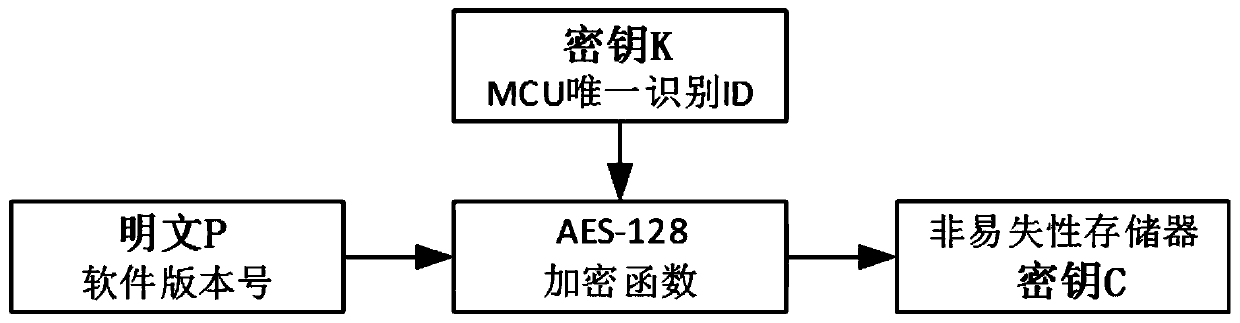
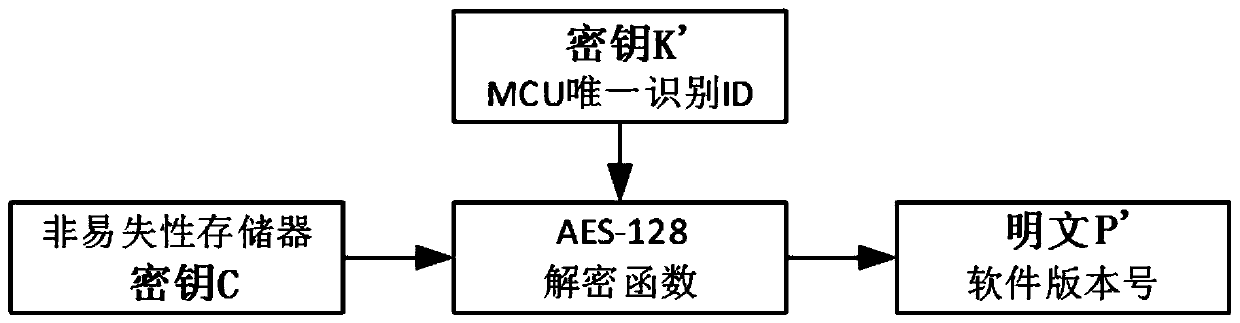
ActiveCN111339573AGuaranteed to be legalEnsure reliabilityDigital data protectionInternal/peripheral component protectionPlaintextAlgorithm
The invention provides a method for identifying data exception of a nonvolatile memory by adopting a hybrid encryption algorithm, which comprises the following steps that: S1, an MCU (MicroprogrammedControl Unit) performs dual backup on electric energy metering data regularly, adopts a unique identification ID (Identity) as an encryption factor K to perform encryption operation on a plaintext P to generate a secret key C, and stores the secret key C; s2, the MCU scans and detects an I / O port of a nonvolatile memory in the electronic electric energy meter at regular time, and judges whether hardware of the nonvolatile memory is abnormal or not; s3, the MCU reads the secret key C of the fixed storage address of the nonvolatile memory at regular time, carries out secret key comparison and judges whether the data is tampered abnormally or not; and S4, the MCU triggers and monitors a clock signal of the nonvolatile memory, and judges an abnormal condition. By adopting the identification information generated by the encryption algorithm based on the hardware ID and the embedded software fault identification algorithm, the method ensures that the data in the electronic electric energy meter is legal and is not lost, and ensures the reliability and safety of data storage.
Owner:JIANGSU LINYANG ENERGY CO LTD
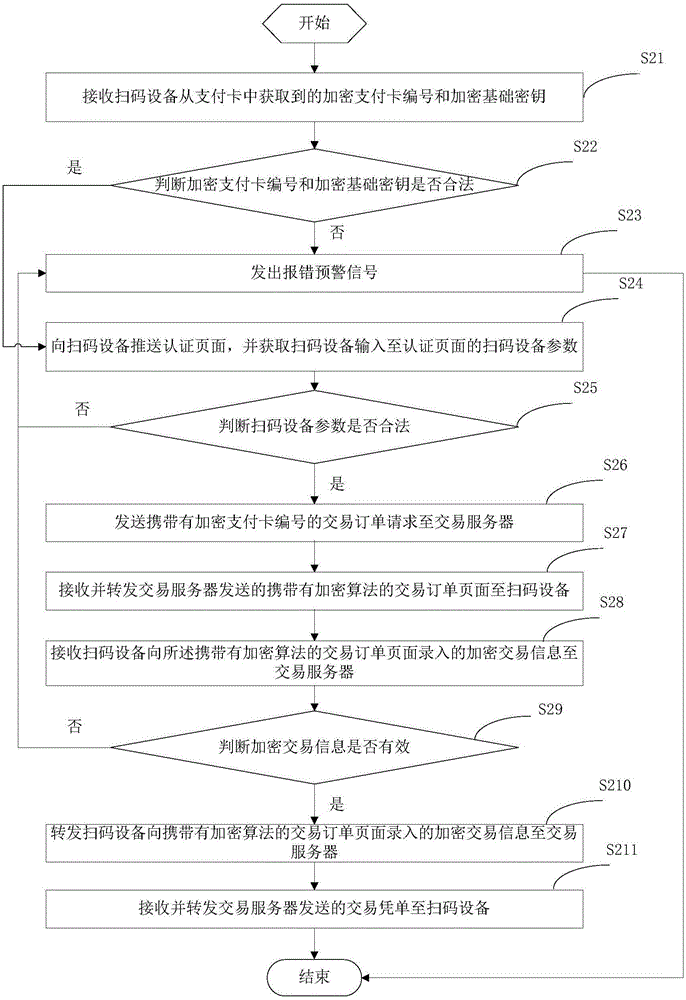
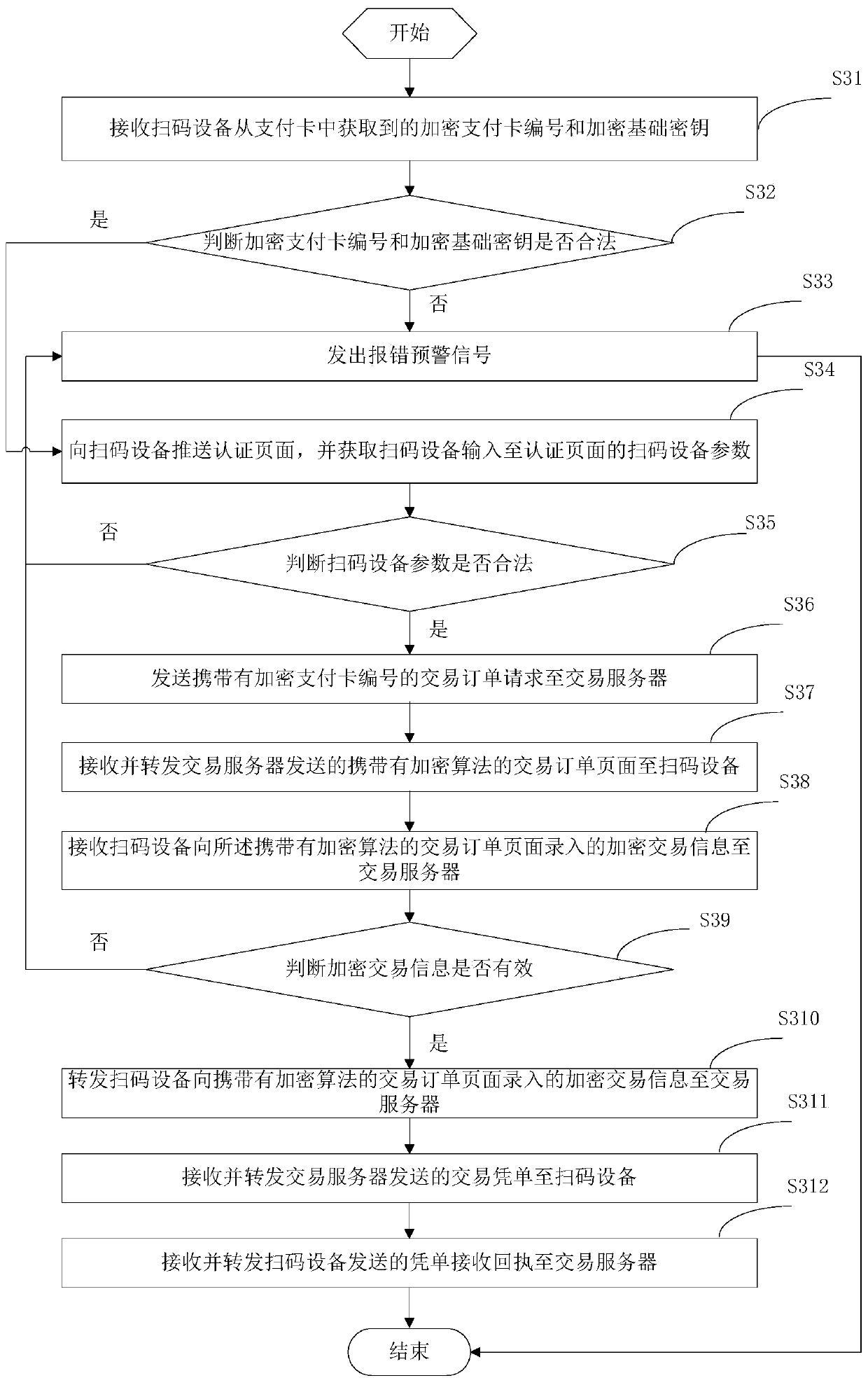
A payment method and device
ActiveCN106251147BGuaranteed to be legalRealize information interactionPayment protocolsPaymentComputer hardware
The invention provides a payment method and a payment device. The payment method comprises steps: an encrypted payment card number and an encrypted basic key acquired from the payment card by a code scanning device are received; whether the encrypted payment card number and the encrypted basic key are legal is judged; if not, an error early warning signal is given; if yes, an authentication page is pushed to the code scanning device, and code scanning device parameters inputted to the authentication page by the code scanning device are acquired; whether the code scanning device parameters are legal is judged; if not, an error early warning signal is given; if yes, a transaction order request carrying the encrypted payment card number is sent to a transaction server; a transaction order page carrying an encryption algorithm sent by the transaction server is received and forwarded to the code scanning device; encrypted transaction information inputted to the transaction order page carrying the encryption algorithm by the code scanning device is received and forwarded to the transaction server; and a transaction voucher sent by the transaction server is received and forwarded to the code scanning device. Thus, through the above mode, the payment process security is improved.
Owner:随行付支付有限公司
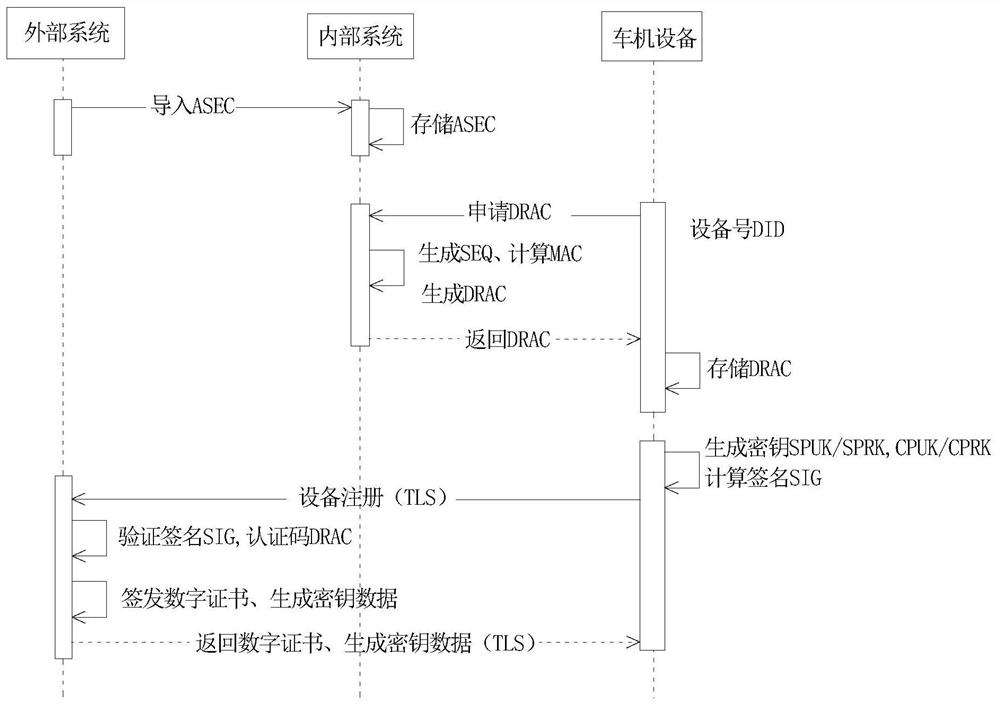
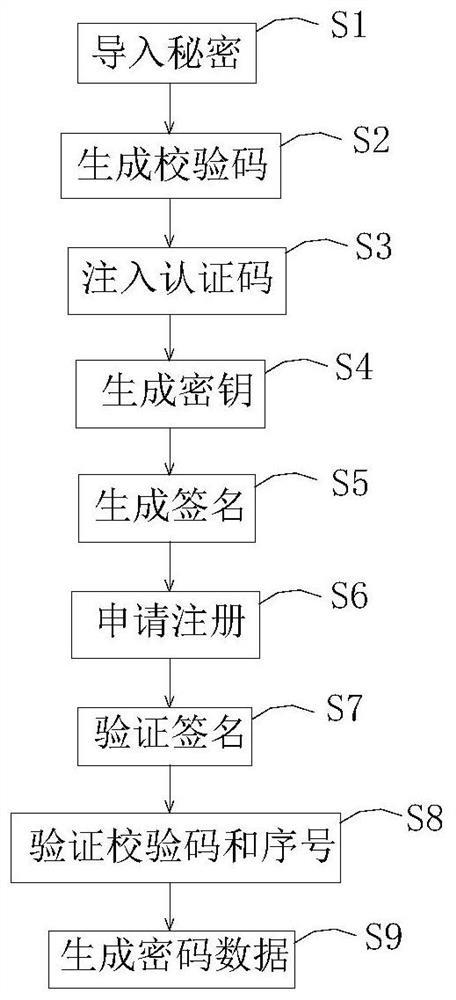
On-line injection method for initial password data of vehicle equipment
ActiveCN111859366ASolve data security issuesSolve data synchronizationDigital data protectionDigital data authenticationPasswordCheck digit
The invention discloses an on-line injection method for initial password data of vehicle equipment, and the method comprises the following steps: S1, enabling an external system to randomly generate asecret ASEC for an internal system, and importing the secret ASEC into the internal system when the internal system is used for the first time; s2, generating a serial number SEQ by the internal system according to a vehicle equipment number DID, and calculating by adopting an abstract algorithm to obtain a check code MAC; s3, enabling the internal system to splice the vehicle equipment number DID, the serial number SEQ and the check code MAC to serve as an equipment registration authentication code DRAC, and import the authentication code DRAC into the vehicle equipment; s4, enabling the vehicle equipment to generate a signature key pair and an encryption key pair; s5, enabling the vehicle equipment to perform signature calculation through the signature private key SPRK, the encryption public key CPUK and the authentication code DRAC to obtain a signature value SIG; and S6, enabling the vehicle equipment to send a registration application to an external system, wherein the registration application comprises an authentication code DRAC, a signature public key SPUK, an encryption public key CPUK and a signature value SIG. According to the invention, the data security and reliability of the vehicle-mounted equipment are ensured.
Owner:HUIZHOU DESAY SV AUTOMOTIVE
A method and system for controlling root of trust in bios
ActiveCN110543768BProtection securityGuaranteed to be legalKey distribution for secure communicationUser identity/authority verificationBIOSReliability engineering
The embodiment of the present invention discloses a method and system for controlling a trusted root in BIOS, including certificate initialization and certificate verification, certificate initialization includes generating a trusted root hardware platform certificate, importing the hardware platform certificate into the trusted root, and hardware platform The certificate includes the information subject and signature value; after the BIOS initializes the trusted root, it verifies that the information subject in the hardware platform certificate is valid, indicating that the hardware platform certificate matches the trusted root, ensures that the hardware platform certificate is valid, and verifies that the signature in the hardware platform certificate is valid , indicating that the hardware platform certificate matches the manufacturer's public key fixed in the BIOS, ensuring that the hardware platform certificate is legal. In the present invention, after the trusted root is initialized, the BIOS verifies the identity of the trusted root, and judges whether to provide the trusted root function for subsequent running programs according to the verification result, so as to protect the safety of computer upper layer application data.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
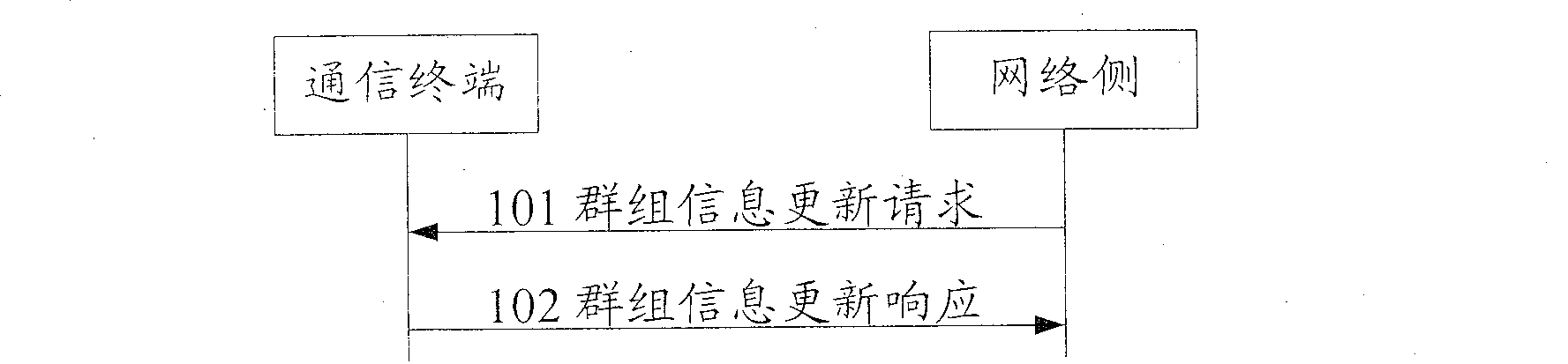
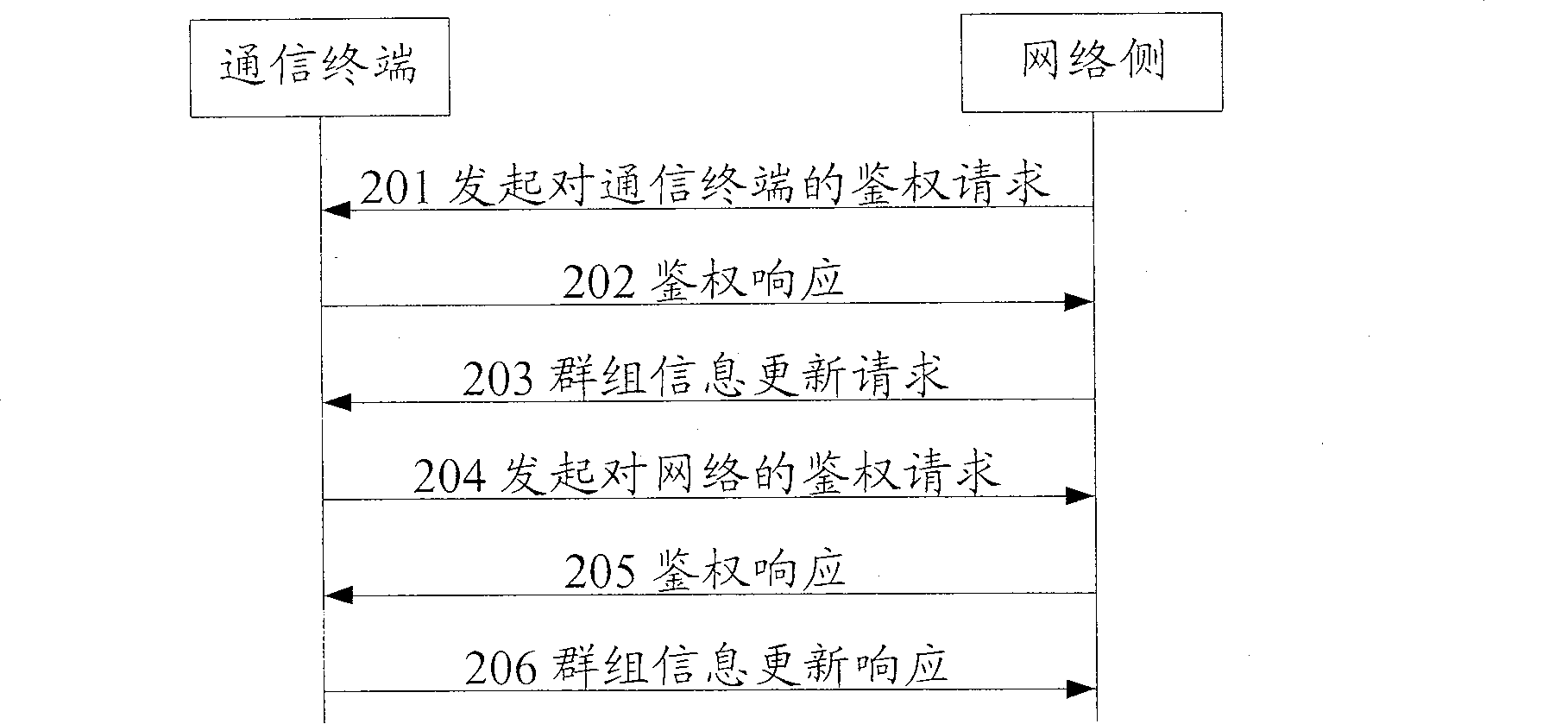
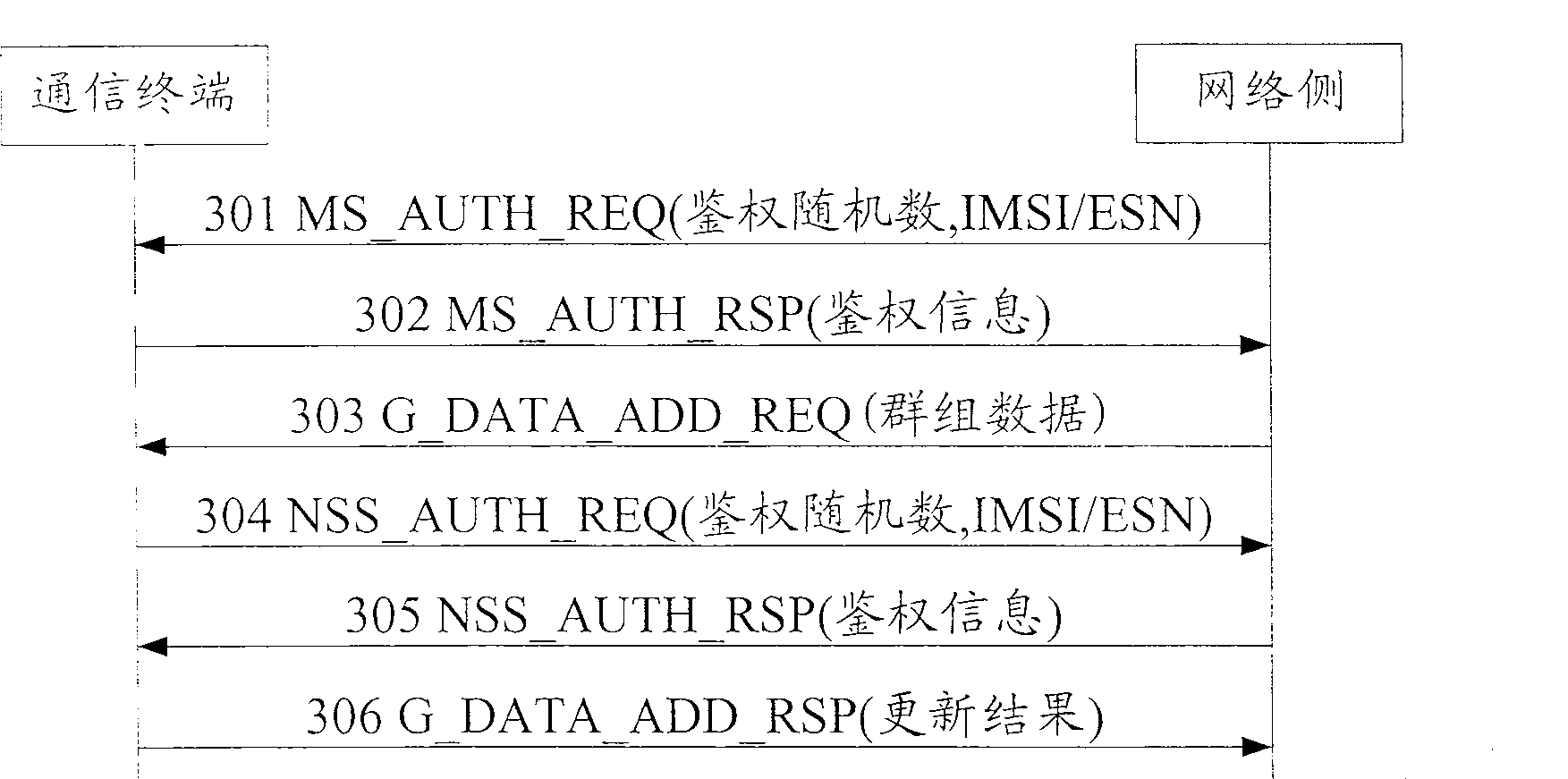
A method for dynamically updating group information in cluster service
InactiveCN100484329CGuaranteed to be legalUser identity/authority verificationNetwork topologiesComputer hardware
Owner:HUAWEI TECH CO LTD
System, method, device and installation for filtering programs
InactiveCN101729853BGuaranteed to be legalKeep healthySelective content distributionFiltrationNetwork connection
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
A security communication system and method for in-vehicle network
ActiveCN110943957BGuaranteed to be legalEnsure safetyKey distribution for secure communicationNetwork connectionEngineering
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
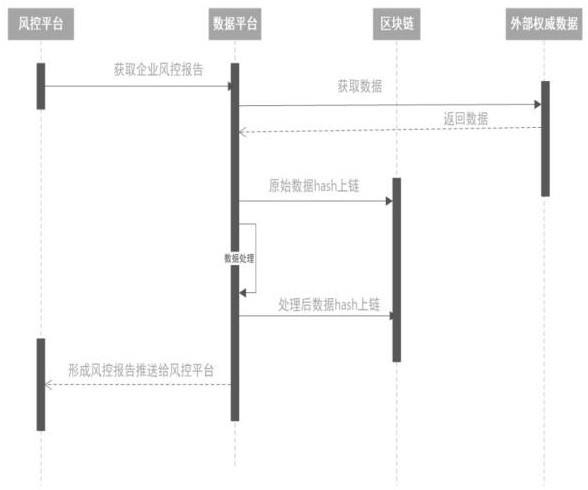
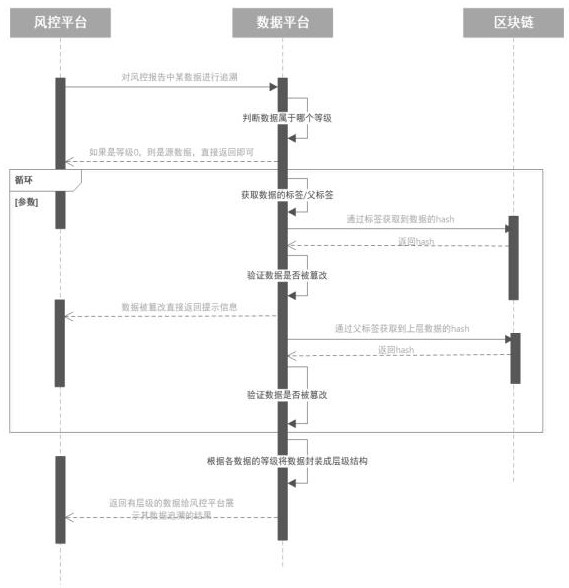
Method for tracing data source in risk control report based on block chain
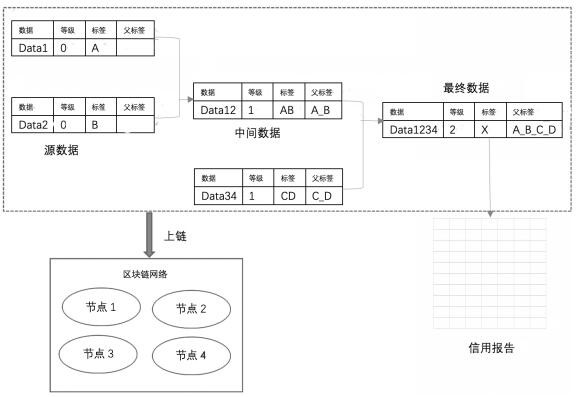
PendingCN113377852AGuaranteed sourcePrevent counterfeitingDatabase management systemsDigital data protectionBlockchainData processing
The invention discloses a method for tracing a data source in a risk control report based on a block chain, and the method specifically comprises the following steps: S1, obtaining original authoritative data to intermediate data, and then obtaining data in the finally obtained risk control report; S2, enabling the risk control report to need to process various data, obtaining the data from the source and directly chained, enabling the data processing flow in each subsequent step to need to be chained, and then completely storing the whole circulation information of the data in a block chain in a chain structure; and S3, signing the data, identifying the source of the data, and facilitating the process of tracing the data by using the risk control report in the later period. According to the invention, data tampering is avoided.
Owner:HUCAIS PRINTING
Network interaction reading system and method for user and content management
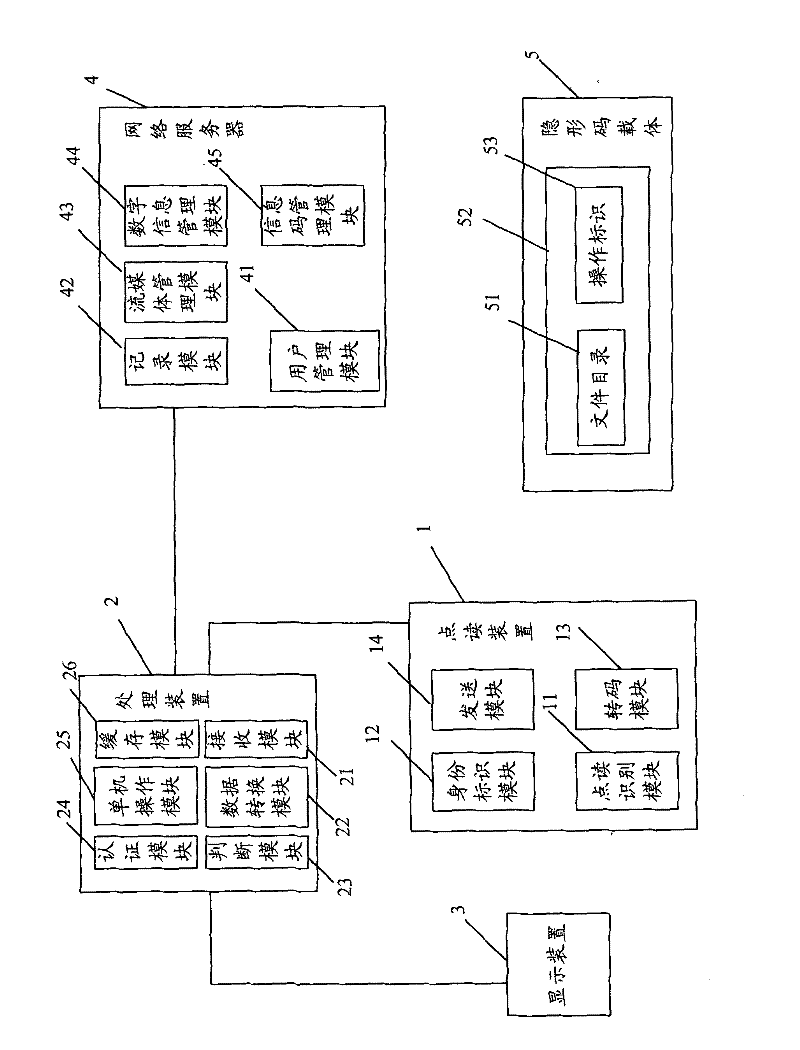
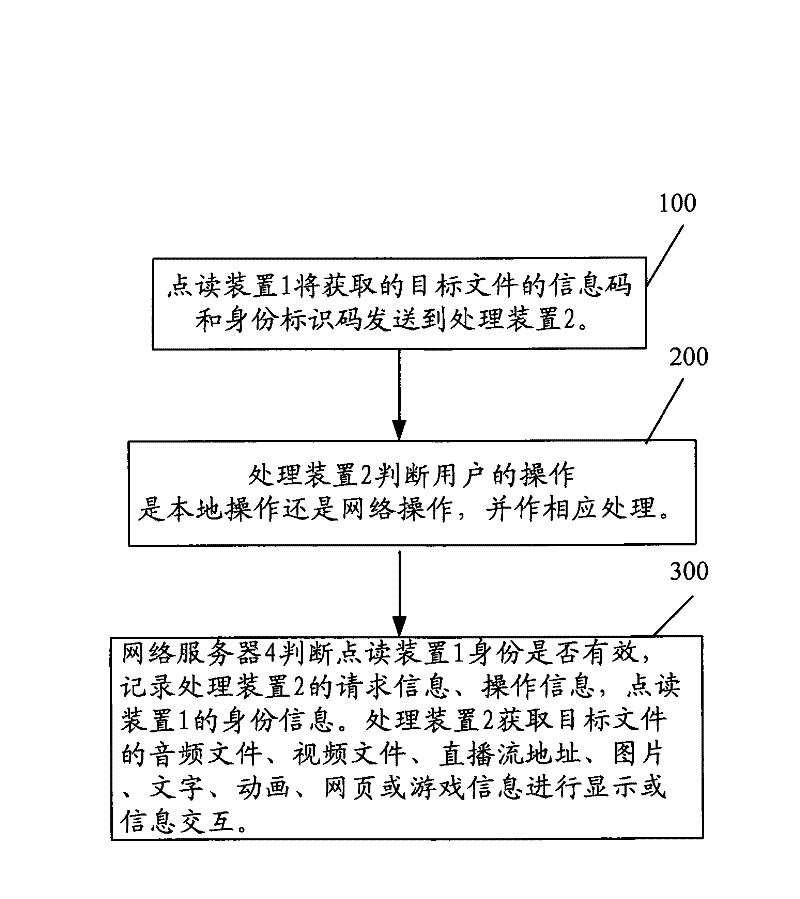
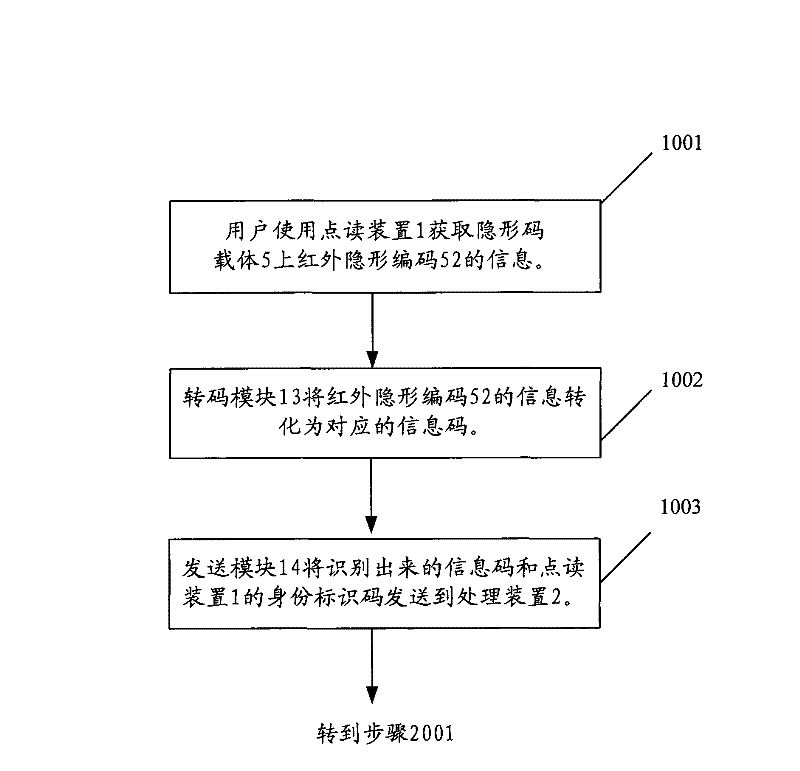
InactiveCN101715104BEasy to useGuaranteed to be legalUser identity/authority verificationSensing record carriersComputer moduleDisplay device
The invention claims a network interaction reading system and a method for user and content management. The system comprises a reading device, a processing device, a display device, a network server and a concealed code carrier; the reading device comprises an identity identification module for storing the identity identification code of the reading device; the processing device comprises an authentication module for sending the identification code of the reading device and the acquired information code to the network server; the network server comprises a user management module and an information code management module, and the user with administration authority manages the contents stored by a stream media management module and a digital information management module; and the network content and the operation mark are collected in the image-text form of concealed code carrier. The method comprises the following steps of: sending the information code and the identification code to the processing device by the reading device; judging the identity authority of the reading device, recording request information and operation information and returning the results to the processing device by the network server; and acquiring and displaying the network information returned by the server by the processing device.
Owner:中电天讯信息技术(北京)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com