Method for issuing, using and protecting controllable component
A component and software component technology, applied in the direction of program/content distribution protection, instrument, electronic digital data processing, etc., can solve problems such as potential safety hazards, inability to release and use control of components, and inability to protect users of software components, so as to ensure security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
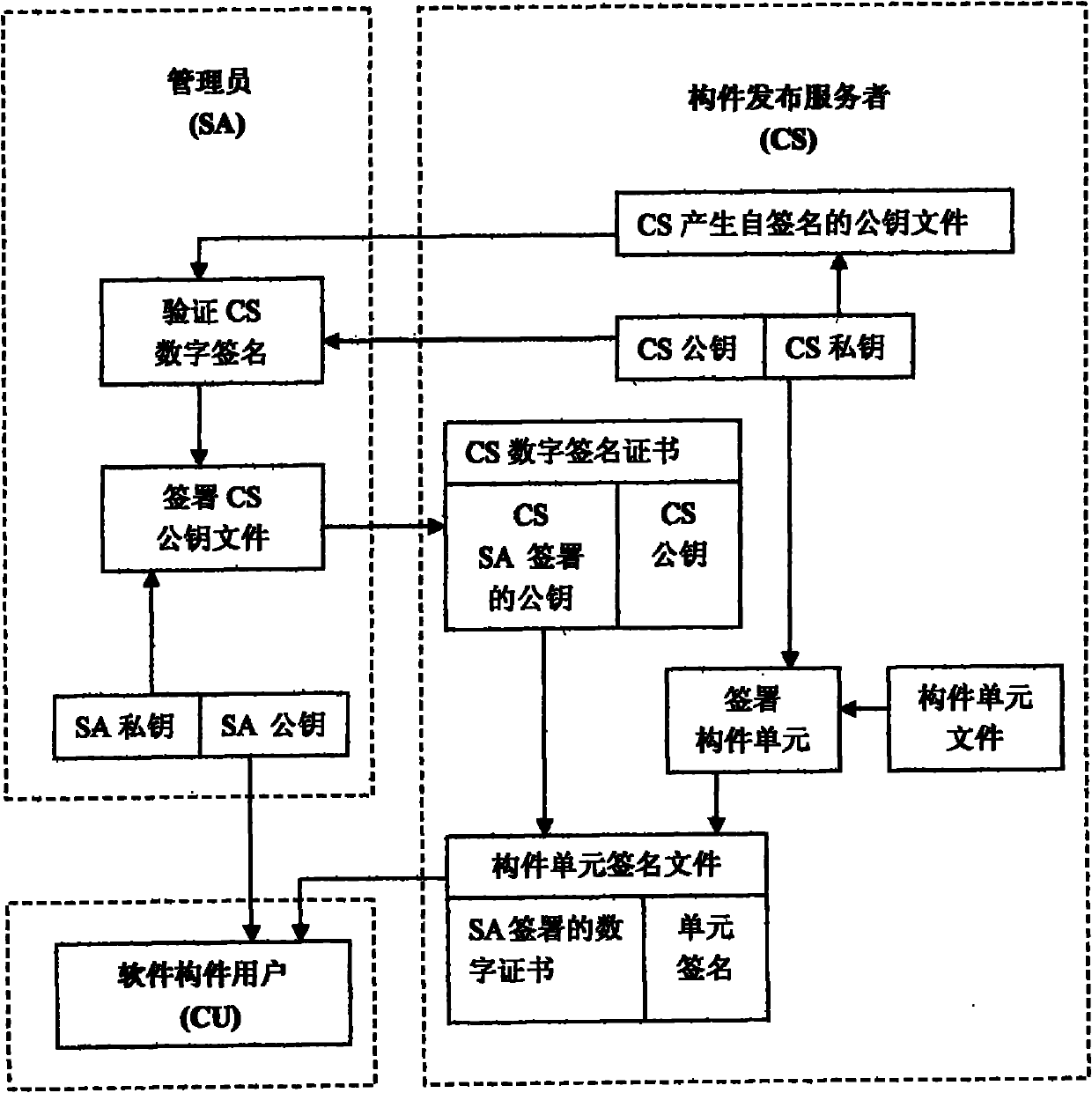
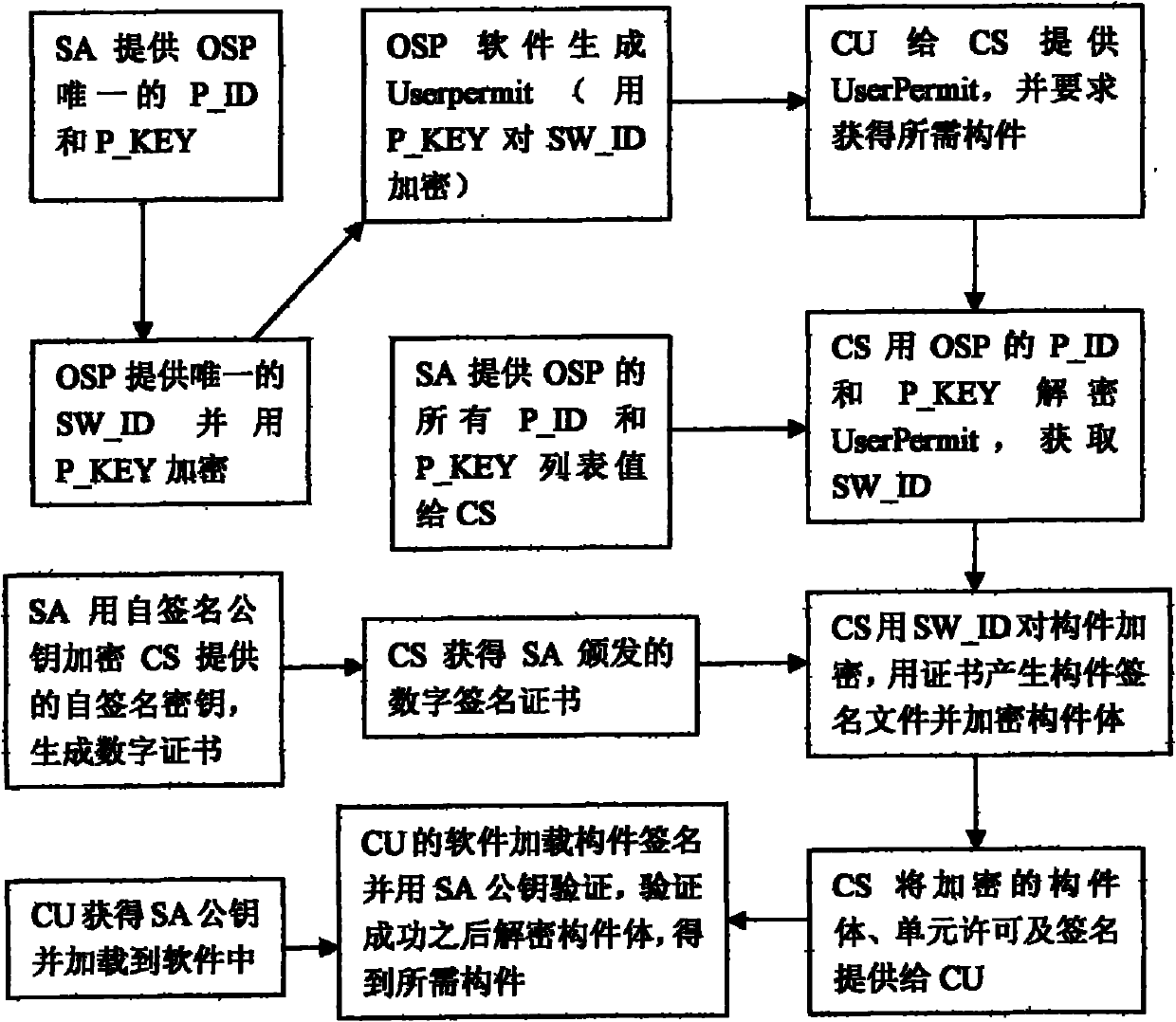
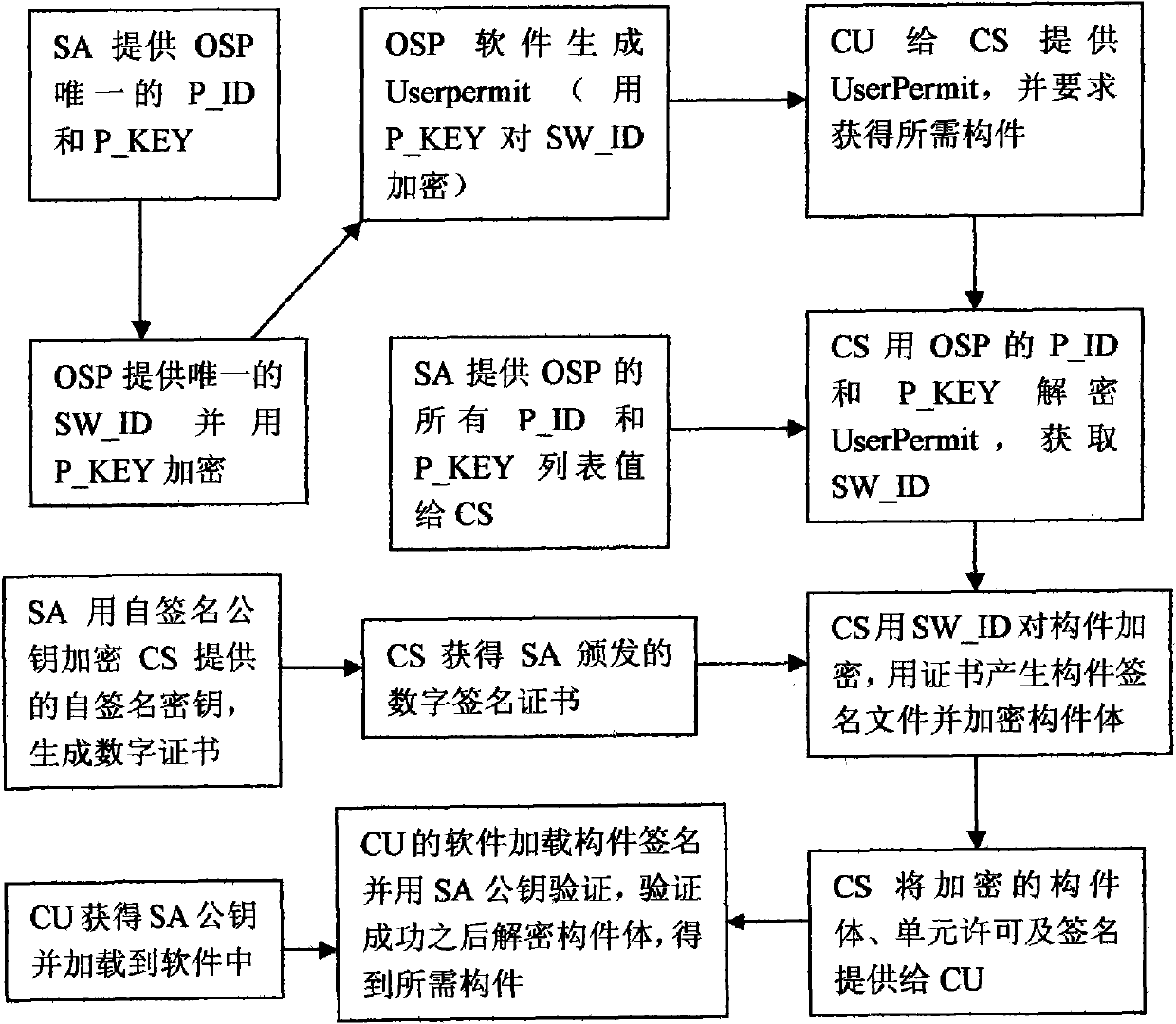
[0052] according to Figure 1-3 As shown, a controllable component release and use protection method includes: five roles need to be established, and the five roles are:
[0053] Role 1: Program Administrator SHCEME ADMINISTRATOR(SA)
[0054] Role 2: ORIGINAL SOFTWARE PRODUCTOR (OSP)
[0055] Role 3: COMPONENT PRODUCTOR (CP)
[0056] Role 4: COMPONENT SERVER (CS)
[0057] Role 5: Software component user COMPONENT USER (CU)
[0058] The roles are mutually authorized, and the components are effectively controlled in the process of release and use through digital certificates, signatures, and encryption methods, so that only the software produced by the recognized original software manufacturer OSP can use legal components. The approved component publishing server CS can issue legal components to software component users CU; software component users CU can apply for legal software components only when they get software from the legal original software manufacturer OSP.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com