Patents
Literature
356results about How to "Realize the binding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
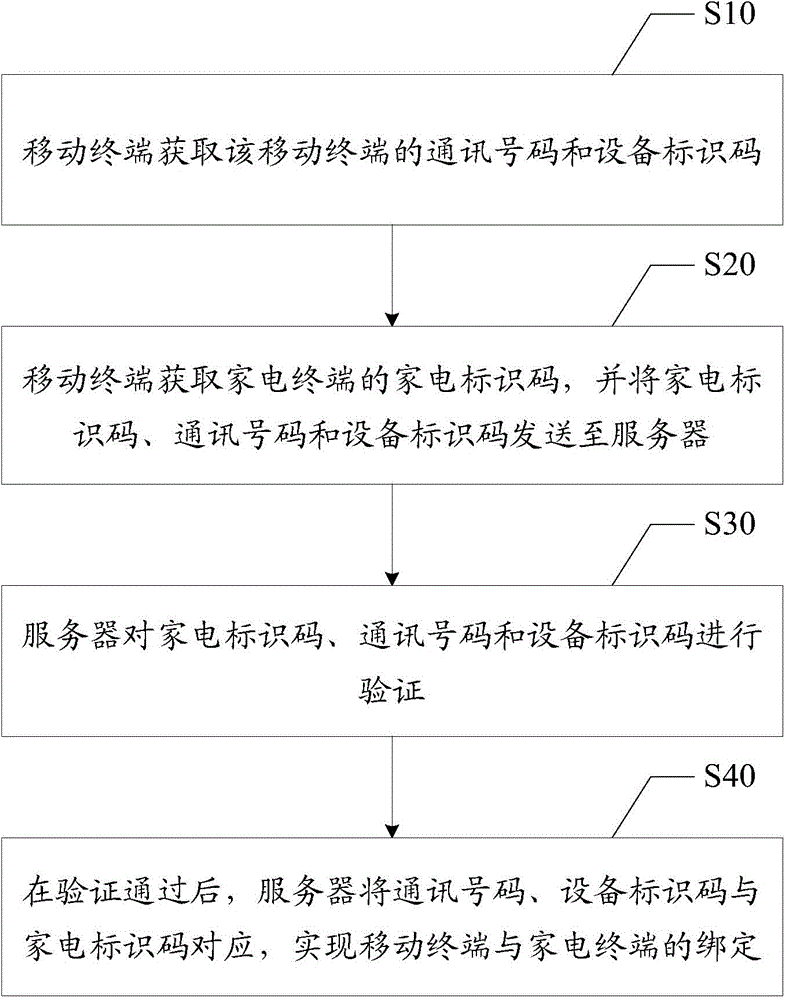
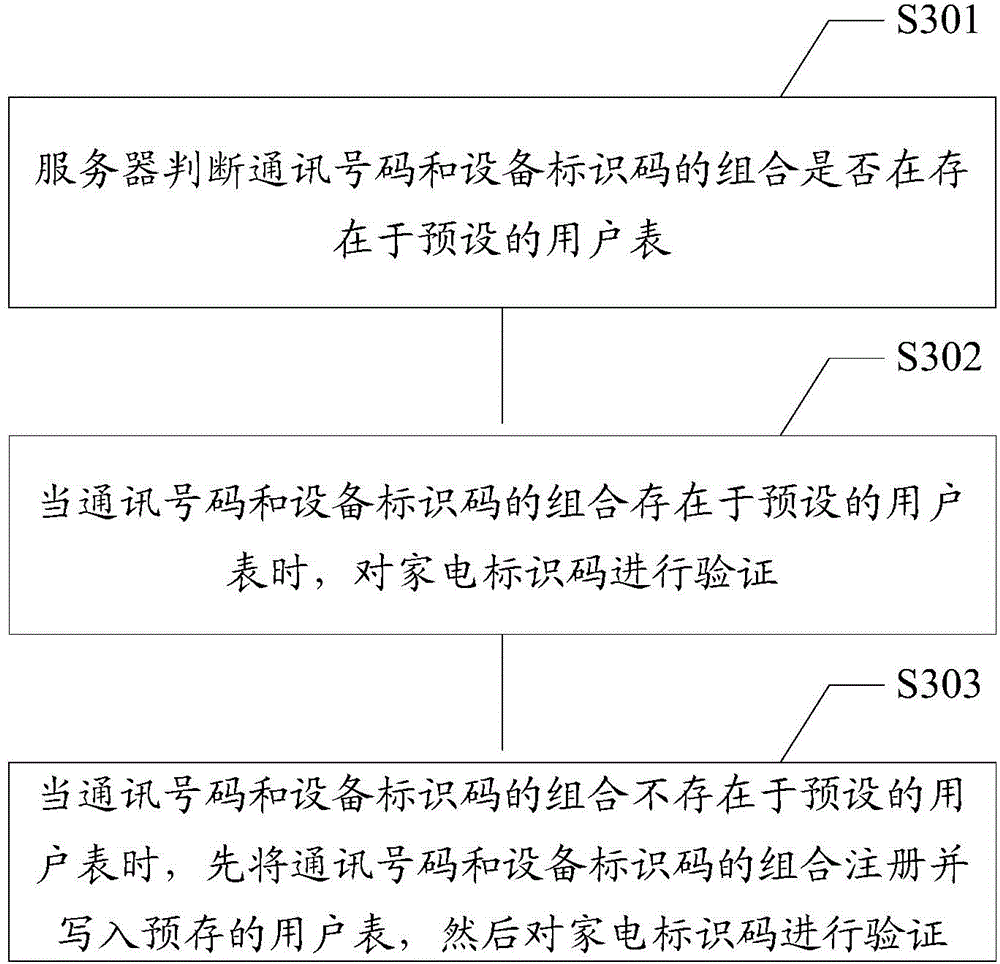
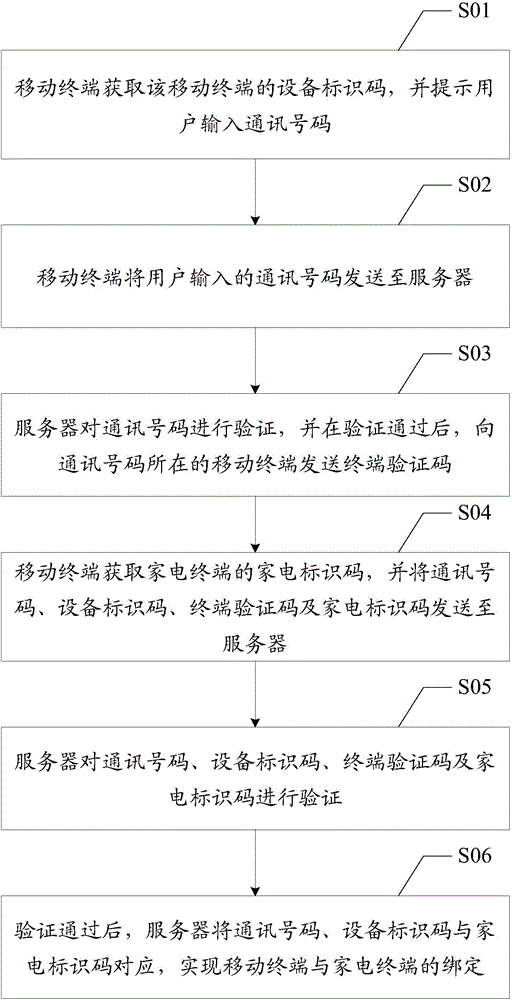
Binding method and system for mobile terminal and household appliance terminal
ActiveCN104468577ARealize the bindingSimplify operational complexityTransmissionSoftware engineeringOperational complexity
The invention discloses a binding method for a mobile terminal and a household appliance terminal. The method includes the steps that the mobile terminal obtains a communication number and an equipment identification code of the mobile terminal; the mobile terminal obtains a household appliance identification code of the household appliance terminal and transmits the household appliance identification code, the communication number and the equipment identification code to a server; the server verifies the household appliance identification code, the communication number and the equipment identification code and makes the communication number and the equipment identification code correspond to the household appliance identification code after verification is successful so that the mobile terminal and the household appliance terminal can be bound. The invention further discloses a binding system for the mobile terminal and the household appliance terminal. The complexity of user operation is reduced, and the user experience is improved.
Owner:GD MIDEA AIR-CONDITIONING EQUIP CO LTD
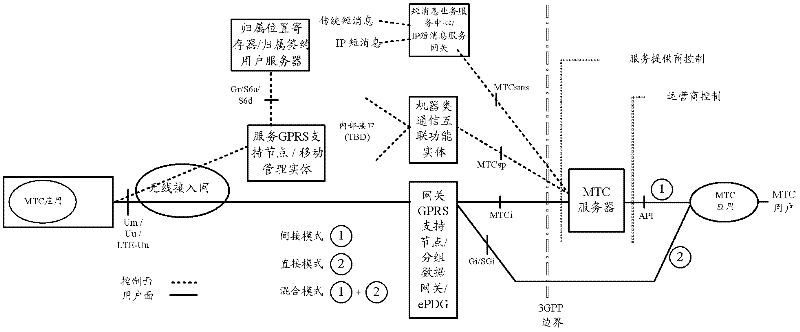
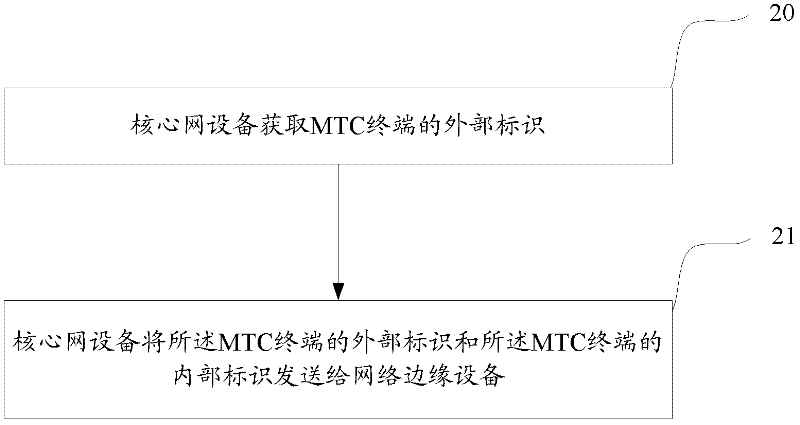
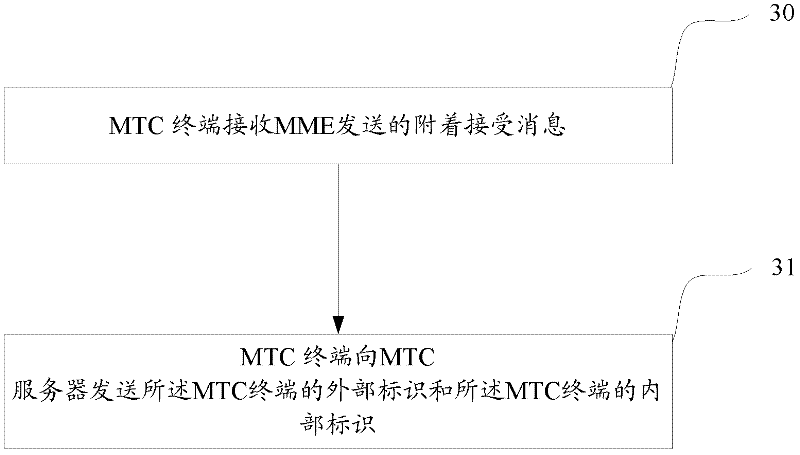
Terminal identifier notification and maintenance methods and equipment
ActiveCN102238534ARealize the bindingConnection managementMachine-to-machine/machine-type communication serviceInternal identifierComputer terminal
The embodiment of the invention discloses a terminal identifier notification method, terminal identifier notification equipment, a terminal identifier maintenance method and terminal identifier maintenance equipment, which relate to the technical field of wireless communication and are used for realizing the binding of an external identifier of a machine type communication (MTC) terminal and an internal identifier of the MTC terminal. The terminal identifier notification method comprises that: core network equipment acquires the external identifier of the MTC terminal; and the core network equipment transmits the internal and external identifiers of the MTC terminal to a network edge. The terminal identifier maintenance method comprises that: the network edge receives the internal and external identifiers of the MTC terminal from the core network equipment; and the network edge locally establishes and maintains mapping relationships between the internal and external identifiers of the MTC terminal. By the scheme, the binding of the internal and external identifiers of the MTC terminal is realized at the network edge.
Owner:DATANG MOBILE COMM EQUIP CO LTD
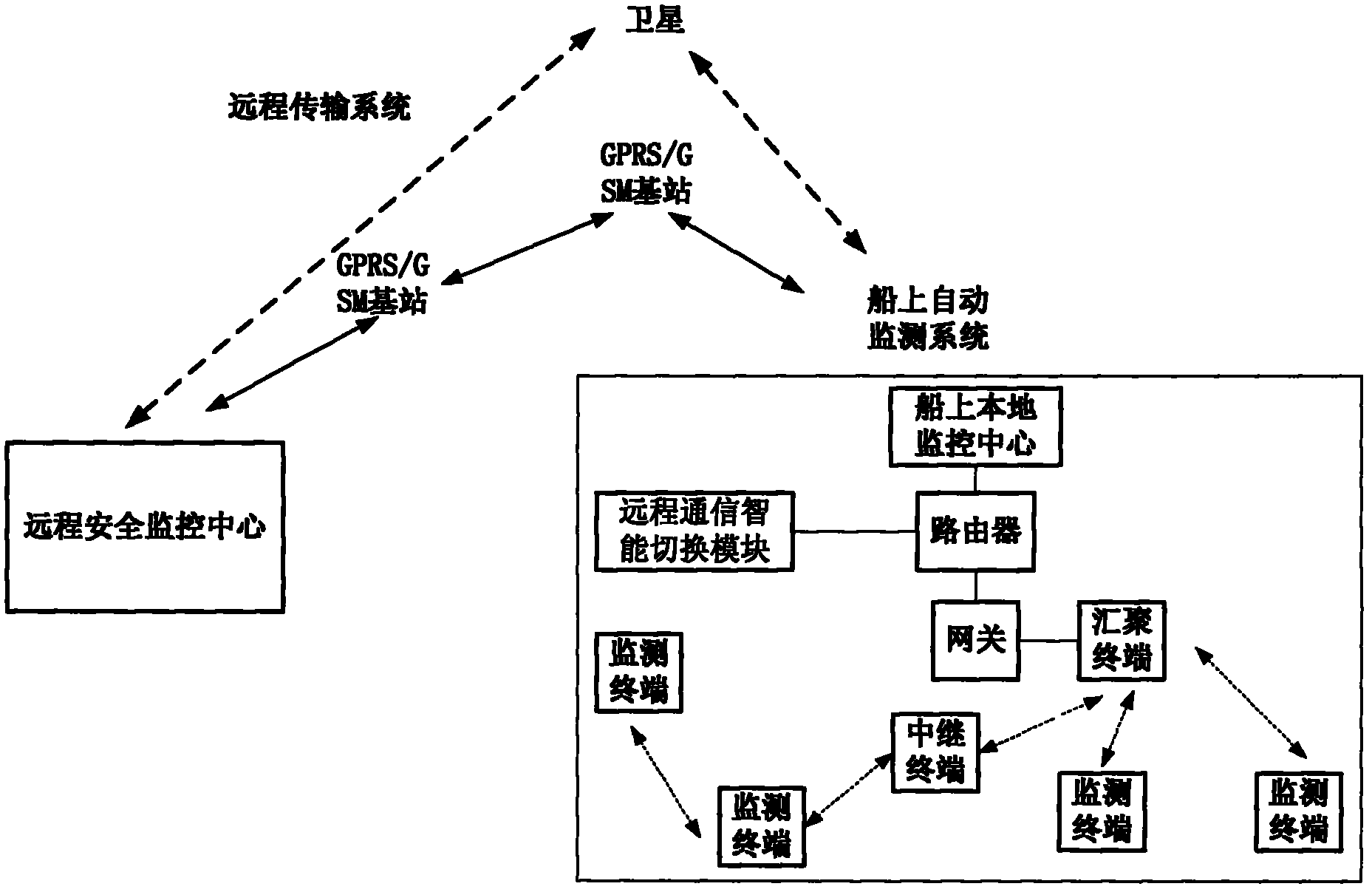
Intelligent monitoring system of dangerous goods container transported by ship
InactiveCN102223413ATroubleshoot temporary outagesRealize monitoring signal transmissionTransmission systemsCo-operative working arrangementsIntelligent lightingGeneral Packet Radio Service
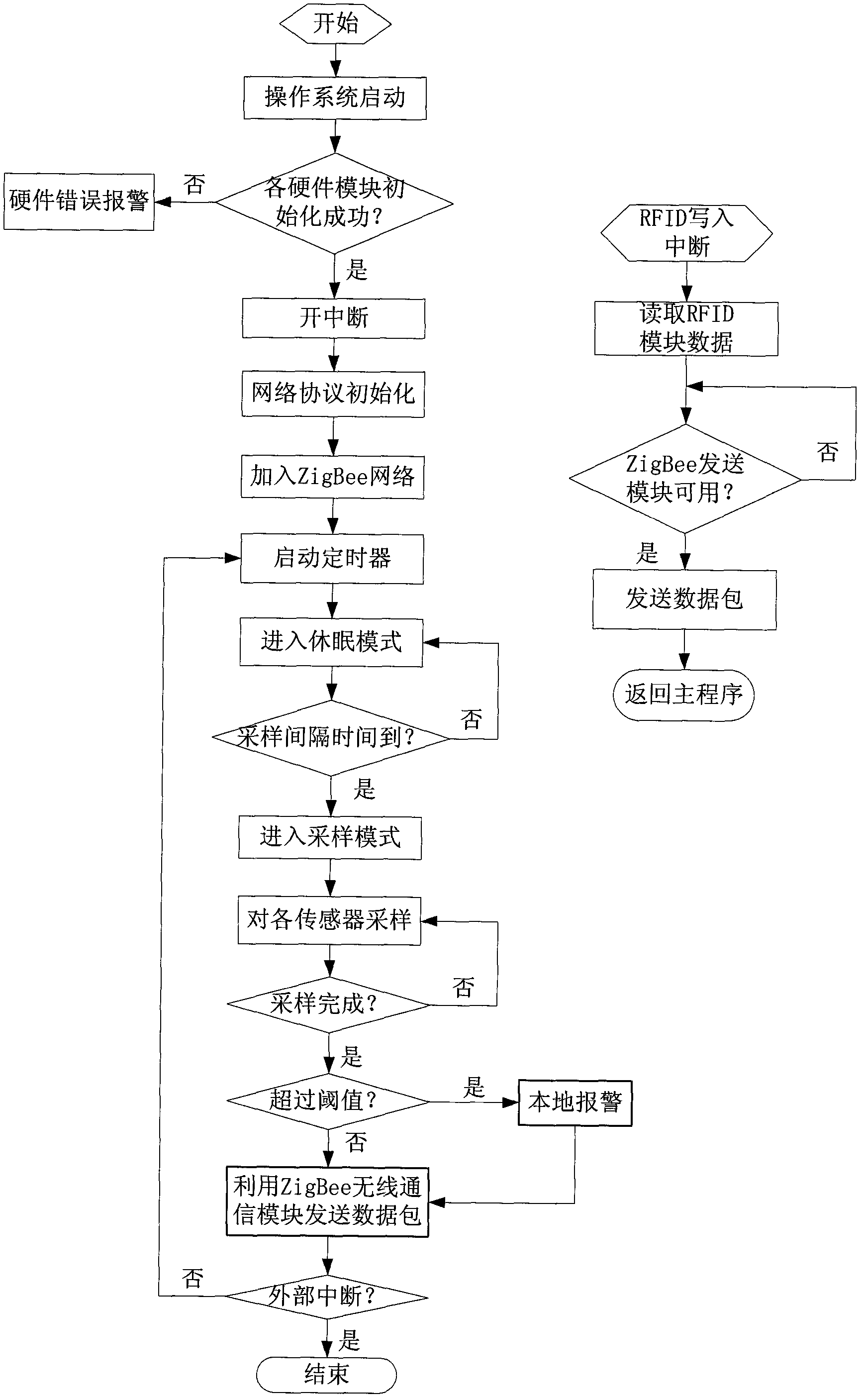
The invention discloses an intelligent monitoring system of a dangerous goods container transported by a ship, comprising an on-board automatic monitoring system, a remote transmission system and a monitoring center, wherein, the on-board automatic monitoring system realizes the real time perception of the on-board container condition by utilizing a monitoring terminal, a relay terminal and a convergence terminal for converging data arranged on the door of the container, transmits the collected condition information of the container to the remote monitoring center through a remote transmission system, and realizes the processing and alarming functions and the like of the collected condition information of the container at the front end. Through the networking of the monitoring terminal of the container based on a ZigBee technique, the system provided by the system solves the problem that the communication is temporarily interrupted caused by that the signals are shielded when a radio frequency identification device (RFID) or a general packet radio service (GPRS) / a global system for mobile communication (GSM), or a satellite is directly adopted as a communication module in the existing container monitoring system; and the system provided by the invention has the characteristics of high reliability and low communication cost and being easy to monitor, and provides an effective solution scheme for intelligently monitoring the dangerous goods container.
Owner:BEIJING INST OF AEROSPACE CONTROL DEVICES +1
Ethernet confirming access method
InactiveCN1403952ABandwidth controlEnsure normal communicationData switching networksSpecial data processing applicationsOperational systemAccess method
The Ethernet confirming access method is a wideband access method for computer network. The present invention adopts unique double web page server technology, and performs the access control and bandwidth limitation via the user access list operation. The unique forced entrance guard technology can re-orient the unauthorized user request imperatively. The present invention realizes the conformation, authorization, charge and bandwidth limitation of users via web page confirming process without needing any client end software, and this simplifies the user's operation, is independent with the user's operation platform and can operate simple and practically.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
Data sending method, data receiving method and relevant devices
InactiveCN103414535AImprove bandwidth utilizationTake full advantage of participation in data transmissionError preventionVirtual memoryNetwork interface controller
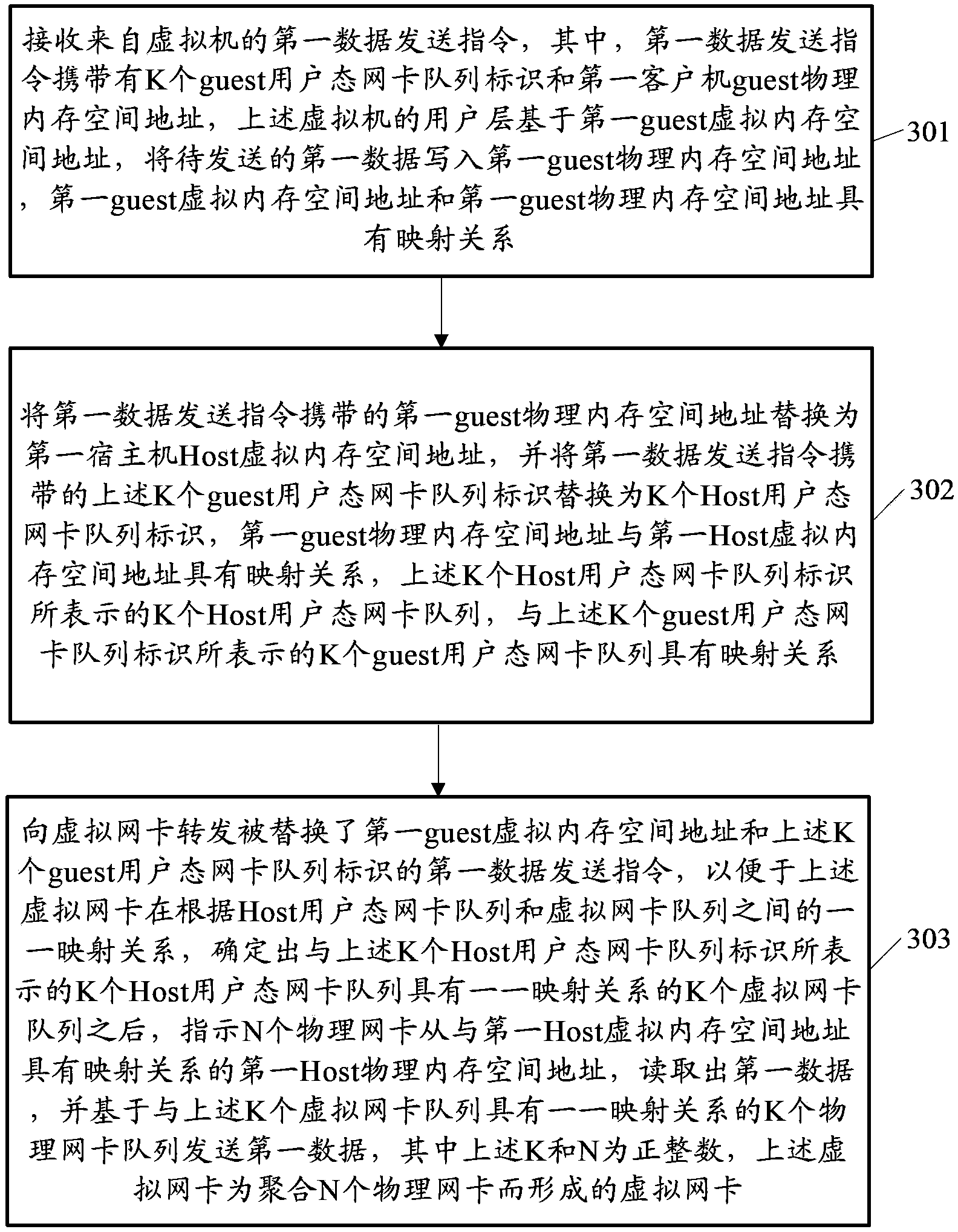
The embodiment of the invention discloses a data sending method, a data receiving method and relevant devices. The data sending method can include the steps of writing first data to be sent into a first kernel-mode physical memory space address based on a first user-mode virtual memory space address, and sending a first data sending instruction to a virtual network adapter so that the virtual network adapter can indicate N physical network adapters to read first data from the first kernel-mode physical memory space address which has a mapping relationship with the first user-mode virtual memory space address after determining K virtual network adapter queues which have one-one mapping relationships with K user-mode network adapter queues represented by K user-mode network adapter queue identifications, and sending the first data based on the K physical network adapter queues which have the one-one mapping relationships with the K virtual network adapter queues. According to the technical scheme, the improvement of the bandwidth use ratio achieved after the physical network adapters are aggregated is facilitated.
Owner:HUAWEI TECH CO LTD
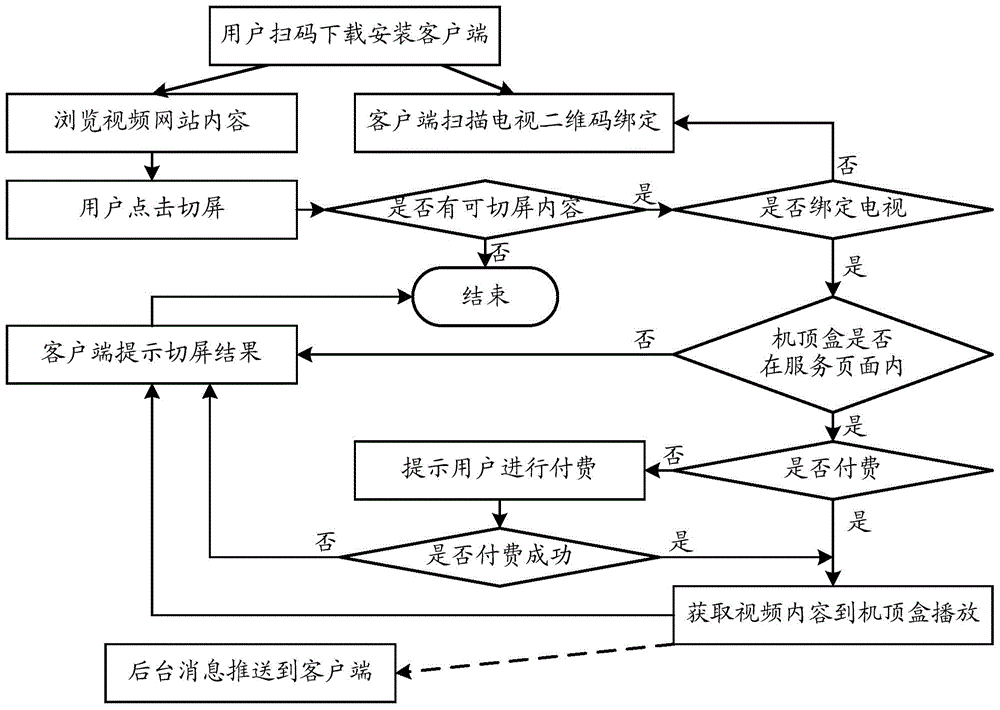
Method and system for binding of television terminal and mobile terminal and achieving switching showing
InactiveCN104486650AEasy to operateImprove experienceSelective content distributionCable televisionIPTV
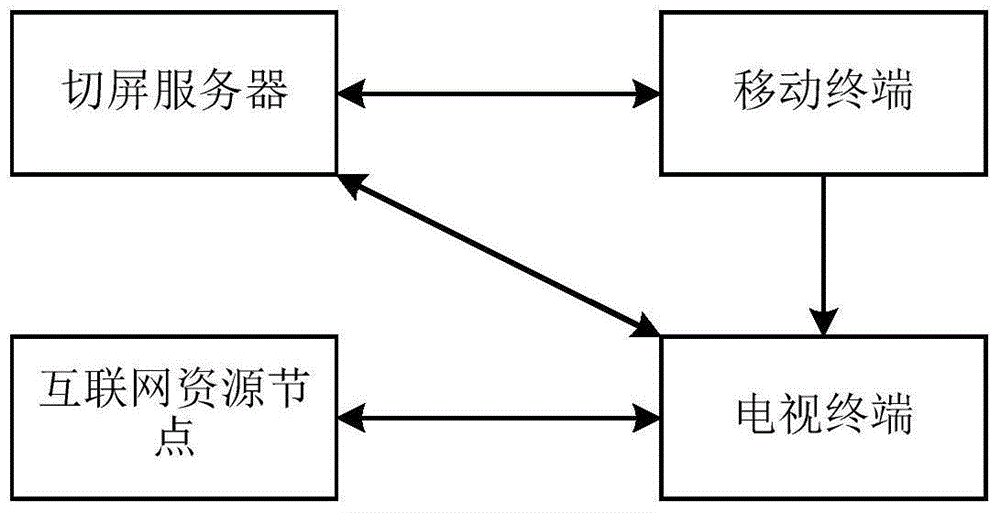
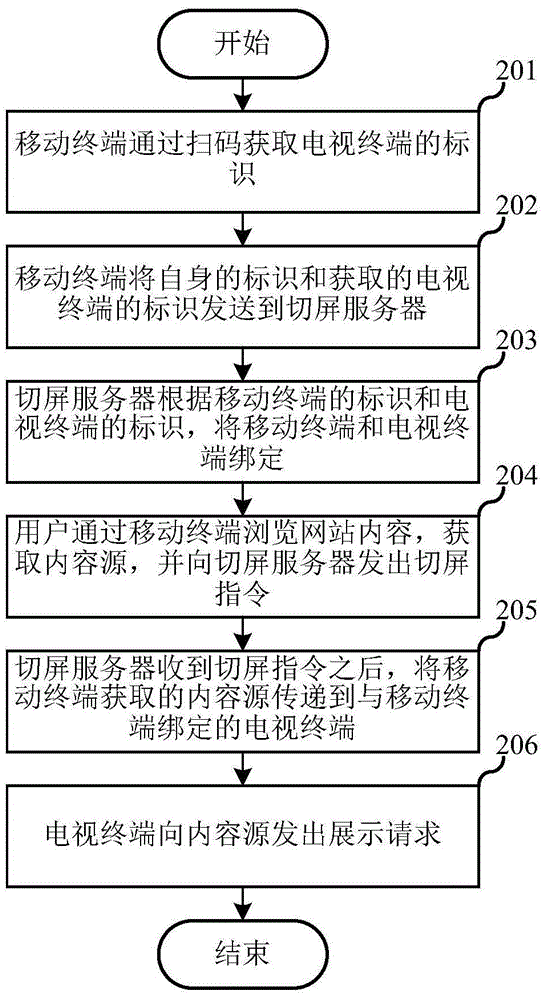
The invention relates to the technical field of IPTV and discloses a method and system for binding of a television terminal and a mobile terminal and achieving switching showing. The mobile terminal obtains the identification of the television terminal by code scanning, the identification of the mobile terminal and the obtained identification of the television terminal are sent to a screen switching server, and the screen switching server binds the mobile terminal and the television terminal according to the identification of the mobile terminal and the identification of the television terminal. When switching showing is needed, a user browses video website content through the mobile terminal, a content source is obtained, screen switching instructions are sent to the screen switching server, and after the screen switching server receives the screen switching instructions, the content source obtained by the mobile terminal is transmitted to the television terminal bound with the mobile terminal. The television terminal sends a showing request to the content source. Binding of the television terminal and the mobile terminal is carried out in a code scanning mode, and binding of the television terminal and the mobile terminal is achieved quickly.
Owner:上海昌视网络科技有限公司
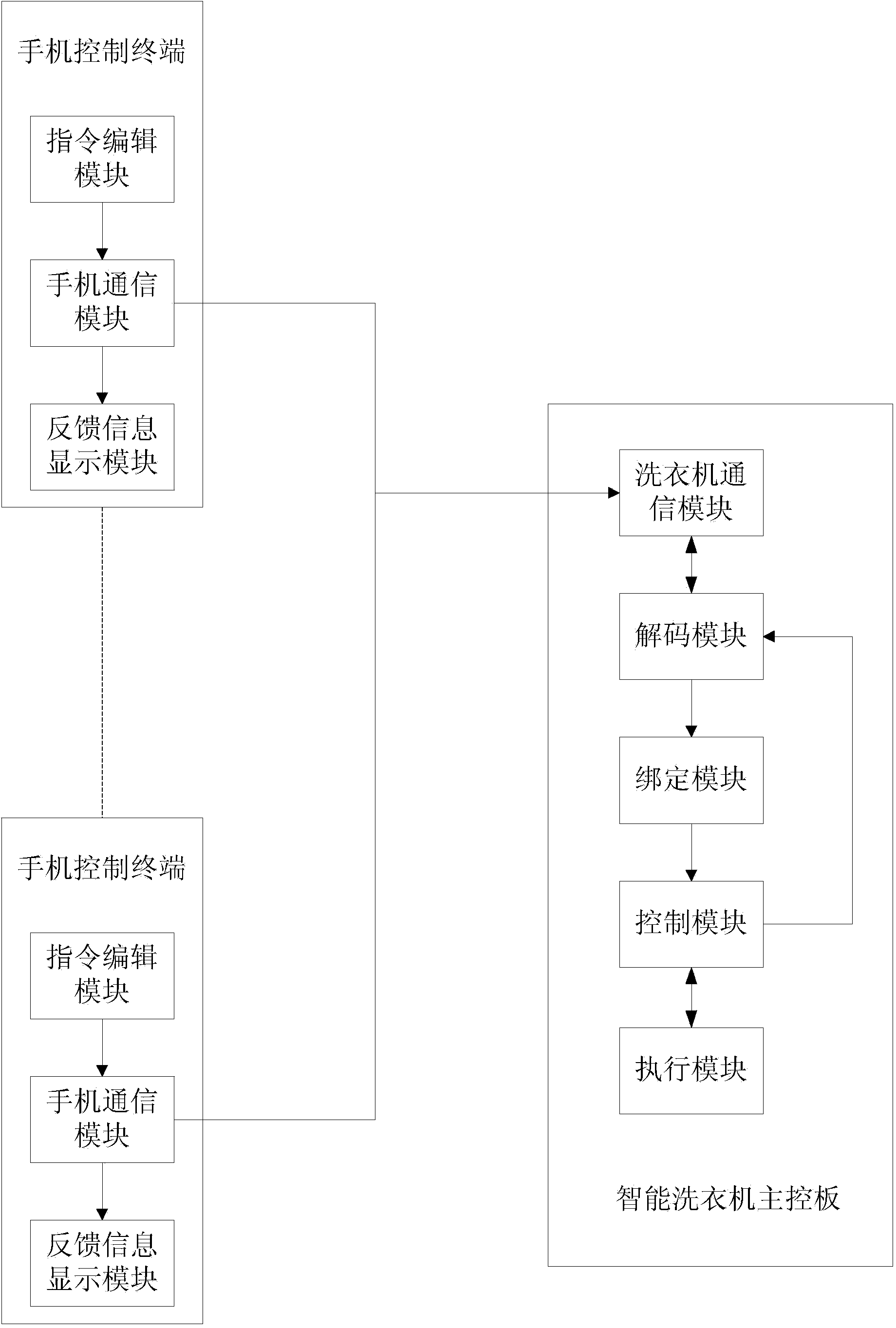
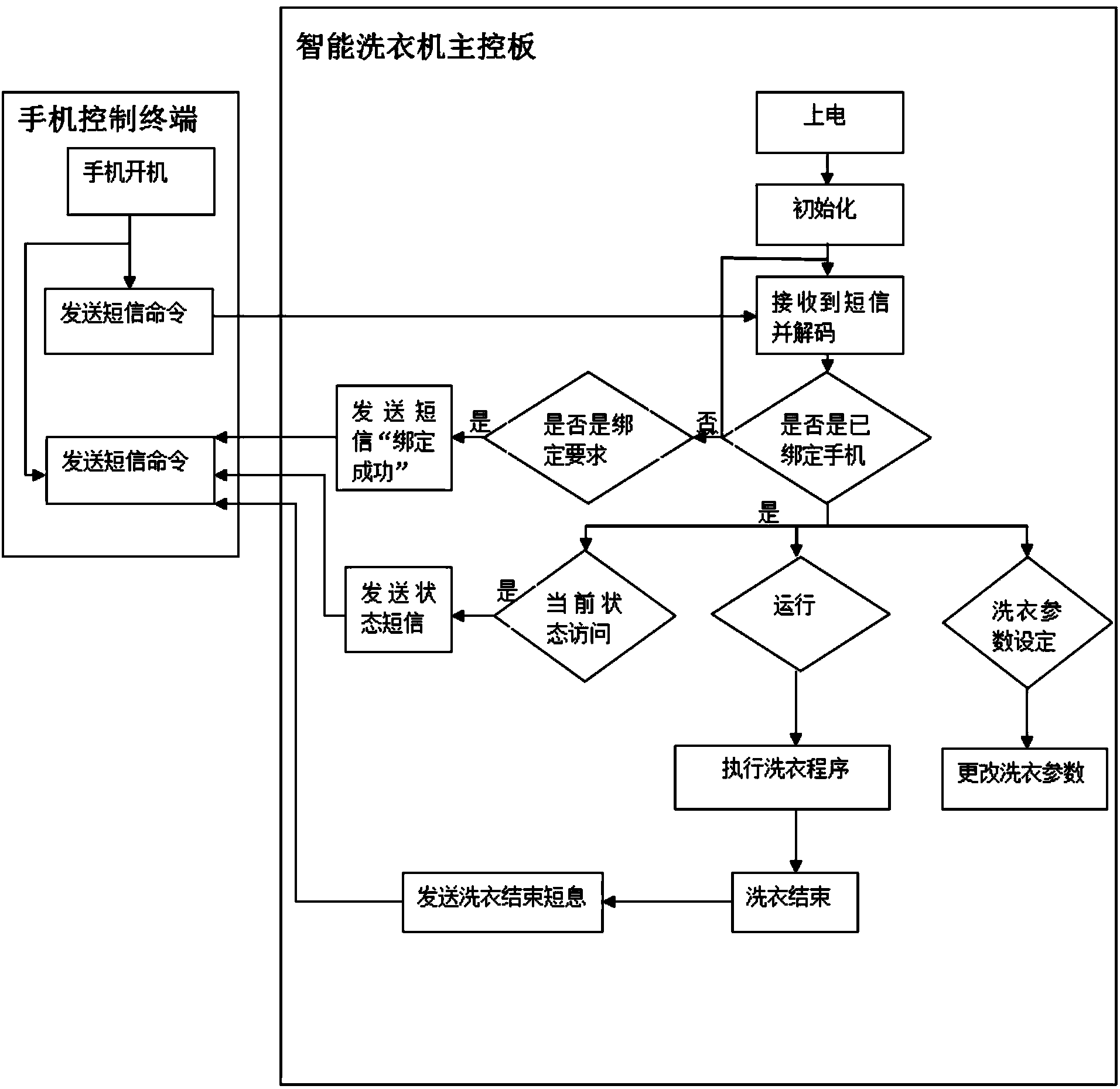
Control system of intelligent washing machine
InactiveCN104404738AAchieve common controlImprove experienceControl devices for washing apparatusSubstation equipmentControl systemComputer module
The invention discloses a control system of an intelligent washing machine. The control system comprises an intelligent washing machine main control board and one or more mobile phone control terminals, wherein a GSM module is directly and additionally arranged on the intelligent washing machine, so that simpleness, convenience and feasibility are realized, and intelligent control can be realized without great modification on the existing intelligent washing machine; the operating statuses of the intelligent washing machine can be controlled and read through transceiving short messages by a mobile phone, and certain economic benefit is realized; in addition, as the additionally arranged GSM module can bind a mobile phone number, and can also bind multiple different mobile phone numbers and partition the priority ranks, multi-user common control is realized; moreover, due to the arrangement of a clothes taking reminding module, a fault detection module and an unbinding module, the entire control system is more flexible and humanized, and the situation that a user can obtain excellent usage experience is ensured.
Owner:XINAN JIANGSU ELECTRIC APPLIANCE CO LTD
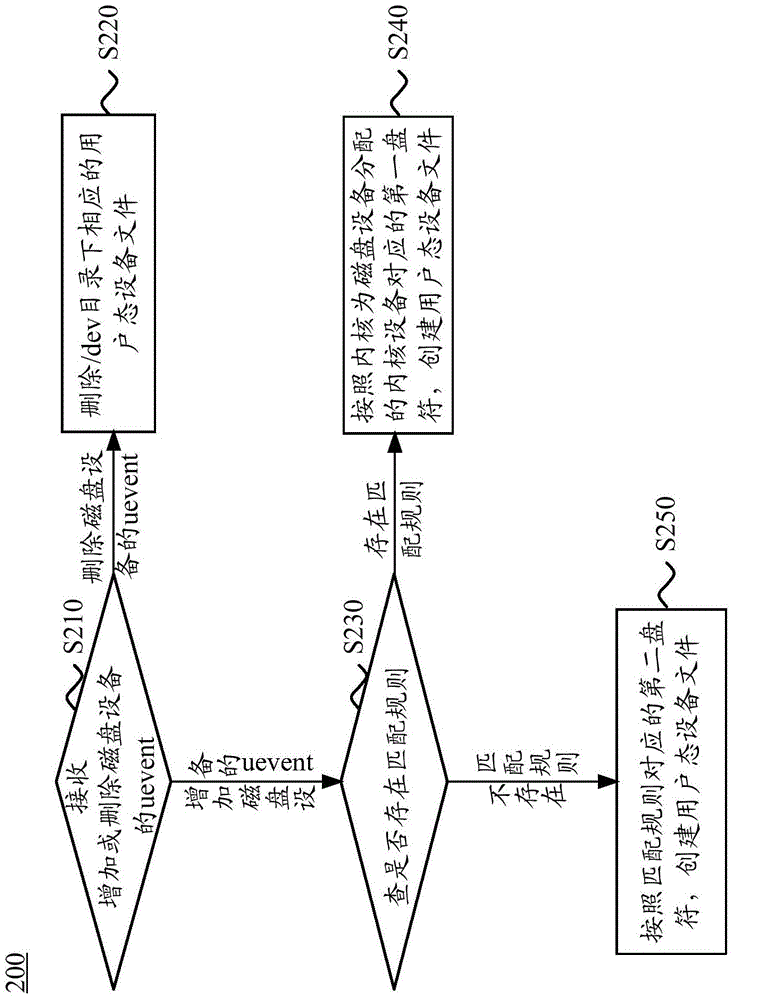
Method and device for binding disk drive in Linux system
The invention discloses a method and device for binding a disk drive in a Linux system. The method comprises the steps that when a disk device is added to the Linux system, a first disk drive corresponding to a kernel device is assigned to the disk device by a kernel; information indicating a slot position of the disk device is obtained by UDEV, and a second disk drive corresponding to a user mode device is assigned to the disk device by the UDEV according to the slot position of the disk device and the mapping relation between a preset slot position and the disk drive; and name change information is transmitted to the kernel by the UDEV, and the name of the kernel device and a name pointing to a link of the kernel device is changed from the first disk drive into the second disk drive by the kernel according to the name change information. According to the method, the disk drive of the user mode device is determined by the UDEV for the new disk device, the name change information is transmitted to the kernel by the UDEV, and the disk drive of the kernel device and the disk drive of the link pointing to the kernel device are modified to be identical to the disk drive of the user mode device by the kernel according to the name change information, so that the binding between the slot position and the disk drive is achieved.
Owner:XFUSION DIGITAL TECH CO LTD
Software license management system based on enterprise network
InactiveCN103347090ARealize the bindingReduce demandTransmissionProgram/content distribution protectionData setSoftware asset management
The invention discloses a denormalization strategy selection method on a data set and particularly relates to a system for reasonably managing establishment, allocation and withdrawing of the software licenses in the enterprise internal network range. The software license management system comprises a main server, agent servers and clients. The software license management system has the advantages that through the mechanism that a part of clients share a small part of software licenses, the demanded quantity of software licenses of an enterprise is effectively reduced, the agent servers are arranged in all departments to manage the issuing of the software licenses of the departments, meanwhile, the main server correspondingly controls the number of the software licenses on each agent server, reasonable allocation of the software licenses in the enterprise is achieved, tasks of allocating the software licenses are distributed to all the agent servers through a layering idea, therefore, the load of the main server can be effectively reduced, meanwhile, flow of the enterprise internal network is saved, and excessive system communication information is prevented from flowing into an enterprise backbone network.
Owner:成都盈锐科技有限公司
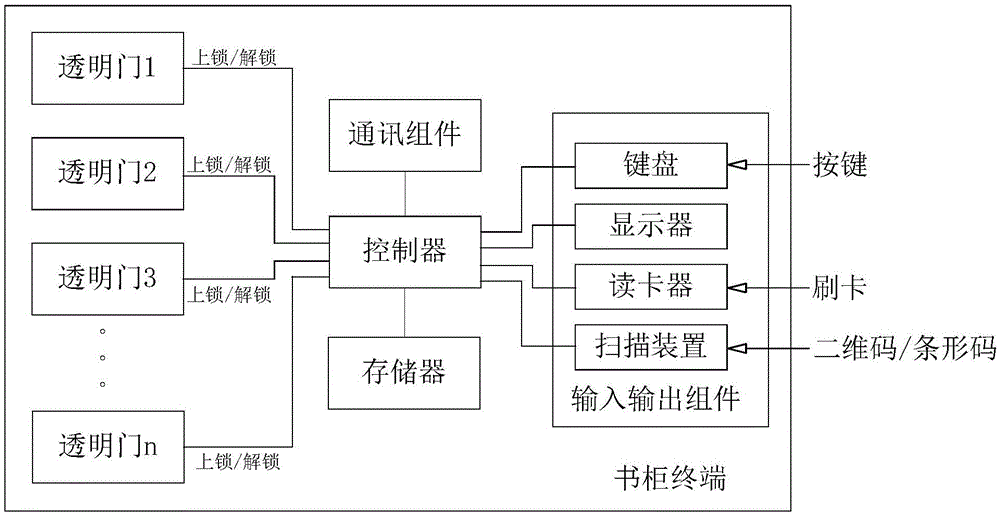
Automatic book borrowing, returning and exchanging method and automatic book borrowing system
InactiveCN105678924ARealize automatic borrowing of booksReturn booksCo-operative working arrangementsCash registersBarcodeComputer terminal
The present invention provides an automatic book borrowing, returning and exchanging method and an automatic book borrowing system. The automatic book borrowing method comprises the steps of S10 providing a bookcase terminal; S11 responding to an input operation via a controller to confirm the user identity of an operator; S12 using the controller to consult whether the pre-contract book borrowing recording of the user exists in a local memorizer, if yes, entering a step S13, if not, entering a step S141; S13 using the controller to respond to the input operation of the two-dimension codes, the bar codes or the ciphers to compare the two-dimension codes, the bar codes or the ciphers with the corresponding two-dimension code, bar code or cipher information stored in the local memorizer, if the two-dimension codes, the bar codes or the ciphers match the stored two-dimension code, bar code or cipher information, driving a corresponding transparent door to unlock; S141 using the controller to respond to the input operation further to confirm a book grid corresponding to a book borrowed currently, and entering a step S142; S142 consulting the local memorizer, using the controller to determine whether the book in the book grid is pre-contacted, if not, driving the corresponding transparent door corresponding to the book grid to unlock.
Owner:梁振华
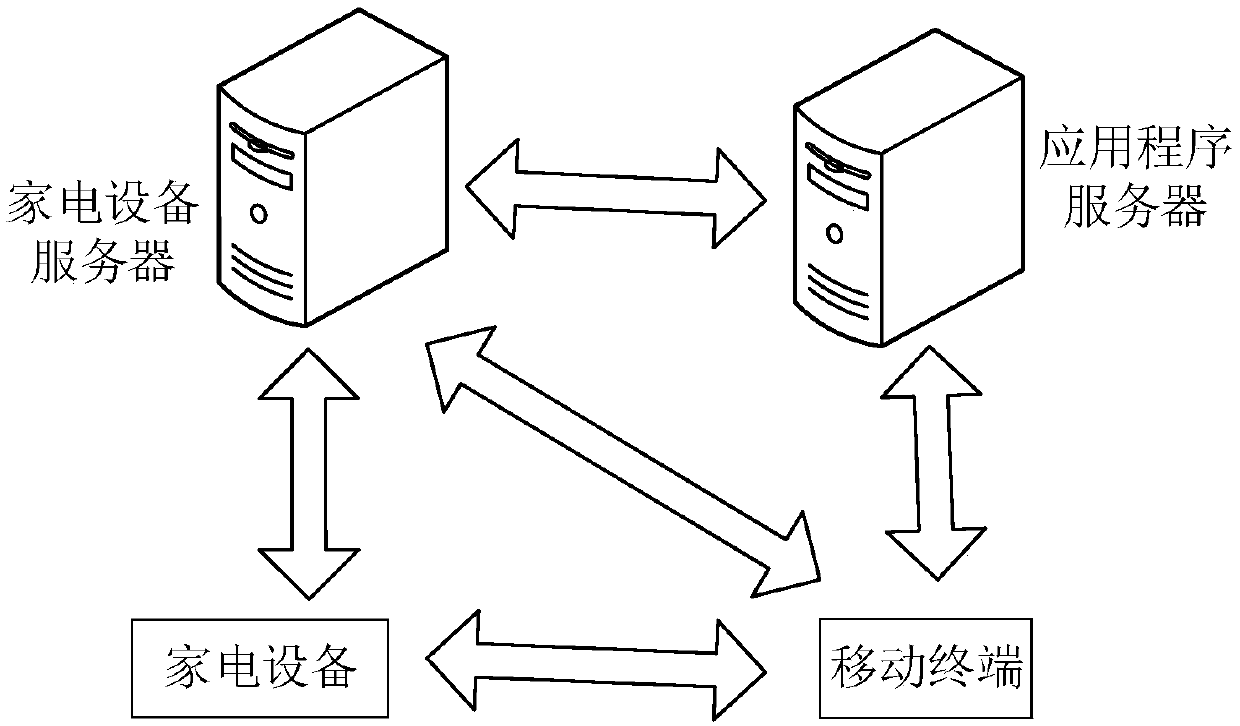
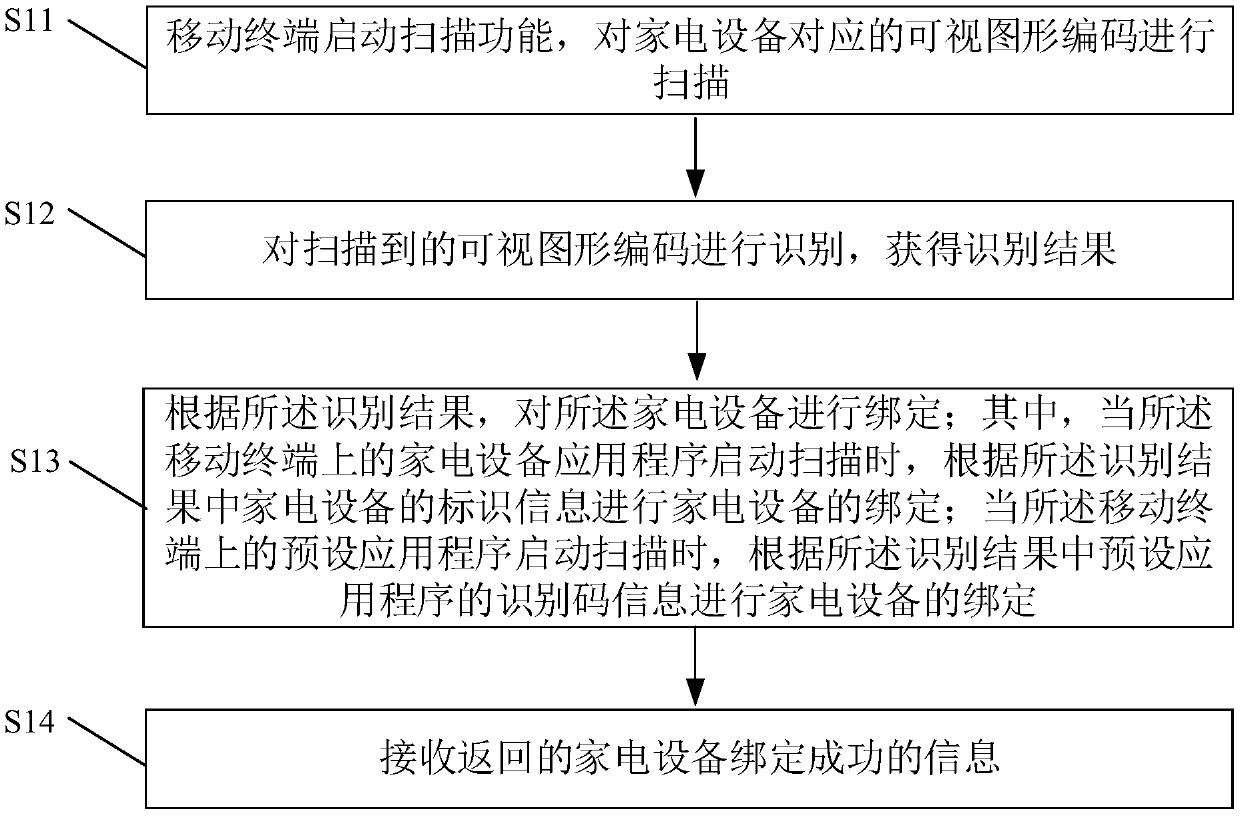
Household appliance binding system and method, mobile terminal, server, household appliance and medium
ActiveCN109587016ARealize the bindingImprove convenienceRecord carriers used with machinesHome automation networksGraphicsApplication server
The invention discloses a household appliance binding system and method, a household appliance, a mobile terminal, a household appliance server, an application program server and a medium. The household appliance binding system is characterized in that the household appliance acquires and displays a visual graphic code; the mobile terminal scans the visual graphic code displayed by the household appliance to generate a binding request and sends the binding request to the household appliance server or the application program server; the household appliance server binds the mobile terminal withthe household appliance according to the identification information of the household appliance in a binding request and the account information of a household appliance application program; the application program server obtains a household appliance serial number corresponding to the identification code of a preset application program in the application program server according to the identification code of the preset application program in the binding request; and the obtained household appliance serial number and the account information of the preset application program are sent to the household appliance server and the binding of the mobile terminal and the household appliance is performed.
Owner:GD MIDEA AIR-CONDITIONING EQUIP CO LTD
Method for logging in online game through mobile equipment
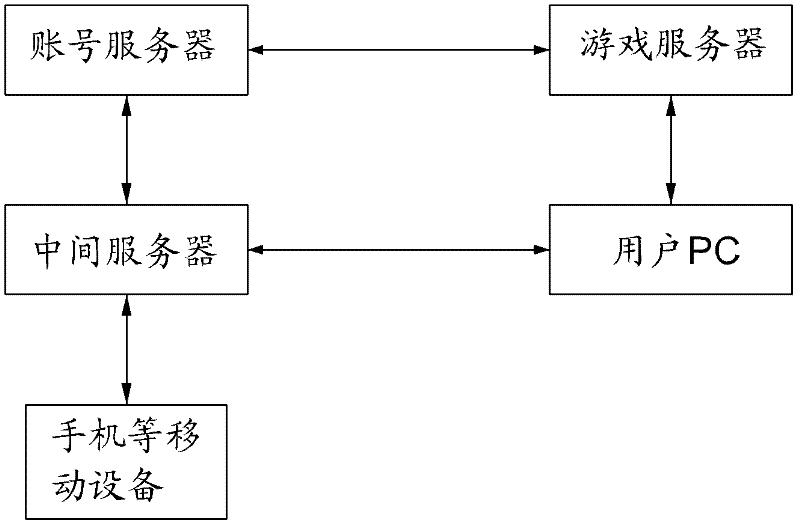
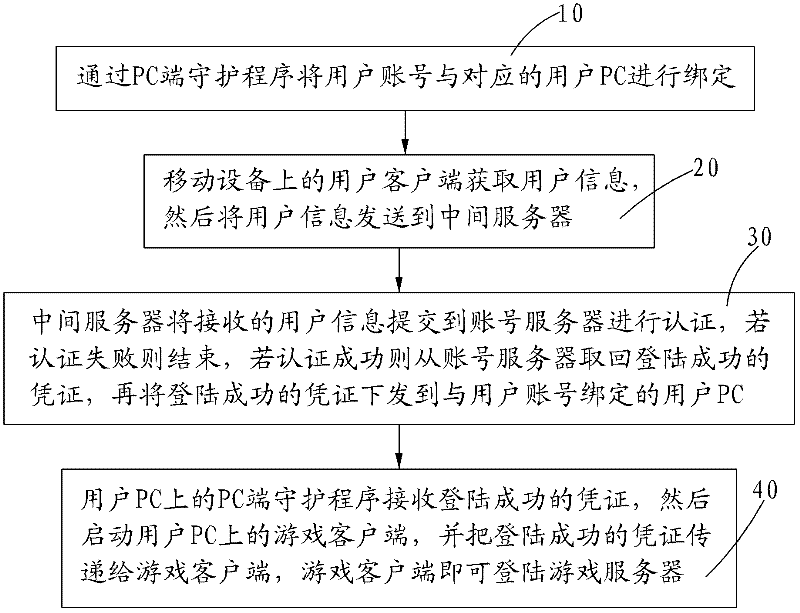
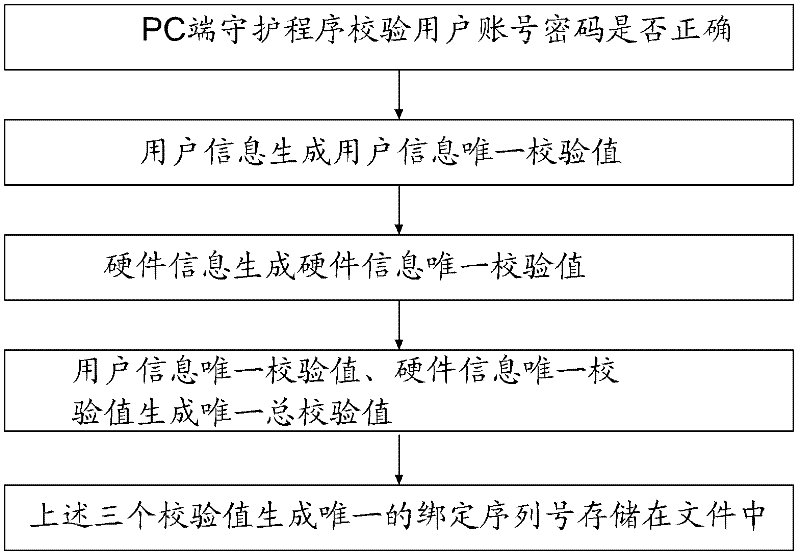
ActiveCN102510378AImprove securitySolve the problem of hackingUser identity/authority verificationNetwork data managementClient-sideInternet privacy
The invention provides a method for logging in an online game through mobile equipment. The method comprises the following steps of: 10, binding a user account and a corresponding user personal computer (PC) by using a PC end daemon on the user PC; 20, acquiring user information which is input by a user through a user client on the mobile equipment, and sending the user information to an intermediate server; 30, after the intermediate server receives the user information, submitting the user information to an account server, authenticating the user information, if authentication fails, finishing operation, and if authentication succeeds, taking back a login success certificate from the account server, and then issuing the login success certificate to the user PC which is bound with the user account; and 40, after the PC end daemon receives the login success certificate, starting a game client on the user PC, and transferring the login success certificate to the game client to log in a game server through the game client. By adoption of the method, the login process is separated from the game client, so that the problem of account stealing based on a PC end can be solved.
Owner:FUJIAN TQ DIGITAL
Ontology library based transportation big data semantic application service method
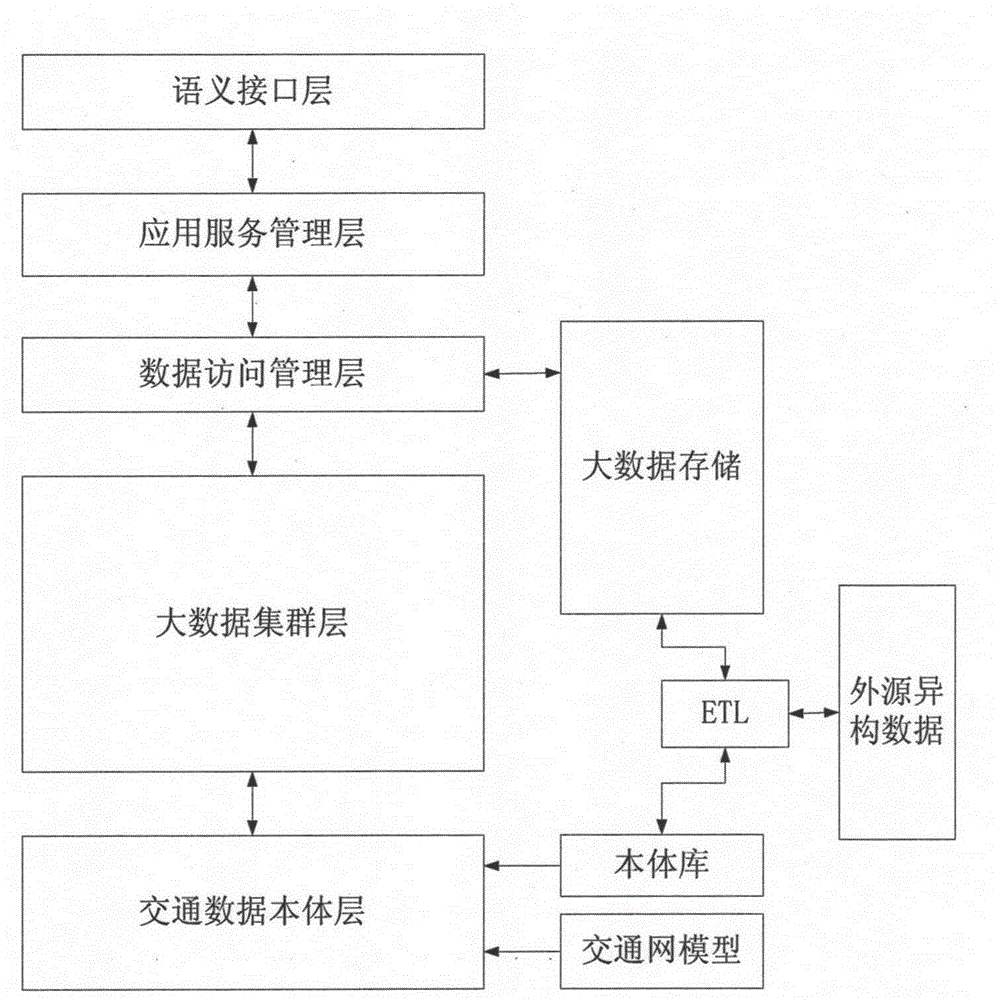
ActiveCN105183834AOntological organizationResolve Smart ServicesRelational databasesSpecial data processing applicationsRelational databaseData platform
The technical solutions of the present invention are to provide an ontology library based transportation big data semantic application service method, and are characterized by comprising steps of: step 1, establishing an ontology library based transportation big data platform, wherein the transportation big data platform comprises a traffic data ontology layer, a transportation network model, a data ETL layer, a big data cluster layer, a data access service layer, an application service logic layer, a big data storage layer, and a logic design of a semantic access interface layer module; and step 2, performing data access based on semantic logic. The ontology library based transportation big data semantic application service architecture method provided by the present invention aims is to resolve ontological organization and intelligent service of multi-source heterogeneous data in an integrated environment of HADOOP / relational database, and especially a key technical problem that in a future large data open service environment, people can retrieve accurate data resources and corresponding services through voice and text.
Owner:SHANGHAI SEARI INTELLIGENT SYST CO LTD
Method and device for binding user account with monitoring equipment in video monitoring system
ActiveCN104410813ASimplify operation stepsImprove usabilityClosed circuit television systemsNetwork data managementEmbedded systemClient-side
The invention belongs to the technical field of video monitoring, and discloses a method and a device for binding a user account with monitoring equipment in a video monitoring system. The method comprises the following steps that: a user scans a two-dimensional code on monitoring equipment through a mobile terminal to obtain an activation code of the monitoring equipment, and carries the activation code to transmit a download request to a management server; the management server generates an exclusive mobile monitoring client installation package for the mobile terminal; the mobile terminal downloads and installs the installation package, and registers and logs in the management server; the management server binds an equipment serial number with the user account according to the equipment serial number of the monitoring equipment in login information, generates a monitoring equipment name, and issues the generated monitoring equipment name to the mobile terminal; and the mobile terminal performs video monitoring service operation according to the issued monitoring equipment name and the IP (Internet Protocol) address and port number of the corresponding monitoring equipment. The invention further discloses a device corresponding to the method. Through adoption of the method and the device, the operation steps of the user are simplified, and safe and accurate binding of the user account with the monitoring equipment is realized.
Owner:ZHEJIANG UNIVIEW TECH
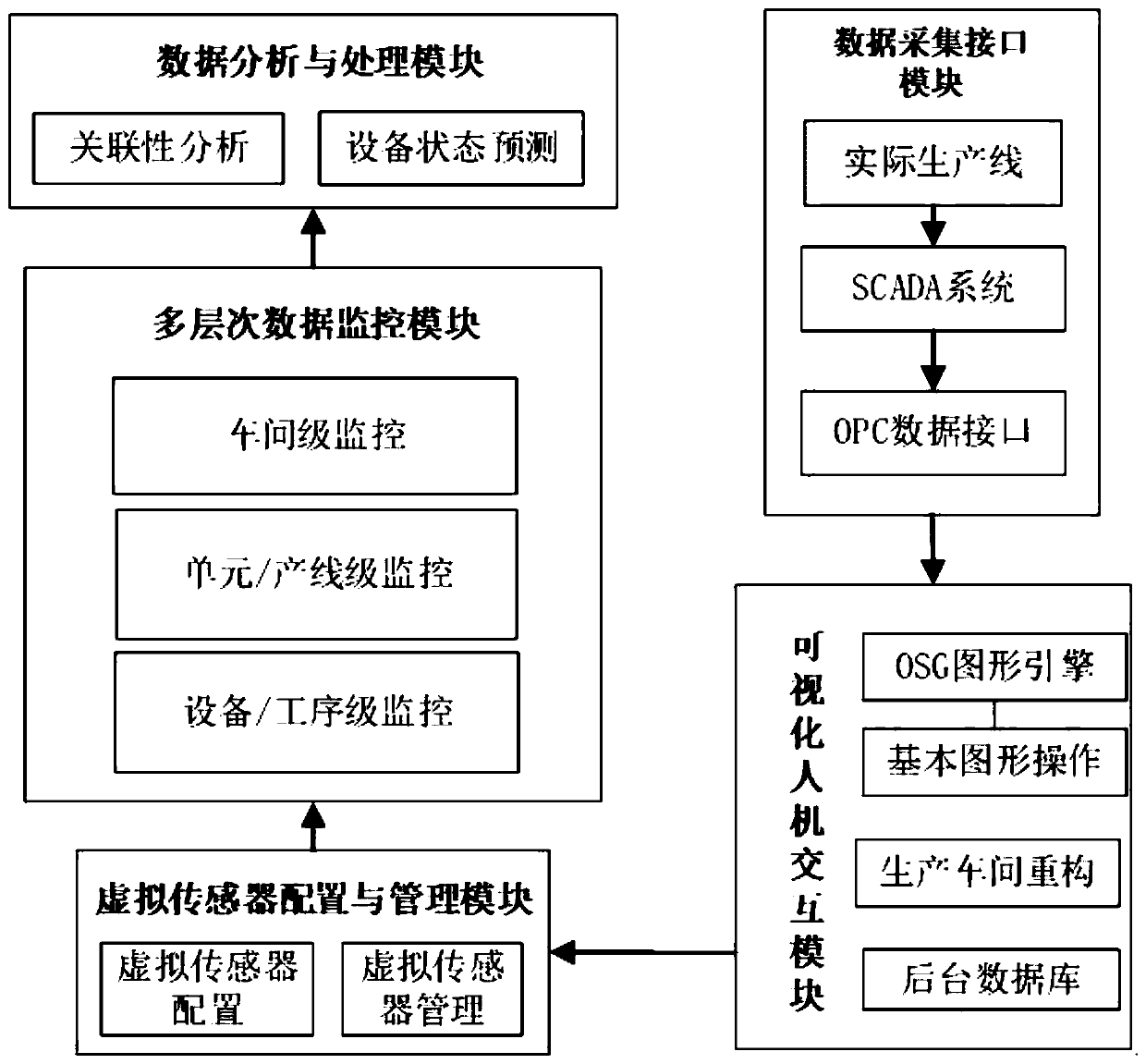
Visual system for workshop production process based on virtual sensor and building method
InactiveCN109976296AImprove data transparencyRealize associationProgramme total factory controlData acquisitionMulti level data
The invention discloses a visual system for a workshop production process based on a virtual sensor and a building method. The visual system comprises a data acquisition interface module, a visual human-machine interaction module, a virtual sensor configuration module, a multi-level data monitoring module, a data analyzing and processing module. Through adoption of the virtual system, data management and control are combined with the visual virtual workshop, and the visual degree of the workshop management and control and the data transparent degree of the production process are improved. A uniform data monitoring format is defined through the virtual sensor, and association and binding of the data monitoring points, the three-dimensional visual model and physical equipment are realized. The visual system is suitable for discrete production enterprises and process type enterprises, can be used for monitoring and managing the workshops implementing different production manners, and hasrelatively high universality.
Owner:SOUTHWEST JIAOTONG UNIV +1
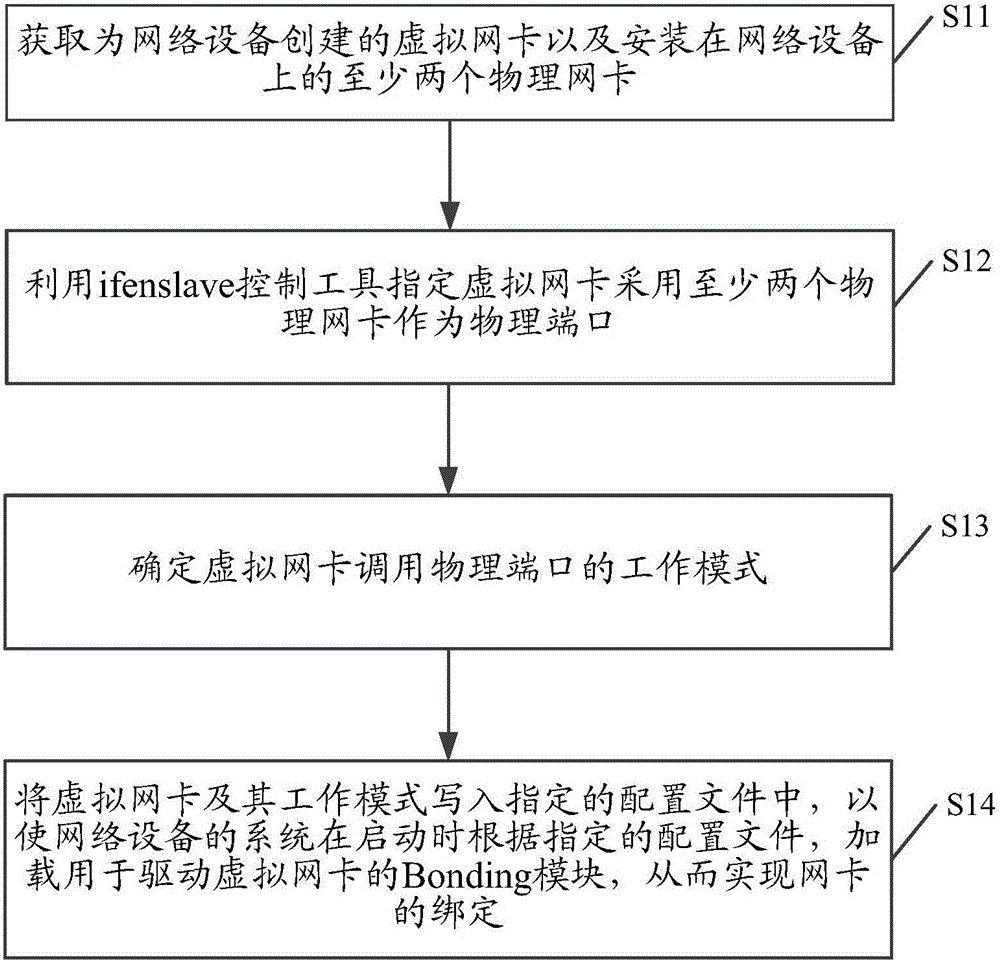
Network interface card binding method and device
InactiveCN106209449AImprove network transmission speedGuaranteed High AvailabilityData switching networksPhysical networkVirtual network interface card
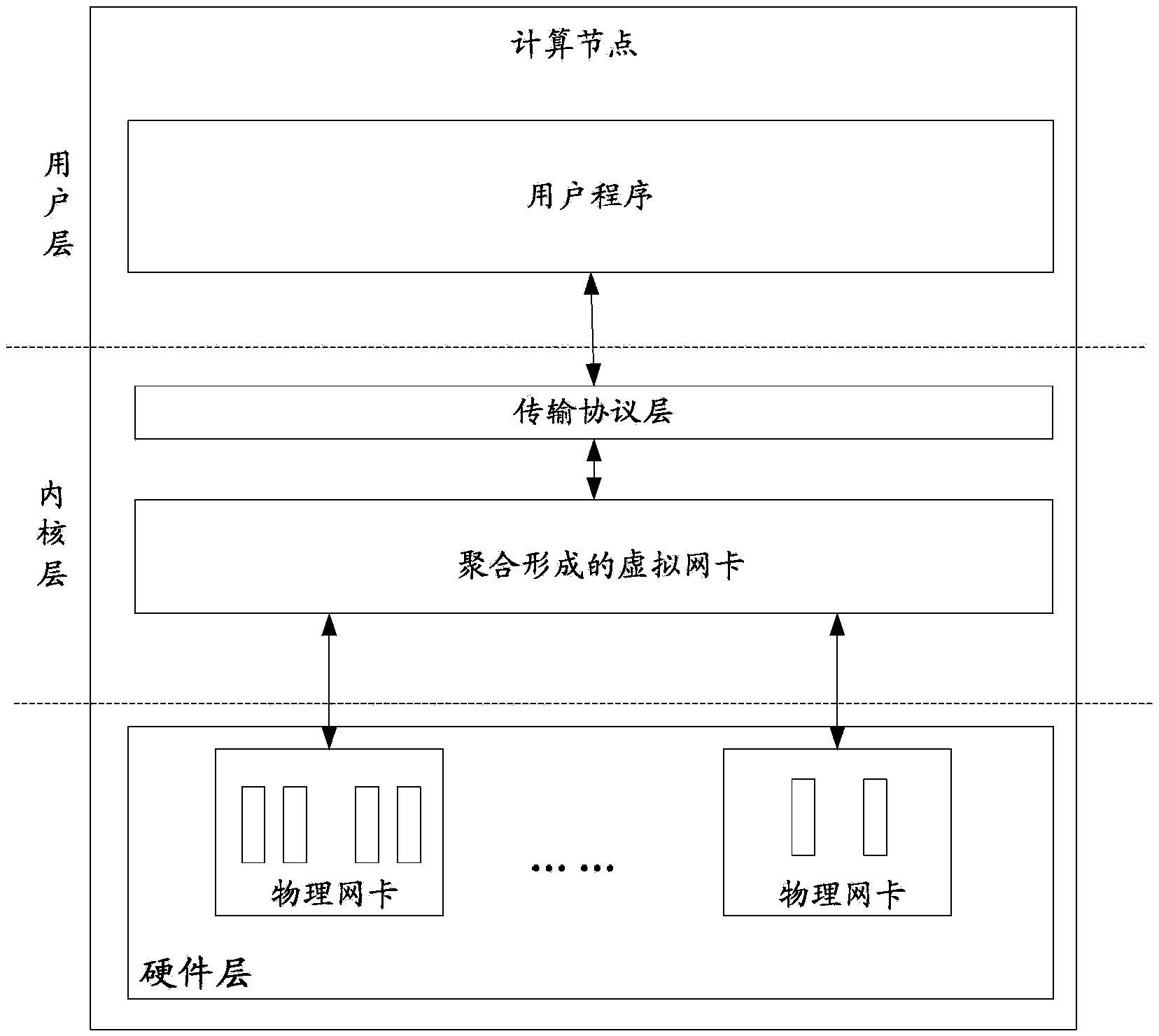
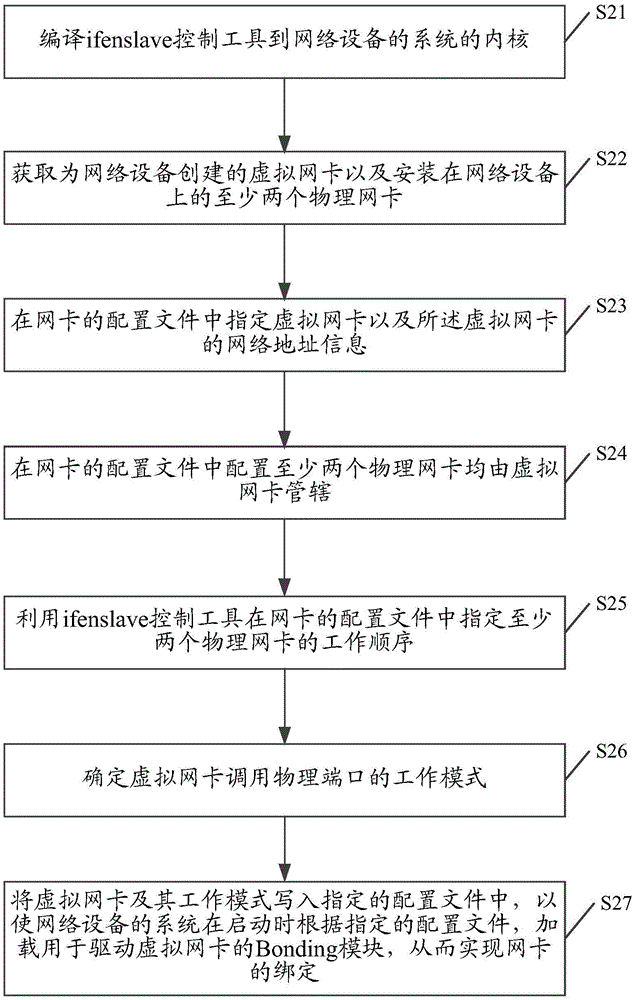
The invention discloses a network interface card binding method and device, and aims at improving the reliability of network equipment. The method comprises that a virtual network interface card created for network equipment and at least two physical network interface cards installed in network equipment are obtained; a control tool ifenslave is used to control the virtual network interface card to use the at least two physical network interface cards as physical ports; a work mode that the virtual network interface card calls the physical port is determined; and the virtual network interface card and the work mode thereof are written in a specified configuration file, so that when being started, a system of the network equipment loads a bonding module for driving the virtual network interface card according to the specified configuration file. Thus, the network interface card is bound.
Owner:TVMINING BEIJING MEDIA TECH
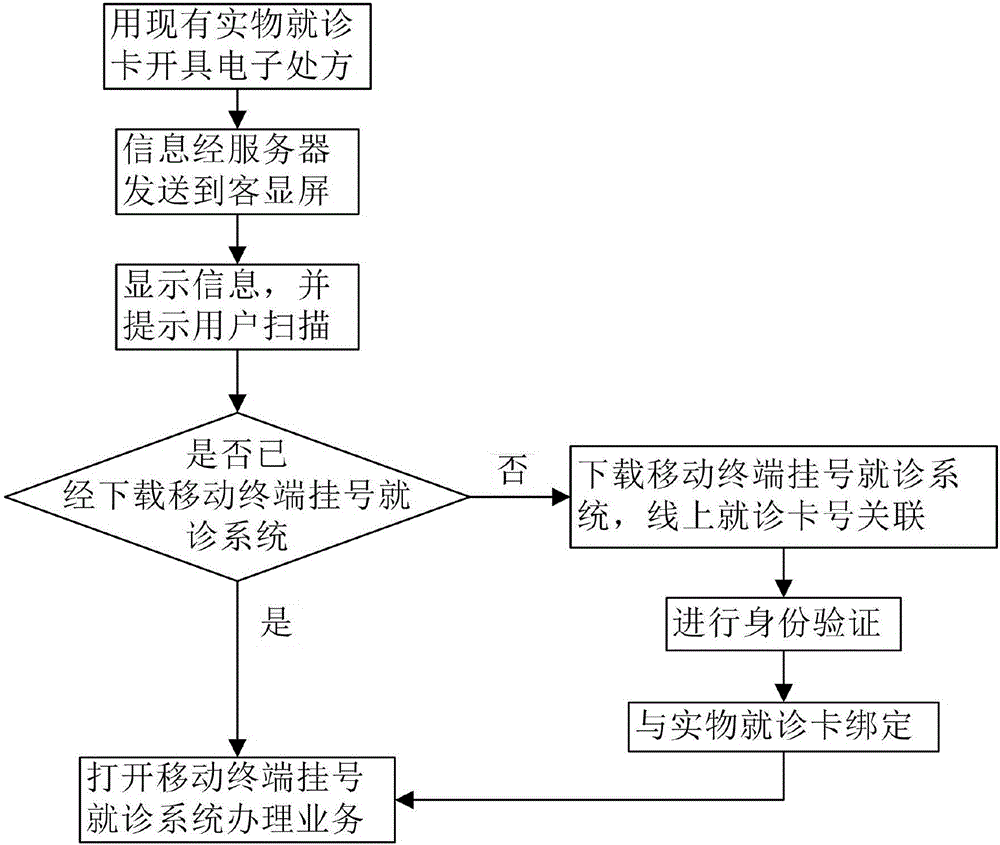
Medical customer display, medical system and methods
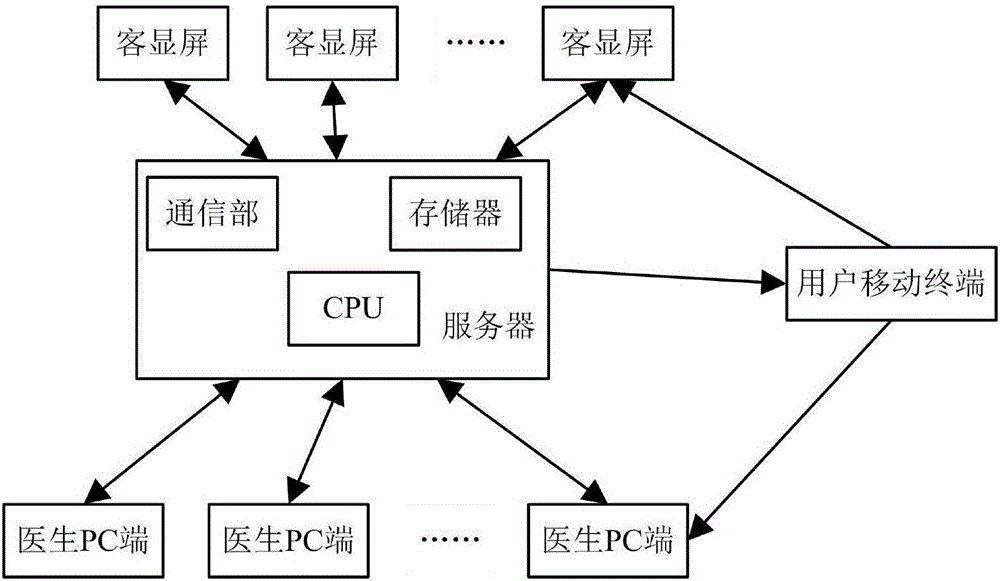
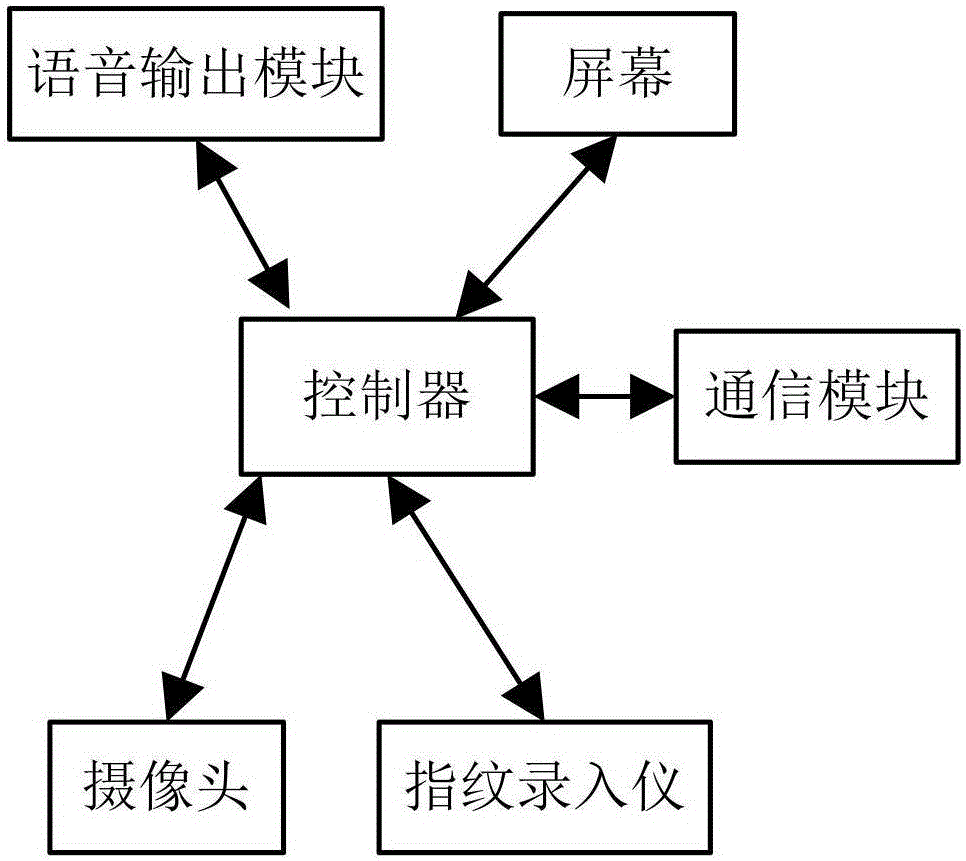
ActiveCN106355533ARealize the bindingWith "card reader" functionReservationsChecking apparatusPaymentLiquid-crystal display
The invention relates to a medical customer display, medical system and methods. The customer display comprises a controller and a liquid crystal display and is characterized by further comprising a communication module, a camera, an internal horn and a fingerprint entry instrument, wherein the liquid crystal display is used for displaying generated treatment information such as a two-dimensional code and the like to a user and allowing the user to scan and pay attention to the information or browse own treatment information at site; the communication module communicates with the server or an external terminal and is used for transmitting data; the camera is used for screening the electronical two-dimensional code generated by a mobile terminal for registration and payment of treatment fees and is also used for recognizing user facial features; the fingerprint entry instrument is used for entering fingerprint information of the user; the horn is used for broadcasting prompt information.
Owner:厦门飓浪信息技术股份有限公司
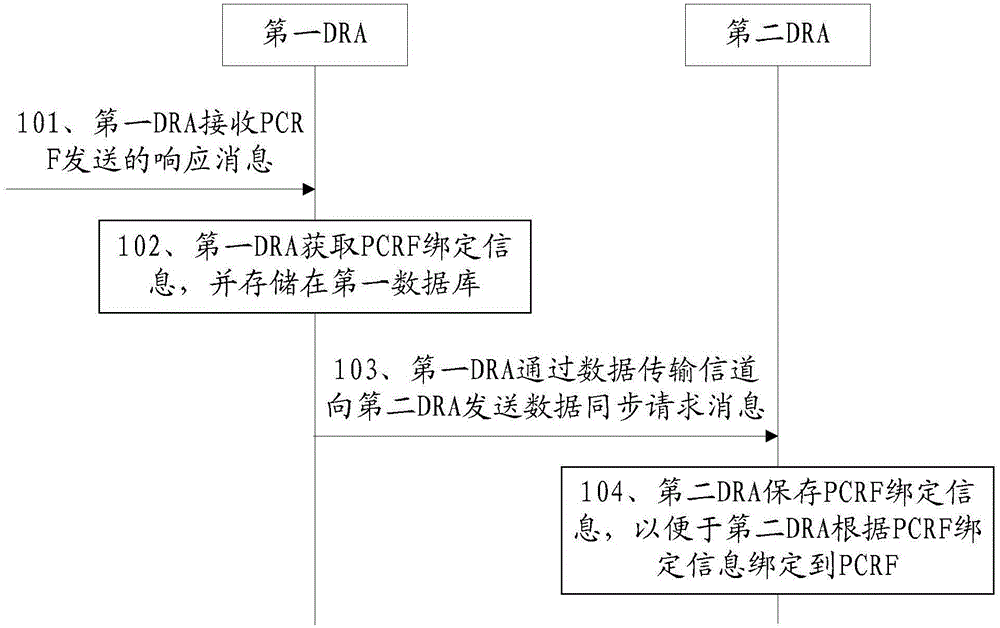
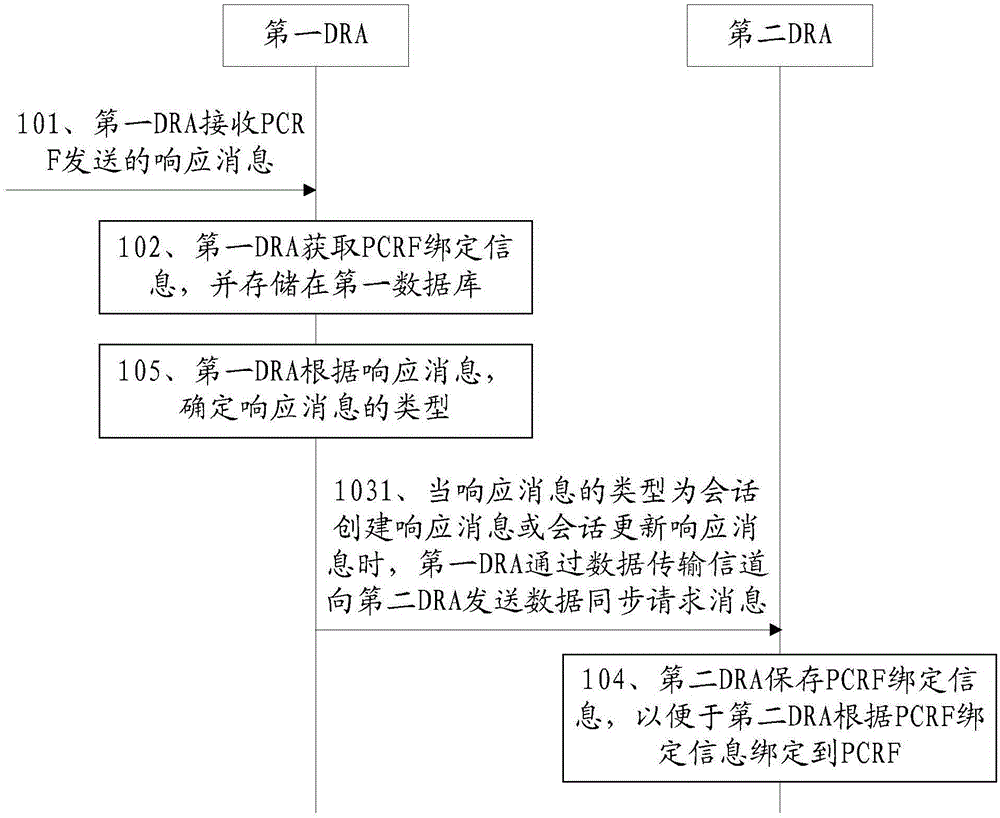
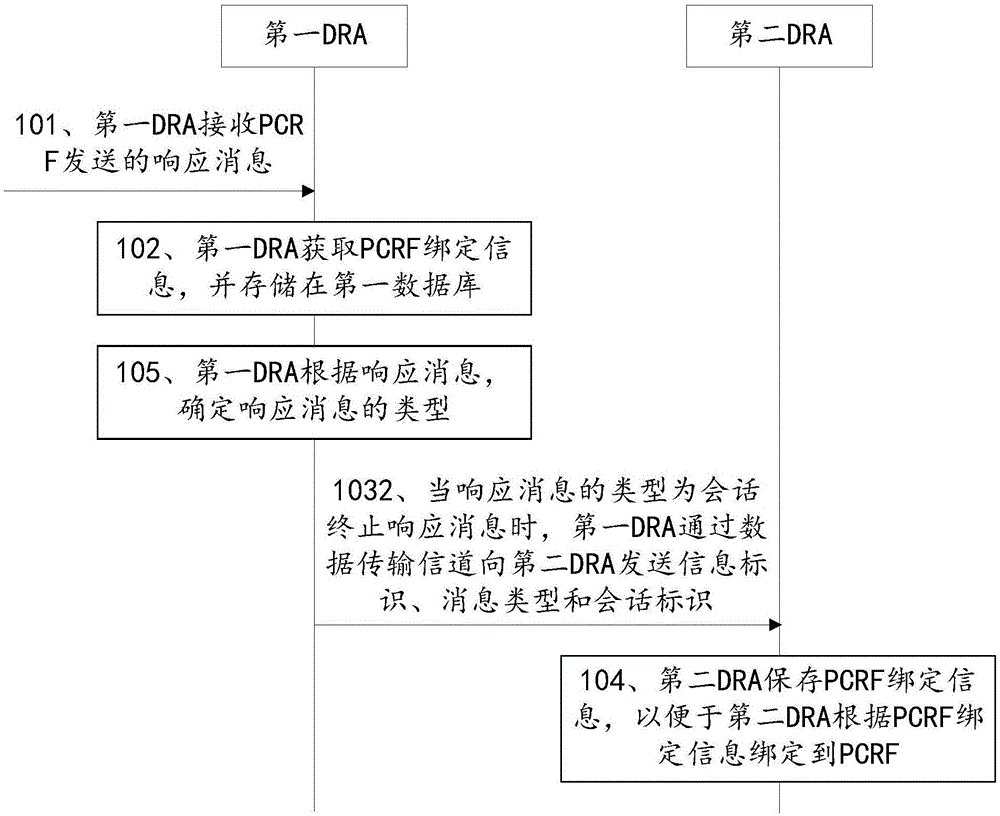
Session binding method and network system
InactiveCN105050072AConvenient bindingRealize the bindingAccounting/billing servicesNetwork data managementData synchronizationData transmission
The invention discloses a session binding method and a network system in an embodiment and relates to the technical field of communications. The session binding method is capable of realizing the binding of DRA2 and DRA1 to the same PCRF. The method of the embodiment comprises the following steps: the first DRA receives a response message sent by the PCRF, wherein the response message carries PCRF binding information; the first DRA obtains the PCRF binding information and stores the PCRF binding information in a first database; the first DRA sends a data synchronization request message to the second DRA via a data transmission channel, wherein the data synchronization request carries the PCRF binding information; and the second DRA saves the PCRF binding information so that the second DRA can be bound to the PCRF according to the PCRF binding information. The session binding method is suitable for a network system.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Binding method of intelligent equipment, identity authentication platform and storage medium
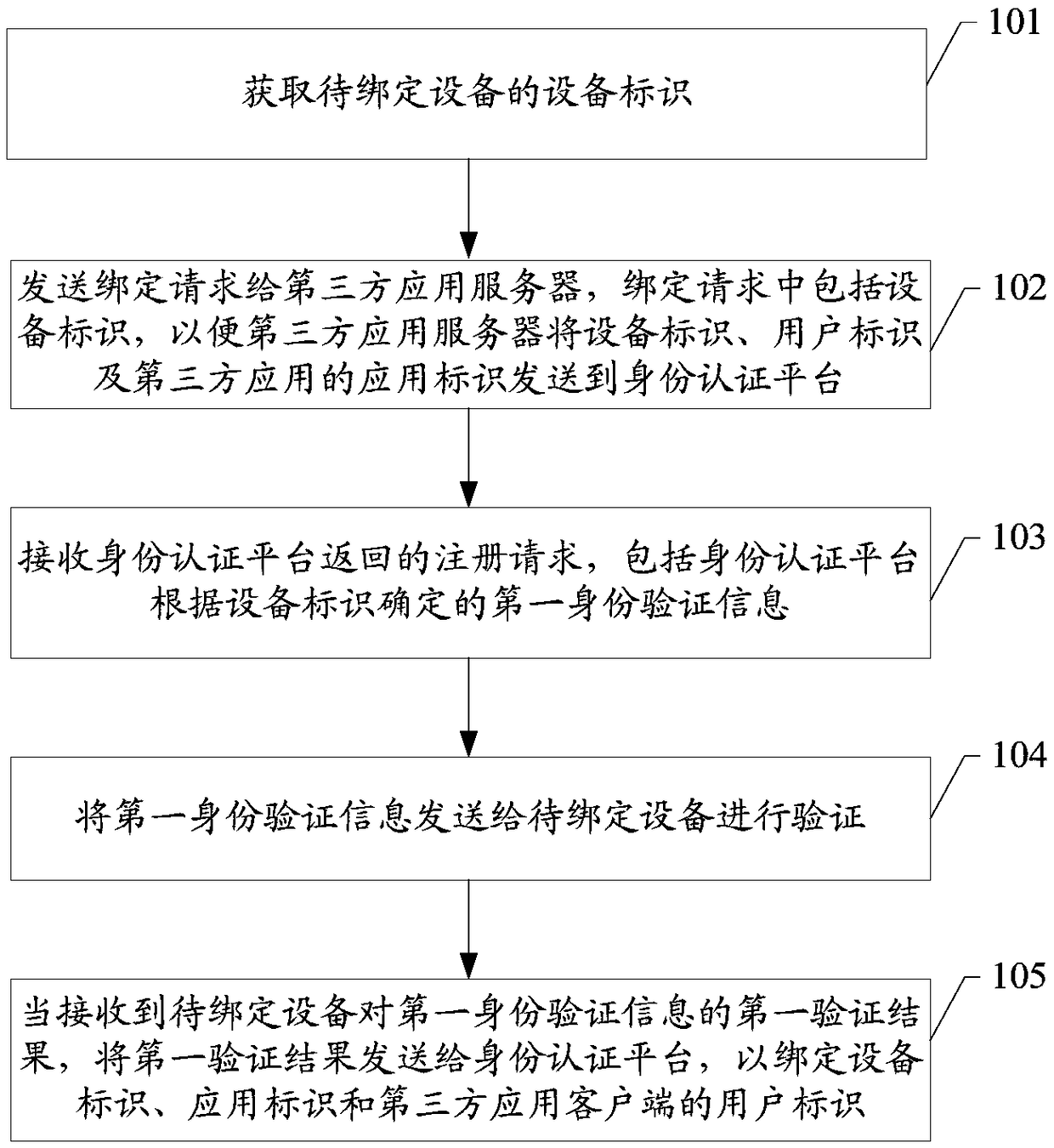
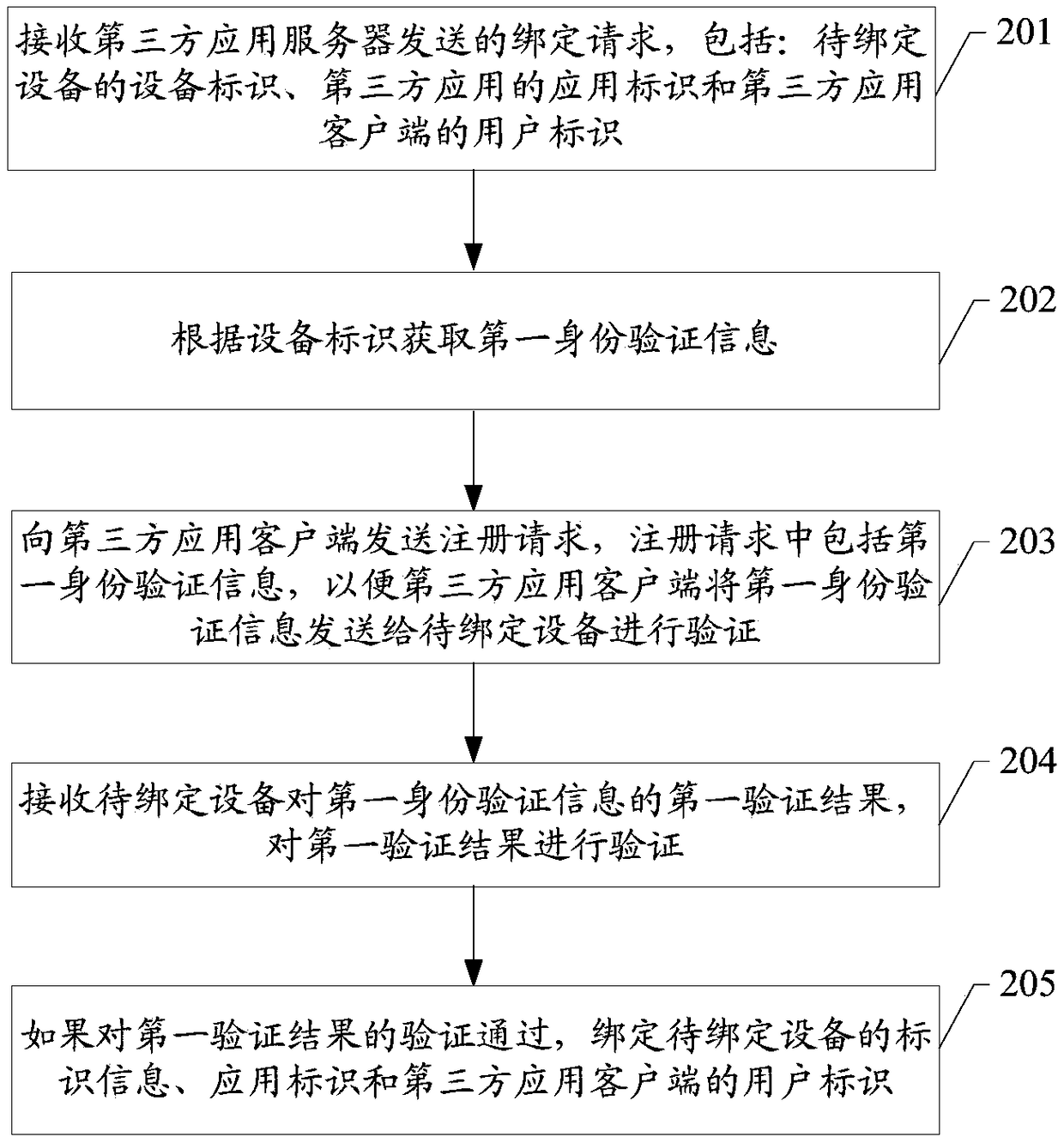
ActiveCN108768970AImprove securityRealize the bindingUser identity/authority verificationTotal factory controlClient-sideApplication server
The embodiment of the invention discloses a binding method of intelligent equipment, an identity authentication platform and a storage medium applied to the technical field of the information processing. When a user initiates a binding request to to-be-bound equipment through a third-party application client, the third-party application client sends an equipment identifier of the to-be-bound equipment, a user identifier and an application identifier of a third-party application to the identity authentication platform through a third-party application server; when the third-party application client receives a registration request returned by the identity authentication platform, first identity verification information in the registration request is sent to the to-be-bound equipment to verify, and then the first verification result of the first identity verification information is sent to the identity authentication platform, thereby binding the equipment identifier, the application identifier and the user identifier of the third-party application client. Therefore, the binding between the equipment identifier and the user of the third-party application is realized through the transmission among the identity authentication platform, the third-party application client and the to-be-bound equipment.
Owner:TENCENT TECH (BEIJING) CO LTD
Access control system and method for implementing binding MAC/IP of network device
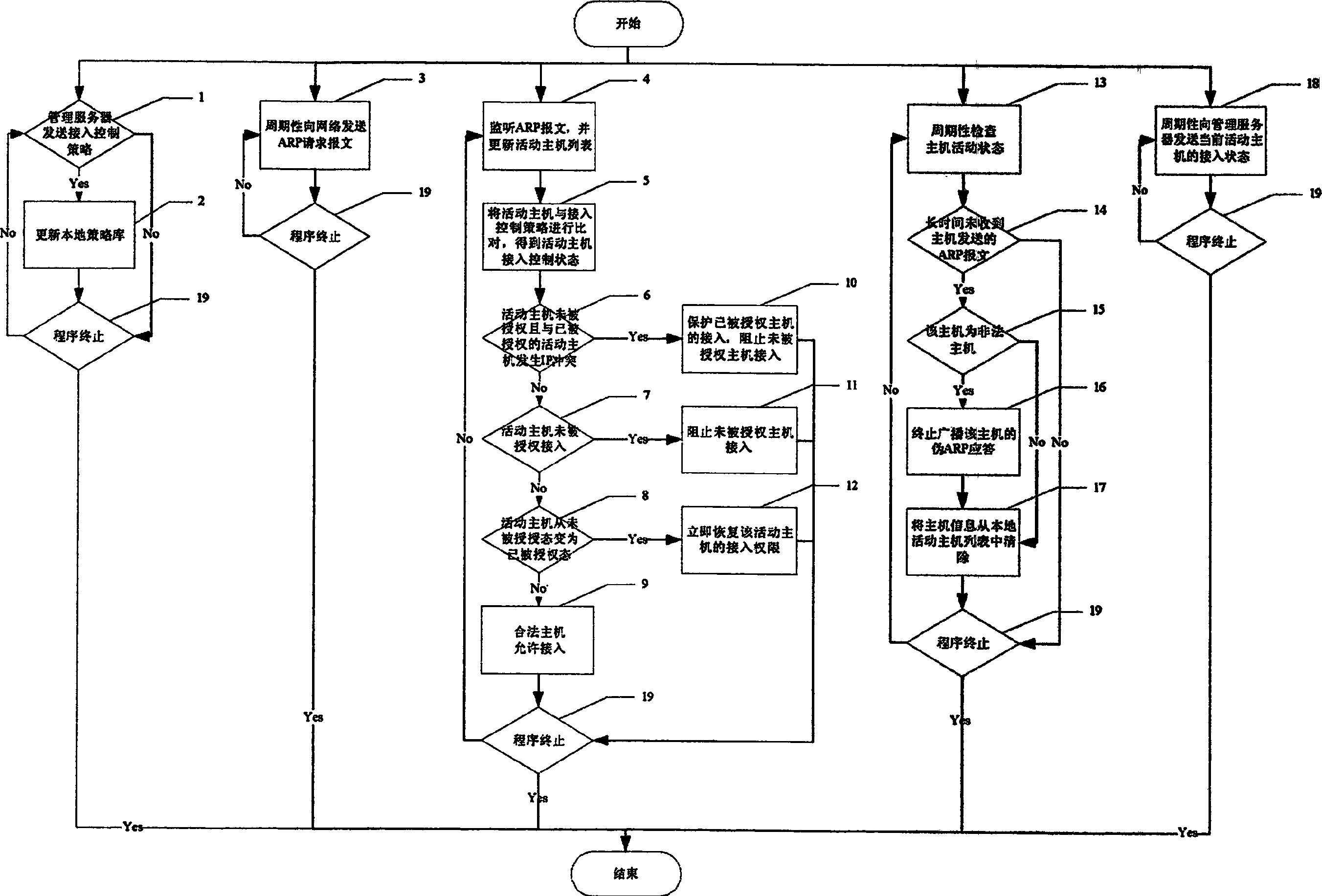
ActiveCN1874223ASave moneyEasy to implementUser identity/authority verificationData switching by path configurationIp addressStructure of Management Information
The system includes access control equipment. Through network wire, network port of the access control equipment in the system is connected to port at any vacant network exchange in controlled sub network. Software for managing server and configuring client end in strategy is installed on any PC server or terminal in network. The method includes steps mainly: using broadcast of pseudo ARP response message periodically to inform all hosts in network co cause IP conflict of unauthorized host; meanwhile, using pseudo MAC to refresh ARP buffer of each host in network to prevent communication between authorized host and unauthorized host so as to realize binding MAC / IP addresses. Without need of replacing any existed network equipment, and carrying out any adjustment for structure of network, the invention possesses advantages of saving large funds, easy of implementation, small maintenance work. The invention is applicable to enterprises and institutions of using computer and Ethernet.
Owner:CHINA MOBILE COMM CORP TIANJIN
School finance service management system
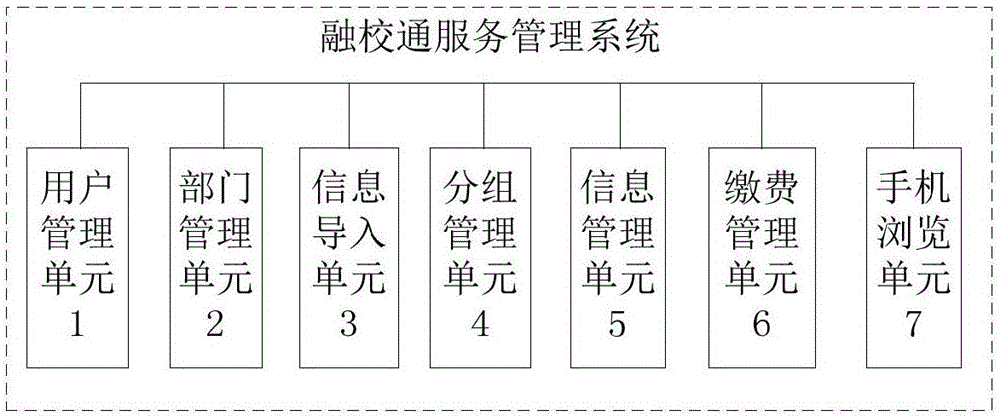
InactiveCN106651703ARealize the bindingData processing applicationsCo-operative working arrangementsPaymentManagement unit
The invention discloses a school finance service management system. The school finance service management system comprises a user management unit, a department management unit, an information import unit, a grouping management unit, an information management unit, a payment management unit and a mobile browsing unit, which are interconnected. The school finance service management system disclosed by the invention has the following beneficial effects: the flexible configuration for teachers to flexibly manage and communicate with a plurality of groups, classes or grades of students can be realized; the function that the effective information of the school website is released to the mobile phones of the teachers, the parents and the students simultaneously can be realized; the recharge for students by means of the bank financial cards can be realized; the reconciliation information and statistics of the payment information can be presented as required according to the needs of the school financial management; the binding of the system and the finance-e-union can be realized; and the real-time access and attendance management of the teachers and the students using mobile phones can be realized.
Owner:HEBEI LAIEN TECH
Method and system for implementing synchronous binding of safe secret keys
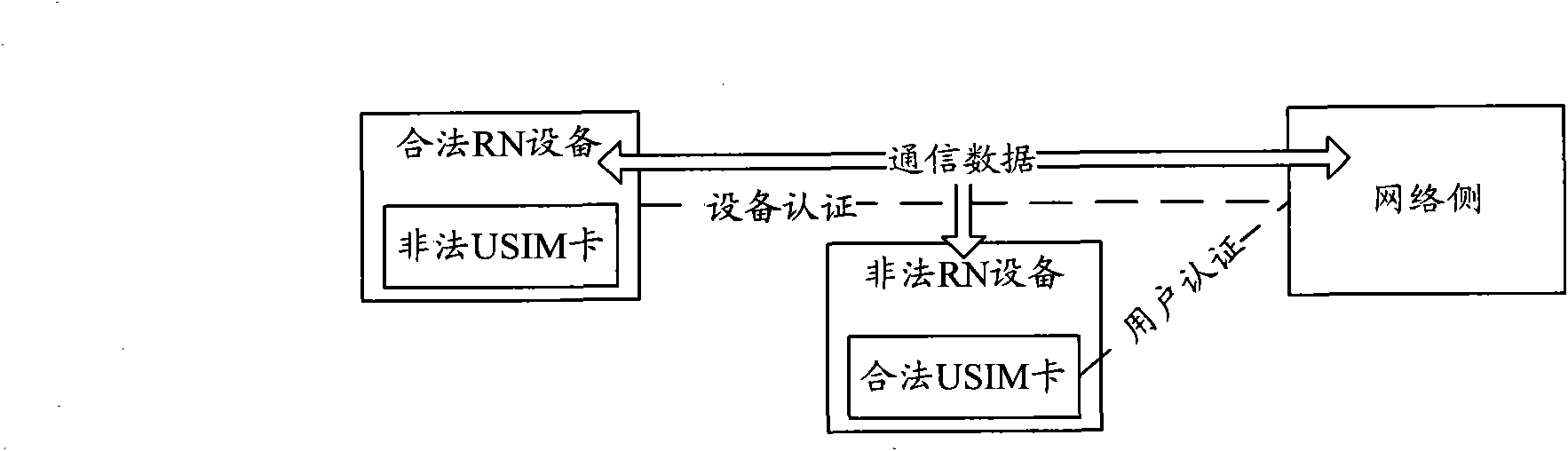
ActiveCN101945386AProtect communication data securityAchieve authenticationSecurity arrangementComputer security
The invention discloses a method and a system for implementing synchronous binding of safe secret keys, comprising the following steps: after an RN is identified by a user, an MME notifies the RN to carry out safe secret key binding; and after receiving the notification, the RN carries out safe secret key binding the same as that of the network side to acquire the safe secret key bound with the equipment, and response to the MME. By the method of the invention, the safe secret key bound with the equipment obtained by the safe secret key binding, or other secret keys which are bound with the equipment and derived from the safe secret key are utilized, thus ensuring the communication data safety between the RN and the network side; and by means of the safe secret key bound with the equipment, the RN user identification and the equipment binding are realized and the RN communicated with the network side is ensured to be a legal RN with a legal USIM card, thus an illegal attacker can not decode the communication data.
Owner:ZTE CORP
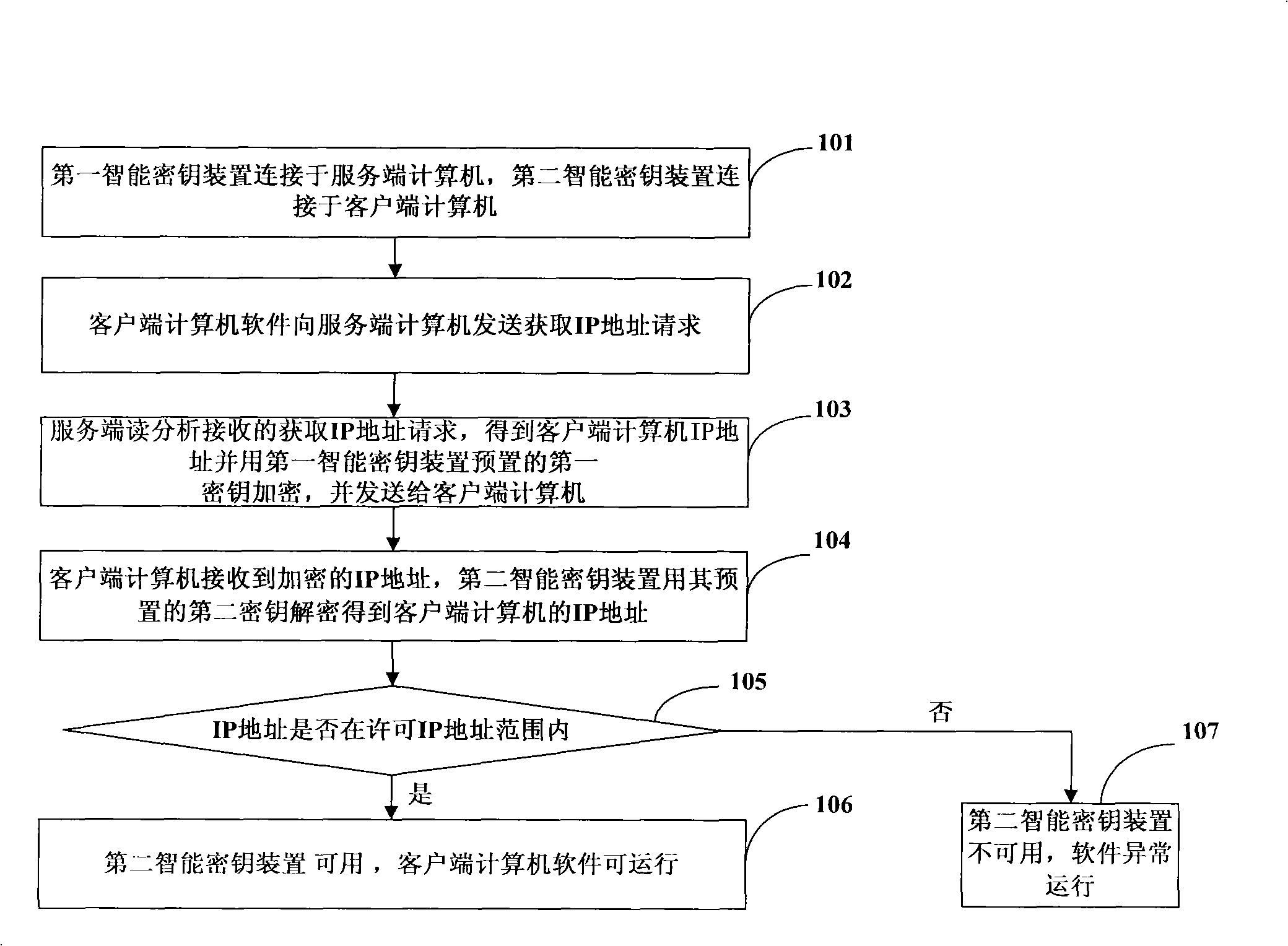
Method for protecting computer software
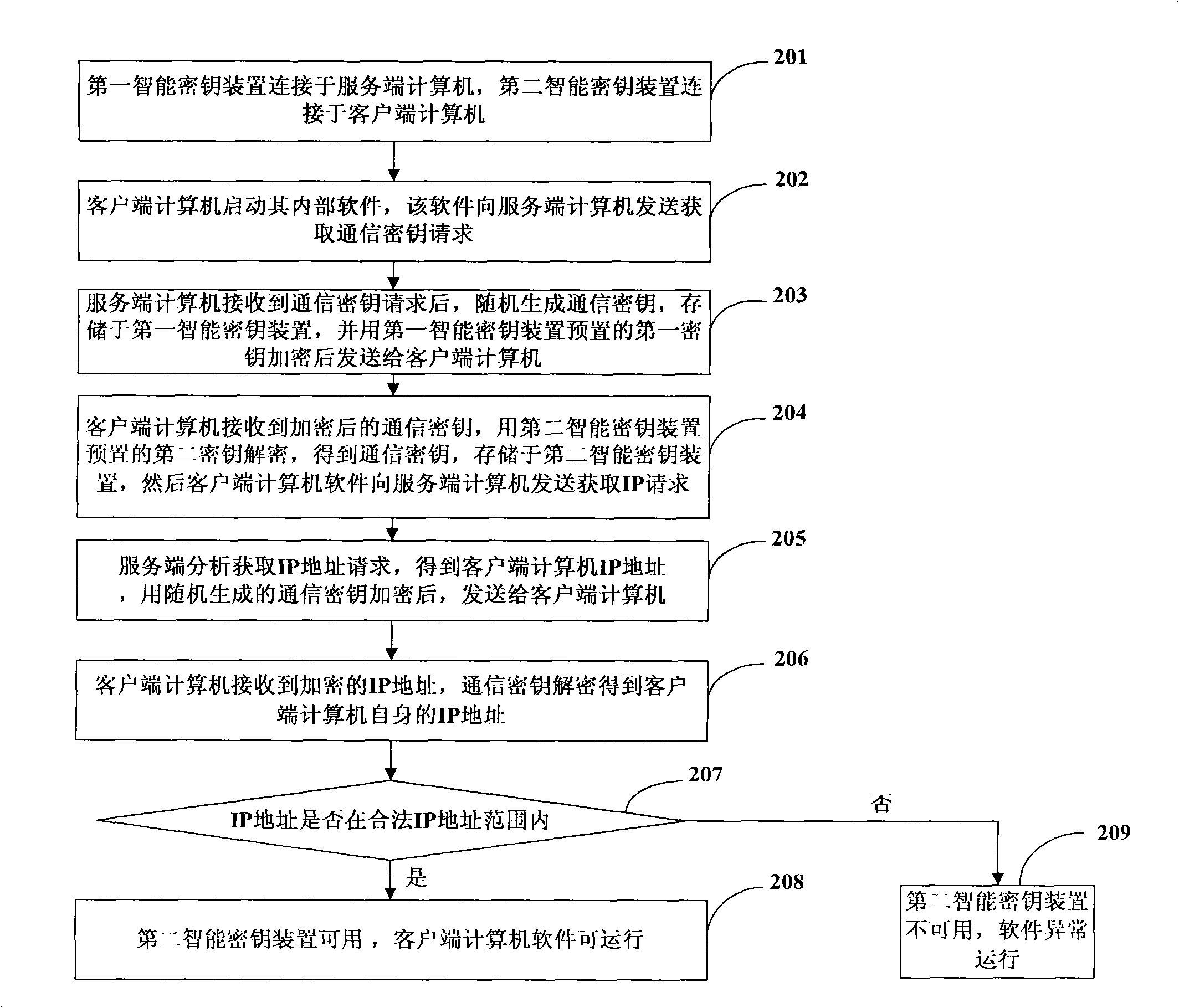
ActiveCN101539977AIncrease the difficulty of crackingRealize the bindingTransmissionProgram/content distribution protectionIp addressSoftware protection
The invention discloses a method for protecting computer software and belongs to the technical field of information security. The technical proposal is that a first intelligent cipher key device is connected with a server computer; a second intelligent cipher key device is connected with a client computer; the client computer starts up the software installed inside the client computer; the software transmits an IP address obtaining request to the server computer; the server computer analyses the IP address obtaining request, obtains the IP address of the client computer, and transmits the IP address to the client computer after the IP address is encrypted by the first intelligent cipher key device; the client computer receives the encrypted IP address, judges whether the IP address is a legal IP address after the IP address is decrypted by the second intelligent cipher key device, if so, the second intelligent cipher key device is available, otherwise, the second intelligent cipher key device is unavailable. The invention improves the security of client software, and synchronously, the invention transfers the IP address after the IP address is encrypted so as to further improve software decryption difficulty.
Owner:FEITIAN TECHNOLOGIES
Resource scheduling allocation method, computer system and super-fusion architecture system
ActiveCN108196958ASecure available resourcesReduce resource contentionResource allocationVirtual memoryComputerized system
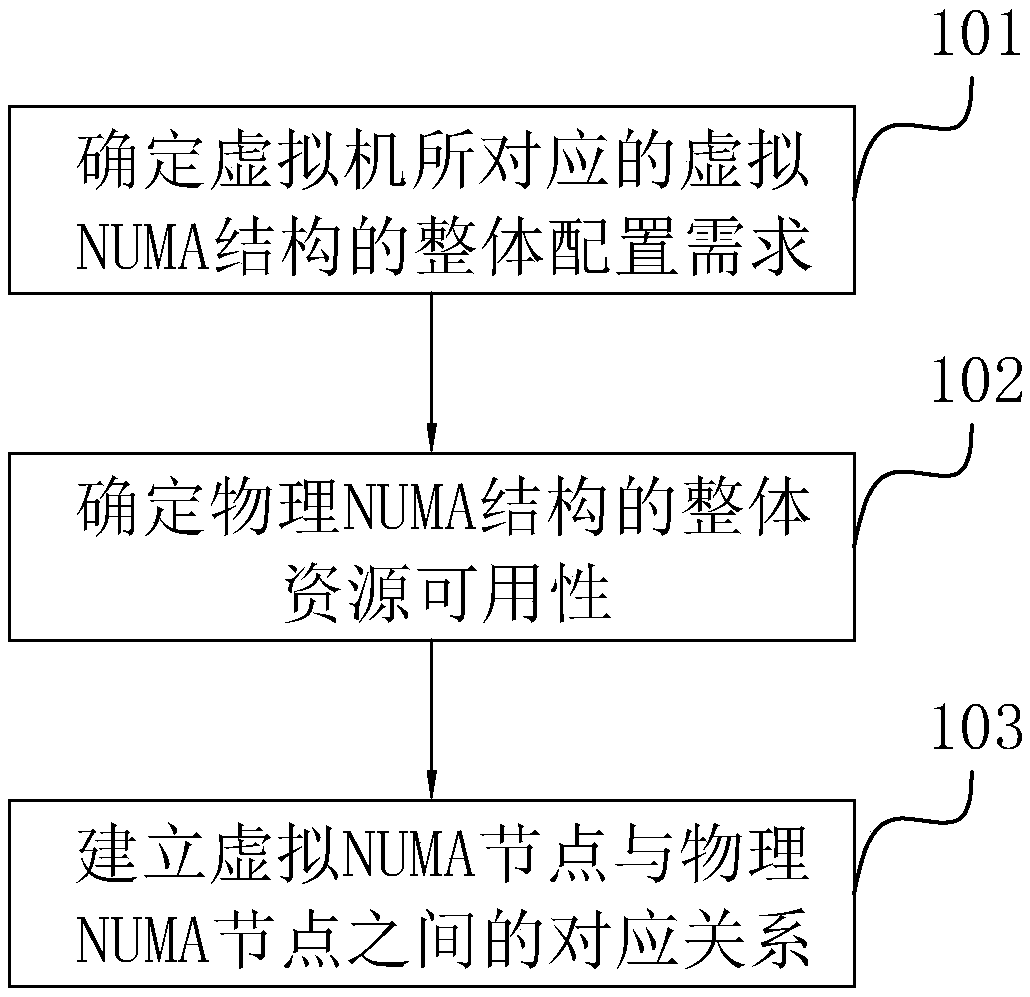
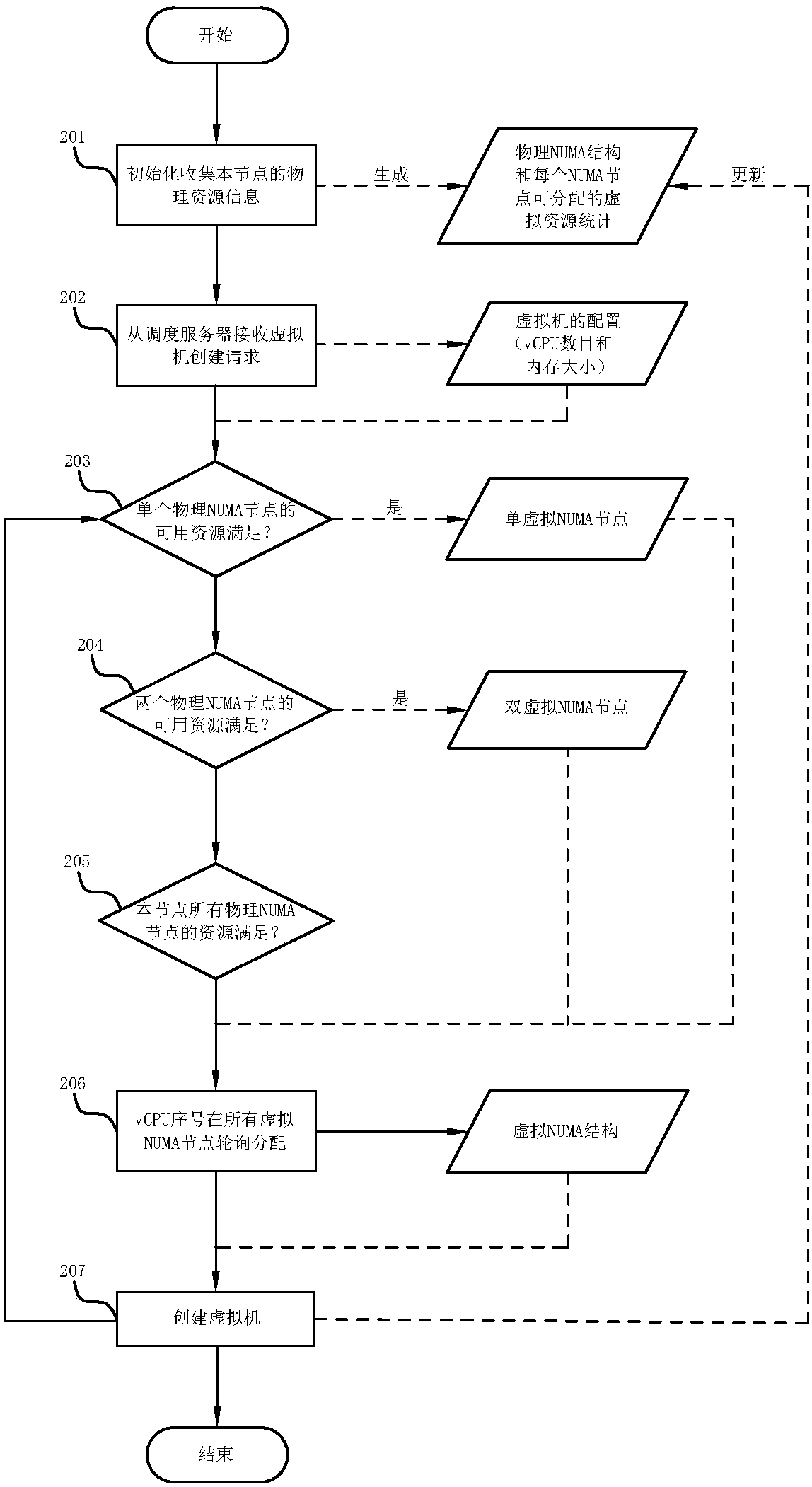
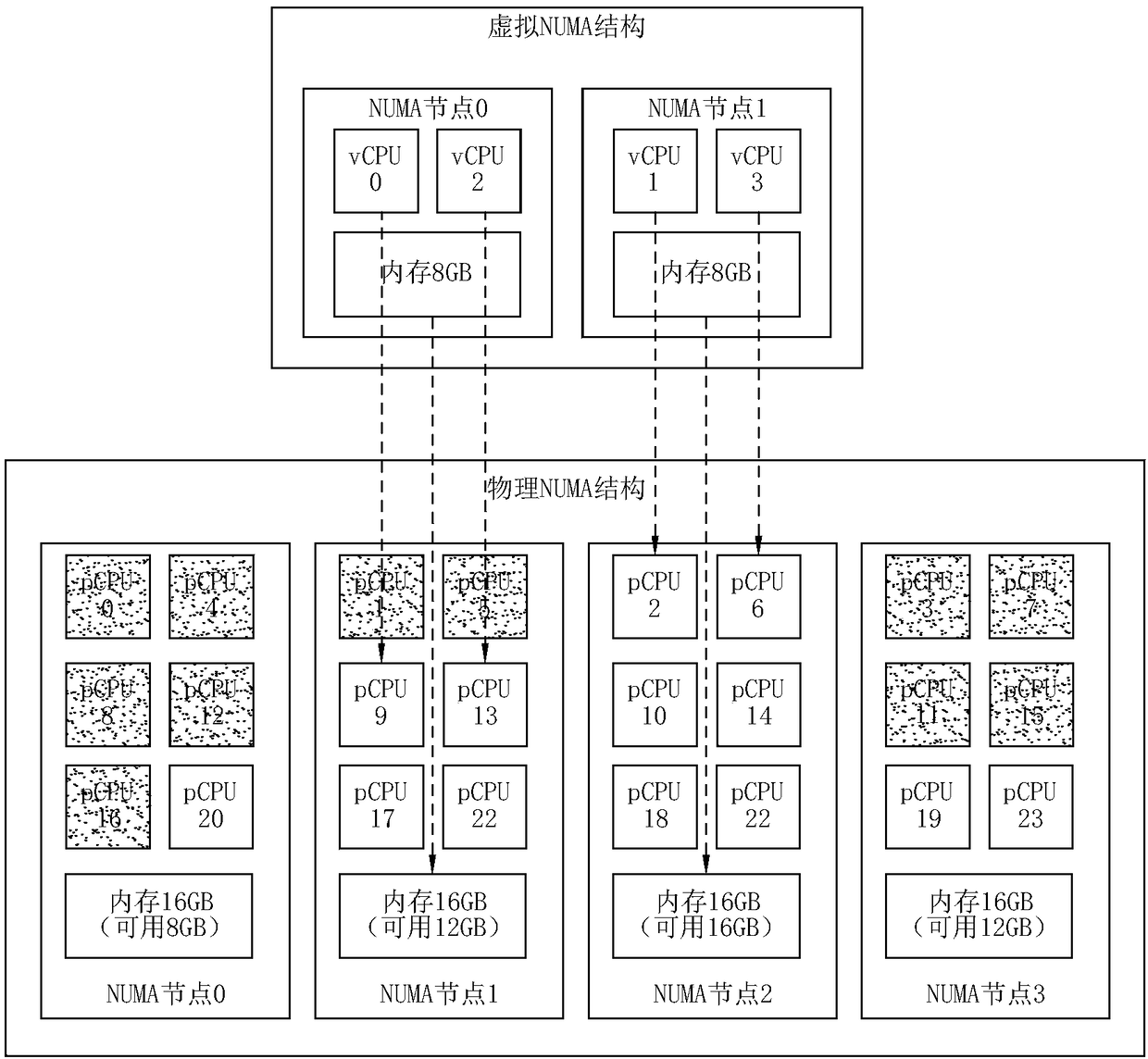
The invention relates to a resource scheduling allocation method, a computer system and a super-fusion architecture system. The resource scheduling allocation method comprises the steps of determiningan overall configuration demand of a virtual NUMA structure corresponding to a virtual machine, wherein the overall configuration demand comprises sub-configuration demands of a virtual NUMA node, and the sub-configuration demands include a first configuration demand for a virtual CPU core and a second configuration demand for a virtual memory; determining overall resource availability of a physical NUMA structure, wherein the overall resource availability comprises sub-resource availability of a physical NUMA node, and the sub-resource availability includes first resource availability for aphysical CPU core and second resource availability for a physical memory; and based on the overall configuration demand and the overall resource availability, establishing a corresponding relationshipbetween the virtual NUMA node and the physical NUMA node. The resource scheduling allocation method realizes mapping and binding of the virtual NUMA structure and the physical NUMA structure, so thatphysical resources are reasonably allocated.
Owner:武汉泽塔云科技股份有限公司
Configuration method and system for realizing port address binding
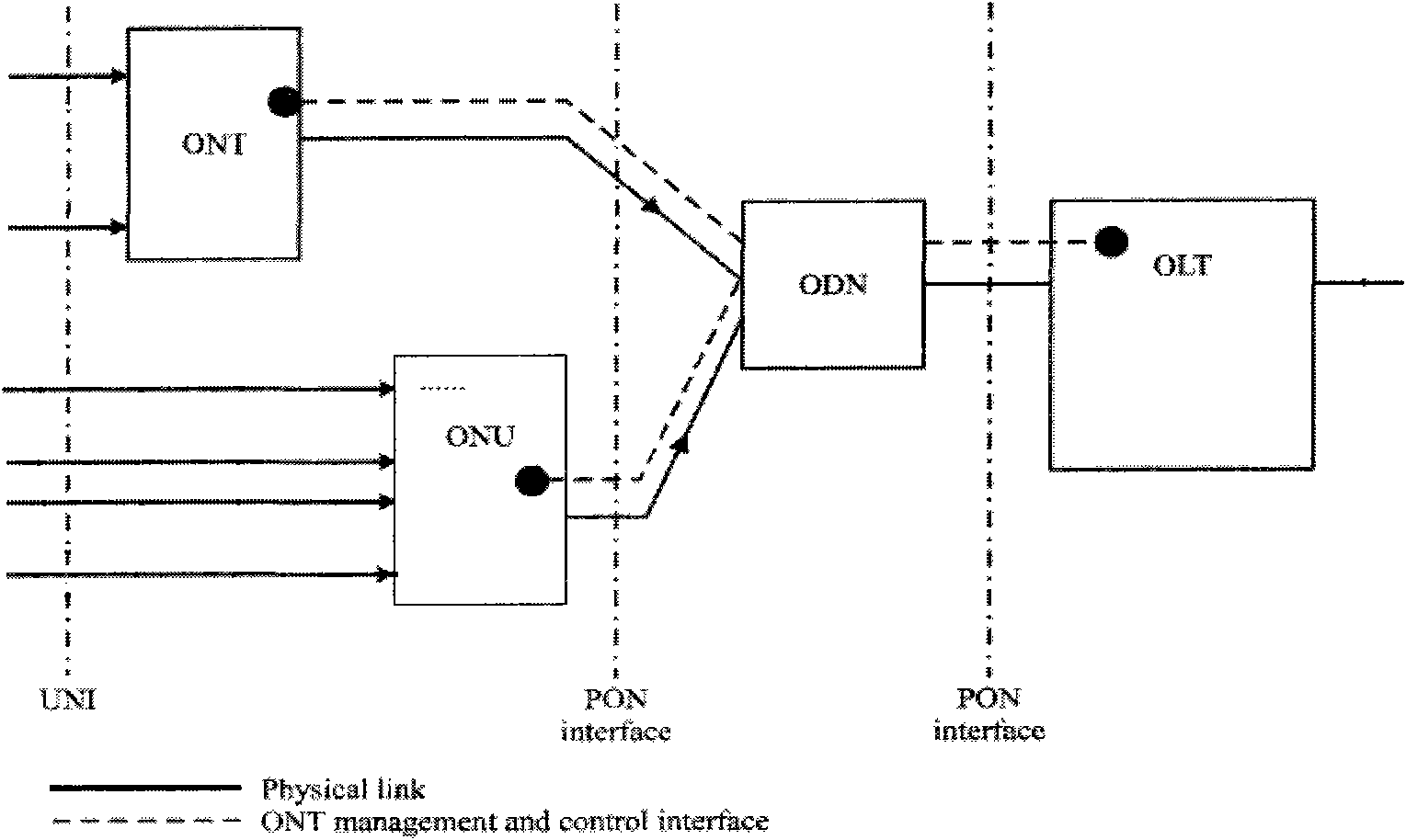
ActiveCN101888575ARealize the bindingEasy to controlMultiplex system selection arrangementsTransmissionIp addressOptical network terminal
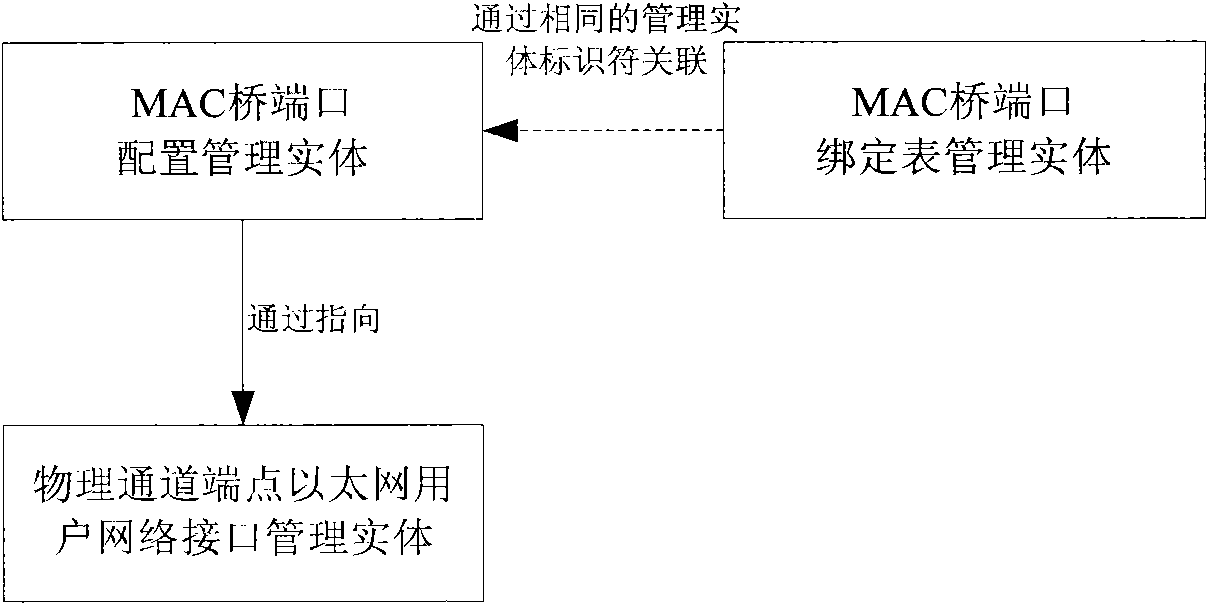
The invention discloses a configuration method and a configuration system for realizing port address binding. The method comprises the following steps that: a management unit sets binding information comprising an IP address and an MAC address of a user host and an ethernet user port identifier and sends the binding information to an optical line terminal (OLT); the OLT generates a configuration message comprising the IP address, the MAC address and a management entity identifier according to the binding information and sends the configuration message to an optical network unit (ONU) or an optical network terminal (ONT), wherein the management entity identifier corresponds to the ethernet user port identifier; and according to the received configuration message, the ONU or ONT writes the IP address and the MAC address into a binding table appointed by the management entity identifier of an MAC bridge port binding table management entity. The configuration method and the configuration system have flexible configuration and can realize complete control over user rights and improve the safety of a user network.
Owner:浙江杭海新城控股集团有限公司
Message sharing method and client
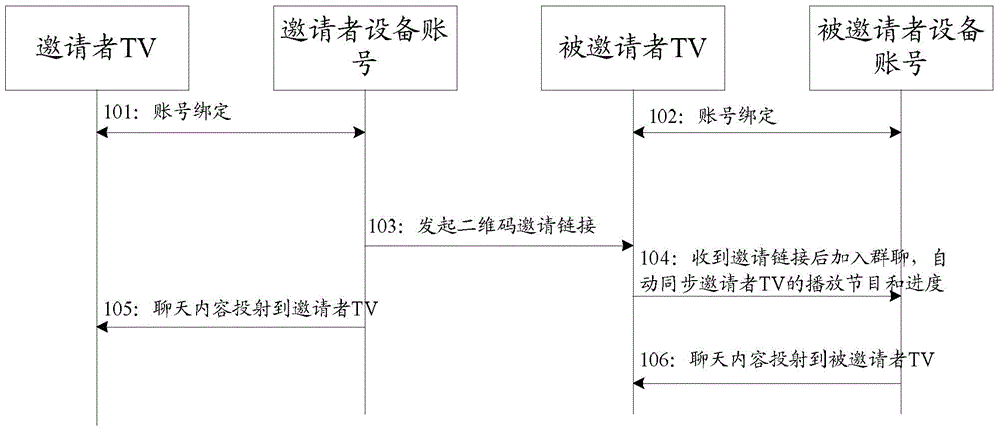
InactiveCN104954882ARealize the bindingRich viewing experienceSelective content distributionClient-side
The invention discloses a message sharing method and a client. The method comprises the following steps of building the association relationship between first electronic equipment and an equipment account; using the equipment account for controlling the first electronic equipment to play first multimedia data and sending an invitation link to a client corresponding to the second account; when the client corresponding to the second account receives the invitation link, using the equipment account for receiving second message data sent by the client corresponding to the second account, wherein the equipment account associated with the second account controls the corresponding second electronic equipment to synchronously play the first multimedia data; sending the second message data and the first message data sent by the client corresponding to the first account received by the equipment account to the first electronic equipment so that the message data is displayed on the first multimedia data.
Owner:TENCENT TECH (BEIJING) CO LTD
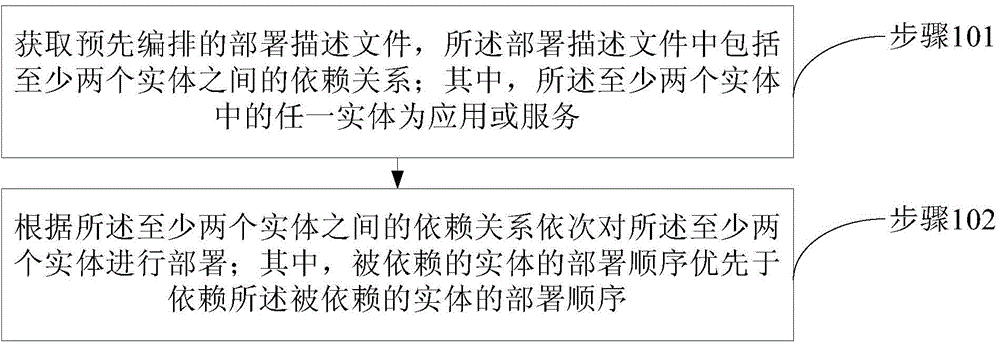
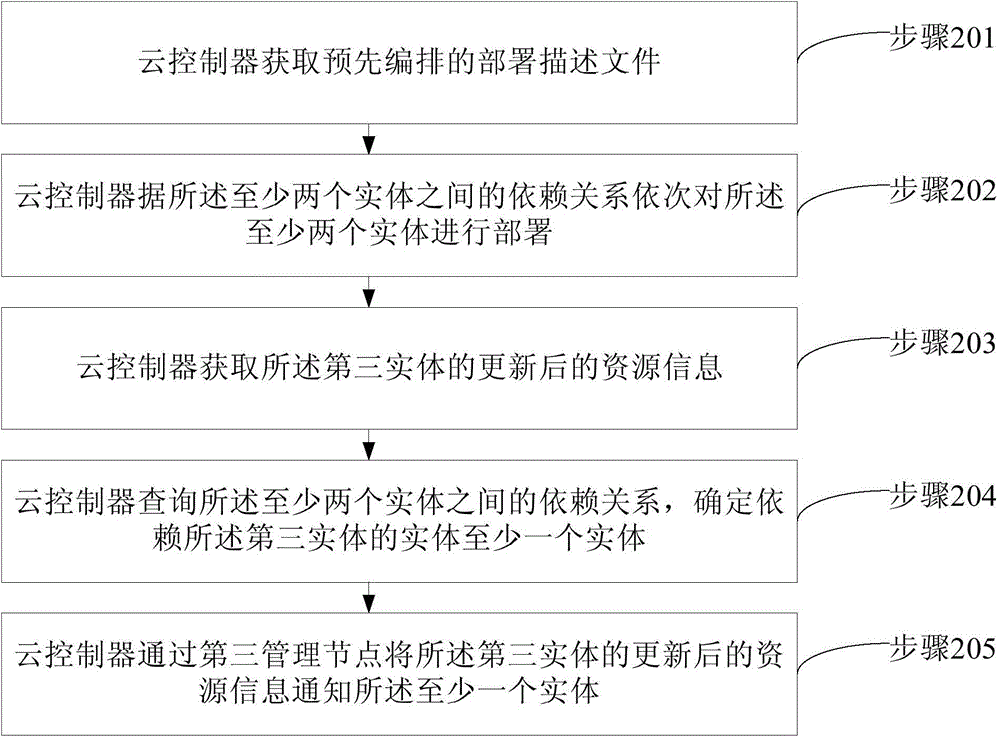
Deployment method and apparatus of applications and services
ActiveCN105704188ASolve the problem of not being able to inform dependentsRealize the bindingTransmissionDatabaseDependency relation
Owner:HUAWEI TECH CO LTD
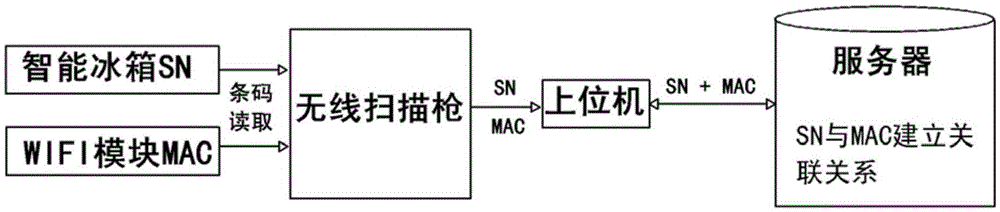
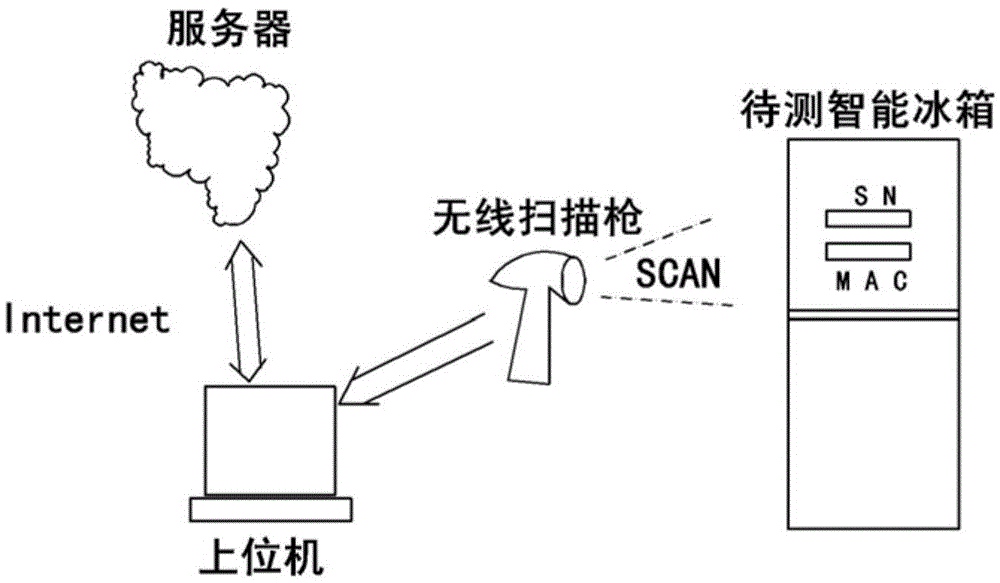
System and method for binding SN (Serial Number) of intelligent refrigerator with MAC (Media Access Control) address
InactiveCN105553575ARealize the bindingImprove test efficiencyTransmission monitoringSensing by electromagnetic radiationTest efficiencyThe Internet
The invention discloses a system and a method for binding an SN (Serial Number) of an intelligent refrigerator with an MAC (Media Access Control) address of a WIFI (Wireless Fidelity) module. The binding system comprises a server, an upper computer and a scanning gun, wherein the server is communicated with the upper computer through Internet; the upper computer is communicated with the scanning gun through a wireless network card; and the scanning gun is a wireless barcode reader. Through adoption of the binding system and method, binding of the SN of the intelligent refrigerator and the MAC address can be realized, so that the testing efficiency of the WIFI module is increased, and effective tracking of the WIFI module is ensured after a sale.
Owner:CHANGHONG MEILING CO LTD
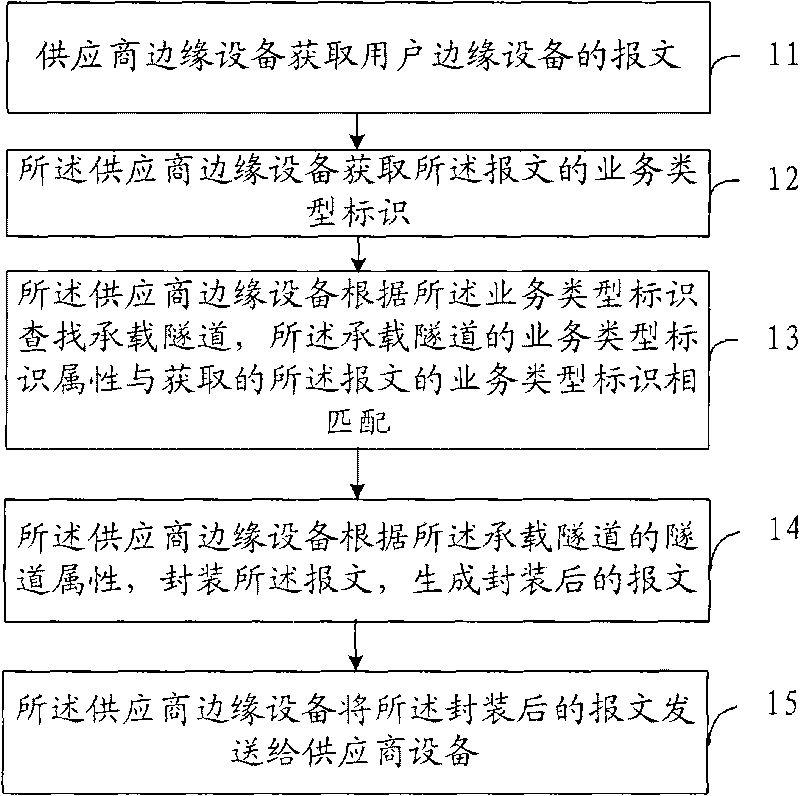
Method of Ethernet service accessing bearing tunnel, operator edge device and system
InactiveCN101702665AEasy to implementRealize the bindingNetworks interconnectionMessage serviceNetwork service
The invention provides a method of Ethernet service accessing bearing tunnel, an operator edge device and a system, which relates to the field of data communication and is designed for solving the technical problem that the binding method of Ethernet service and a bearing tunnel are complex to realize in the prior art. The method comprises: a supplier edge device obtains the message of a user edge device; the supplier edge device obtains the service type identification of the message; the supplier edge device searches the bearing tunnel according to the service type identification; the service type identification property of the bearing tunnel is matched with the obtained message service type identification; the supplier edge device packages the message according to the tunnel property of the bearing tunnel to generate a packaged message. The invention can bind the Ethernet network service with the bearing tunnel and is easy to realize.
Owner:ZTE CORP
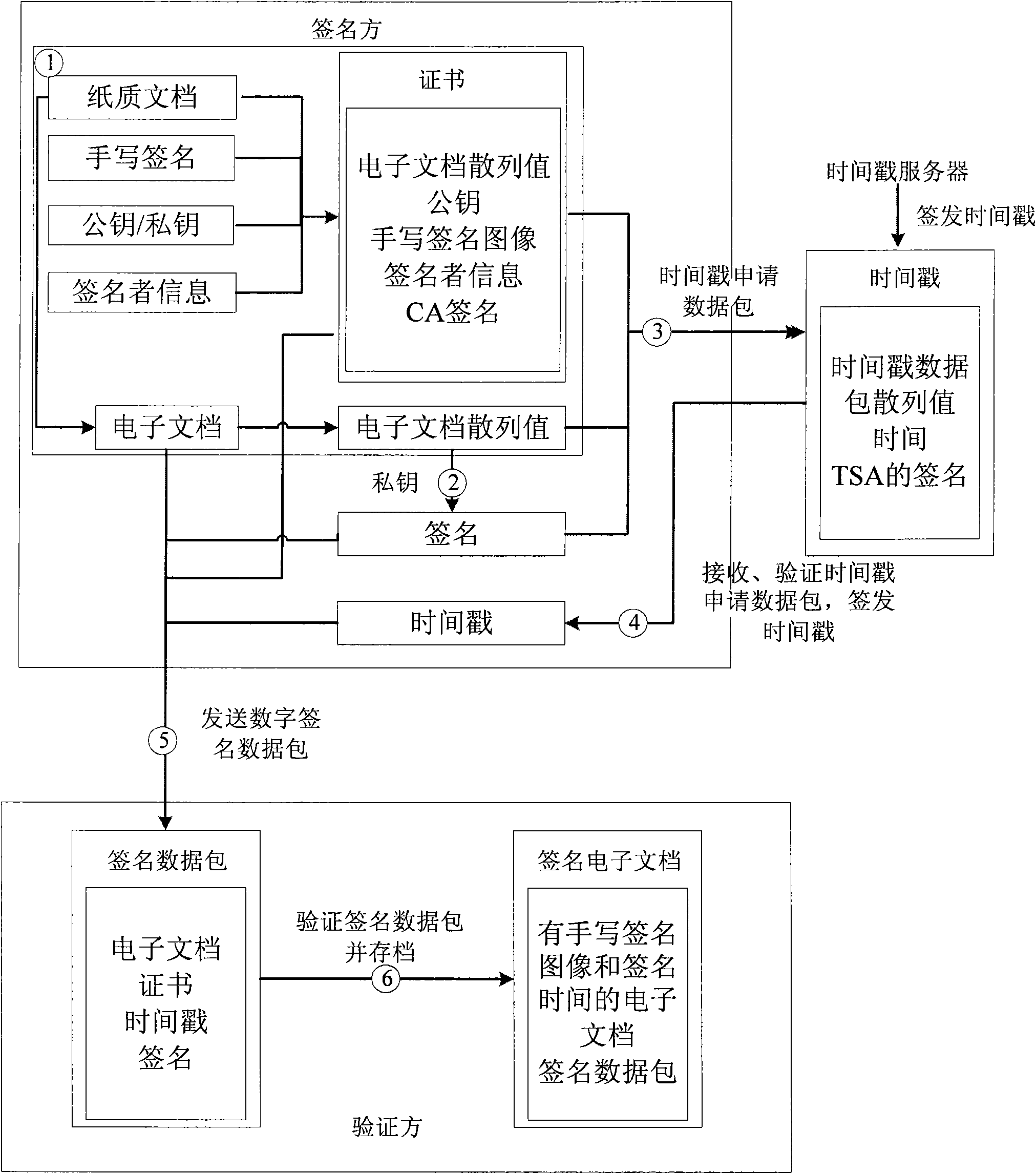
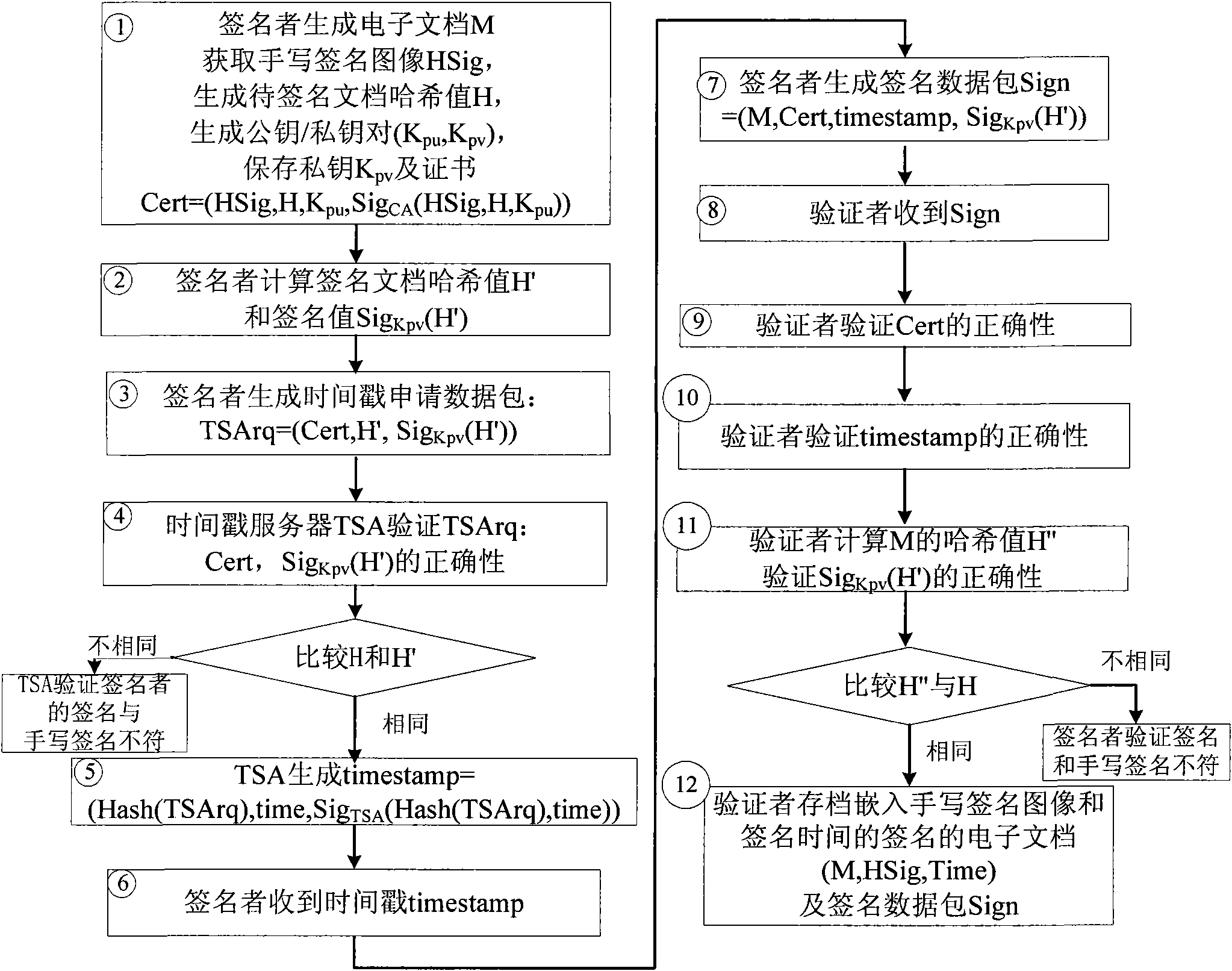
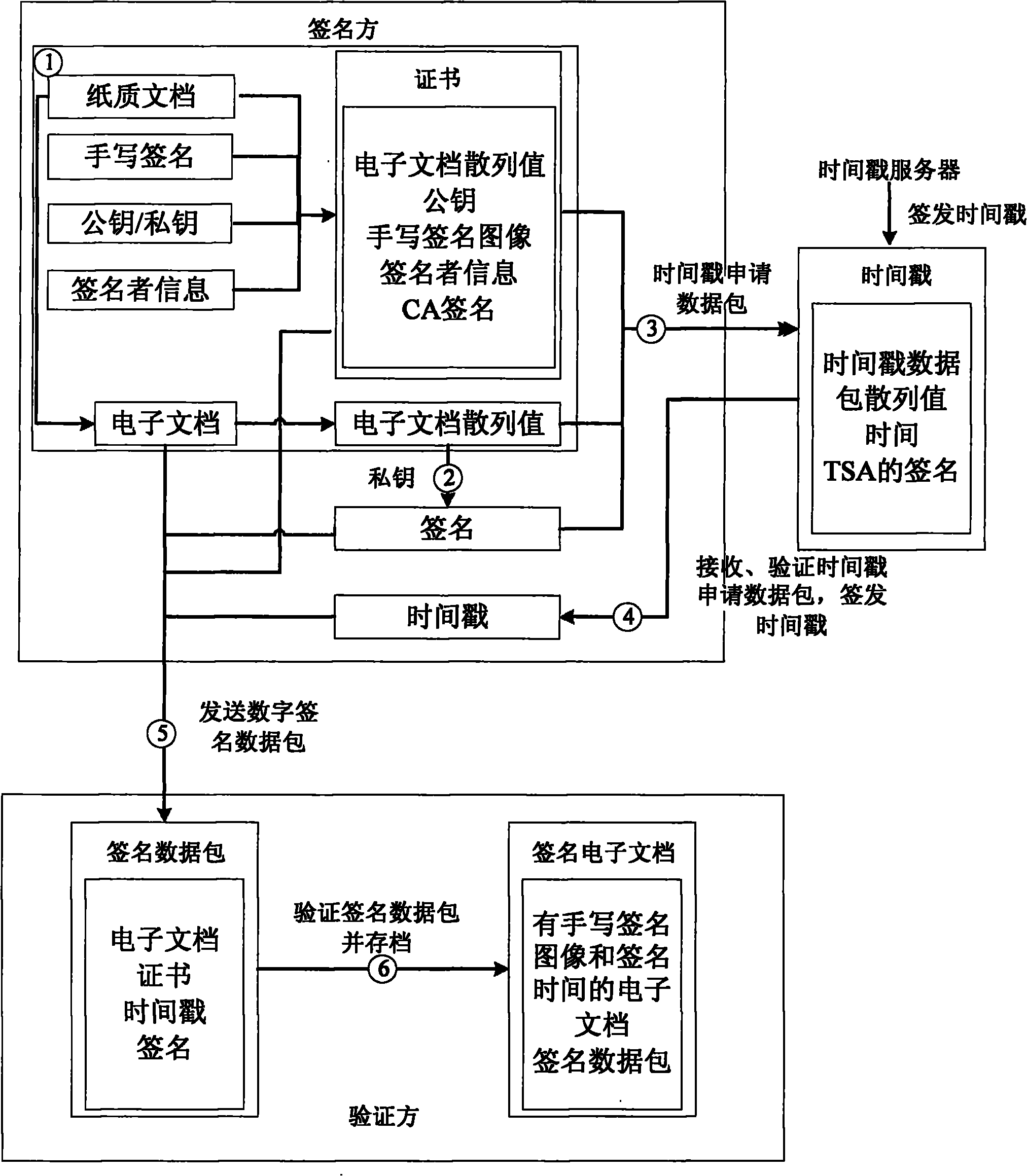
Method for digital signatures capable of establishing reliable correspondence with handwritten signatures
ActiveCN101931631AClear signature timeReliable correspondenceUser identity/authority verificationElectronic documentDigital signature
The invention relates to a method for digital signatures capable of establishing reliable correspondence with handwritten signatures, in particular to a method for signing digitally on electronic documents corresponding to the handwritten signatures based on a digital certificate for limiting signature contents. In the method, the electronic documents with the digital signatures can be generated while signers write the signatures on paper documents; and the digital signatures of the electronic documents and the handwritten signatures have the characteristics of one-to-one correspondence and non-repudiation.
Owner:BEIJING CERTIFICATE AUTHORITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com