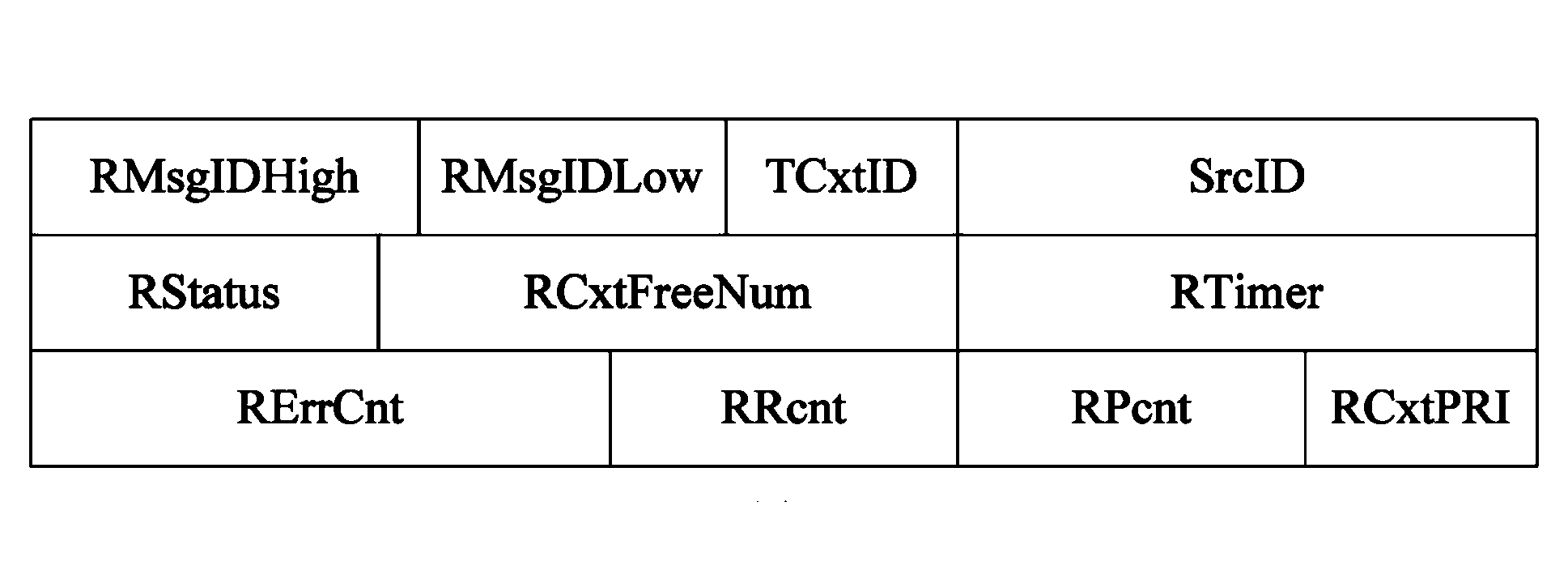
Patents
Literature
176 results about "Virtual network interface card" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
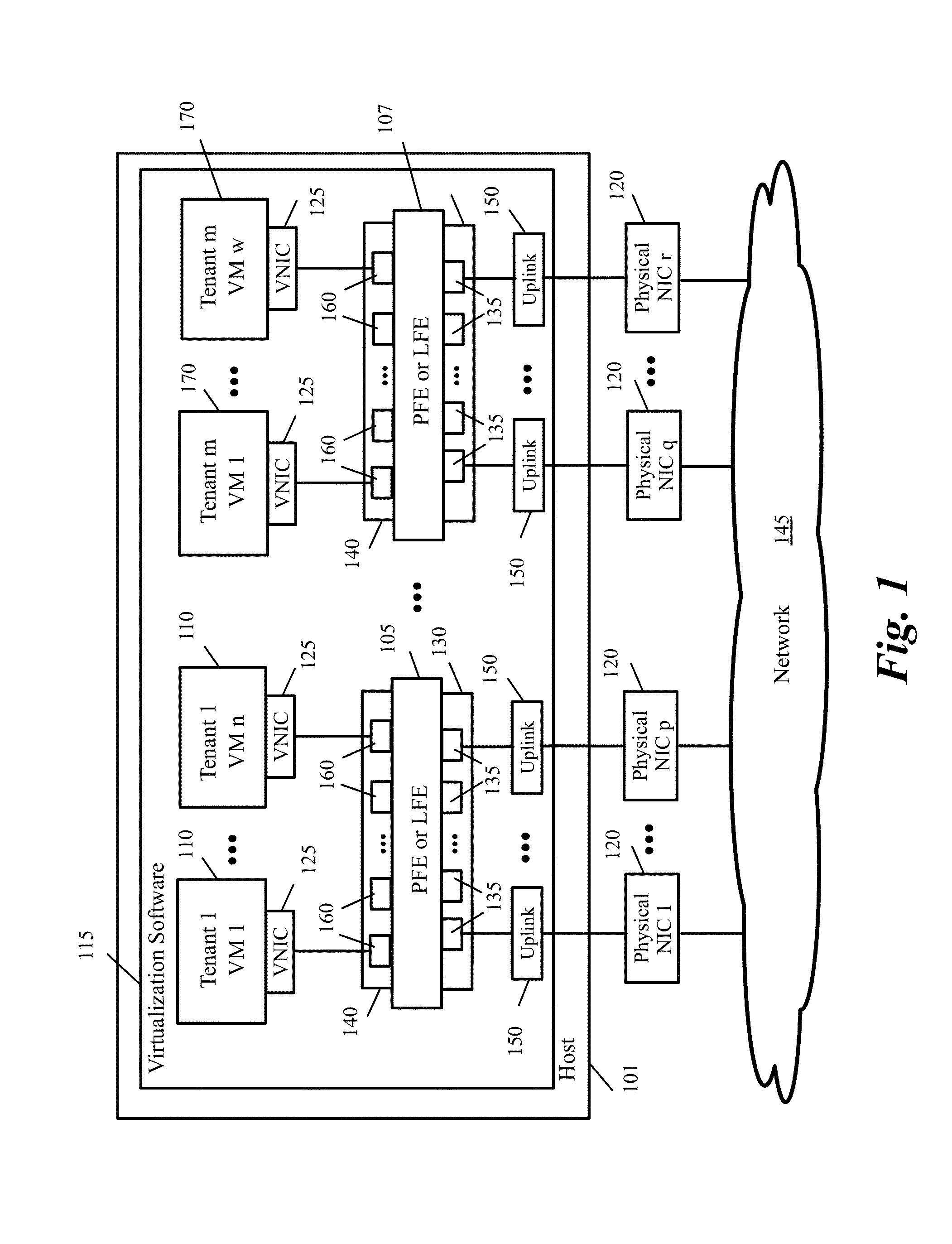
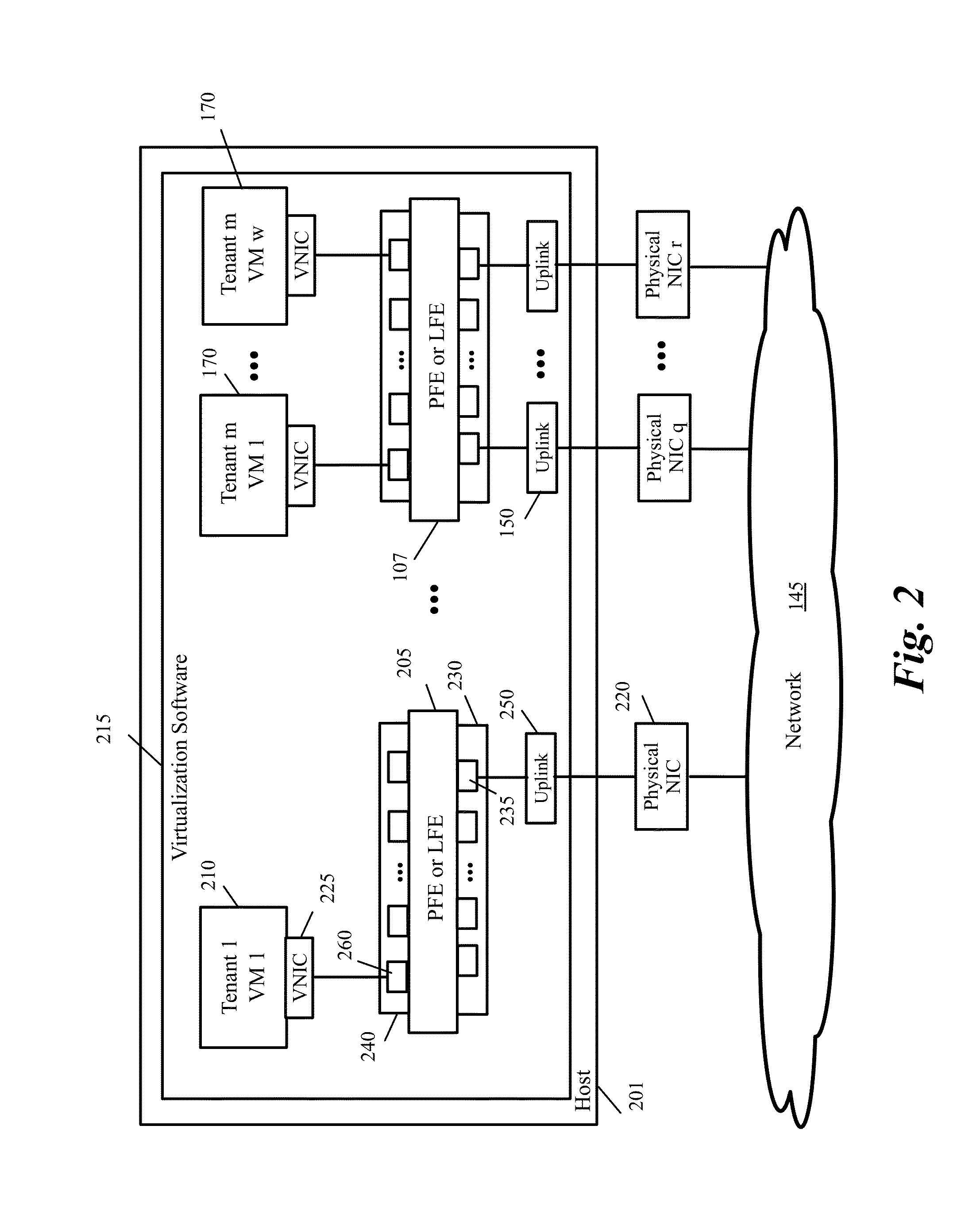
A Virtual Network Interface Card (vNIC) profile is a collection of settings that can be applied to individual virtual network interface cards in the Manager.
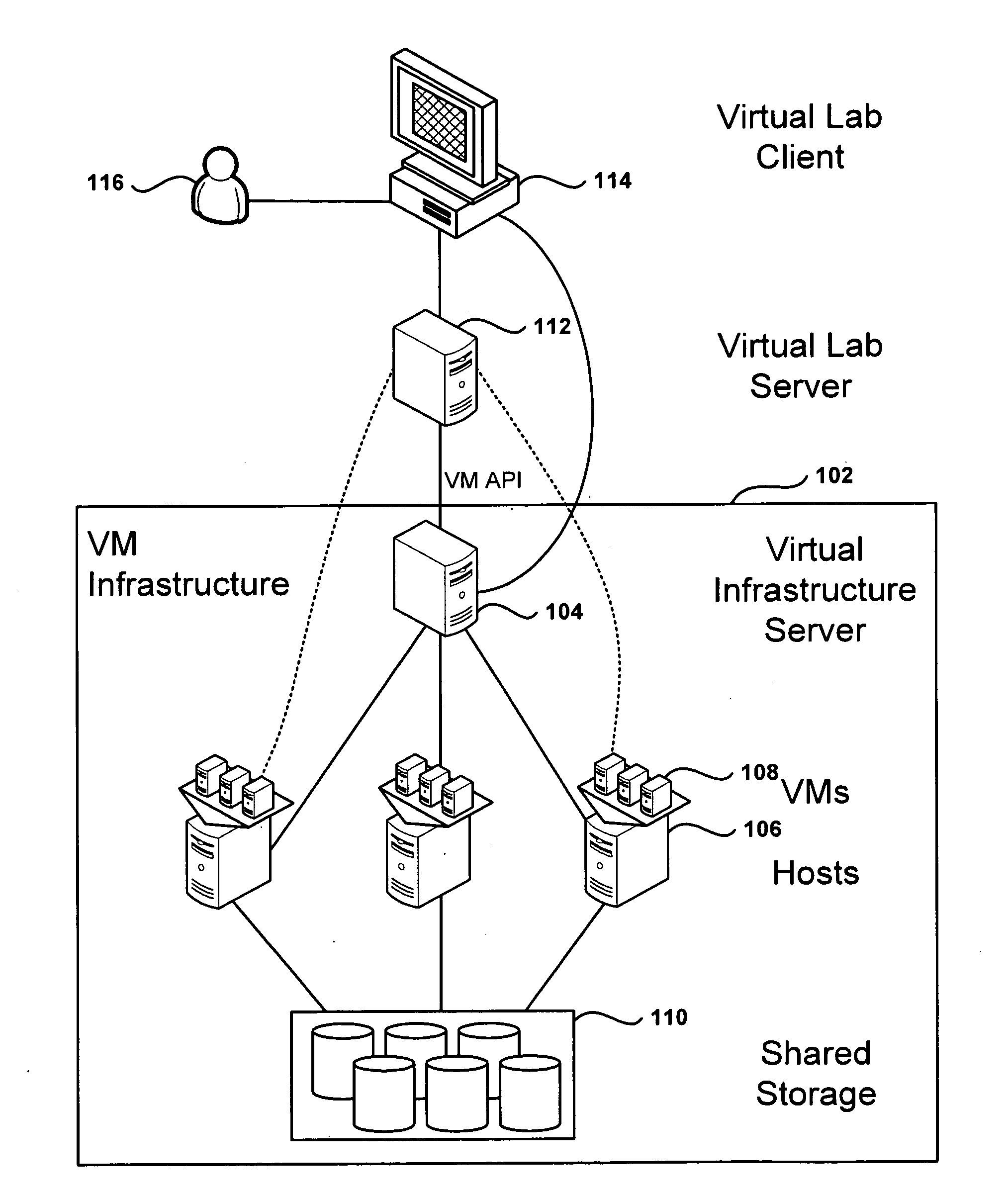
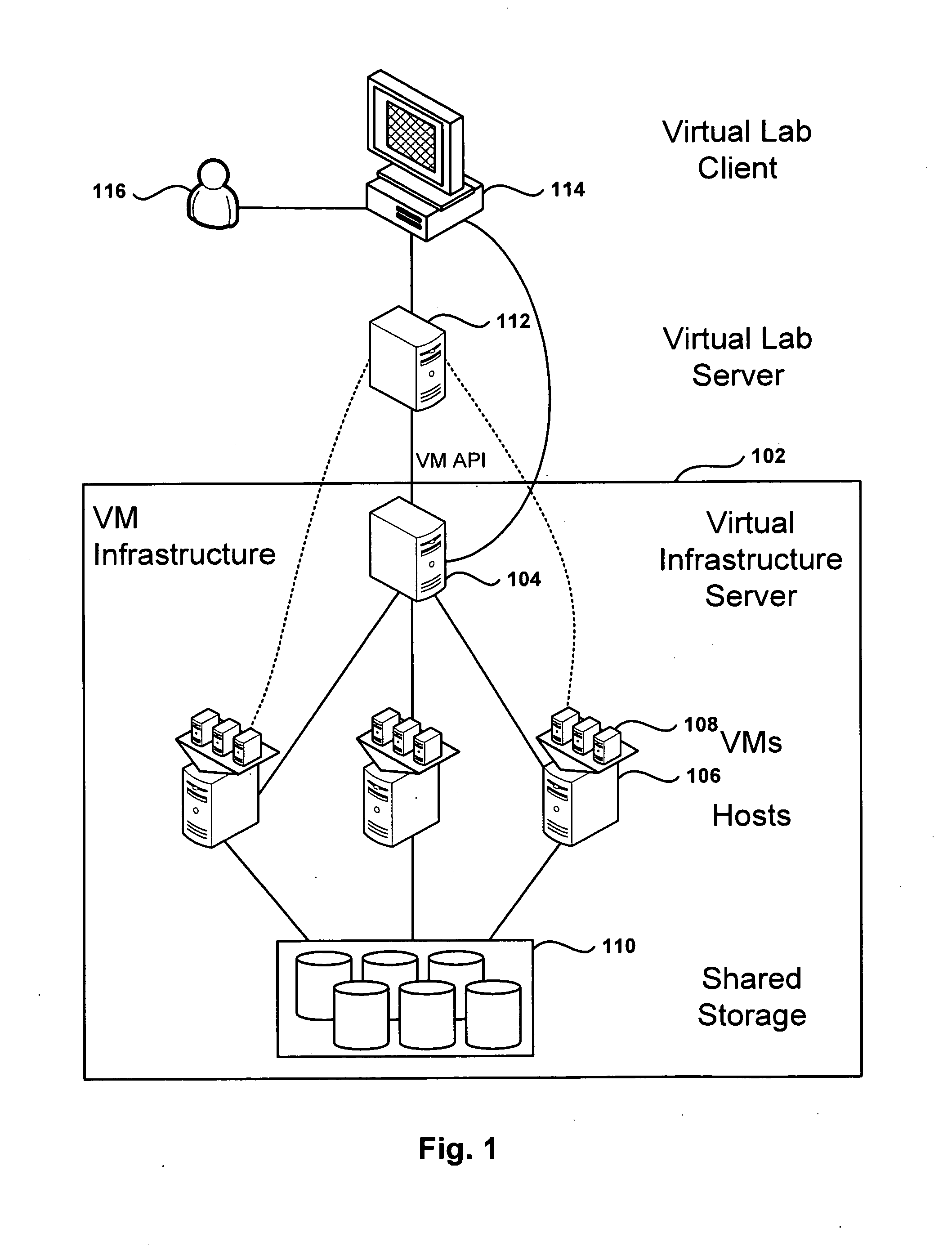
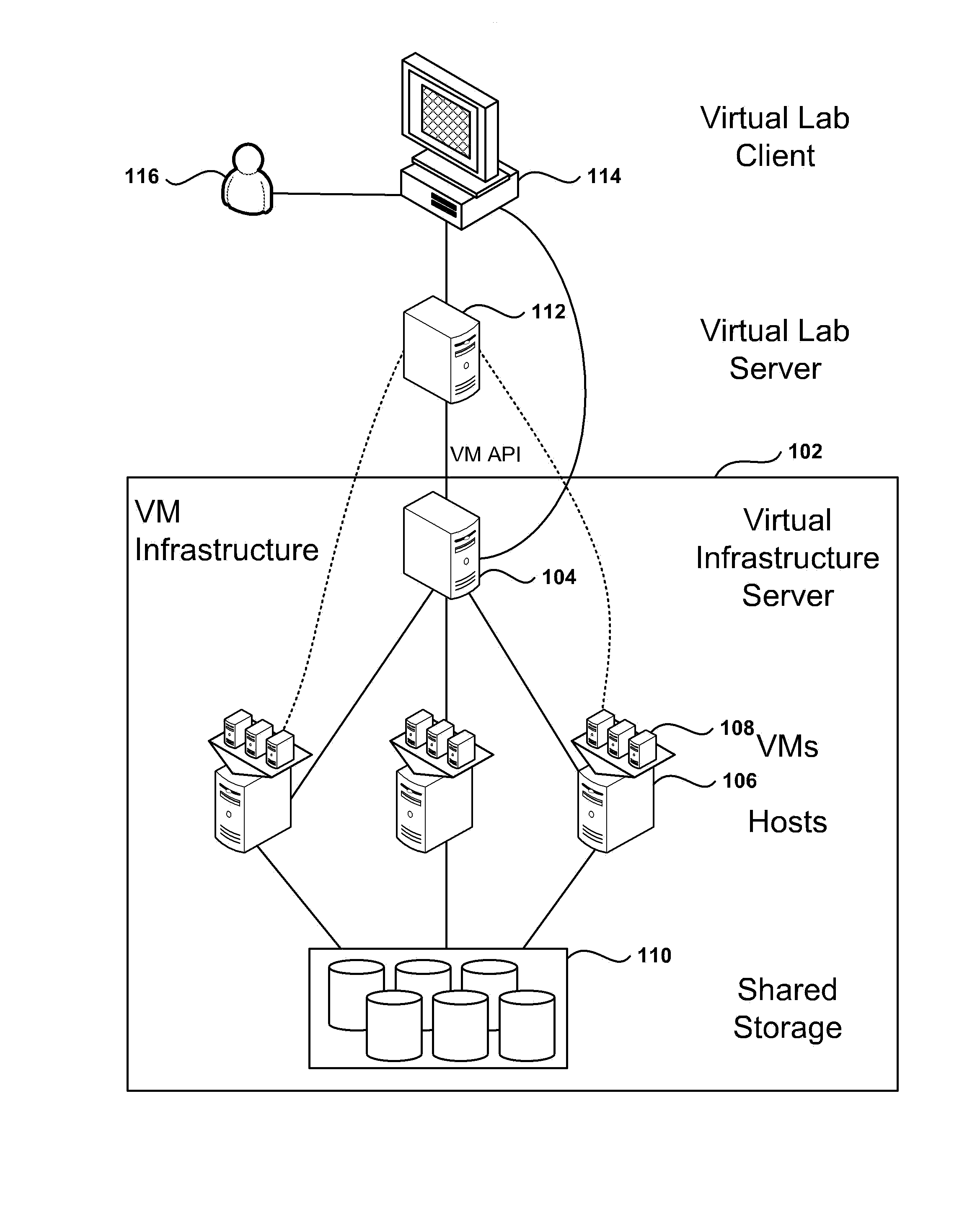
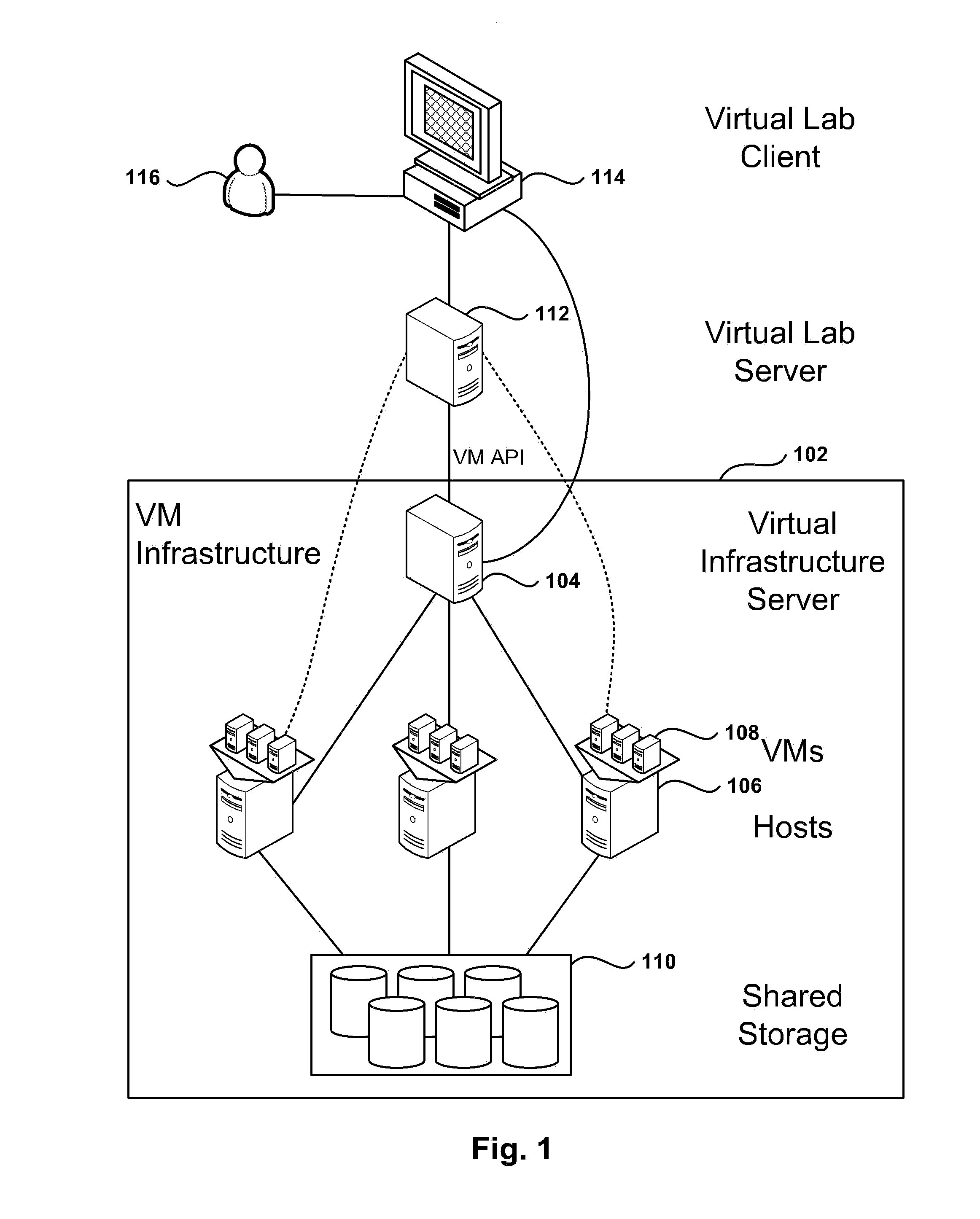
Management and Implementation of Enclosed Local Networks in a Virtual Lab
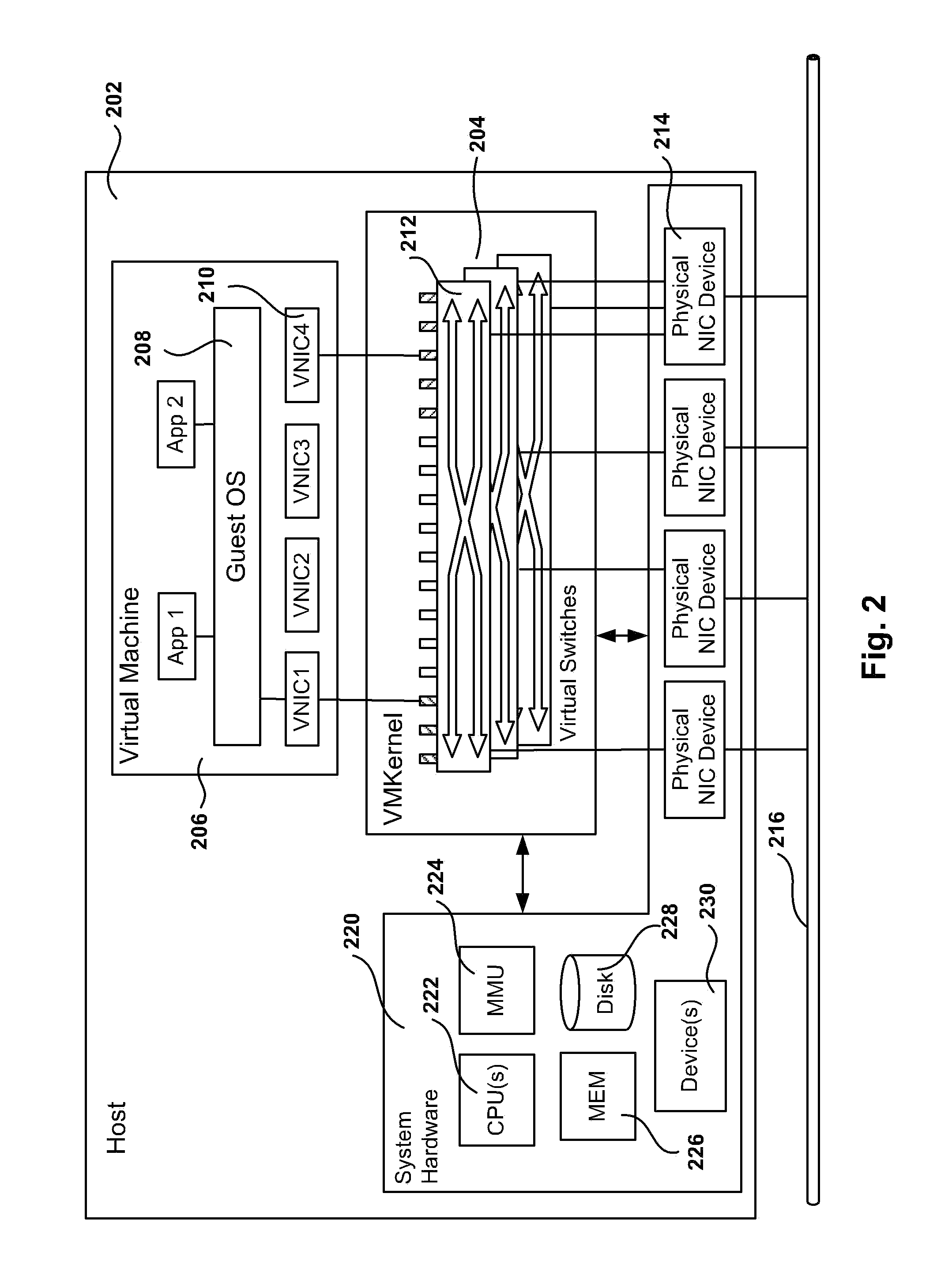
Methods, systems, and computer programs for creating isolated environments that include virtual machines (VM) and networks in a virtual infrastructure are presented. The method includes an operation to define a configuration of a virtual system which includes VMs, virtual network interface cards (VNIC) in the VMs, and configuration local networks (CLN). Further, the method associates each VNIC with one of the CLNs and transmits instructions to the virtual infrastructure for deploying the configuration. Deploying the configuration includes instantiating VMs and CLNs in the virtual infrastructure. Each VM is instantiated in a host monitored by a virtual lab server, and the CLNs are instantiated in the same hosts where the VMs have been instantiated. Only VMs from the configuration can connect to the instantiated CLNs. The method further transmits instructions to the virtual infrastructure to customize the VMs by executing the customization instructions in the guest operating systems of the VMs to configure the VMs' VNICs.
Owner:VMWARE INC
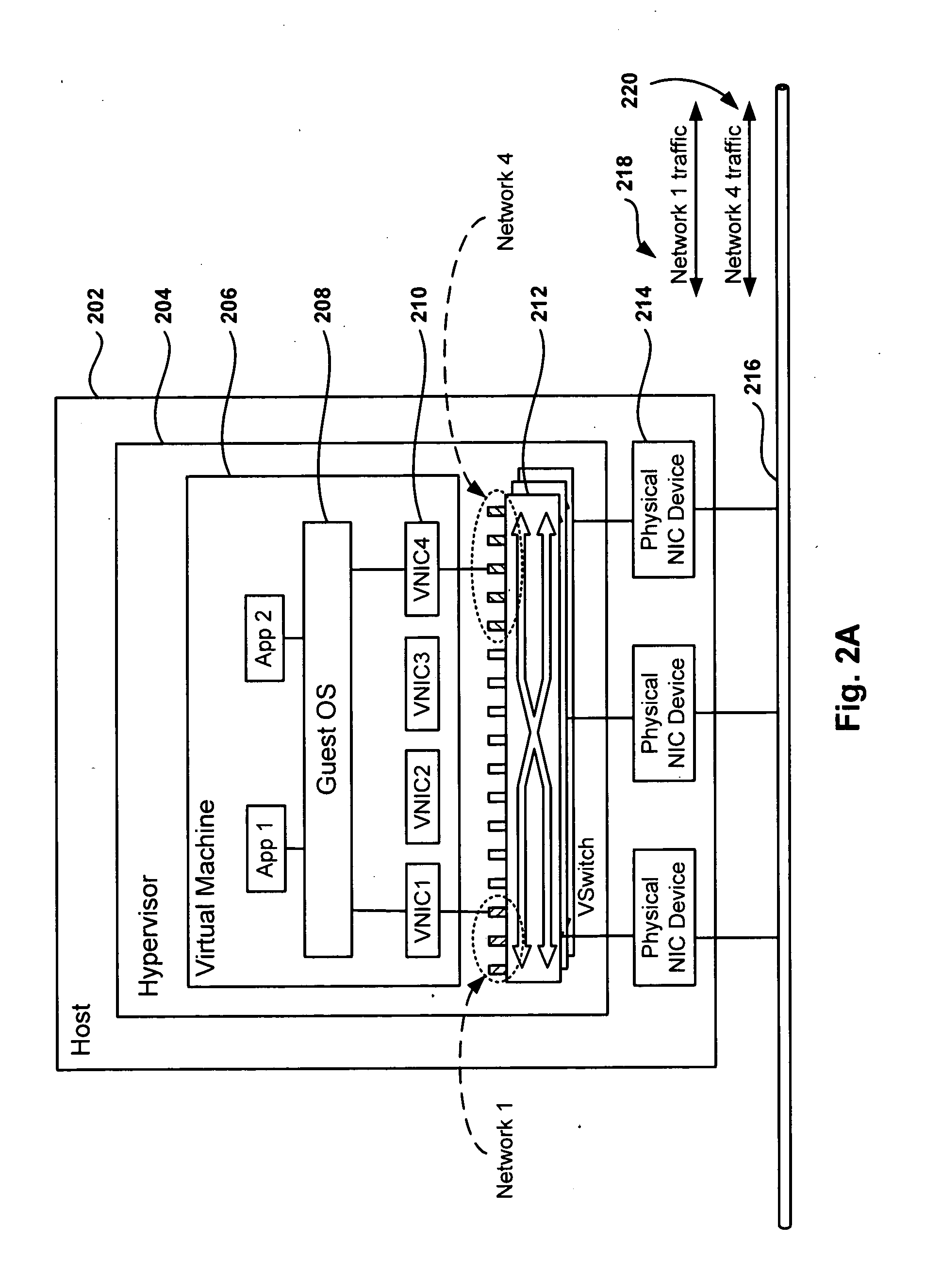
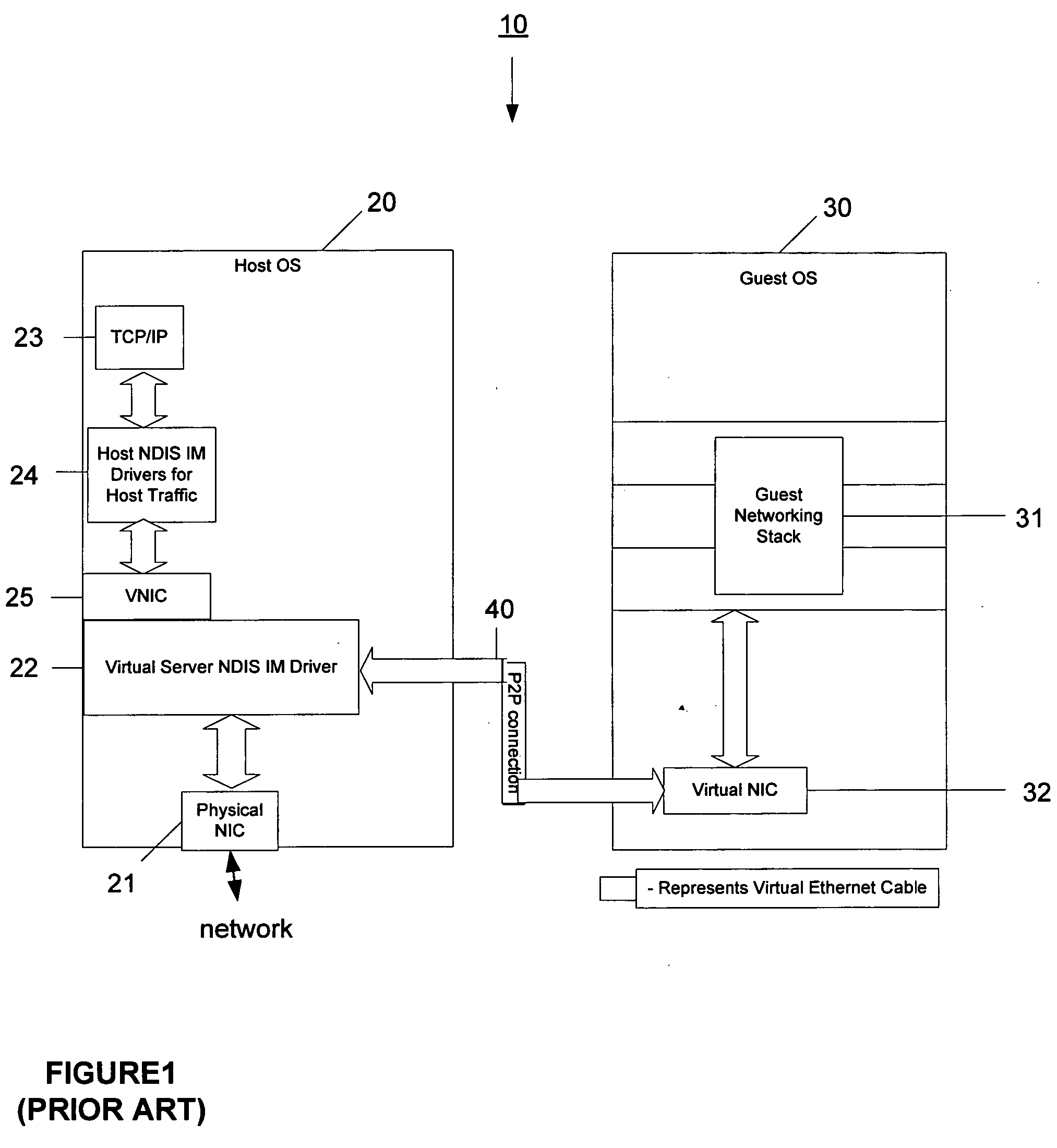
VM network traffic monitoring and filtering on the host
InactiveUS20060206300A1Software simulation/interpretation/emulationMemory systemsQuality of serviceOperational system
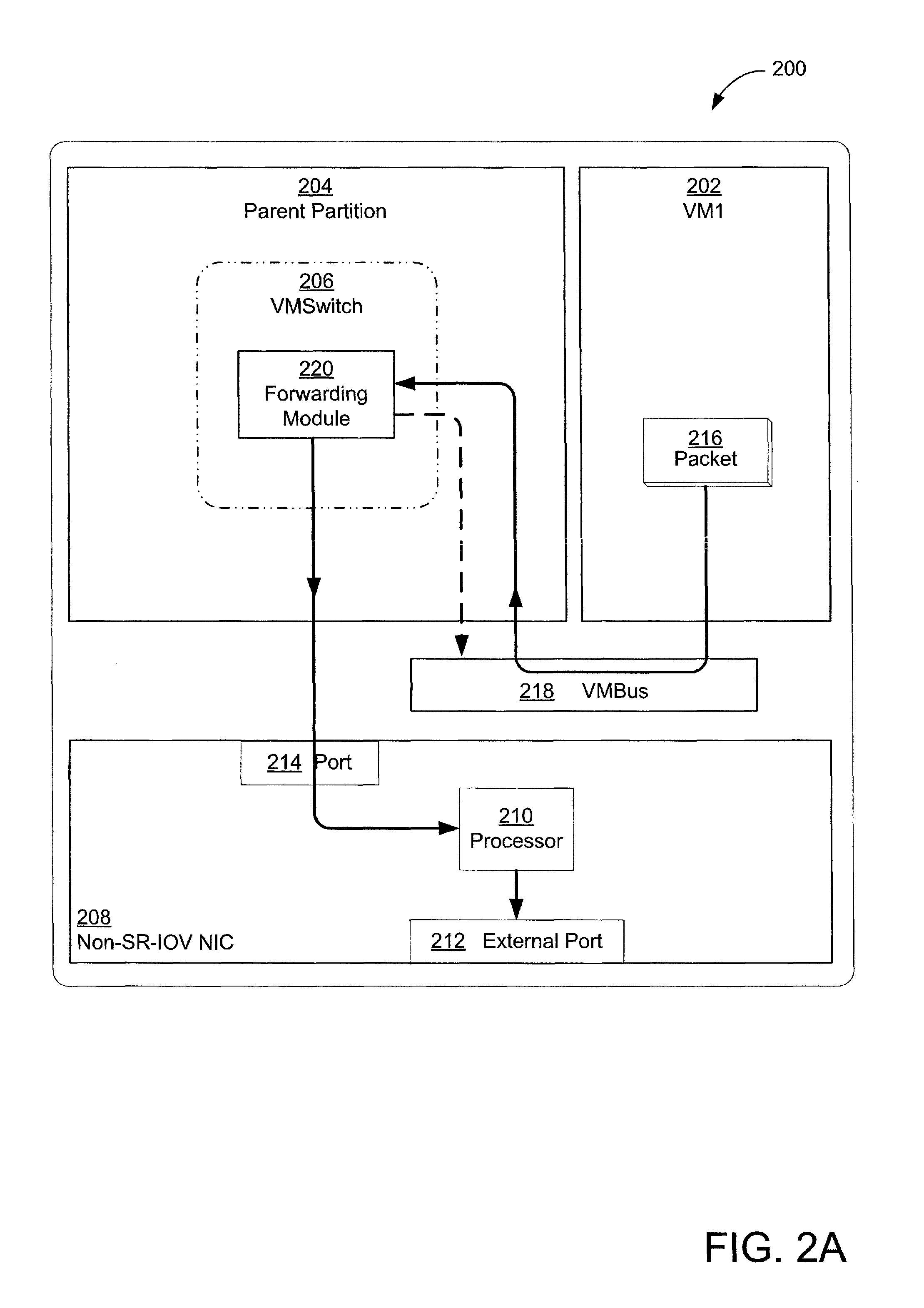
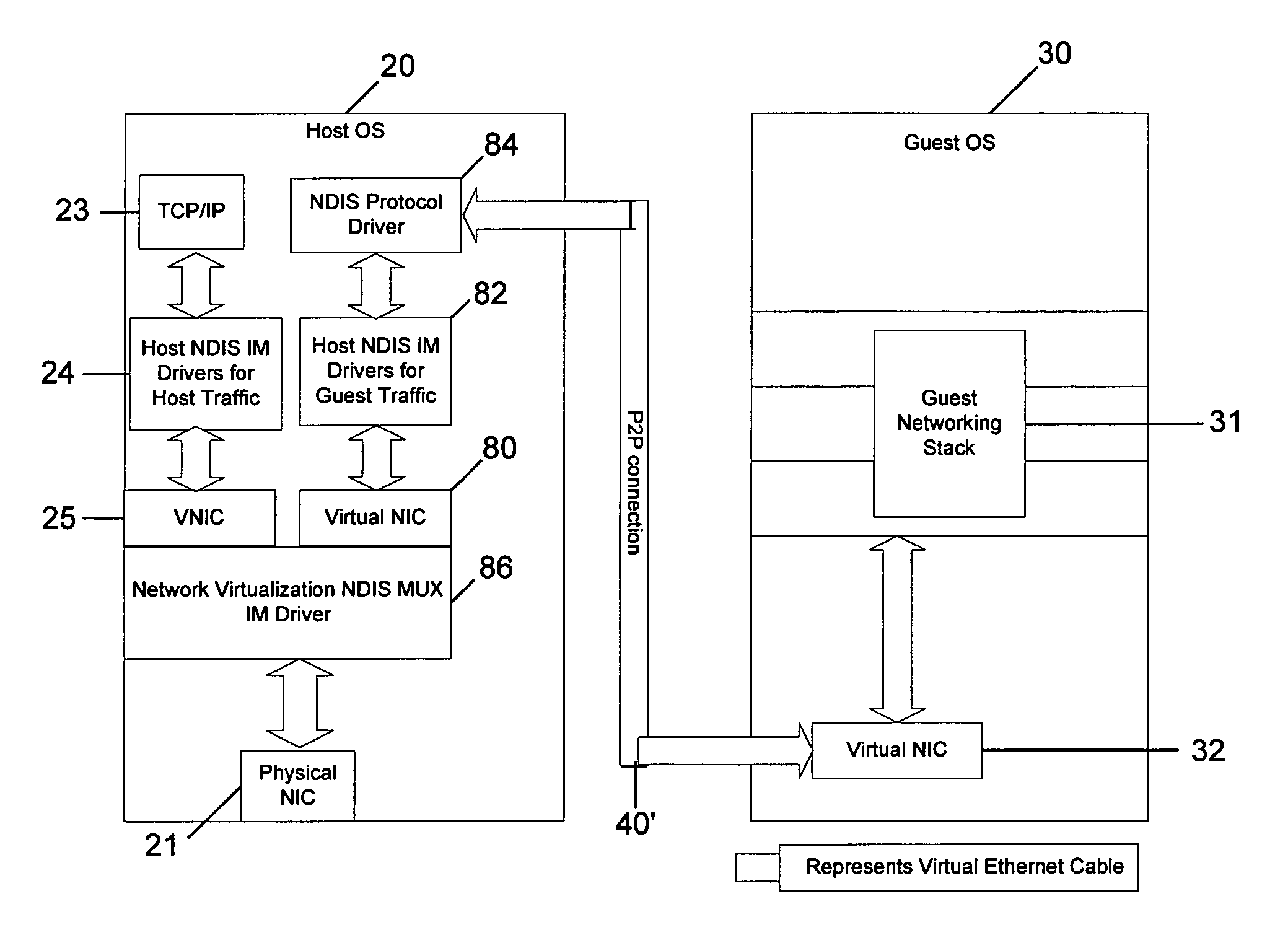
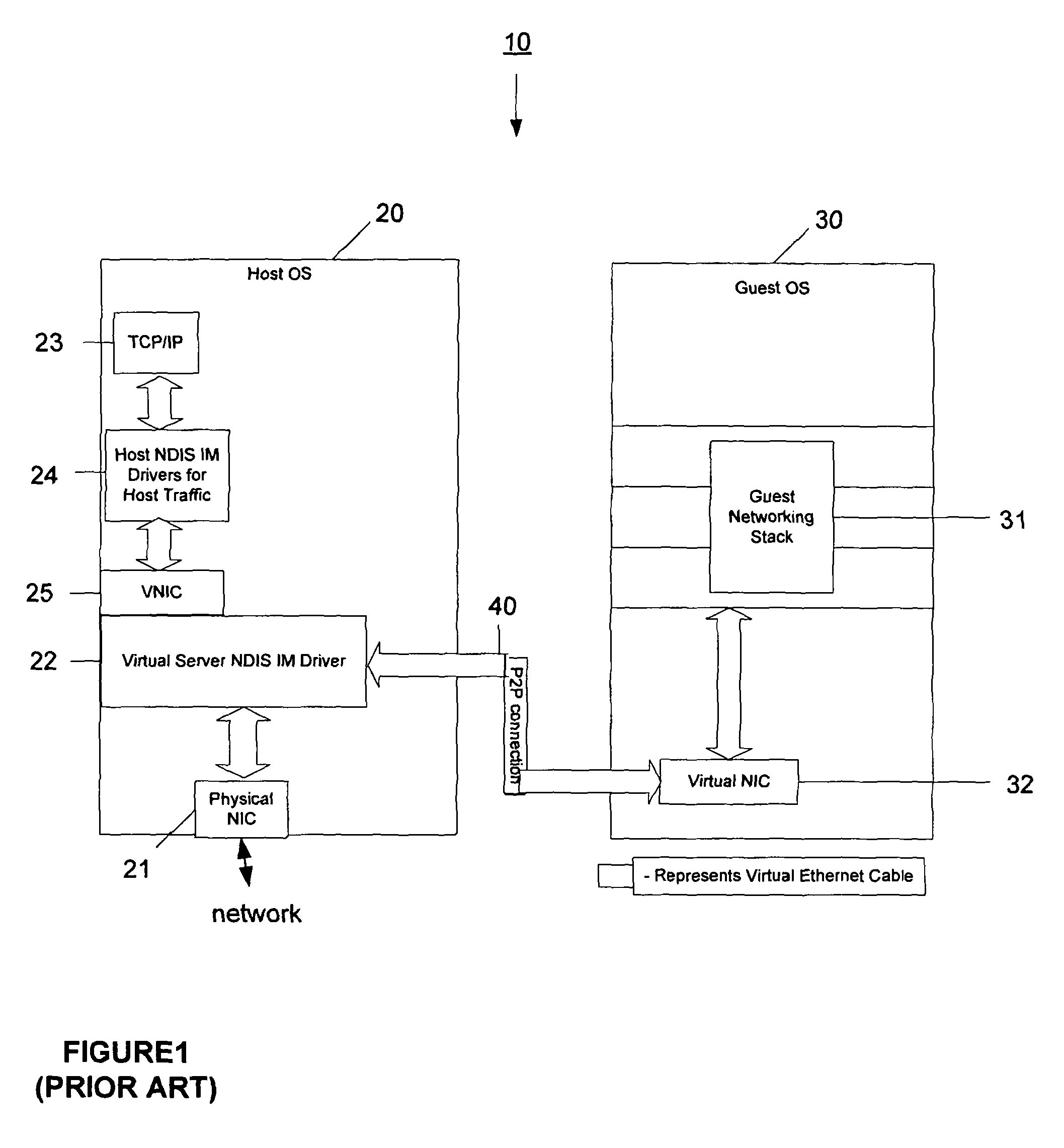
A system and method is provided that enables older legacy guest operating systems like Windows NT 4.0 and Windows95® to take advantage of newly developed NDIS Intermediate (IM) drivers that support firewalls, quality of service, IP security, intrusion detection, and other functionality for monitoring / filtering incoming and outgoing network traffic in contemporary host operating systems such as Windows XP operating in a virtual machine (VM) environment. The invention thus makes such older legacy operating systems less susceptible to Internet viruses, and worms, network denial of service (DOS) attacks, and the like. For each Virtual Network Interface Card (VNIC) in a guest VM, a corresponding VNIC is created on the host OS, and a point to point connection is established between the guest and host VNICs. The NDIS IM drivers bind themselves on top of the host VNIC and effectively place themselves as a filter on the point to point connection.
Owner:MICROSOFT TECH LICENSING LLC
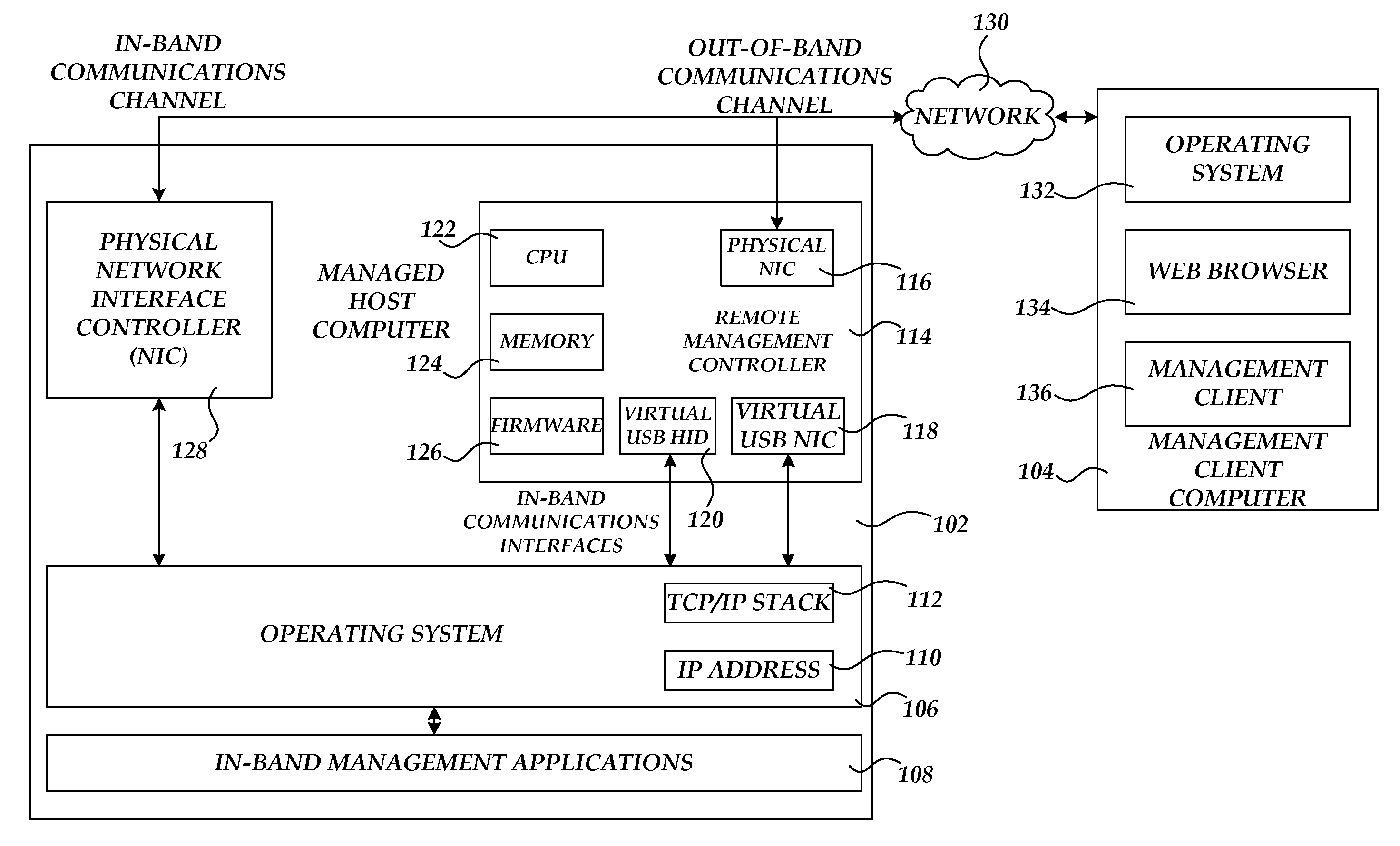
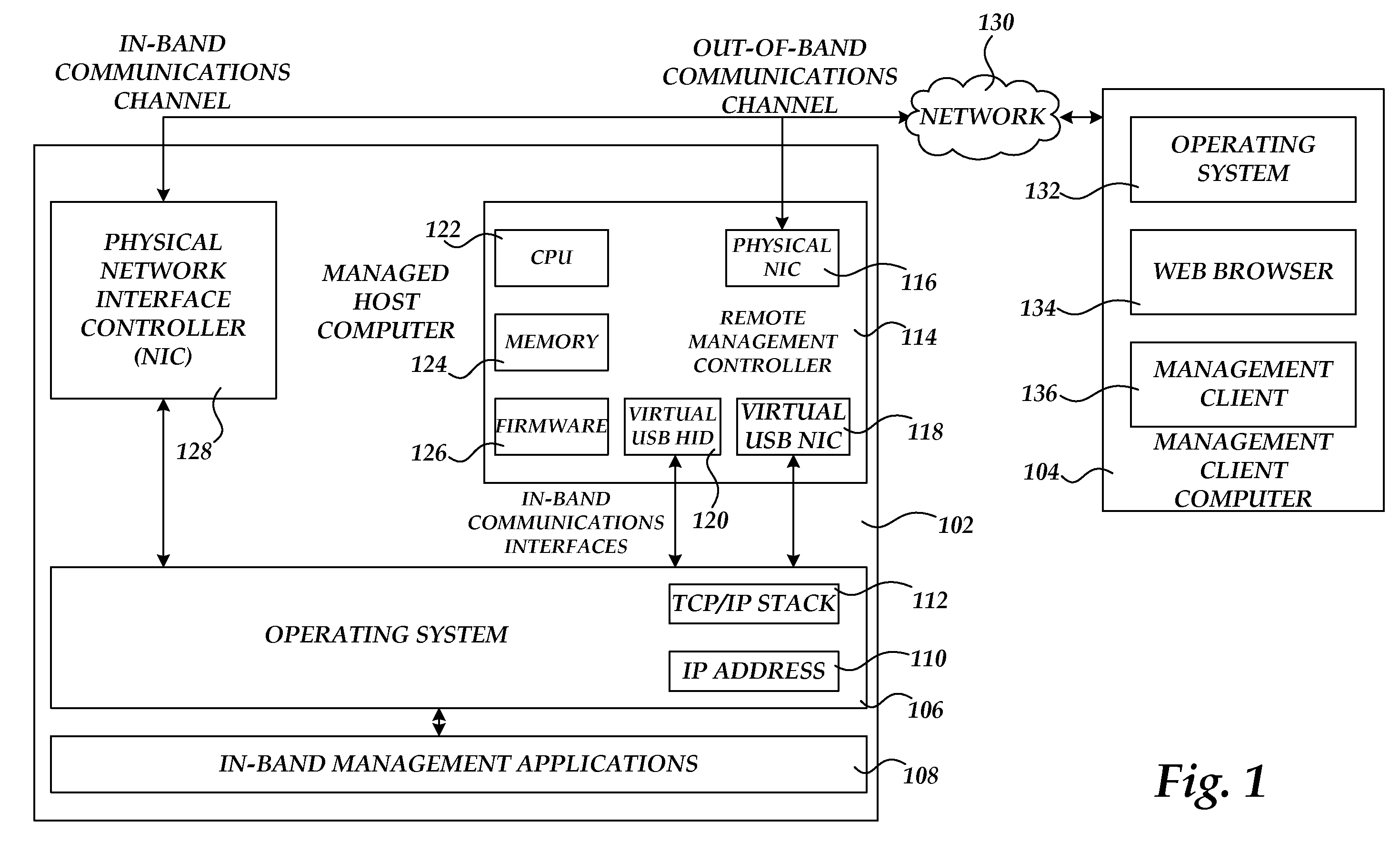
Communicating with an in-band management application through an out-of-band communications channel
ActiveUS20110283006A1Multiple digital computer combinationsData switching networksCommunication interfaceNetwork management application
A remote management controller is provided for use in conjunction with a managed host computer. The remote management controller exposes a virtual network interface controller, such as a driverless virtual USB network interface controller, to the managed host computer. Through the in-band connection provided by the virtual network interface controller, the remote management controller can communicate with in-band management applications executing on the managed host computer. The managed host computer can also access services executing on the remote management controller through the in-band communications interface. The remote management controller can also enable communication between the management client computer and in-band management applications executing on the managed host computer. The managed host computer can also access an out-of-band communications network between the remote management device and a management client computer.
Owner:AMERICAN MEGATRENDS
Offloading packet processing for networking device virtualization
ActiveUS20130254766A1Improve network performanceTransmissionSoftware simulation/interpretation/emulationComputer hardwareData virtualization
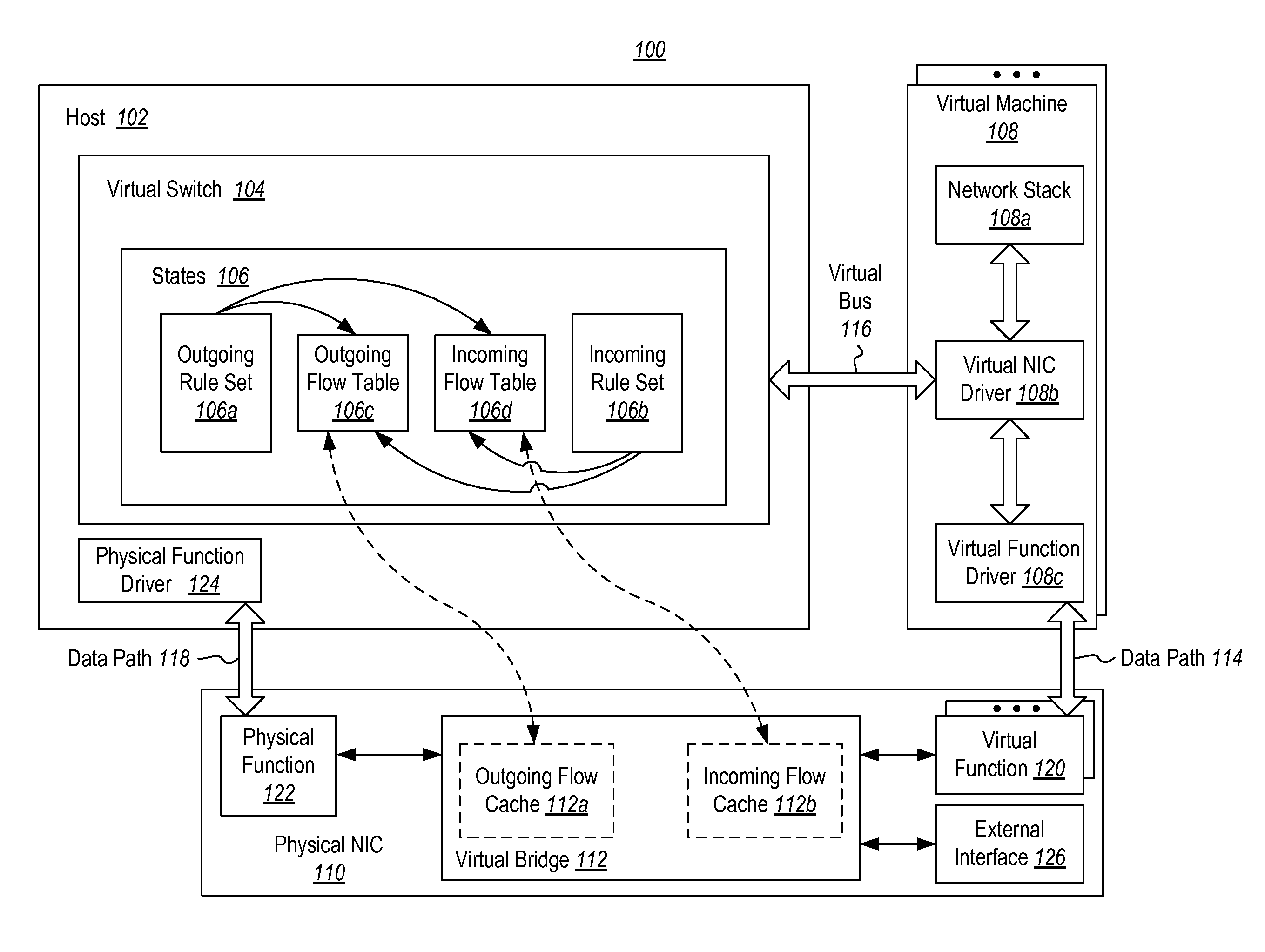
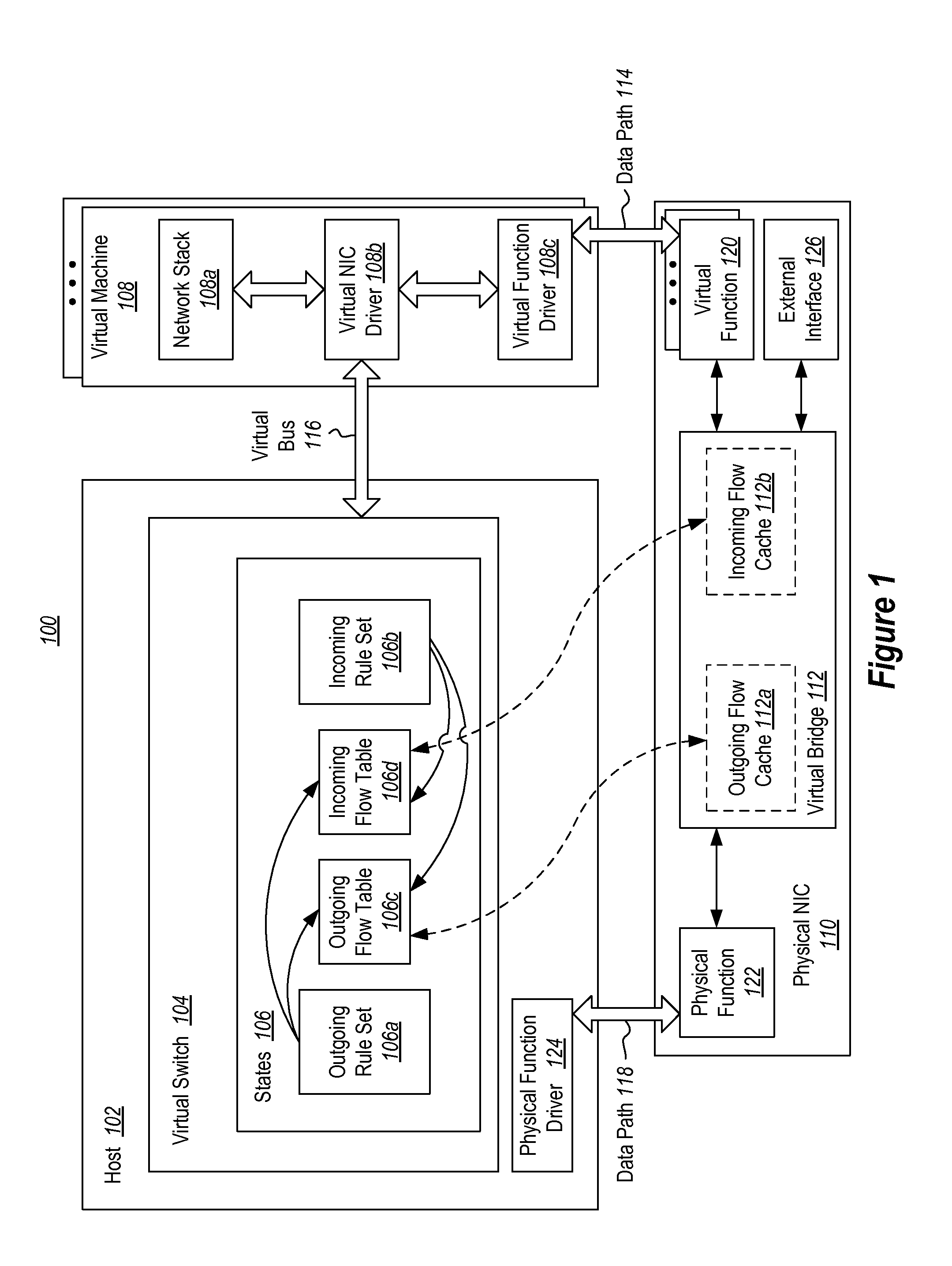
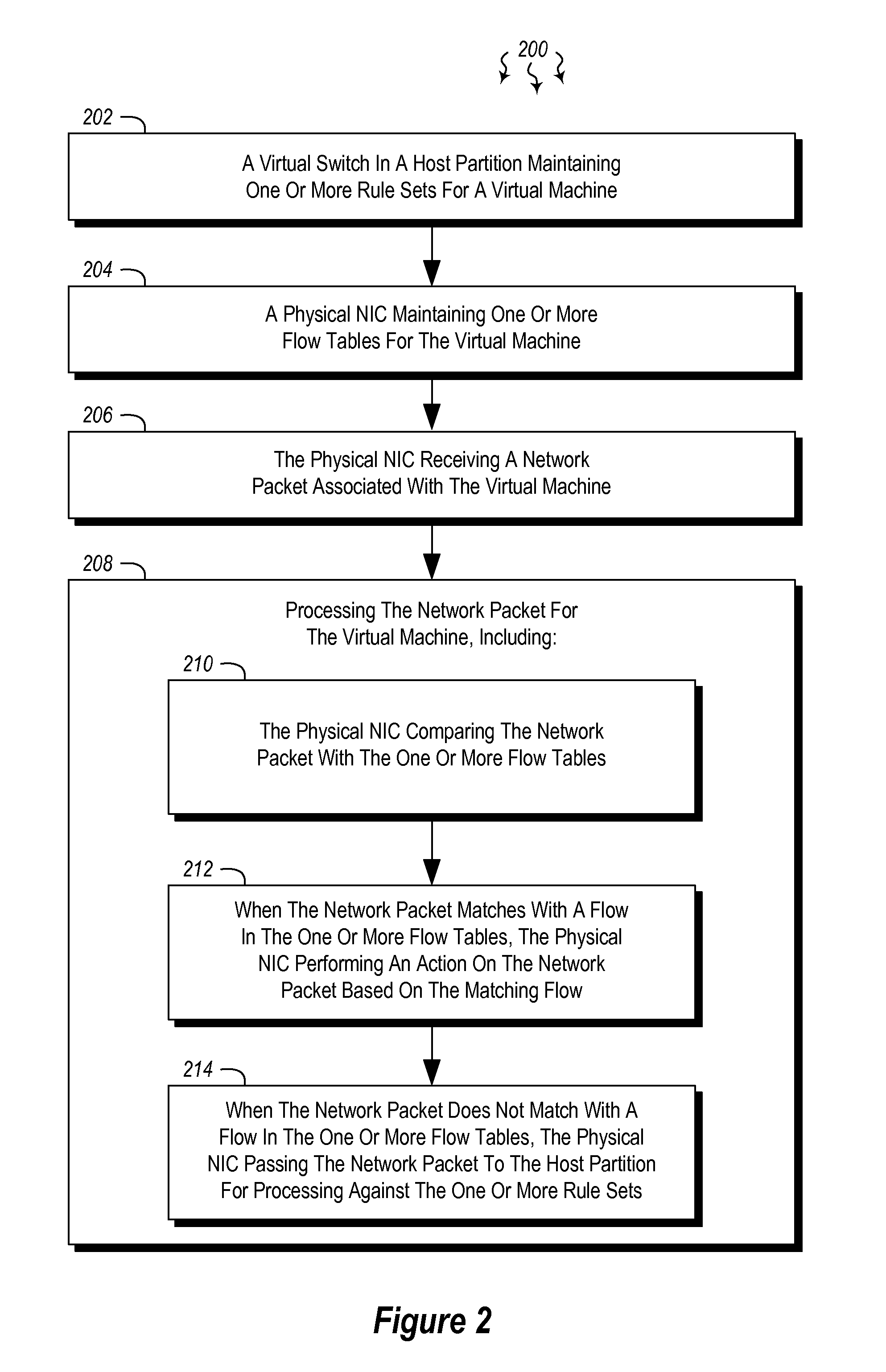
The present invention extends to methods, systems, and computer program products for offloading packet processing for networking device virtualization. A host maintains rule set(s) for a virtual machine, and a physical network interface card (NIC) maintains flow table(s) for the virtual machine. The physical NIC receives and processes a network packet associated with the virtual machine. Processing the network packet includes the physical NIC comparing the network packet with the flow table(s) at the physical NIC. When the network packet matches with a flow in the flow table(s) at the physical NIC, the physical NIC performs an action on the network packet based on the matching flow. Alternatively, when the network packet does not match with a flow in the flow table(s) at the physical NIC, the physical NIC passes the network packet to the host partition for processing against the rule set(s).
Owner:MICROSOFT TECH LICENSING LLC
Secure and efficient offloading of network policies to network interface cards
ActiveUS8856518B2Multiple digital computer combinationsData switching networksVirtualizationProtocol for Carrying Authentication for Network Access
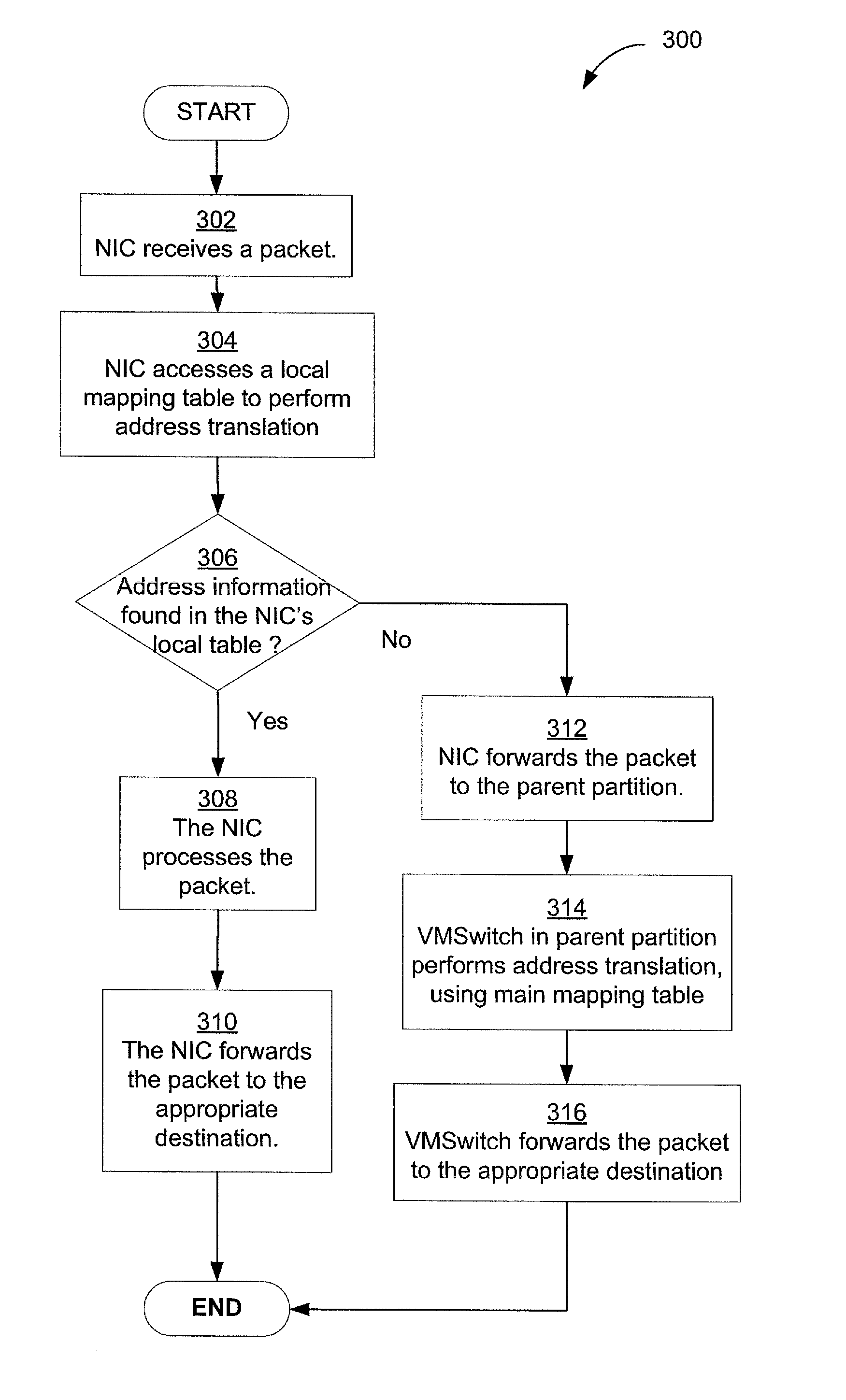
Techniques for efficient and secure implementation of network policies in a network interface controller (NIC) in a host computing device operating a virtualized computing environment. In some embodiments, the NIC may process and forward packets directly to their destinations, bypassing a parent partition of the host computing device. In particular, in some embodiments, the NIC may store network policy information to process and forward packets directly to a virtual machine (VM). If the NIC is unable to process a packet, then the NIC may forward the packet to the parent partition. In some embodiments, the NIC may use an encapsulation protocol to transmit address information in packet headers. In some embodiments, this address information may be communicated by the MC to the parent partition via a secure channel. The NIC may also obtain, and decrypt, encrypted addresses from the VMs for routing packets, bypassing the parent partition.
Owner:MICROSOFT TECH LICENSING LLC
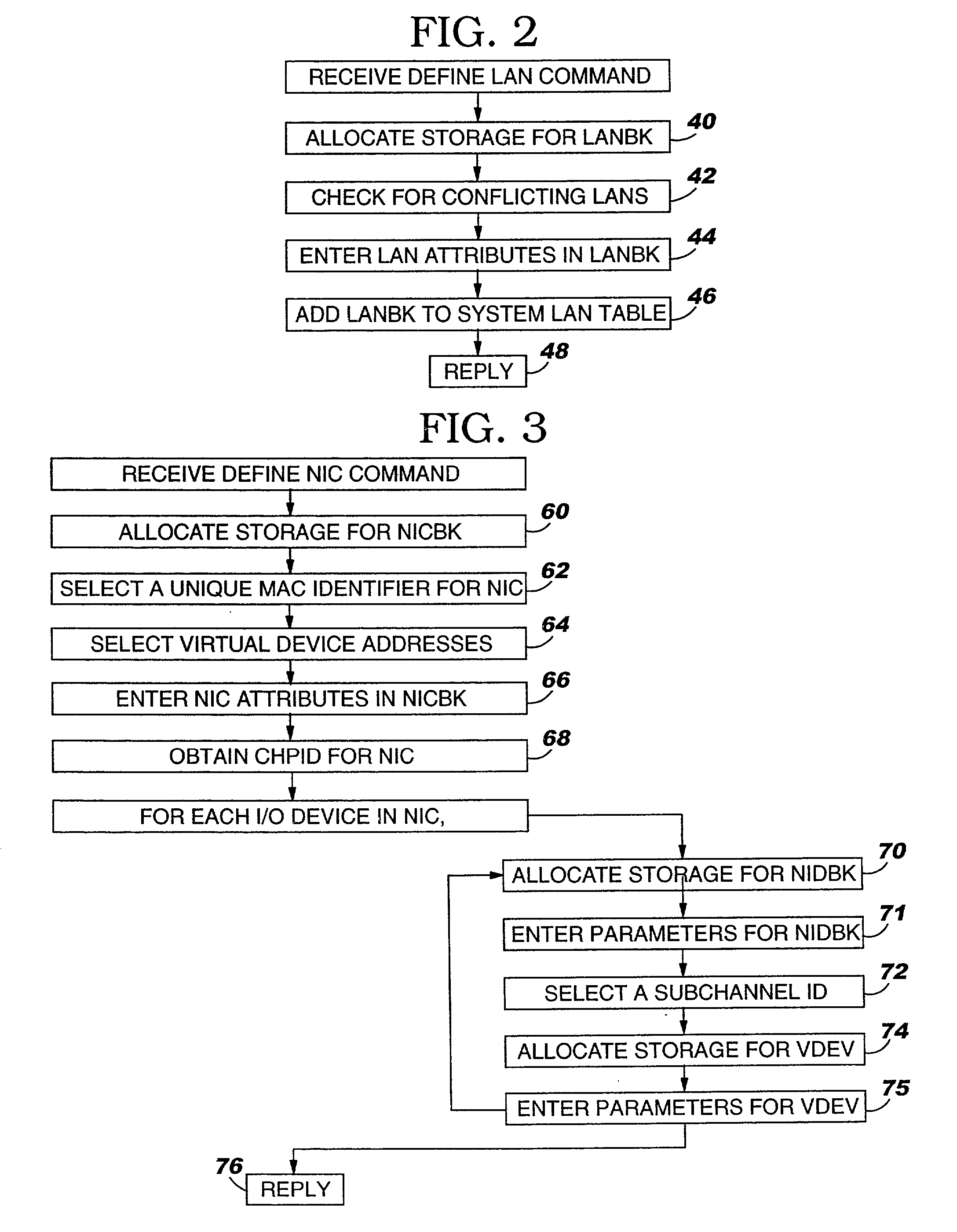
Virtual machine operating system LAN
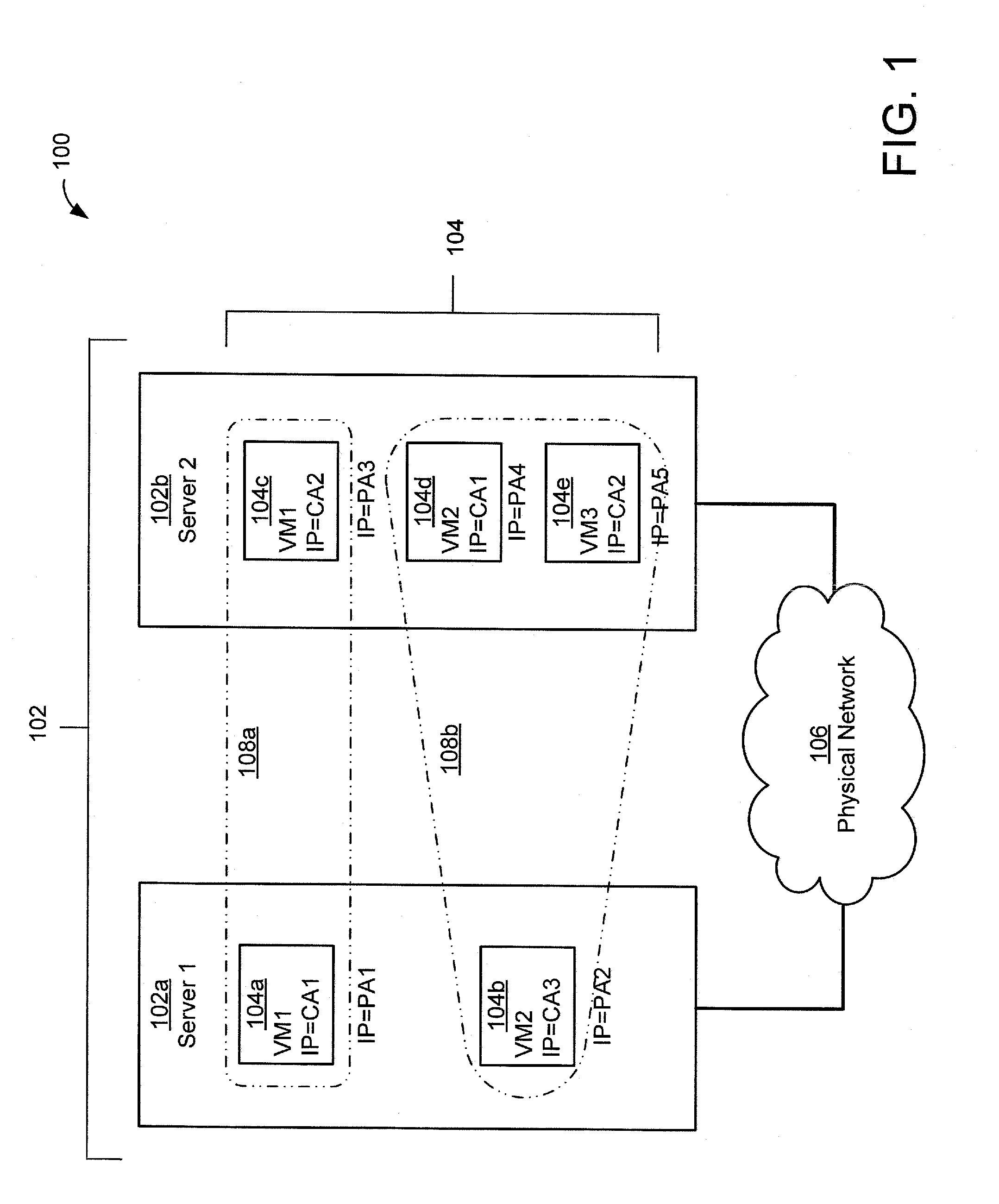
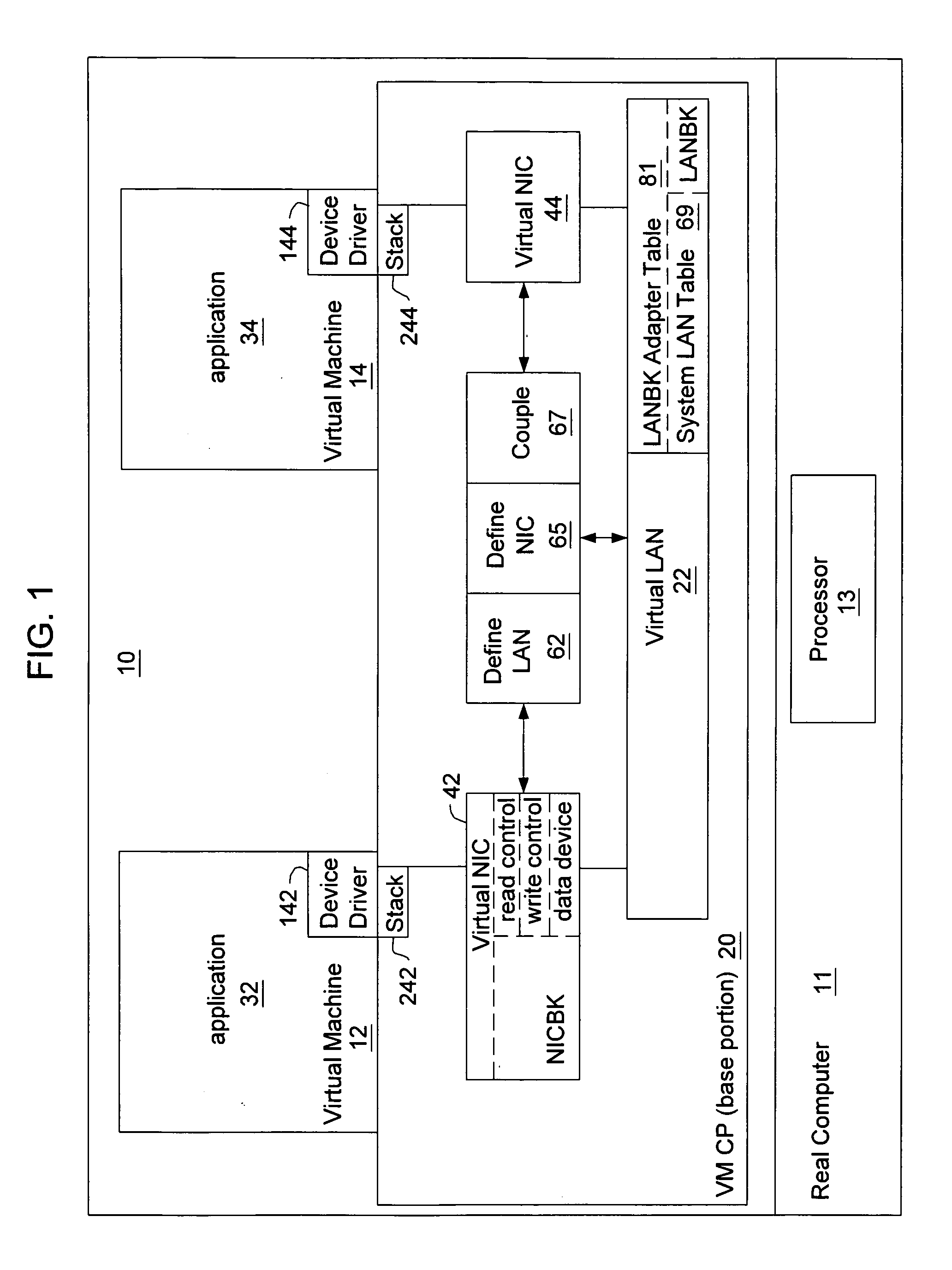
ActiveUS7111303B2Simple methodMultiprogramming arrangementsMultiple digital computer combinationsOperational systemIp address
A virtual machine operating system for communication between first and second applications which execute in different user portions of the virtual machine operating system and use Internet Protocol (IP). The virtual machine operating system comprises a first user portion, a second user portion and a base portion. The first user portion executes the first application and includes a first device driver for a first virtual network interface card (NIC). The second user portion executes the second application and includes a second device driver for a second virtual NIC. The base portion is shared by the first and second user portions and includes the first and second virtual NICs. The base portion maintains a table of IP addresses by which each device driver addresses its respective NIC and other, corresponding addresses by which the base portion addresses the virtual NIC. The first device driver is programmed to receive an IP datagram from the first application and pass it to the first NIC using IP. The datagram includes an IP address of the second virtual NIC and an indication that the second application should receive the datagram. The base portion is programmed to determine the other address of the second NIC based on the table and transfer the datagram to a storage location associated with the second virtual NIC or the second device driver.
Owner:IBM CORP
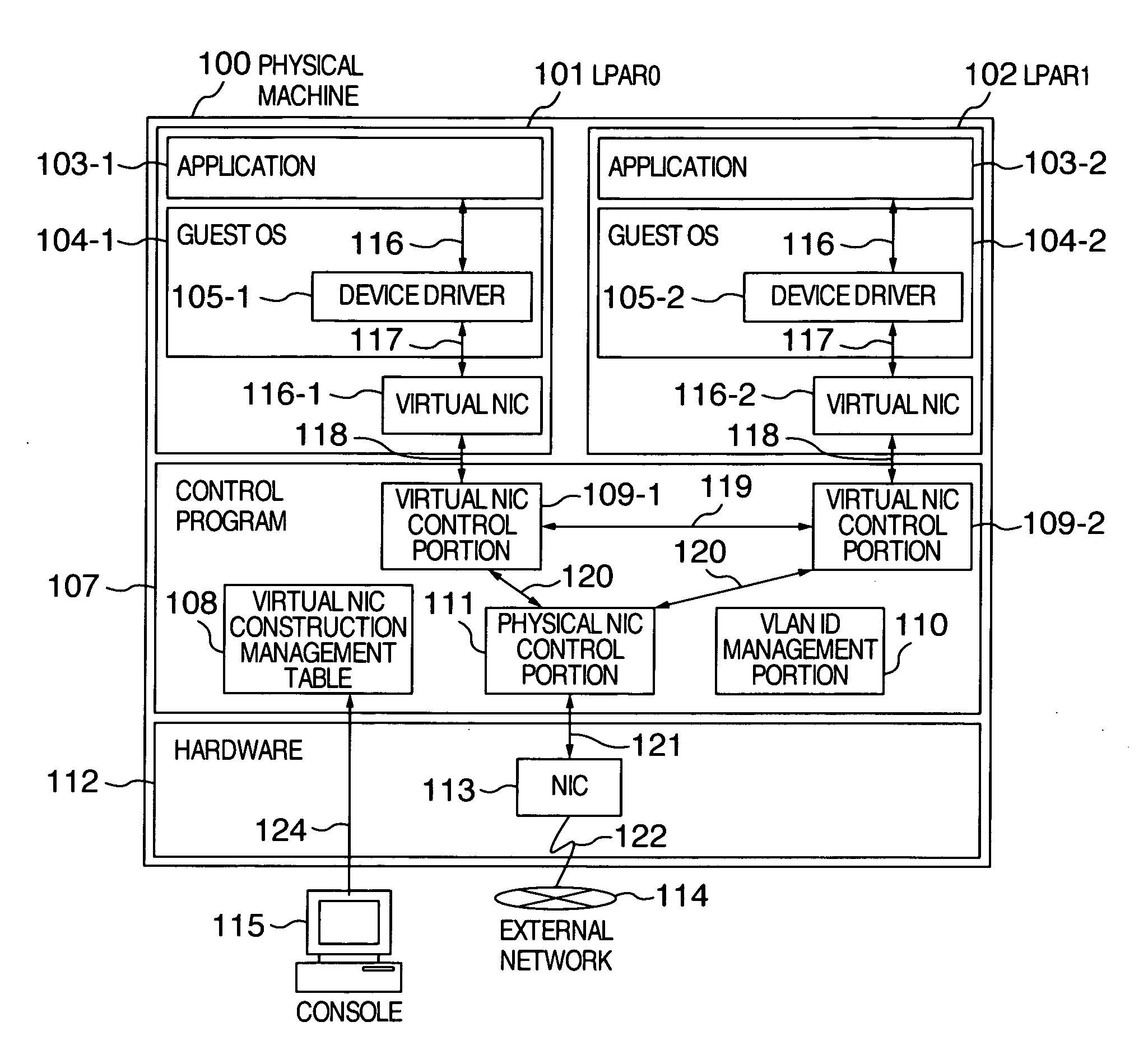
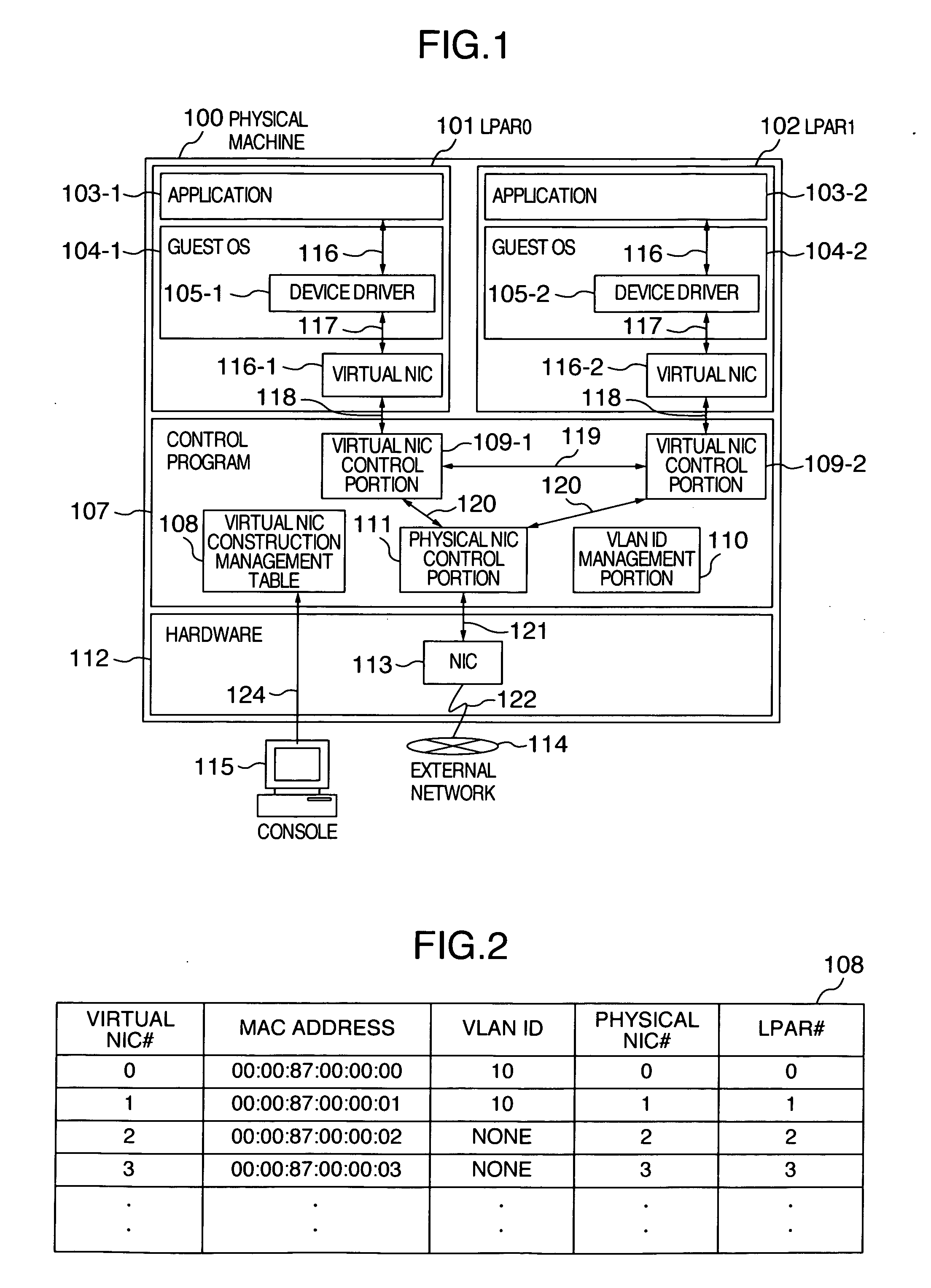
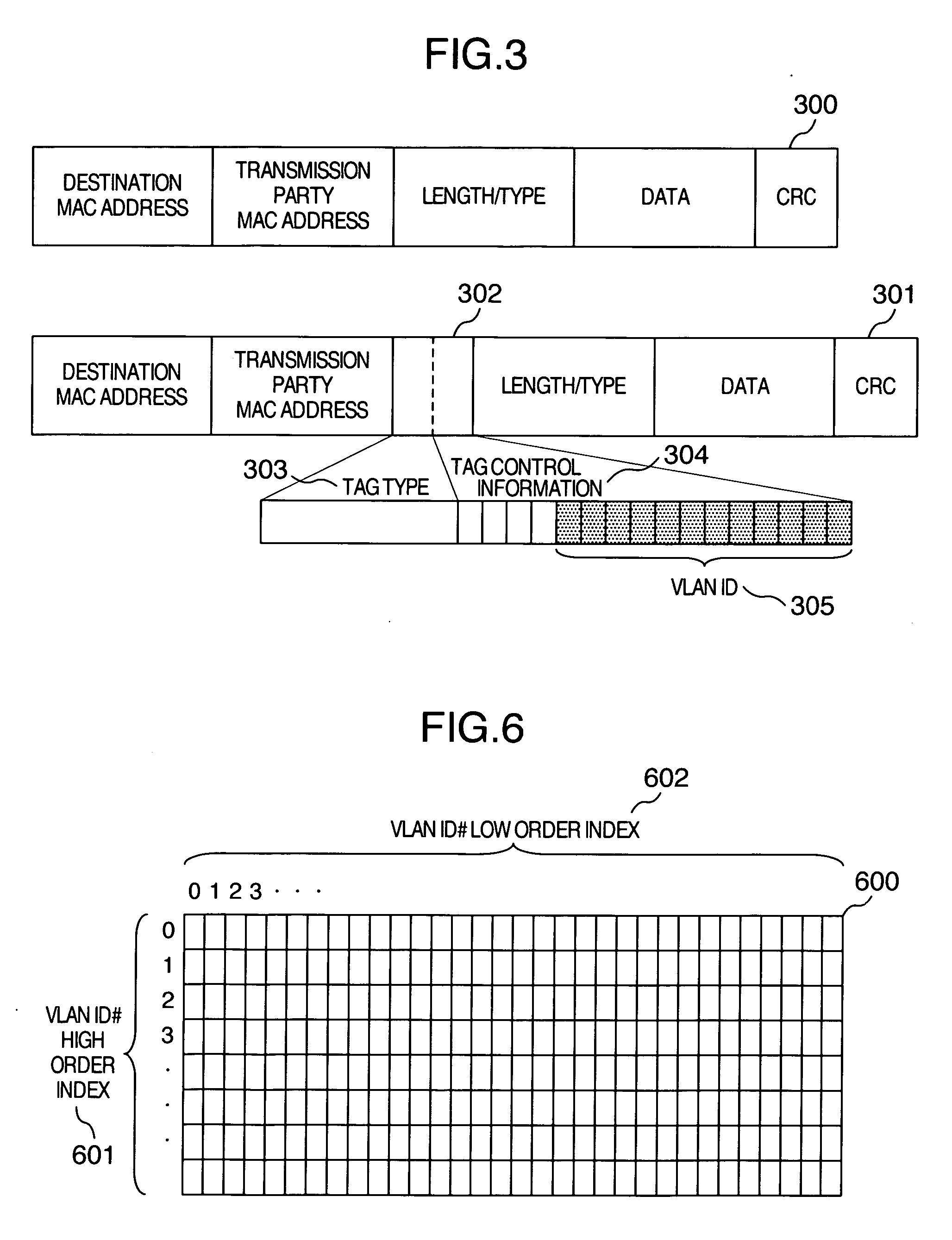
Virtual machine system and method of network communication between virtual machines
ActiveUS20070140263A1More flexiblyMore flexibly copeMultiprogramming arrangementsMultiple digital computer combinationsComputer hardwareNetwork communication
A plurality of machine systems constituted by different VLAN constitution methods are integrated on one machine system by using virtual machines. An operation can be switched for virtual network interface cards to VLAN communication corresponding to VLAN ID set to a virtual network interface card or to VLAN communication corresponding to VLAN ID set by OS on a virtual machine using the virtual network interface card depending on whether or not VLAN ID is set.
Owner:HITACHI LTD
Private ethernet overlay networks over a shared ethernet in a virtual environment
ActiveUS20150071301A1Time-division multiplexData switching by path configurationEthernetVirtual network interface card
Owner:NICIRA
VM network traffic monitoring and filtering on the host
InactiveUS7865908B2Software simulation/interpretation/emulationMemory systemsQuality of serviceTraffic capacity
A system and method is provided that enables older legacy guest operating systems like Windows NT 4.0 and Windows95® to take advantage of newly developed NDIS Intermediate (IM) drivers that support firewalls, quality of service, IP security, intrusion detection, and other functionality for monitoring / filtering incoming and outgoing network traffic in contemporary host operating systems such as Windows XP operating in a virtual machine (VM) environment. The invention thus makes such older legacy operating systems less susceptible to Internet viruses, and worms, network denial of service (DOS) attacks, and the like. For each Virtual Network Interface Card (VNIC) in a guest VM, a corresponding VNIC is created on the host OS, and a point to point connection is established between the guest and host VNICs. The NDIS IM drivers bind themselves on top of the host VNIC and effectively place themselves as a filter on the point to point connection.
Owner:MICROSOFT TECH LICENSING LLC
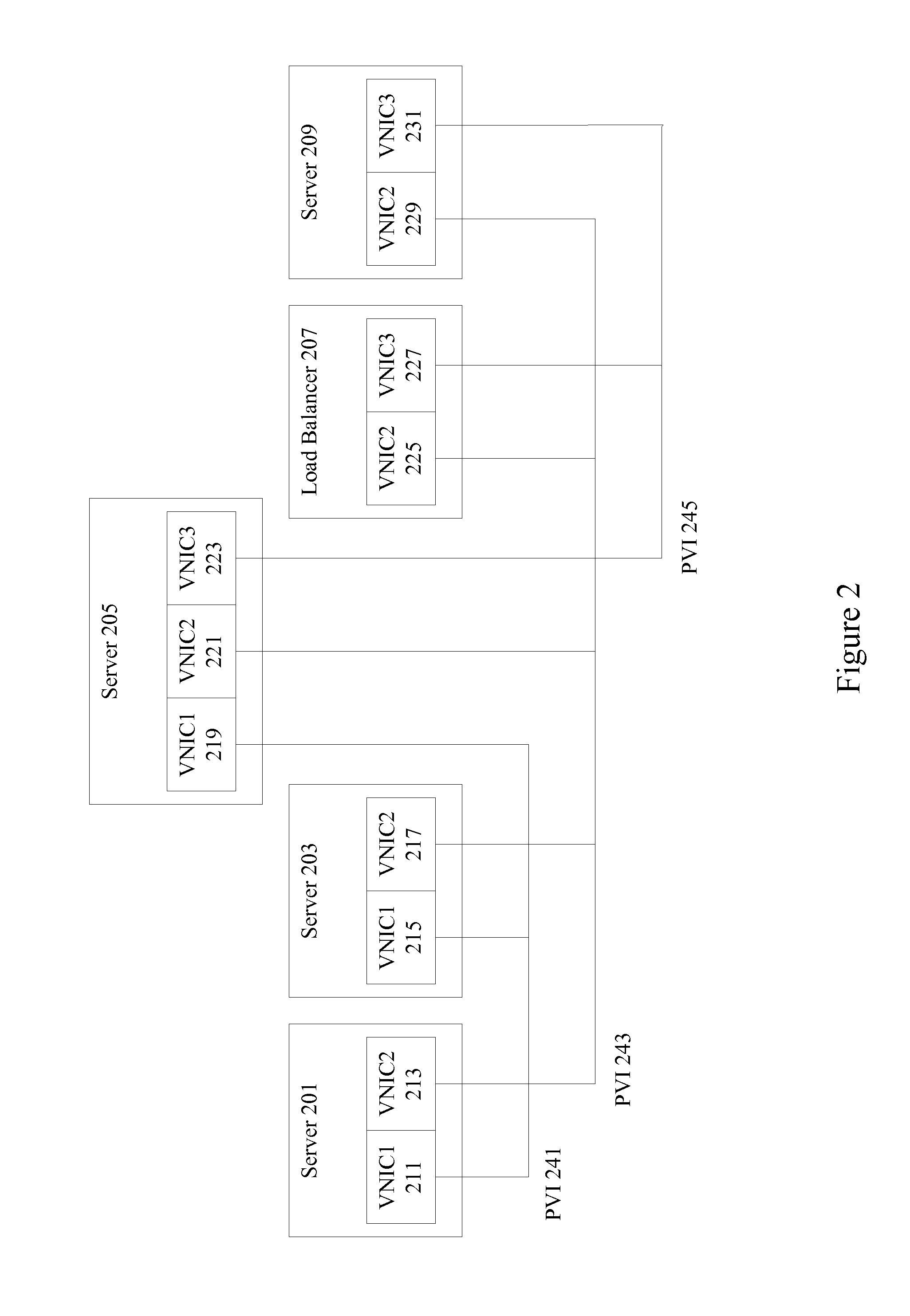
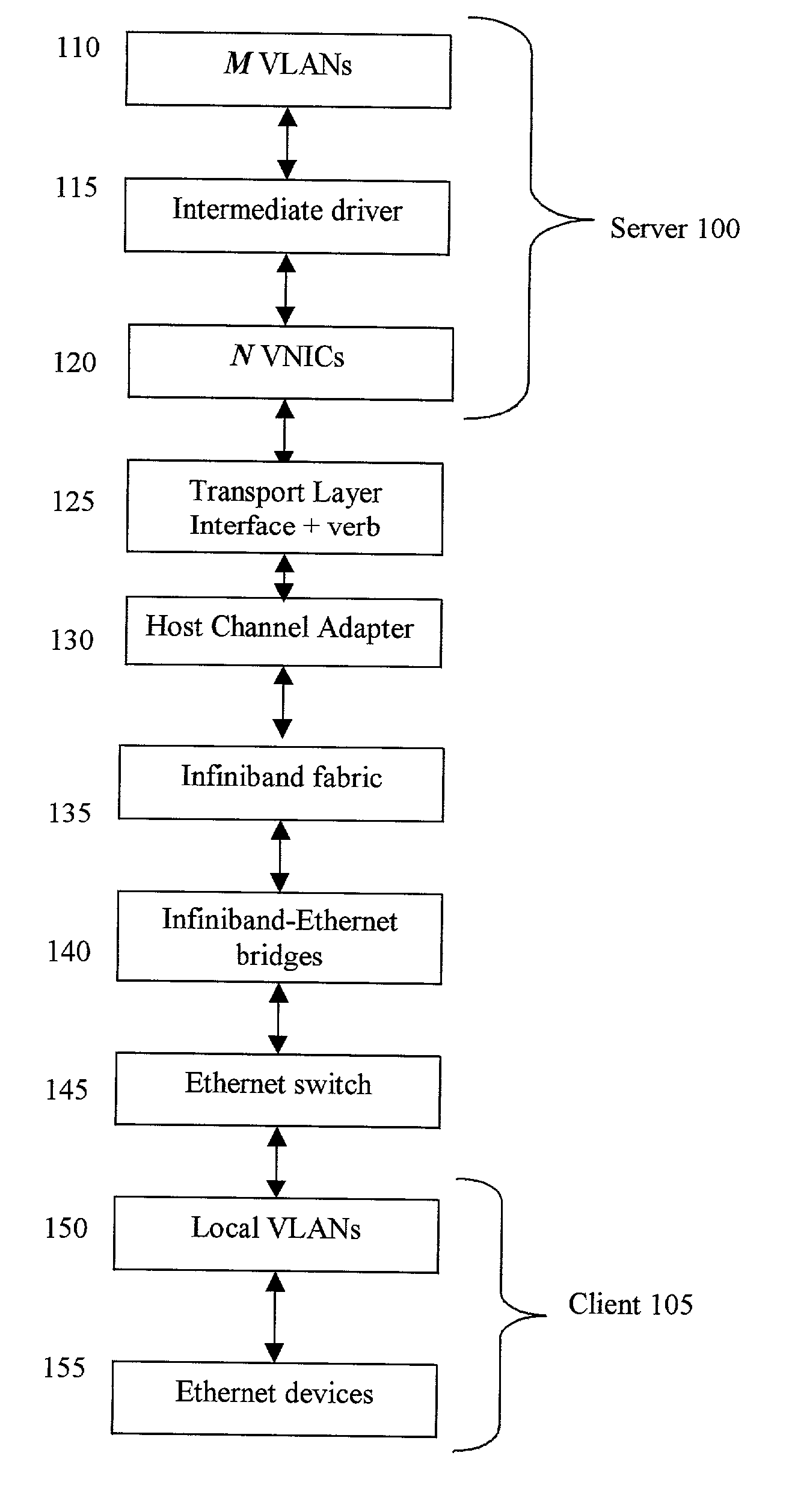
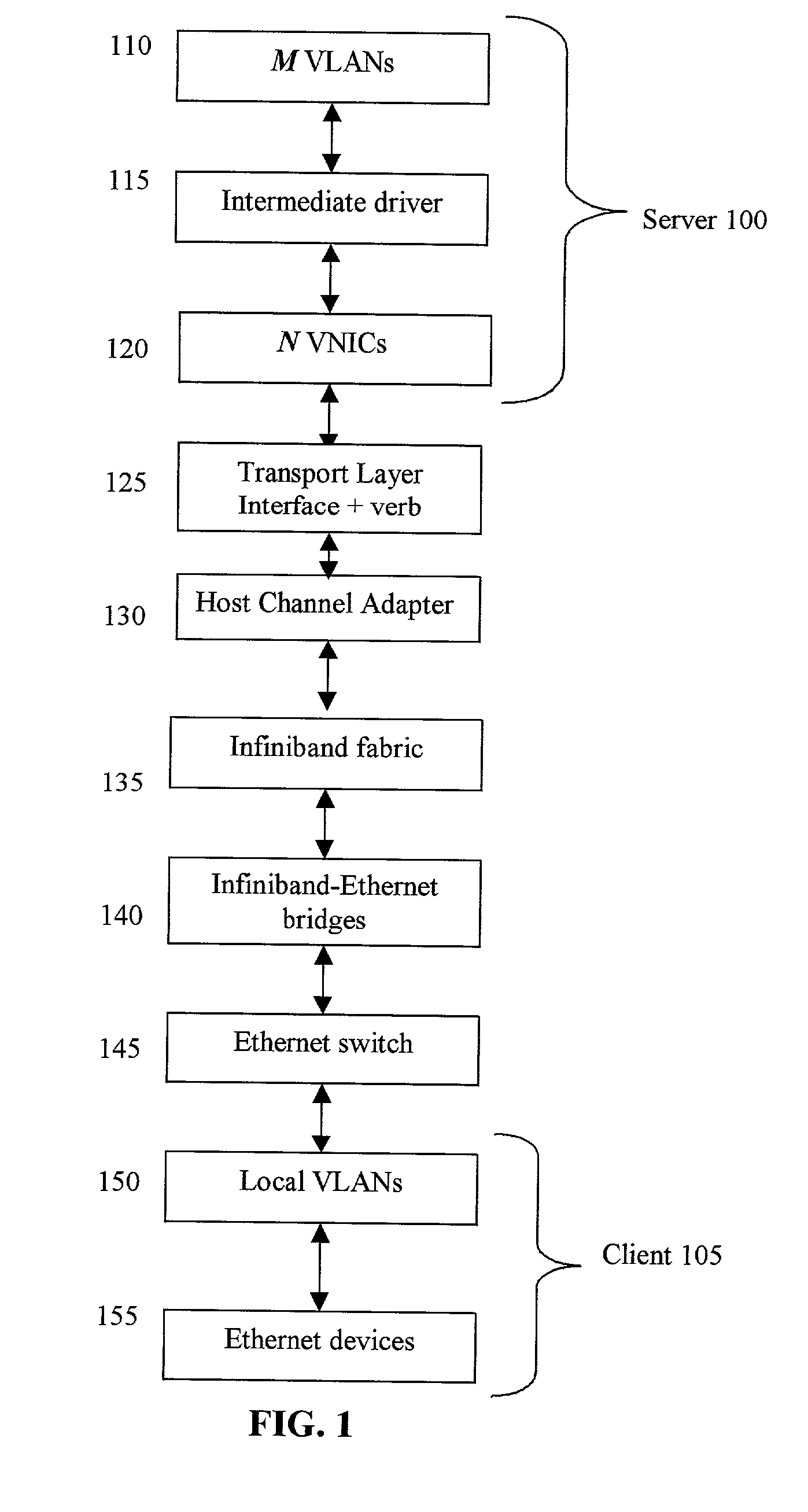
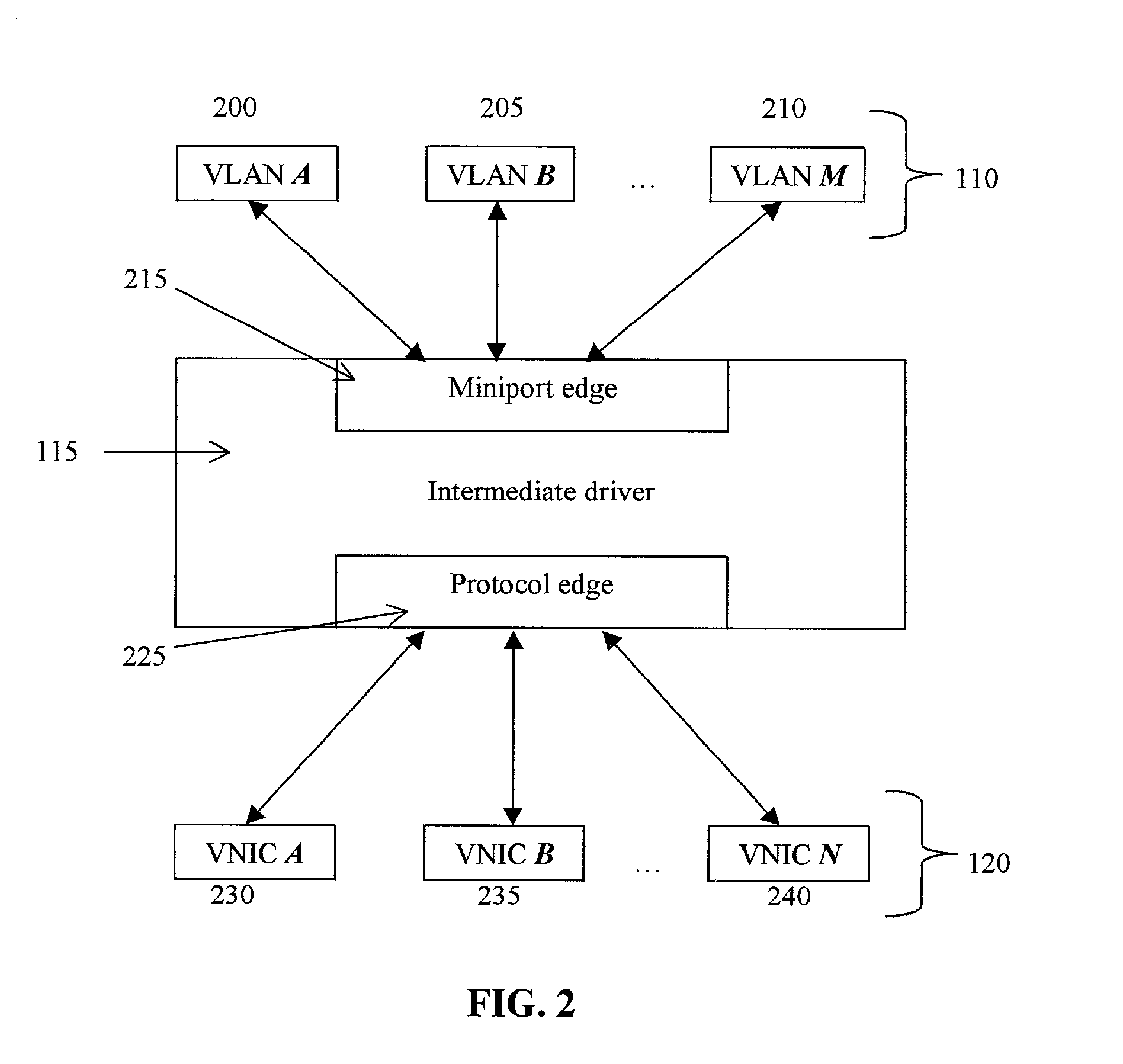
Network virtualization over infiniband
ActiveUS20140122675A1Digital computer detailsData switching networksBroadcastingNetwork virtualization platform
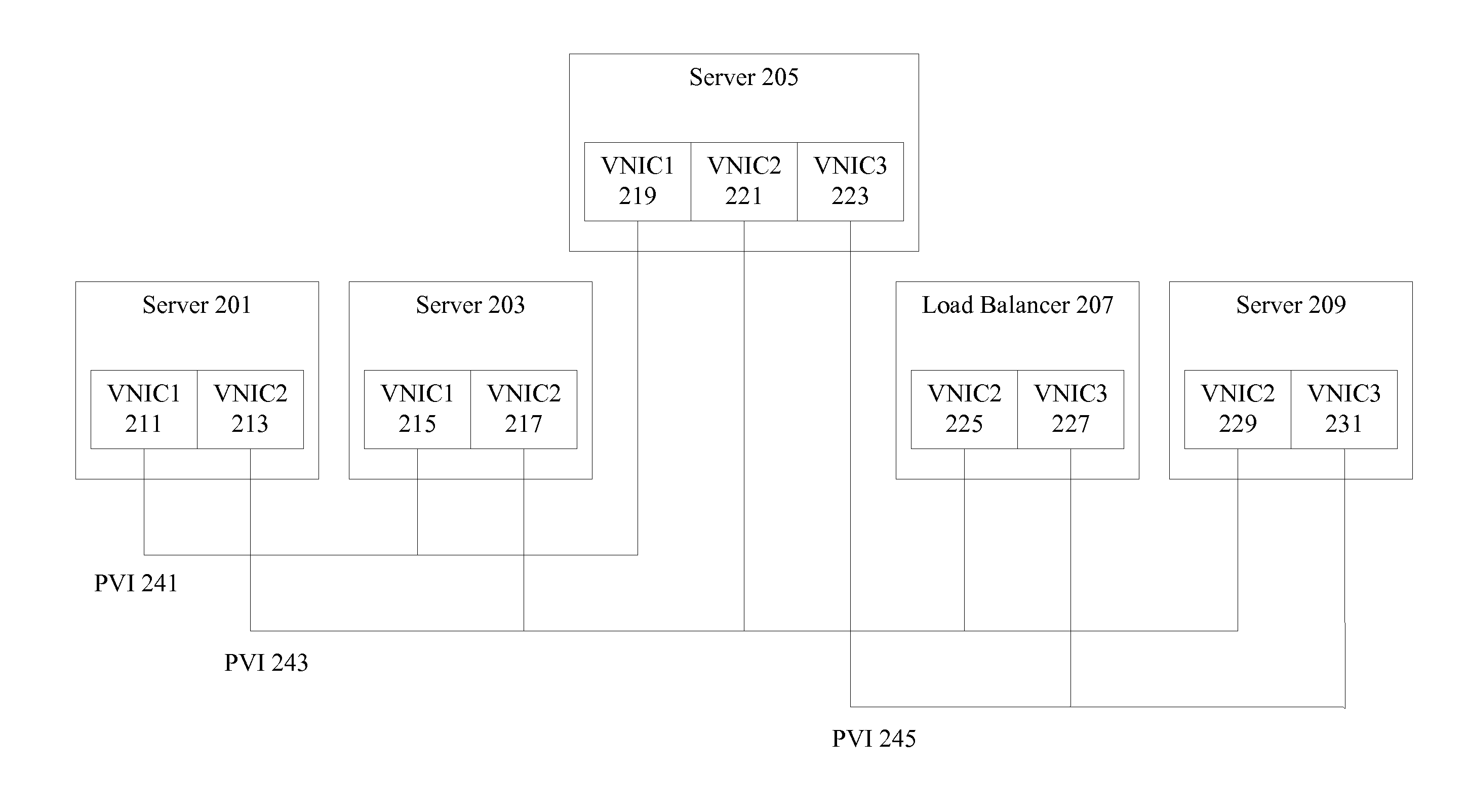
Mechanisms are provided to allow servers connected over an InfiniBand fabric to communicate using multiple private virtual interconnects (PVIs). In particular embodiments, the PVIs appear as virtual Ethernet networks to users on individual servers and virtual machines running on the individual servers. Each PVI is represented on the server by a virtual network interface card (VNIC) and each PVI is mapped to its own InfiniBand multicast group. Data can be transmitted on PVIs as Ethernet packets fully encapsulated, including the layer 2 header, within InfiniBand messages. Broadcast and multicast frames are propagated using InfiniBand.
Owner:ORACLE INT CORP
System and method for creating a secure tunnel for communications over a network
ActiveUS20110153793A1Sufficient informationCommunicate seamlesslyTime-division multiplexData switching by path configurationVirtual LANIp address
A system and method for establishing a virtual local area network (LAN) between a local device and a remote device are provided. The local device and the remote device may each have a physical and a virtual network interface card (NIC), and a virtual driver associated with each respective device virtual NIC may assign a Media Access Control (MAC) address to the virtual NIC and an Internet Protocol (IP) address to the physical NIC. The local device may communicate an IP to MAC address translation to the remote device that maps the assigned IP address to the assigned MAC address. Thereafter, the remote device may transmit secure data that can be received by the local device. For example, the remote device may encapsulate the data being communicated as well as the IP to MAC address translation for the local device into an HyperText Transfer Protocol (HTTP) request.
Owner:CA TECH INC
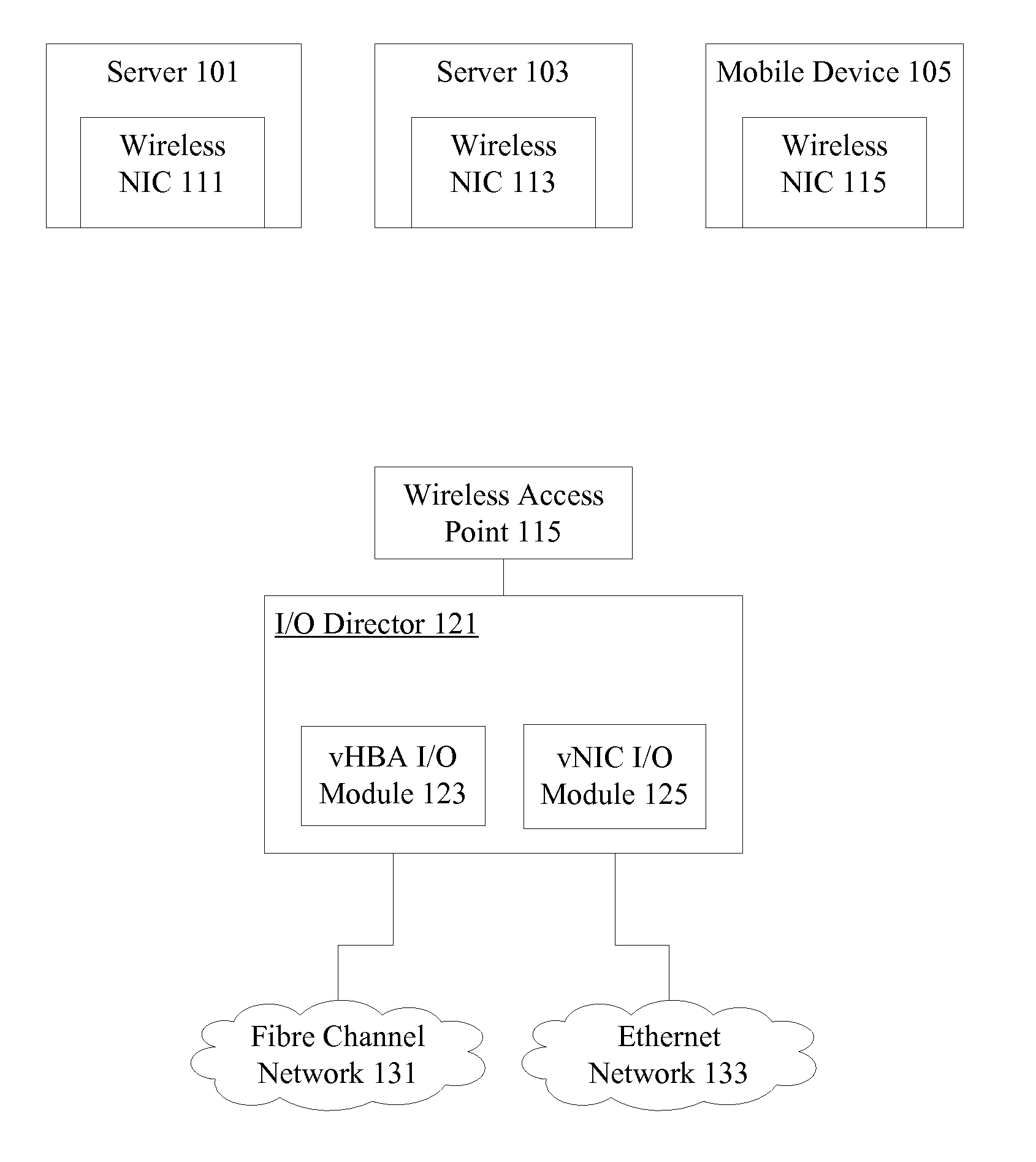
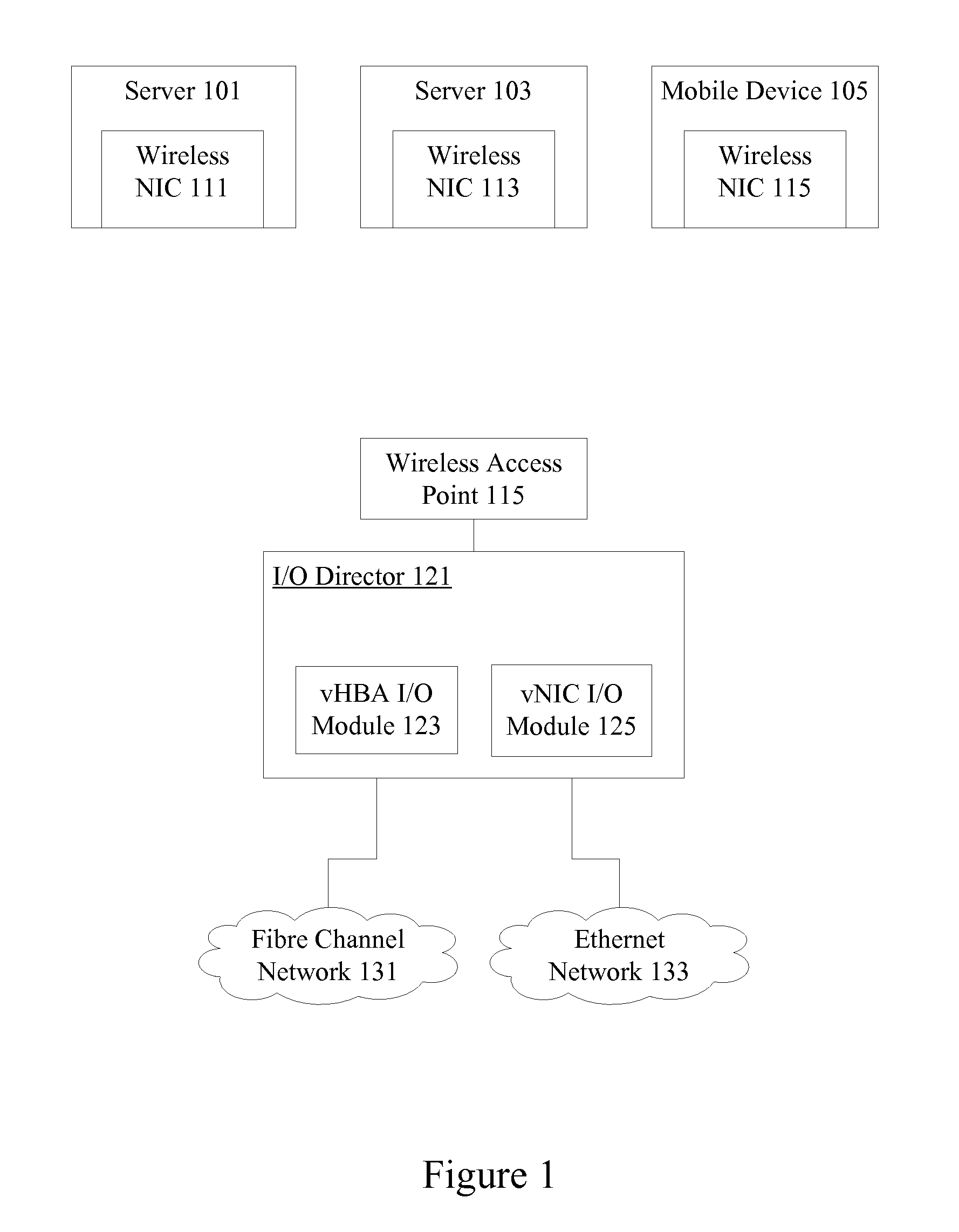
Wireless host I/O using virtualized I/O controllers
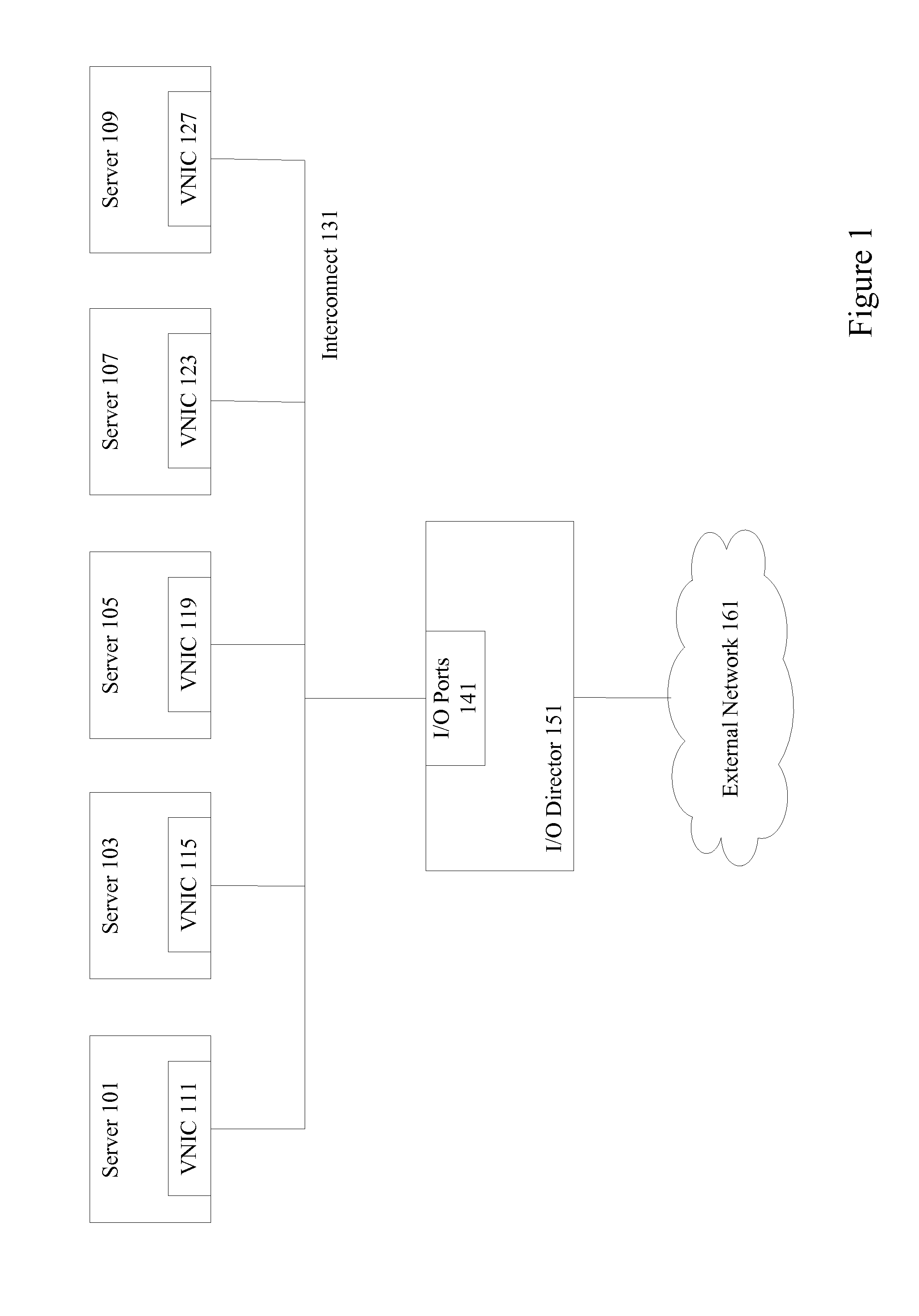
Mechanisms provide hosts such as servers and mobile devices with access to virtualized I / O resources including virtual Host Bus Adapters (vHBAs) and virtual Network Interface Cards (vNICs) over a wireless I / O interconnect. Host applications access virtualized I / O resources using virtual device drivers that communicate with virtualized I / O resources on an I / O director using a reliable communication protocol running over a wireless network. I / O data is throttled if necessary based on wireless network considerations.
Owner:ORACLE INT CORP
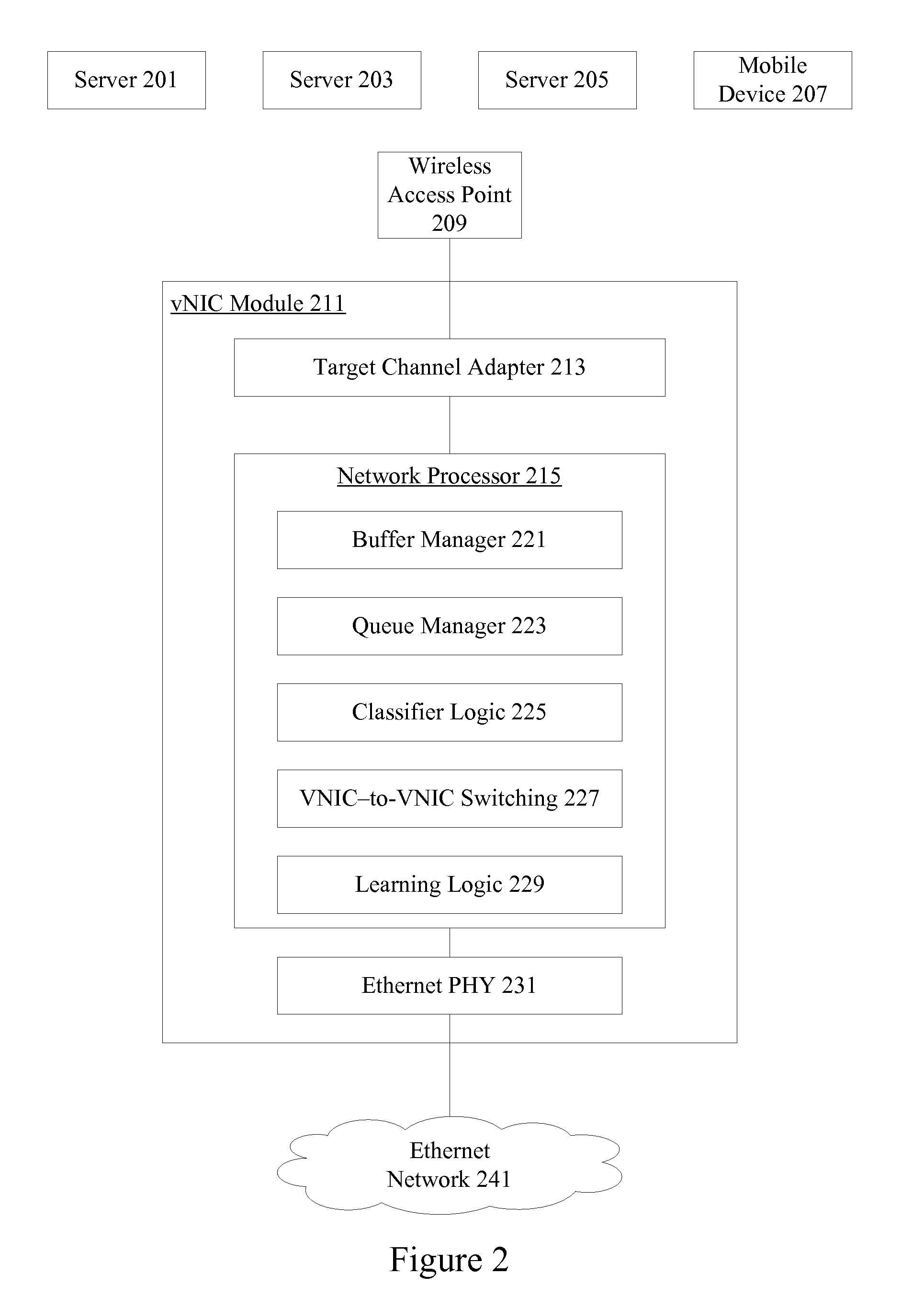
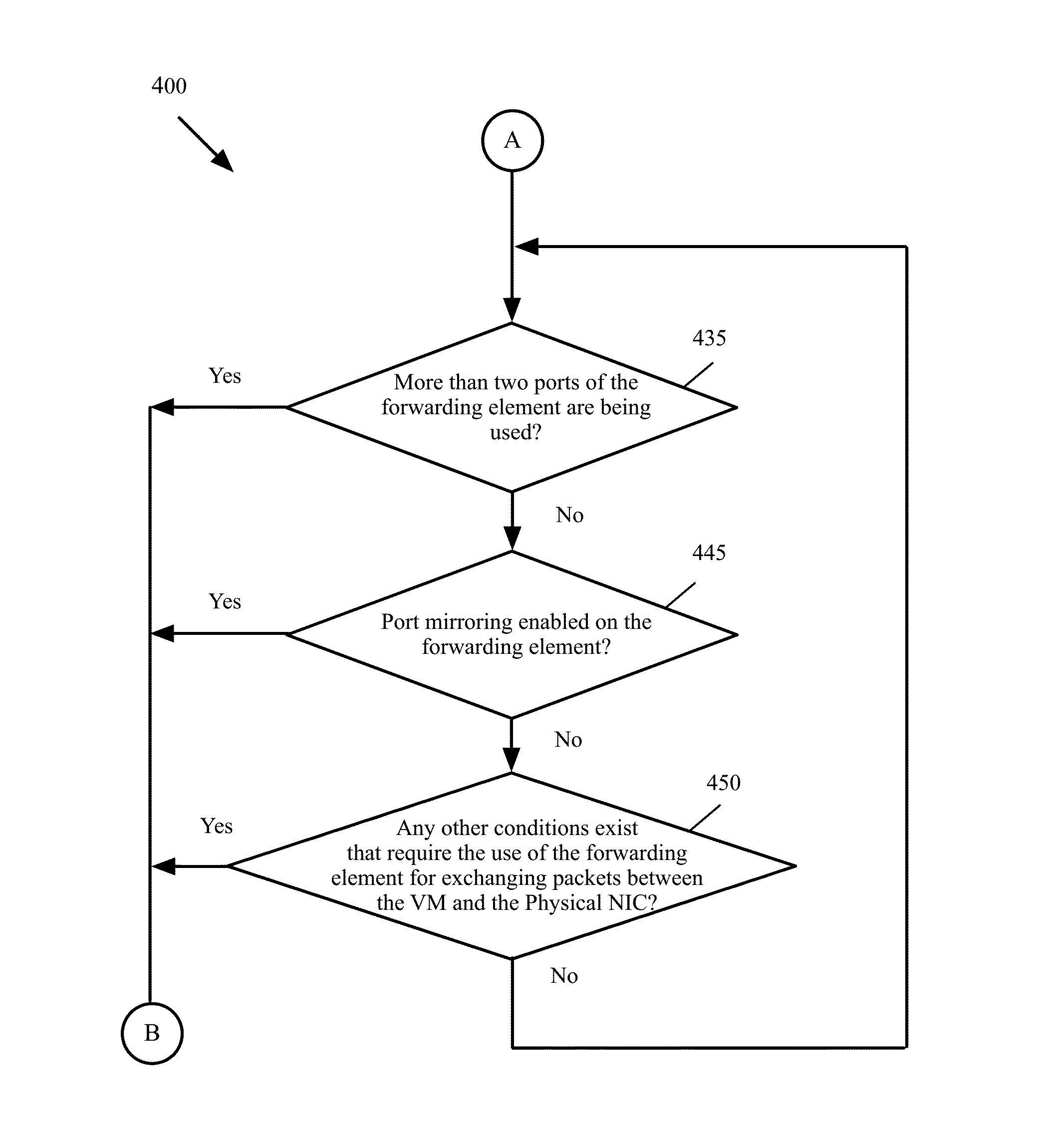
Specializing virtual network device processing to avoid interrupt processing for high packet rate applications
ActiveUS20160182342A1Reduce processing costsImprove packet processing performanceError preventionTransmission systemsNetwork processingVirtual network interface
A method of high packet rate network processing in a system that includes a physical host and a set of physical network interface controllers (PNICs). The physical host is hosting a set of data compute nodes (DCNs). Each DCN includes a virtual network interface controller (VNIC) for communicating with one or more PNICs to exchange packets. The method determines that a rate of packets received from a particular DCN at the VNIC of the particular DCN exceeds a predetermined threshold. The method performs polling to determine the availability of packets received at the VNIC from the particular DCN while the rate of packets received from the DCN at the VNIC is exceeding the threshold. The method utilizes interrupts to determine the availability of packets received at the VNIC from the particular DCN while the rate of packets received from the DCN at the VNIC does not exceed the threshold.
Owner:VMWARE INC
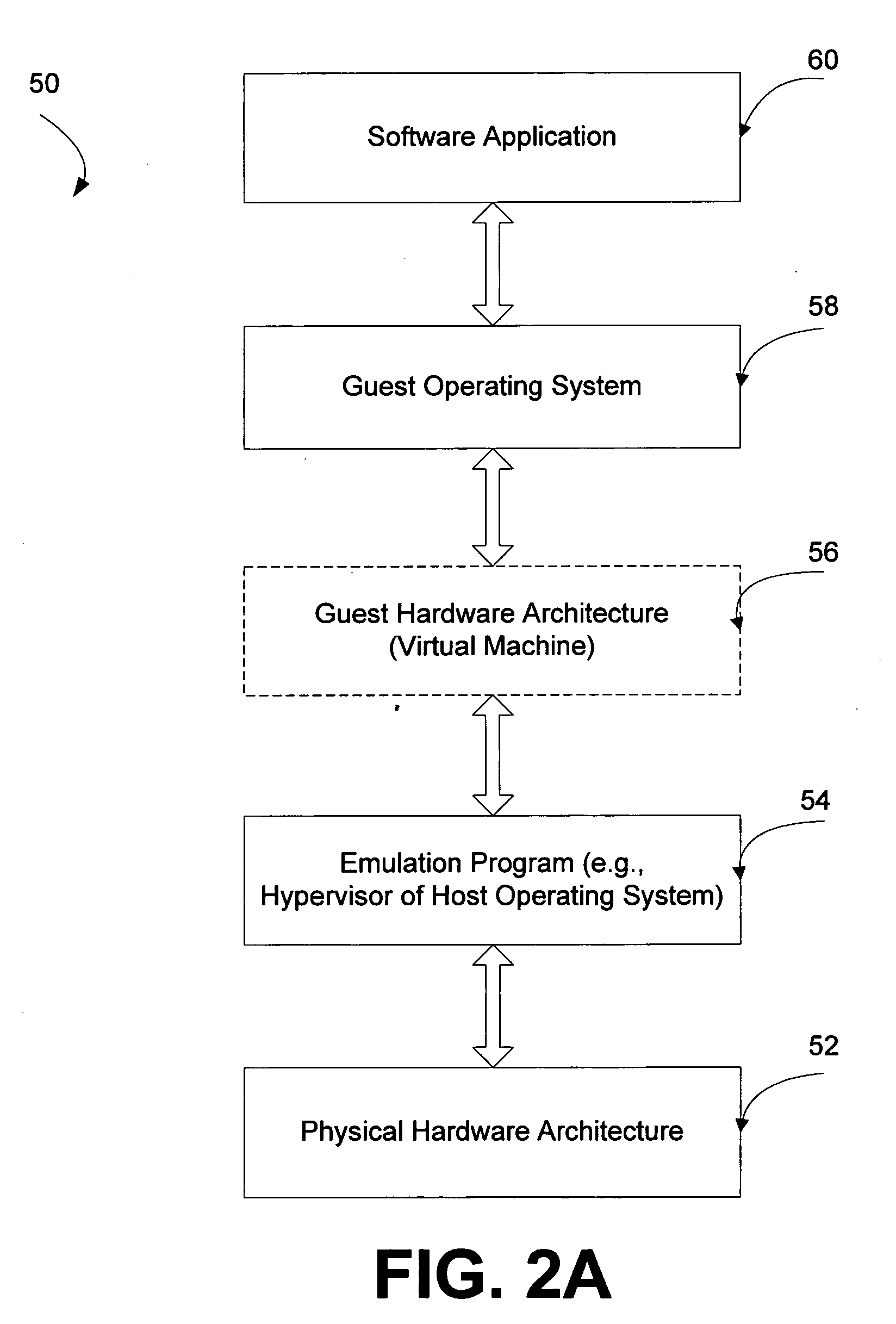
Methods and systems for provisioning a virtual disk to diskless virtual and physical mahcines
ActiveUS20090193413A1Reduce needDigital computer detailsSoftware simulation/interpretation/emulationVirtual computingComputer science
Methods and systems are described for provisioning a common virtual disk to both a physical and a virtual computing machine. These methods and systems can include creating a virtual disk that has binding information for both a paravirtual network interface card and a physical network interface card so that, either a virtual machine having a paravirtual network interface card, or a physical machine having a physical network interface card, may boot from the created virtual disk. Creation of the virtual disk can include exposing the paravirtual network interface card to a physical machine so that an installer program may bind to both the paravirtual network interface card and the physical network interface card.
Owner:CITRIX SYST INC
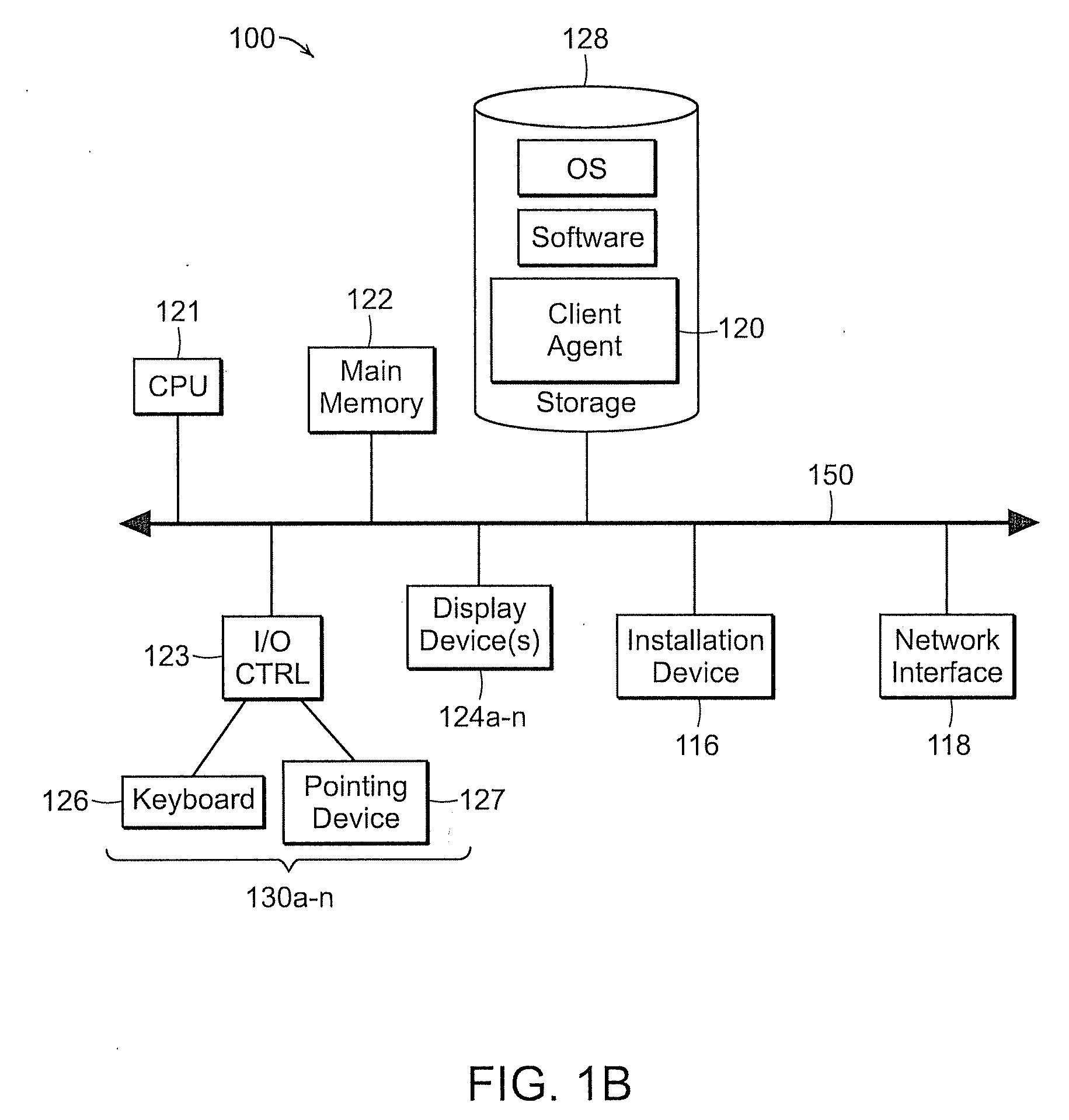
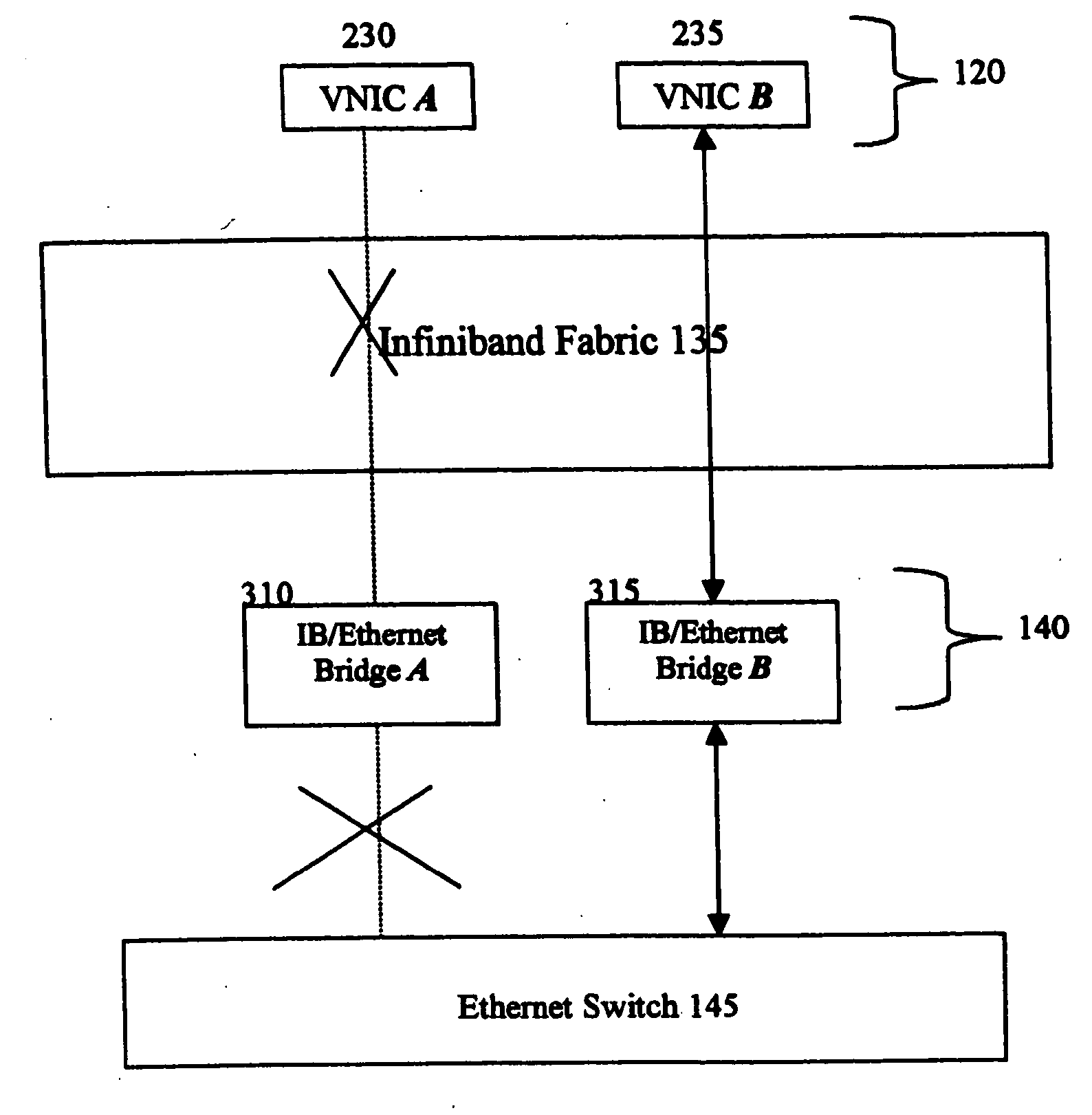
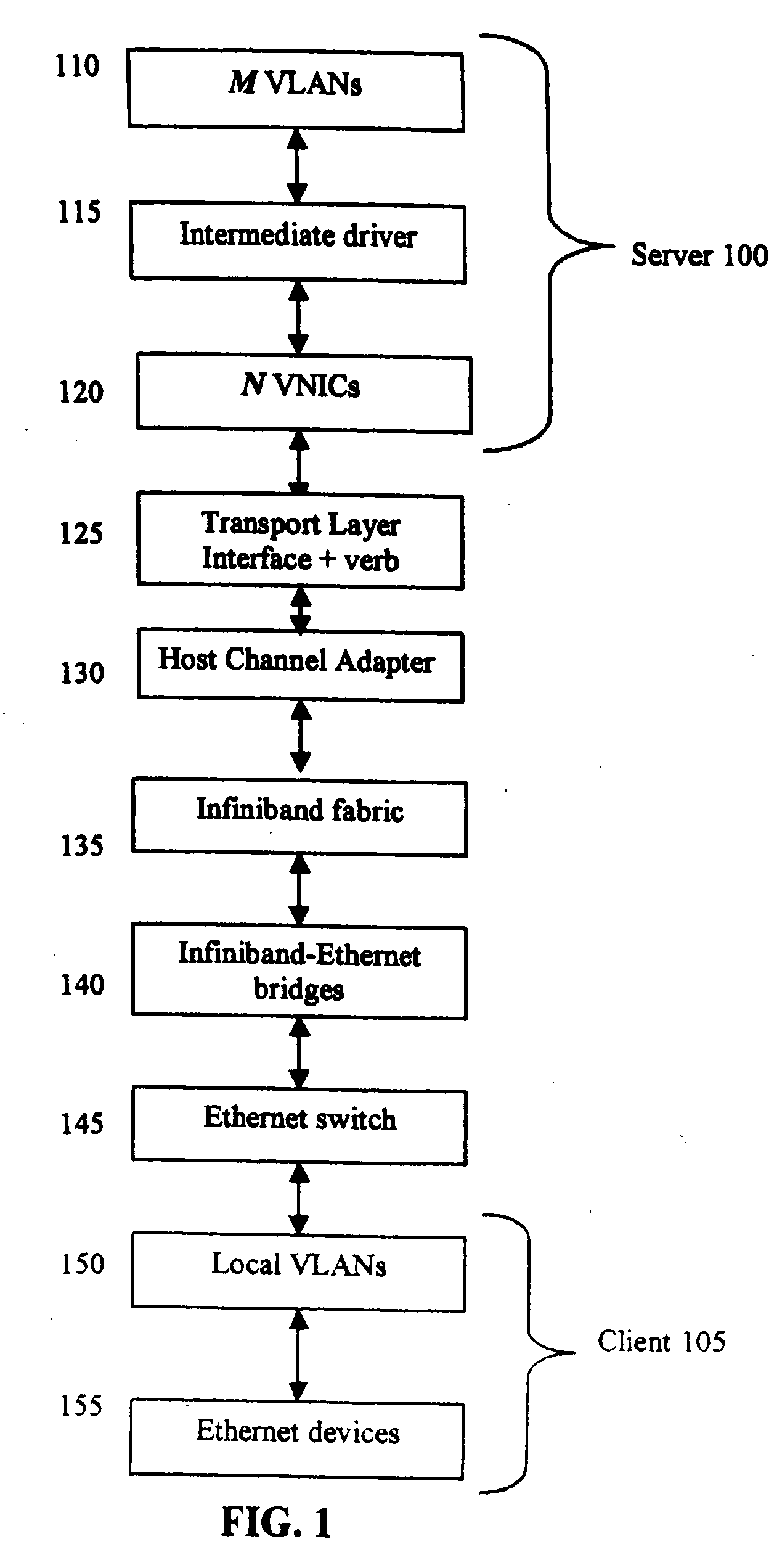
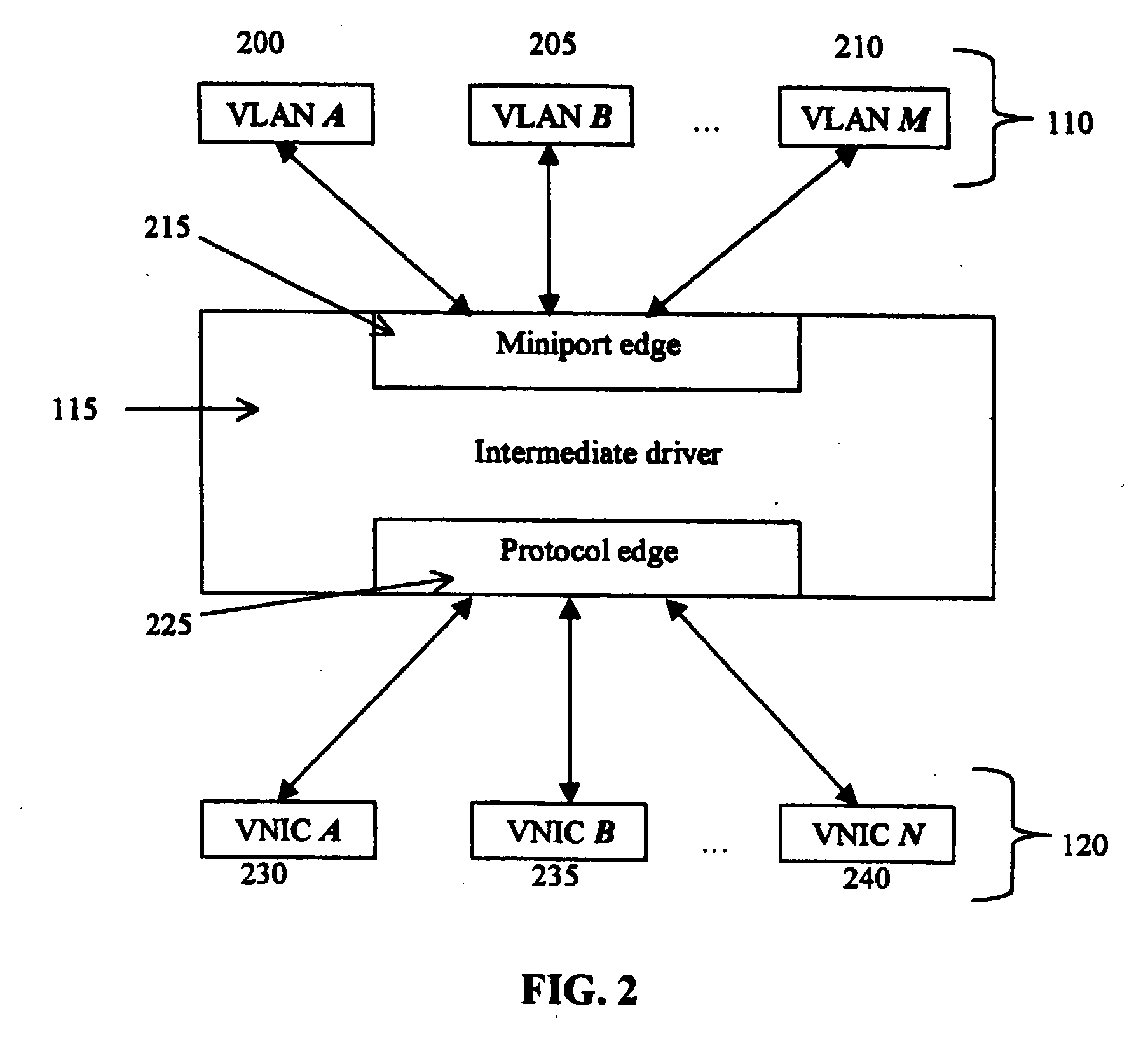
Intermediate driver having a fail-over function for a virtual network interface card in a system utilizing Infiniband architecture
ActiveUS6963932B2Error detection/correctionMultiple digital computer combinationsFailoverClient-side
A system to facilitate data transfer between a server and a client in an uninterrupted manner. At least one server network communicates data via a first Input / Output (I / O) architecture. At least two Virtual Network Interface Cards (VNICs) communicate the data via the first I / O architecture. A client network communicates data via a second I / O architecture. At least two bridging devices convert packets useable in the first I / O architecture to packets useable in the second I / O architecture. No more than one of the at least two bridging devices transfers the data with any one of the at least two VNICs, and the at least two bridging devices transfer the data with the client network. At least one intermediate driver binds to the at least one server network and to the at least two VNICs. The at least one intermediate driver provides a fail-over function to maintain a connection between the server network and the client network.
Owner:INTEL CORP
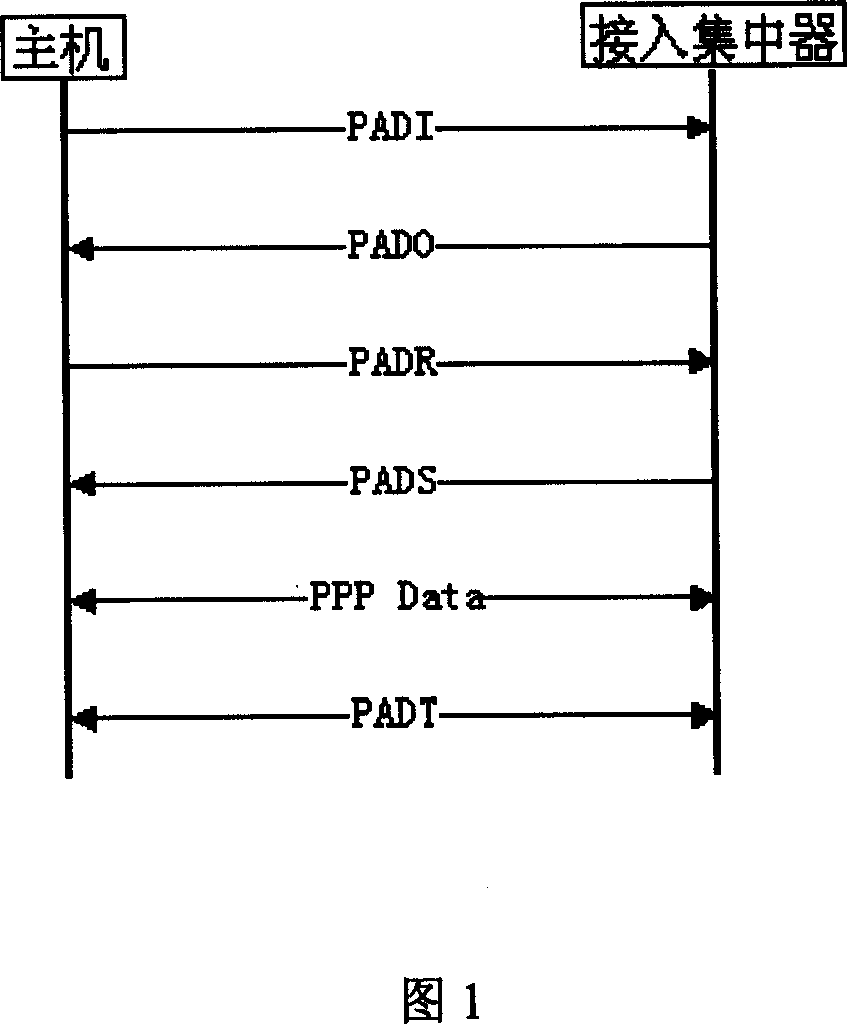
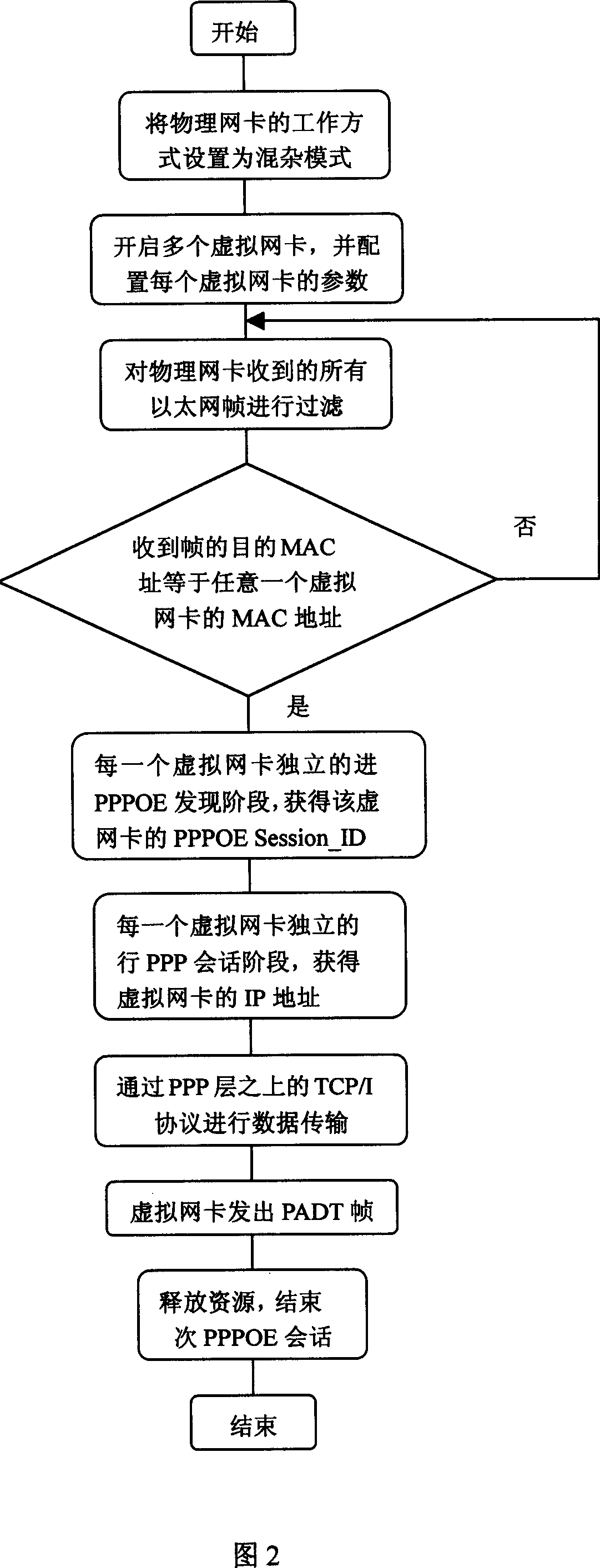
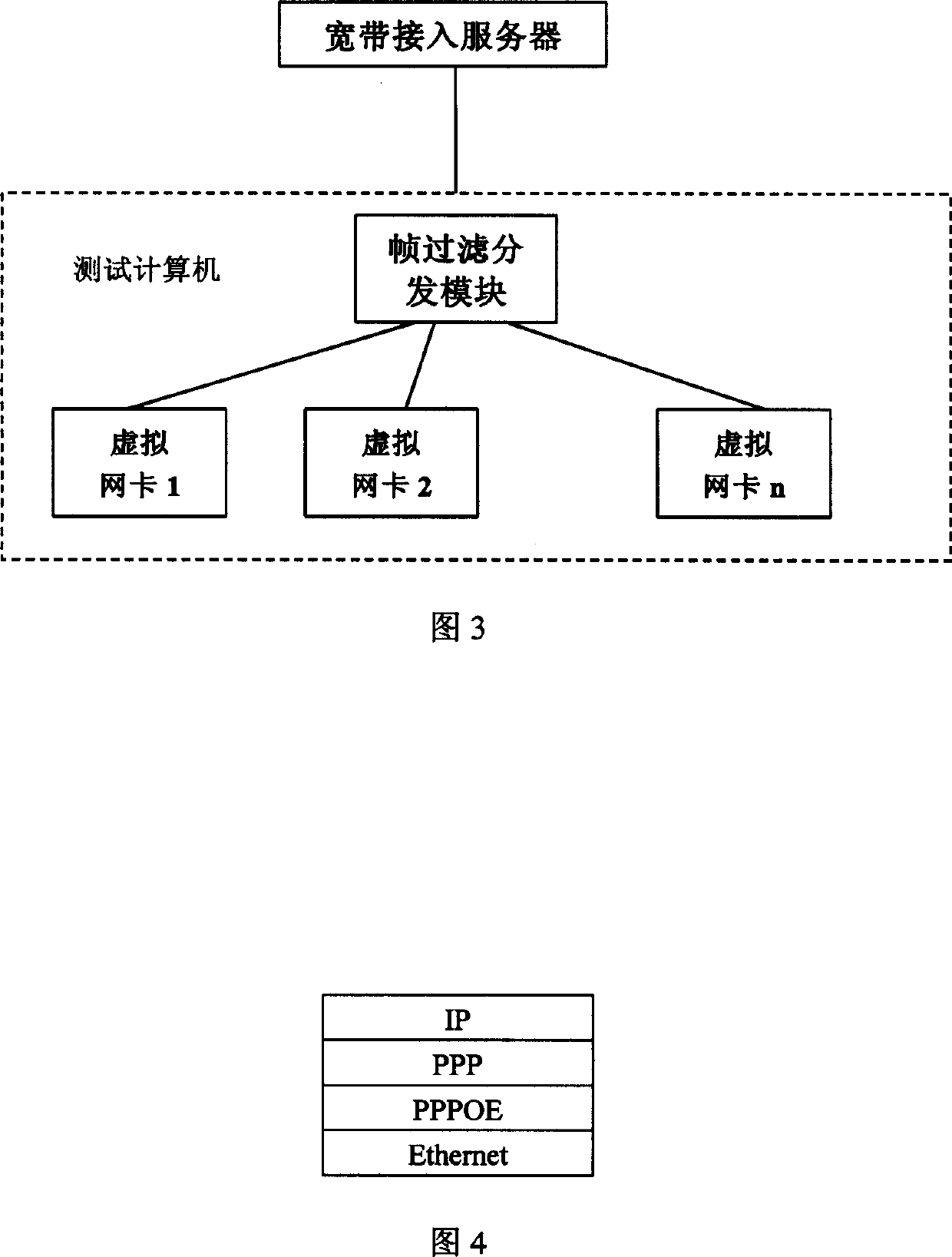
Broad-band insertion service apparatus dialing testing method
InactiveCN1462131AFully testedLow test cost inputSubscriber signalling identity devicesTransmission monitoringWidebandPhysical network
A dialing test method for broad band insertion server features that a cheap computer and a network card are only used to simulate hundred users. It includes such steps as using a physical network card to simulate multiple virtual network cards, assigning a uniqe MAC address to each of the virtual network cards, receiving the frames from wideband access server, and transmitting them with differentMAC sources to different virtual network cards.
Owner:ZTE CORP
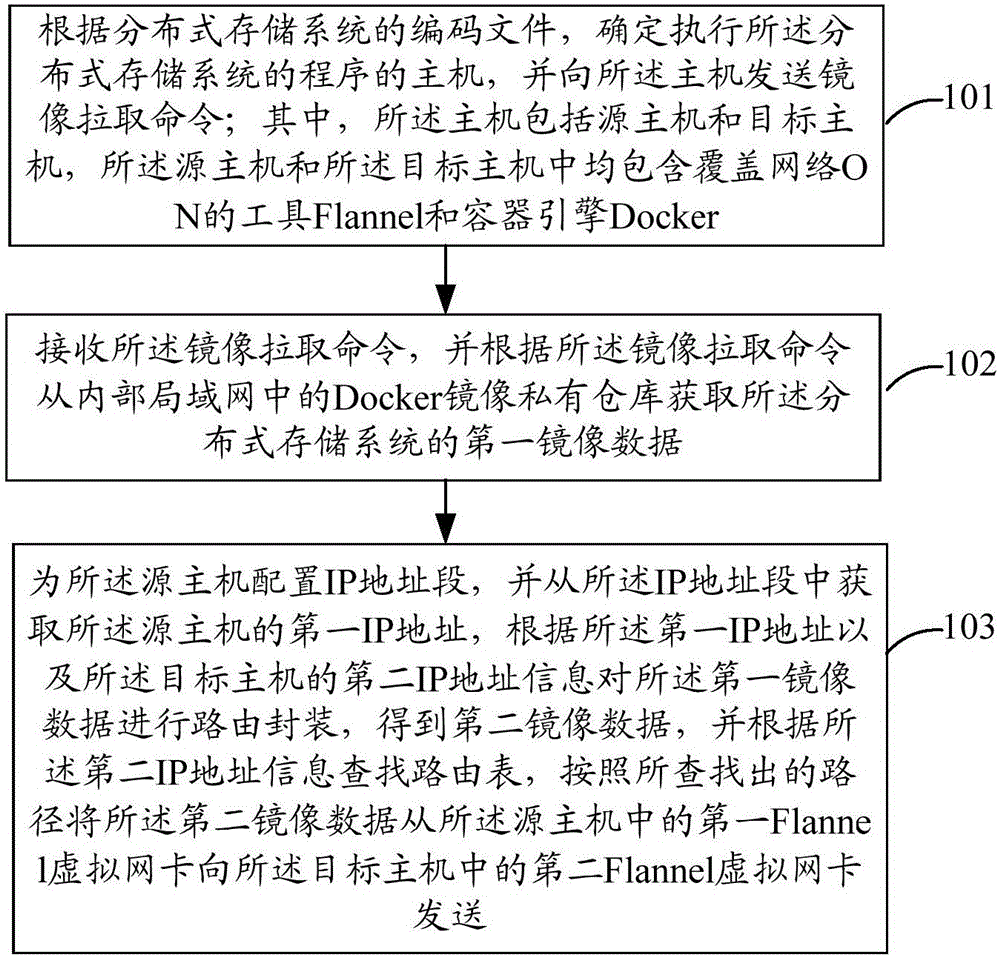
Deployment method and device realizing distributing type storage system
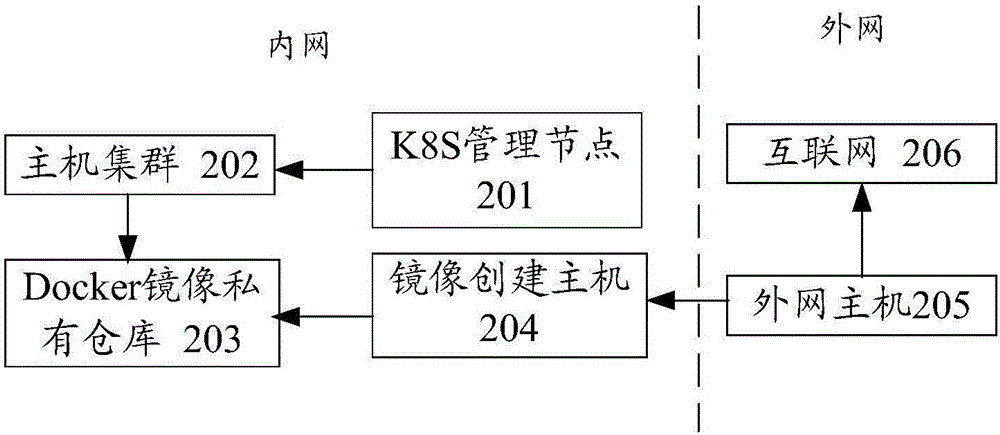
The invention discloses a deployment method realizing a distributing type storage system. The deployment method comprises the following steps that a mainframe executing programs is determined and a mirroring pulling instruction is sent to the mainframe according to an encoding file in the distributing type storage system, wherein the mainframe comprises a source mainframe and a target mainframe and the source mainframe and the target mainframe each include Flannel and Docker; first mirroring data in the distributing type storage system is obtained from a private warehouse of Docker mirroring at an intranet according to the mirroring pulling instruction; an IP address field is configured for the source mainframe and a first IP address of the source mainframe is obtained from the IP address field; routing encapsulation is performed on the first mirroring data according to the first IP address and information about a second IP address of the target mainframe and second mirroring data is then obtained; a routing table is searched according to the information about the second IP address; the second mirroring data is sent from a first Flannel virtual network interface card in the source mainframe to a second Flannel virtual network interface card in the target mainframe according to a found route in the routing table. The invention meanwhile discloses a deployment device realizing the distributing type storage system.
Owner:MIGU VIDEO TECH CO LTD
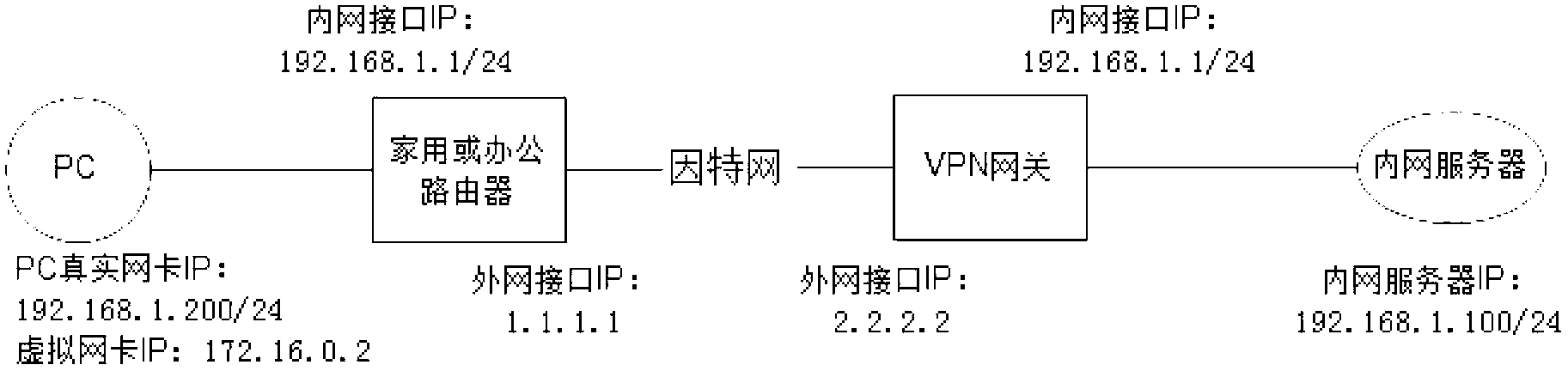
Method and device for accessing intranet resource of virtual private network (VPN) server
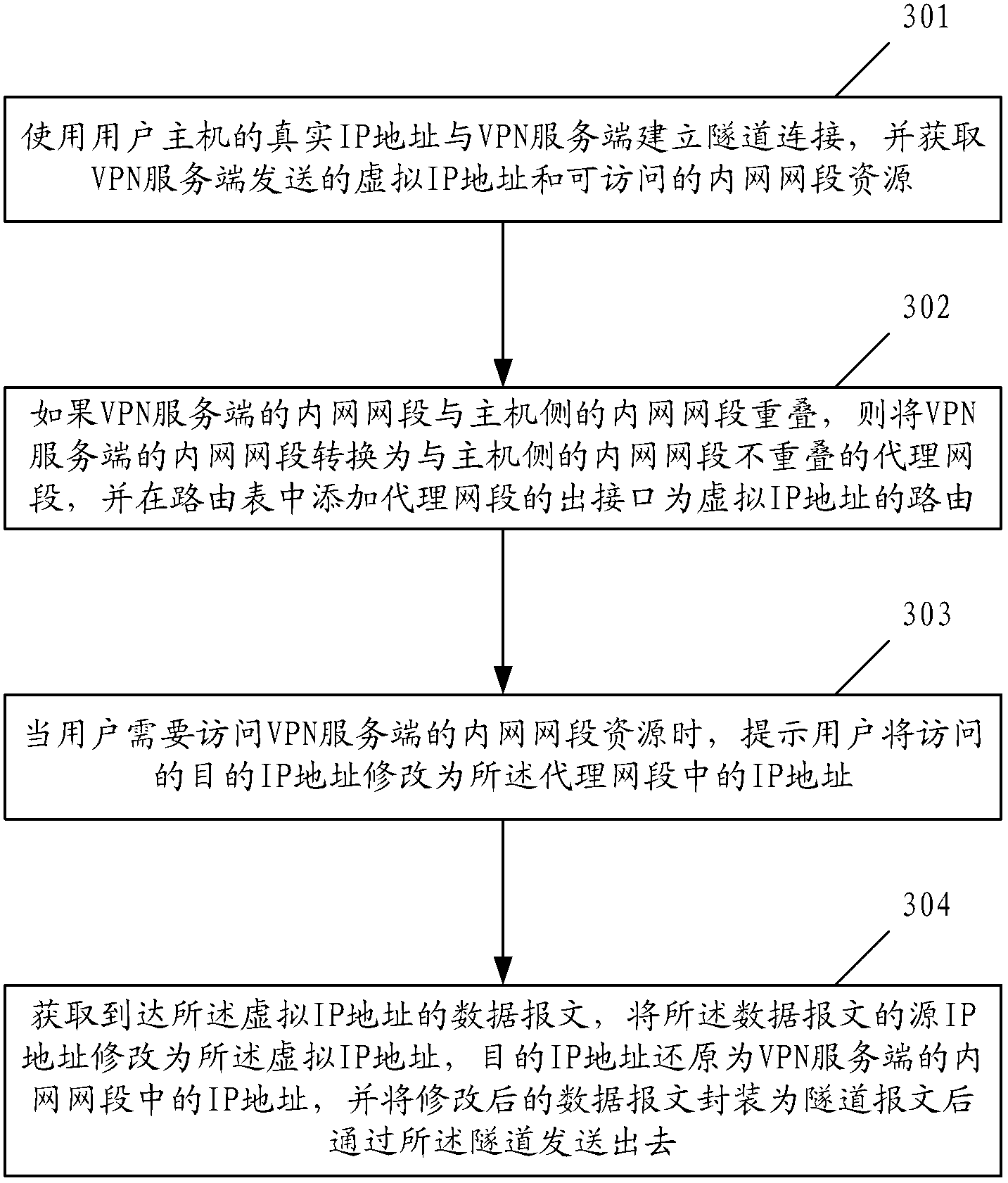
The invention provides a method and device for accessing an intranet resource of a virtual private network (VPN) server. The method includes that a real internet protocol (IP) address is used for building tunnel connection with the VPN server, and a virtual IP address sent by the VPN server and an accessible intranet section resource are obtained; an intranet section of the VPN server is overlapped with an intranet section of a host side, the intranet section of the VPN server is changed into a proxy network section which is not overlapped with the intranet section of the host side, and an output interface of the proxy network section is added into a routing table and used as a virtual IP route; if addresses are overlapped, users are prompted to revise an accessed target IP address into an IP address in the proxy network section; and a datagram reaching a virtual network interface card is obtained, the target IP address is restored into the IP address in the intranet section of the VPN server, and the datagram is packaged into a tunnel datagram and sent out through a tunnel. By means of the method and device, the problem that a user host can not access the intranet resource of the VPN server normally due to address overlapping can be solved.
Owner:杭州迪普信息技术有限公司
Method, network card and communication system for binding physical internet ports
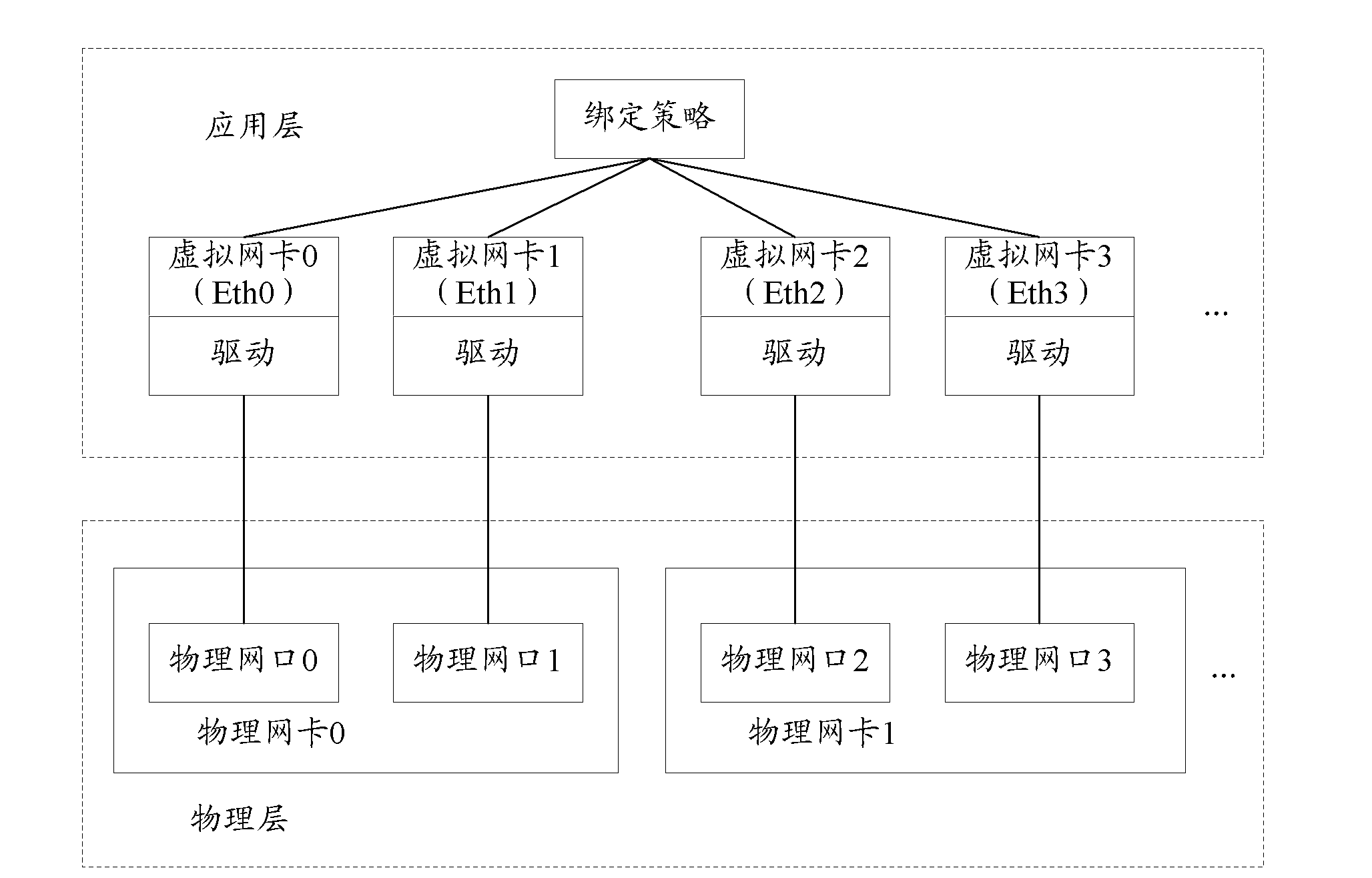
ActiveCN102137169ARequirements for realizing secondary bindingMeet business needsData switching detailsCommunications systemProtocol Application
The invention discloses a method, a network card and a communication system for binding physical internet ports. The method comprises the steps of building a virtual port which corresponds to a virtual network card in an application layer, and binding the virtual port with other ports established in the application layer by application layer software; adding the multiple physical network ports needing to be bound to the established virtual ports; obtaining available physical ports which are determined to be normal in communication when the physical network ports in the visual ports are normal; and choosing one or multiple physical network ports from the available physical ports to receive and send messages according to an allocation mode when the messages need to be received and sent. According to the embodiment of the invention, the secondary binding of the physical network ports can be realized, thereby meeting business requirements better.
Owner:HUAWEI TECH CO LTD
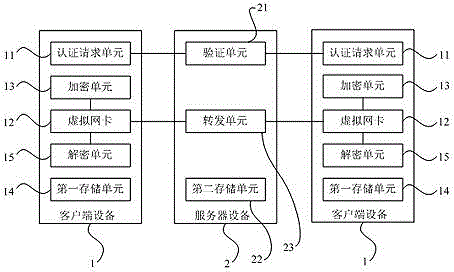
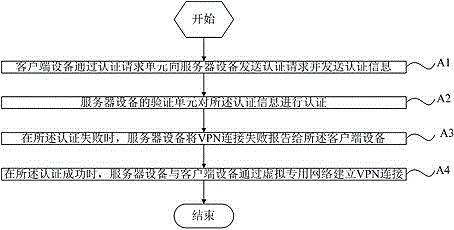
Virtual private network communication system, connection method and data packet transmission method
The invention discloses a virtual private network communication system. The virtual private network communication system comprises a plurality of client apparatuses and a server apparatus which establishes VPN connection with the client apparatuses through a virtual private network by using a preset protocol, wherein each of the client apparatuses comprises an authentication request unit, a first storage unit, a virtual network interface card and an encryption unit; the authentication request units are used for sending authentication information to the server apparatus to authenticate; the first storage units are used for storing the MAC address linked list of opposite-end client and the IP address of the server apparatus; the virtual network interface cards are provided with virtual IP addresses belonging to the virtual private network; the encryption units correspond to the virtual network interface cards and are used for encrypting the data packets which need to be sent from the virtual network interface cards. The invention also discloses a virtual private network connection method and a data packet transmission method. According to the virtual private network communication system, the virtual private network connection method and the data packet transmission method, an N2N structure is used for realizing the VPN network so as to ensure that the privacies of both sides of the communication are not revealed, the structure is concise and clear and simplicity and simplification are realized.
Owner:PHICOMM (SHANGHAI) CO LTD
Load balancing method, server and system for virtual machine cluster
ActiveCN103384255ASolve insecurityData switching networksPhysical networkVirtual network interface card
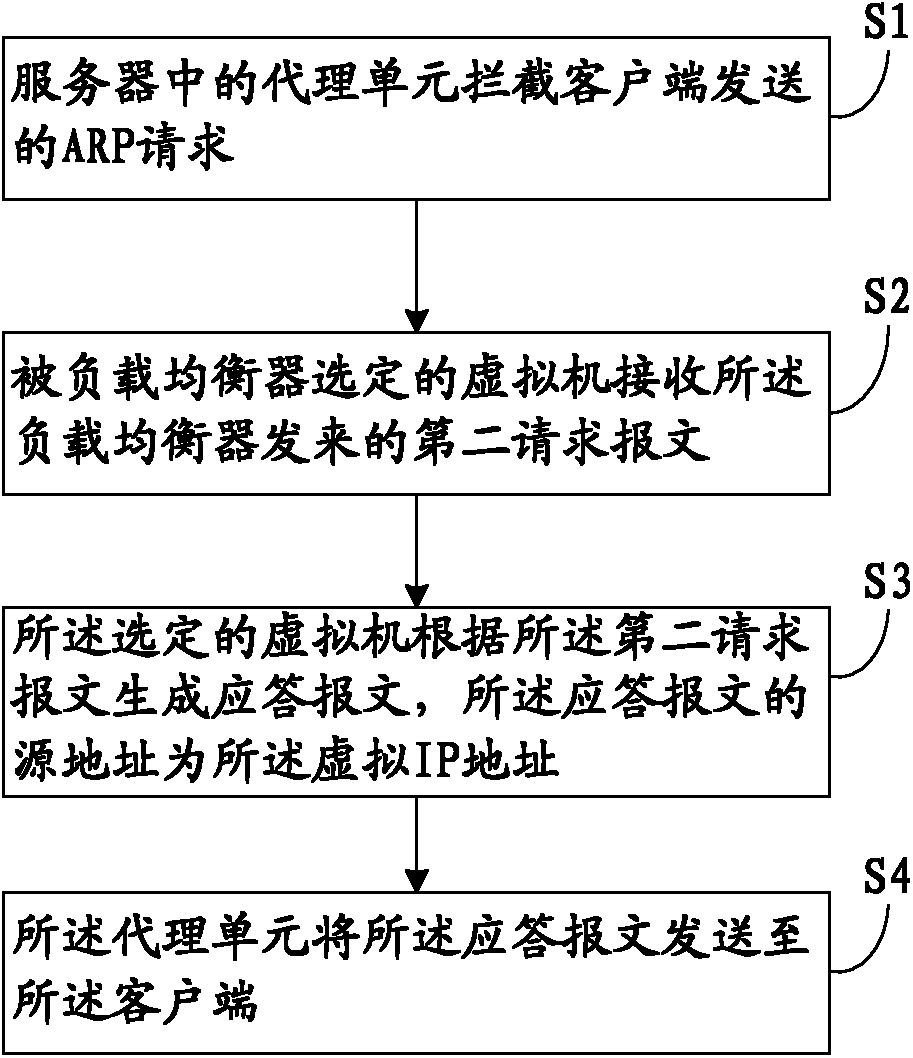
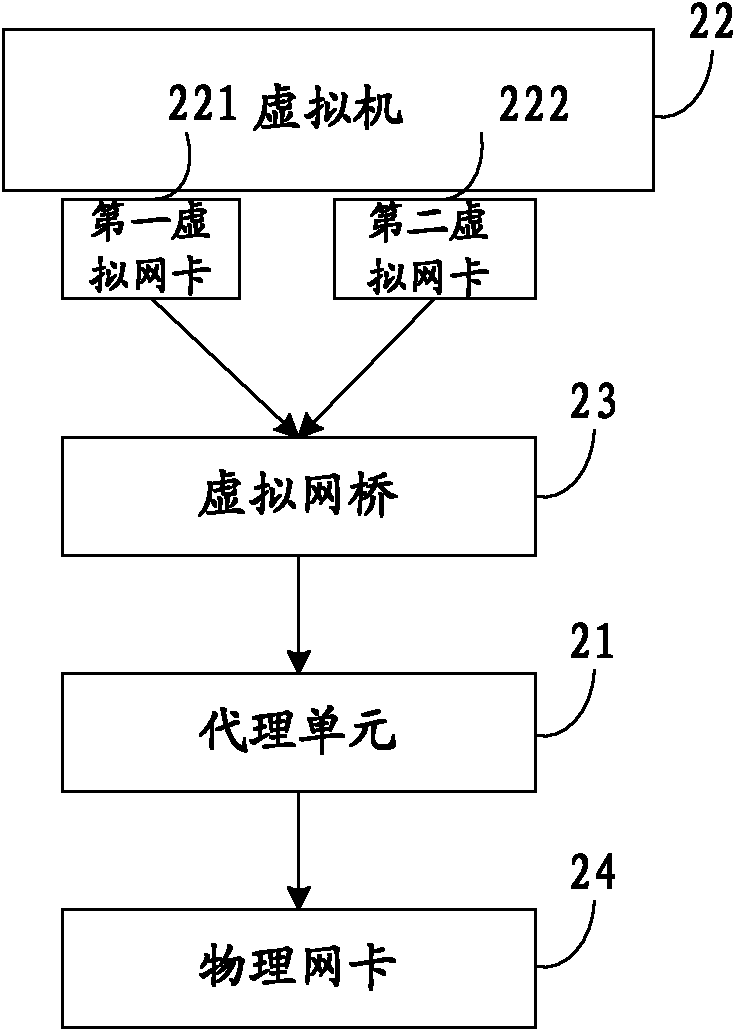
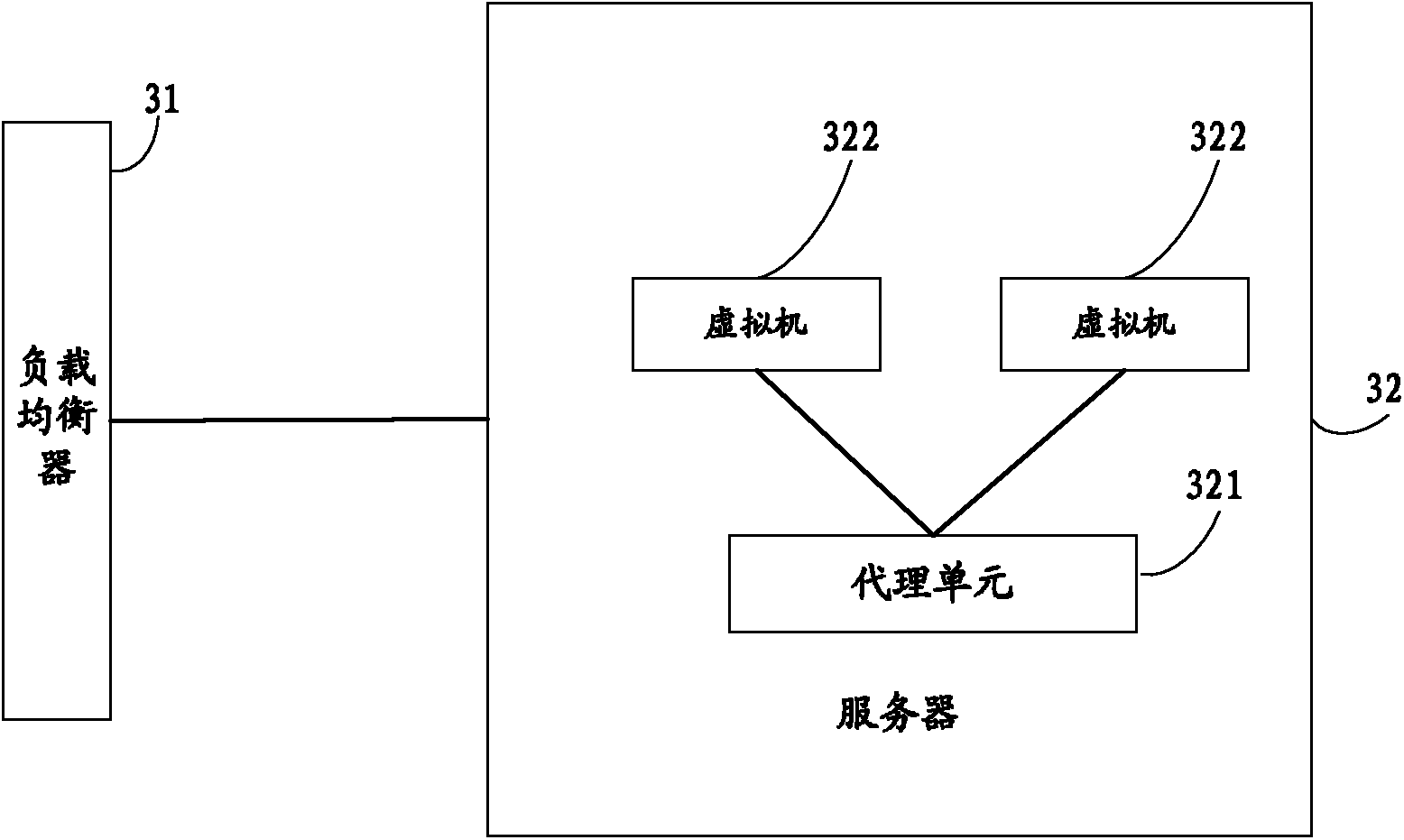
The invention discloses a load balancing method, server and system for a virtual machine cluster. The method is applied to a server where at least one virtual machine is established and comprises the steps that an agency unit which is arranged between a virtual network interface card of the virtual machine and a physical network interface card of the server in the server intercepts ARP requests sent by a client, the agency unit can configure a virtual IP address identical with the IP address of a load balancer for each virtual machine, the virtual machine chosen by the load balancer can receive second request message sent by the load balancer, the chosen virtual machine can generate response message according to the second request message, a source address of the response message is the virtual IP address, and the agency unit can send the response message to the client. By means of the load balancing method, load balance can be achieved without carrying out configuration in the virtual machine, and the safety of the system is improved.
Owner:CHENGDU HUAWEI TECH
Network architecture based on cloud computing and virtual network management method thereof
InactiveCN102413190AAutomate managementReduce transmission delayEnergy efficient ICTNetworks interconnectionIp addressNetwork architecture
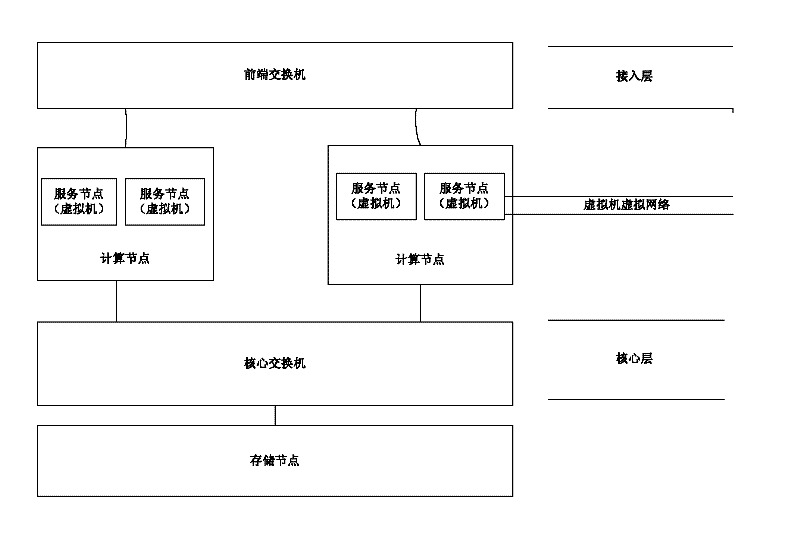
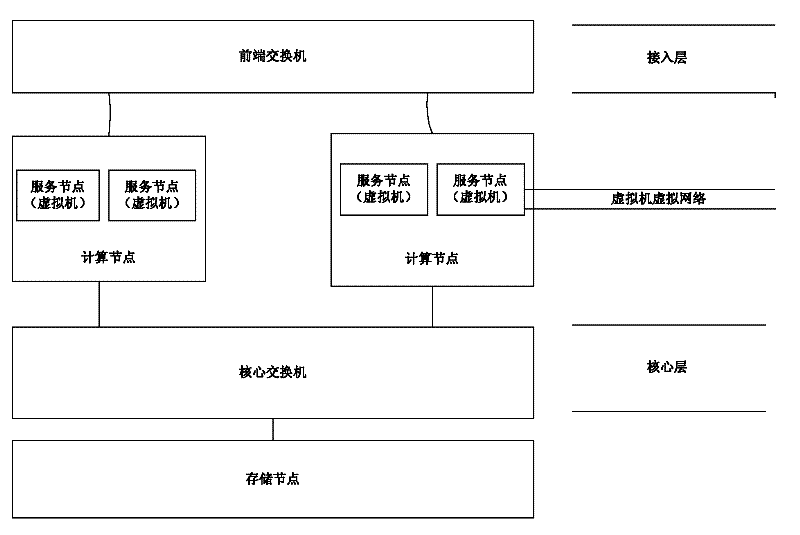
The invention relates to the technical field of cloud computing networks, particularly a network architecture based on cloud computing and a virtual network management method thereof. The network architecture based on cloud computing is implemented by three-layer virtualization: access layer virtualization, core layer virtualization and virtual machine virtual network. Access layer virtualization: virtualizing network resources on the access layer, thereby implementing the functions of bandwidth allocation, IP (Internet Protocol) address allocation, security access control and the like. Core layer virtualization: virtualizing core layer network devices, and directly intercommunicating service nodes and a service node and a storage node. Virtual machine virtual network: implementing a virtual network card and a virtual switching machine in a computation node. The virtual network card implements connection through the virtual switching machine, and is communicated with an external network. The invention solves the problem in managing the cloud computing network resources through three-layer virtualization technology, and improves the network performance; and the invention can be widely used in virtual networks.
Owner:GUANGDONG ELECTRONICS IND INST
Intermediate driver having a fail-over function
InactiveUS20060200584A1Multiple digital computer combinationsNetworks interconnectionFailoverVirtual network interface
A system to facilitate data transfer between a server and a client in an uninterrrpted manner. At least one server network communicates data via a first Input / Output (I / O) architecture. At least two Virtual Network Interface Cards (VNICs) communicate the data via the first I / O architecture. A client network communicates data via a second I / O architecture. At least two bridging devices convert packets useable in the first I / O architecture to packets useable in the second I / O architecture. No more than one of the at least two bridging devices transfers the data with any one of the at least two VNICs, and the at least two bridging devices transfer the data with the client network. At least one intermediate driver binds to the at least one server network and to the at least two VNICs. The at least one intermediate driver provides a fail-over function to maintain a connection between the server network and the client network.
Owner:INTEL CORP
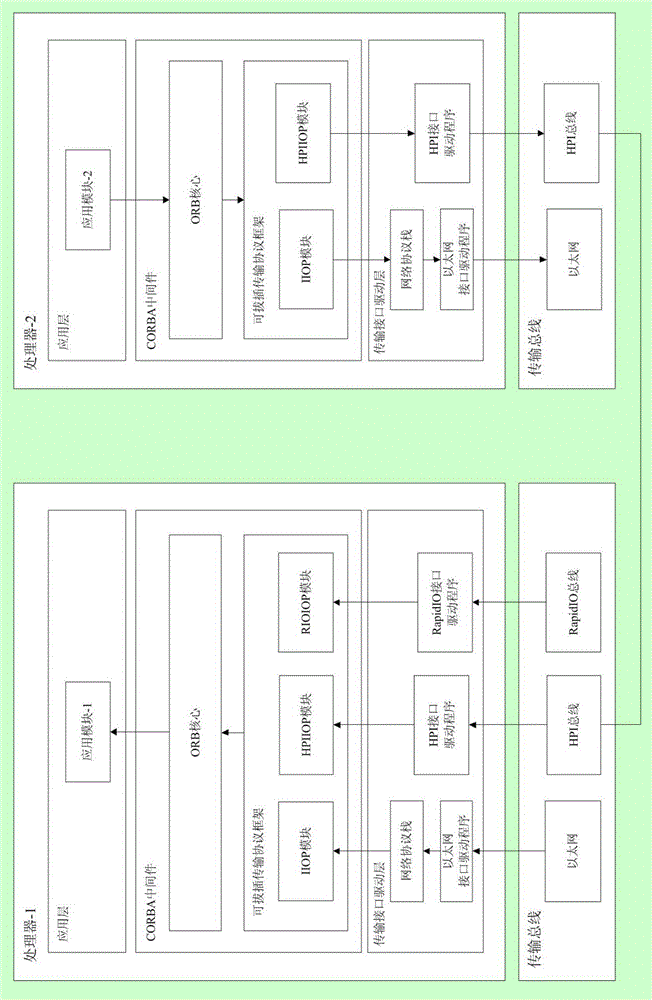
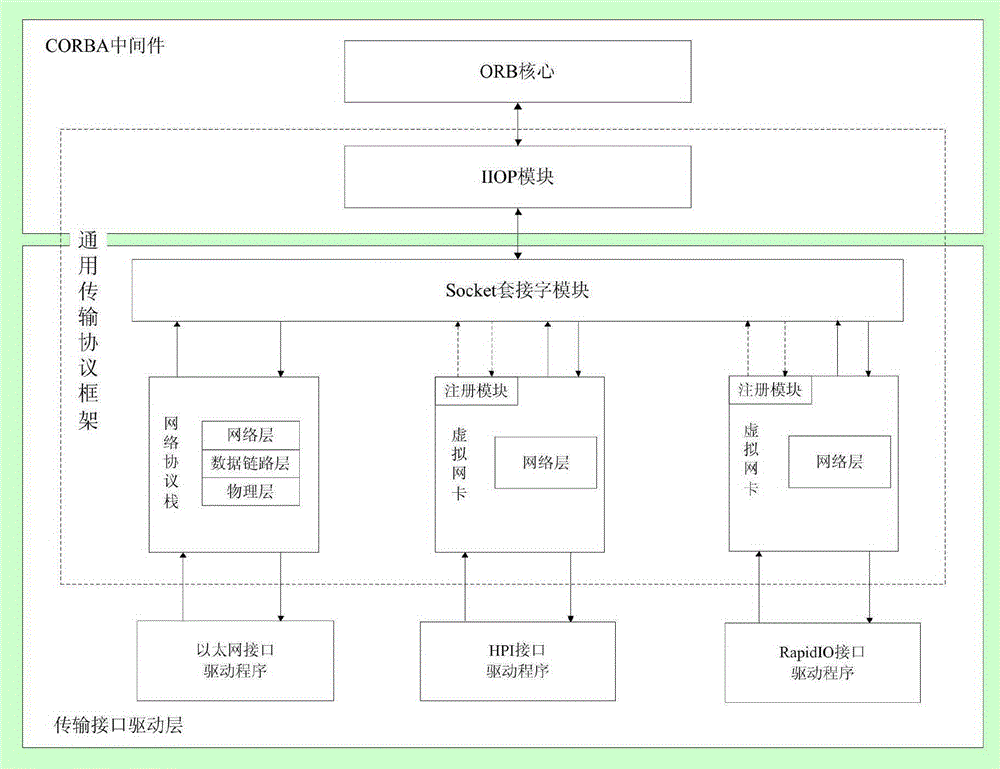
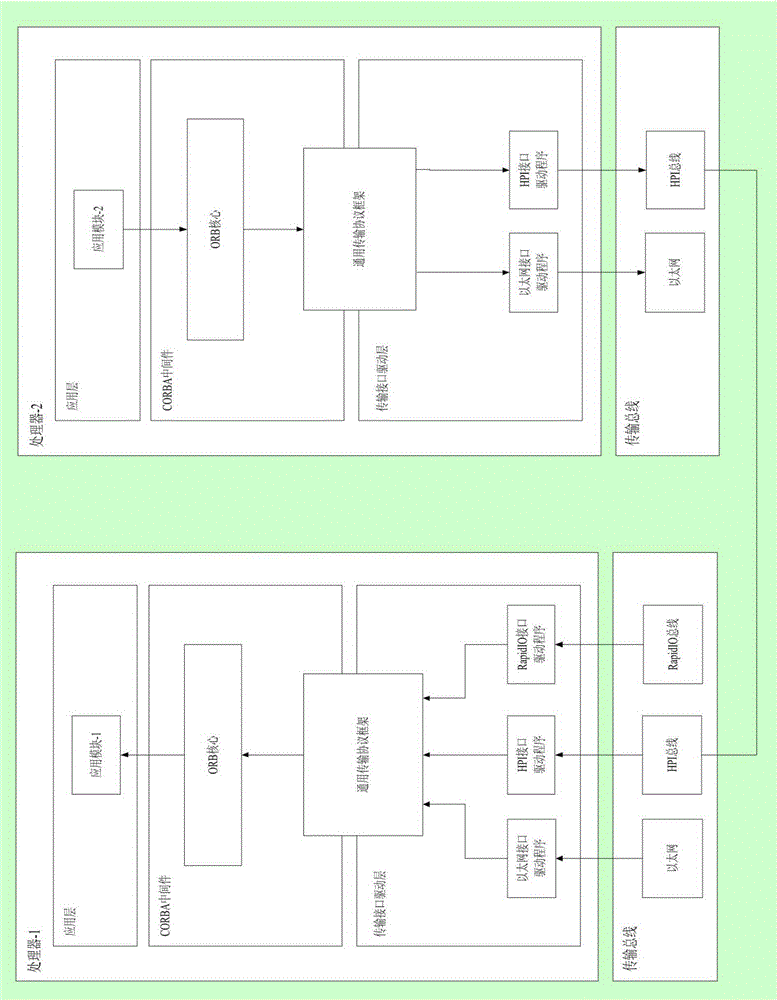
General transmission protocol frame aimed at CORBA middleware, communication system and method
ActiveCN105162858AReduce performanceImprove performanceData switching networksDistributed object oriented systemsTransmission protocolNetworking protocol
The invention relates to the field of wireless communication, and specifically discloses a general transmission protocol frame aimed at CORBA (Common Object Request Broker Architecture) middleware, a communication system and a method. The general transmission protocol frame comprises an IIOP (Internet Inter-ORB Protocol) module, a Socket module, a network protocol stack module and a plurality of virtual network interface cards, an IP message from the Socket module is converted into corresponding protocol message through the corresponding virtual network interface card, then, the converted message is sent to a server through a corresponding bottom drive program; the message received by the server is sent to the corresponding virtual network interface card through the corresponding bottom drive program, and the virtual network interface card packages the message into the IP message and further sends the packaged message to the Socket module. When a new bottom transmission mechanism needs to be supported, modification on own codes of the CORBA is not needed, support to the new transmission mechanism is added in the network protocol stack of an operating system, and thus, possibility of lowering performance of the CORBA is avoided.
Owner:NAT UNIV OF DEFENSE TECH
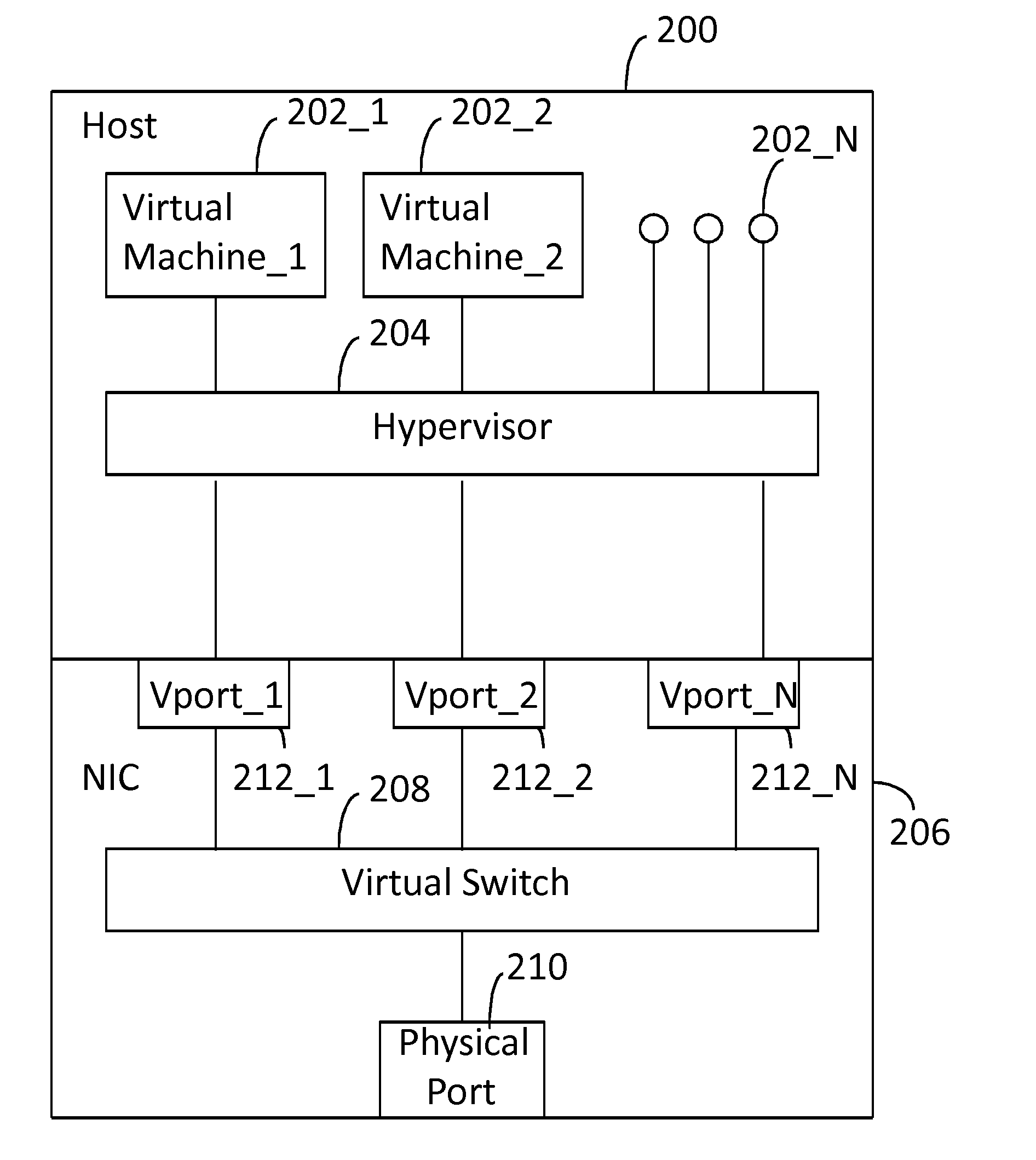
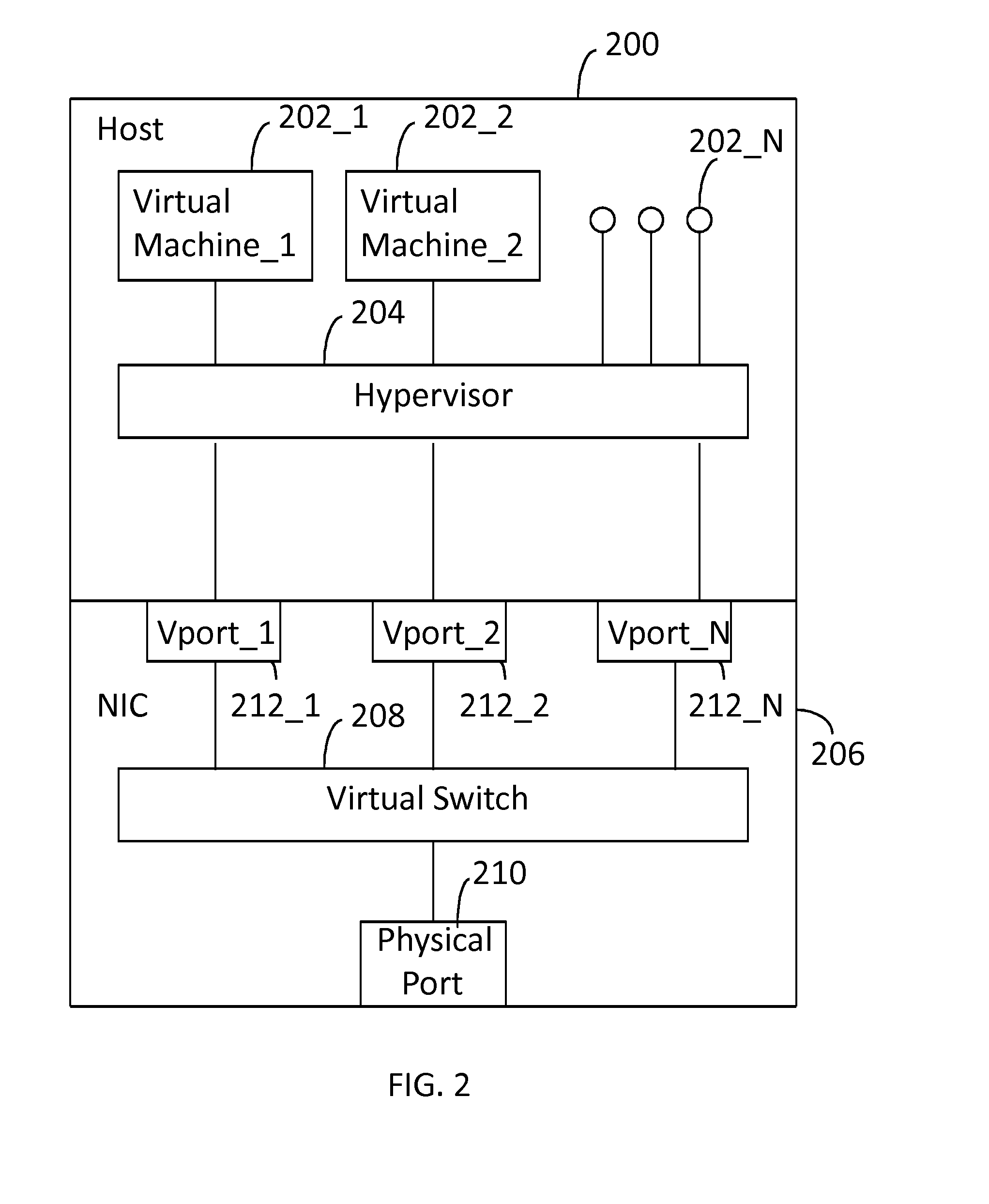
Network Interface Card with Virtual Switch and Traffic Flow Policy Enforcement
InactiveUS20150033222A1TransmissionSoftware simulation/interpretation/emulationTraffic capacityVirtual switch
A system includes a host computer executing virtual machines under the control of a hypervisor. A network interface card is coupled to the host machine. The network interface card implements a virtual switch with virtual ports. Each (one or more) virtual port is associated with a virtual machine. The network interface card may operate as a co-processor for the host computer by managing selected traffic flow policies, such as QoS and bandwidth provisioning on a per virtual machine basis.
Owner:CAVIUM NETWORKS
Server system and management method thereof
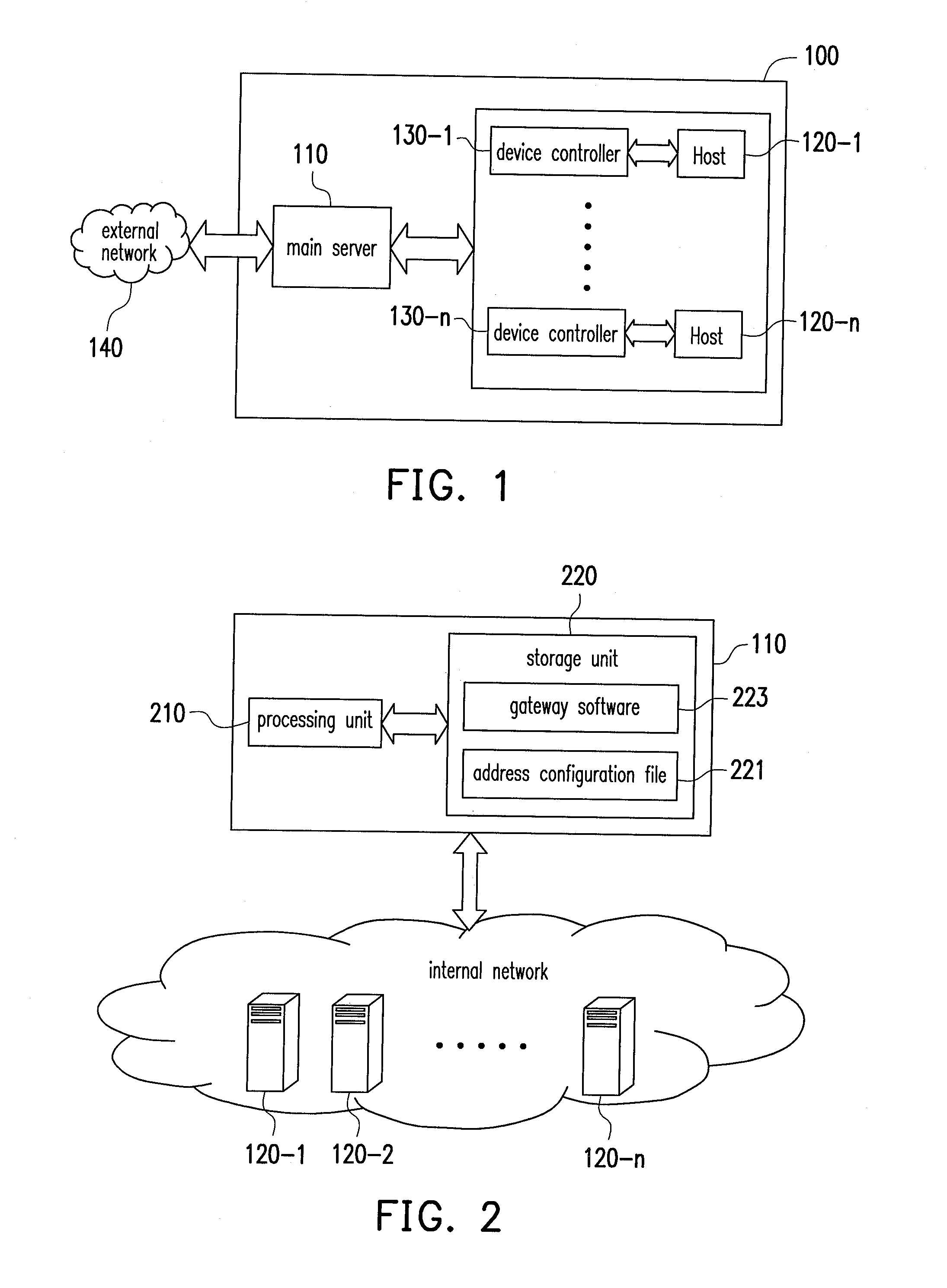
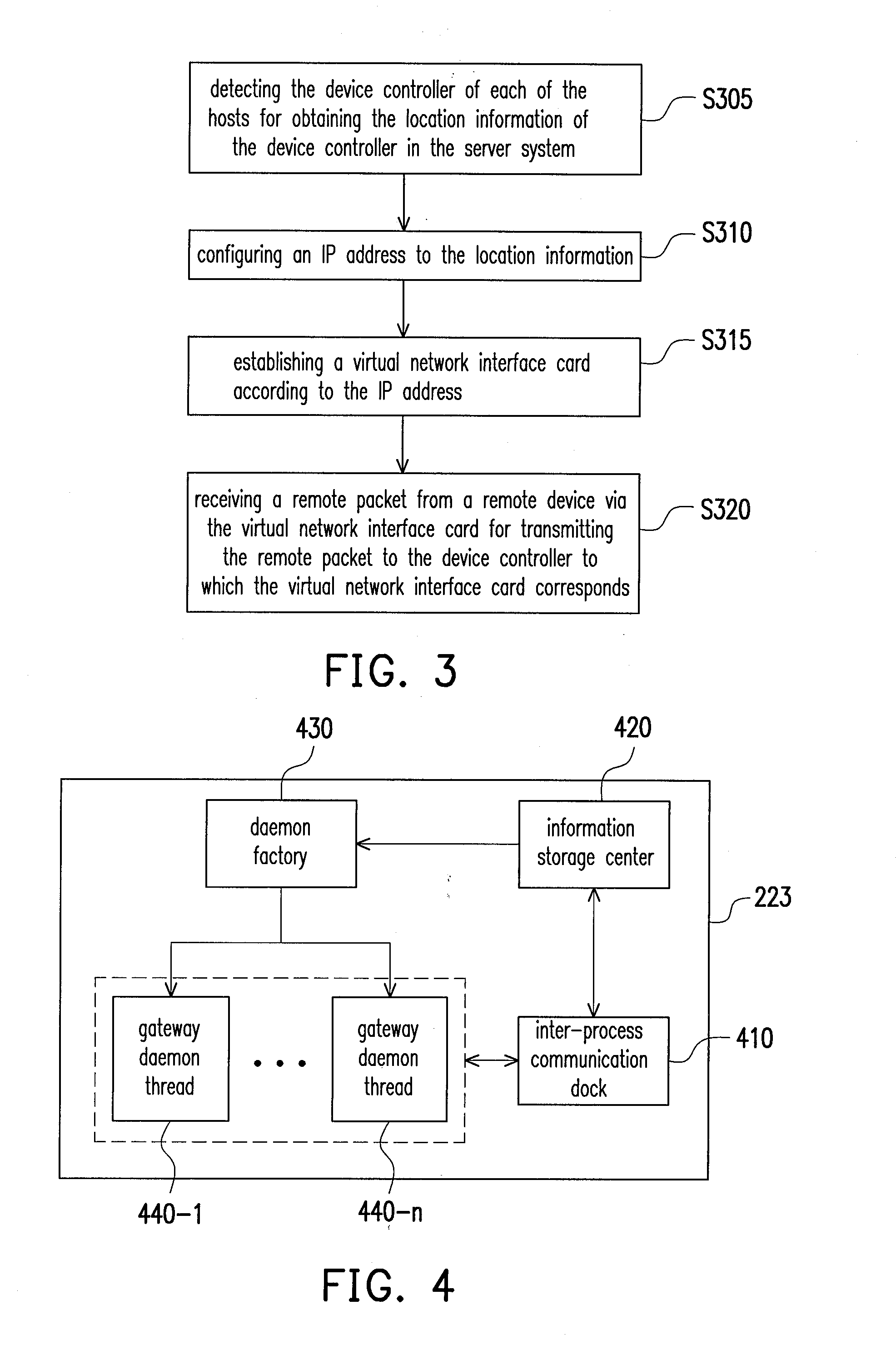
ActiveUS20130254361A1Improve securityDigital computer detailsTransmissionApproaches of managementIp address
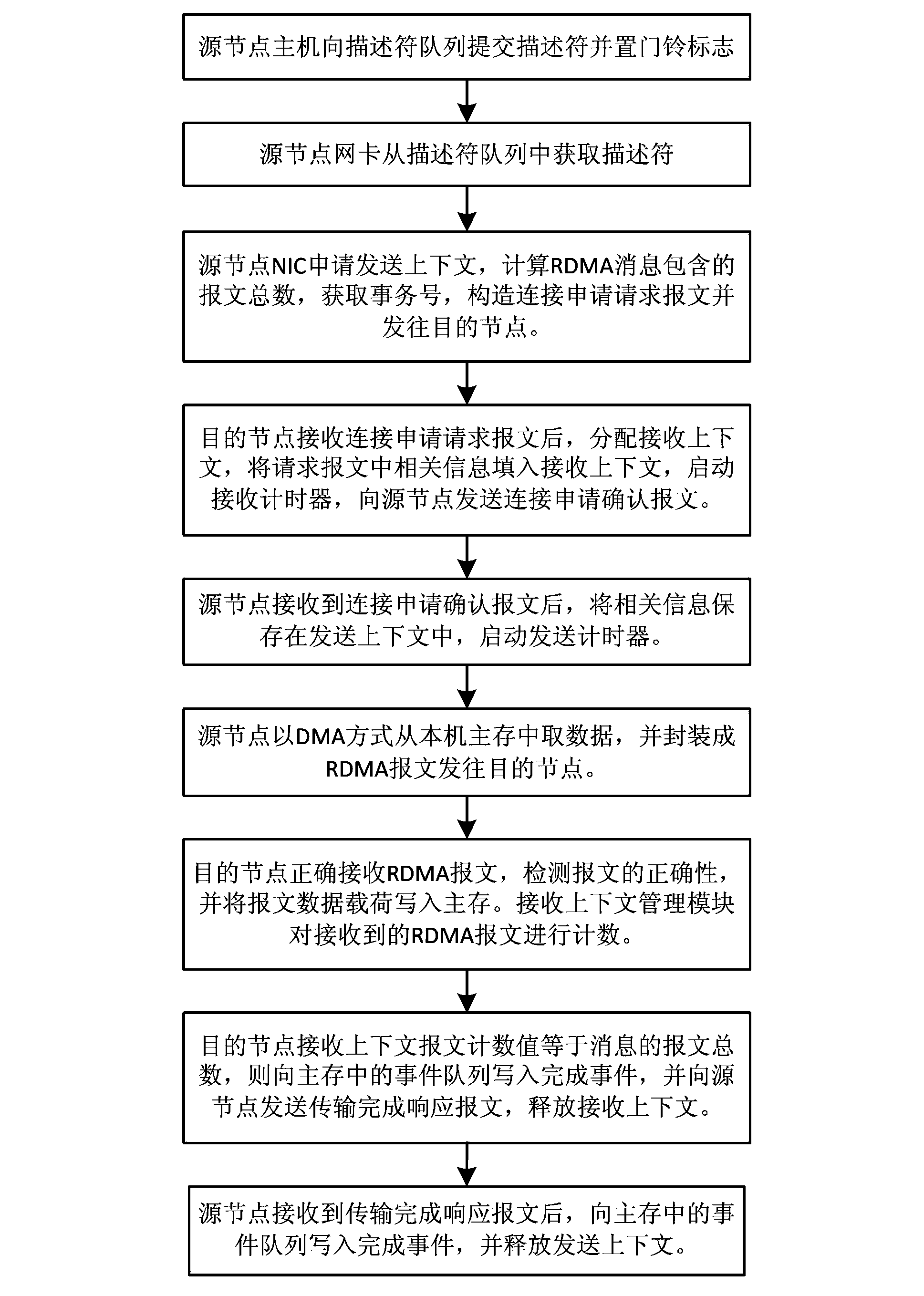
A server system and a management method thereof are provided. A main server is used to manage a plurality of hosts in the server system. The main server detects a device controller of each of the hosts for obtaining location information of each device controller. One Internet Protocol (IP) address is configured to each location information. A virtual network interface card (NIC) is established according to the IP address, and a remote package is received through the virtual NIC for transmitting package to the device controller corresponding to the virtual NIC.
Owner:WISTRON CORP
In-chip connection management-based RDMA communication method
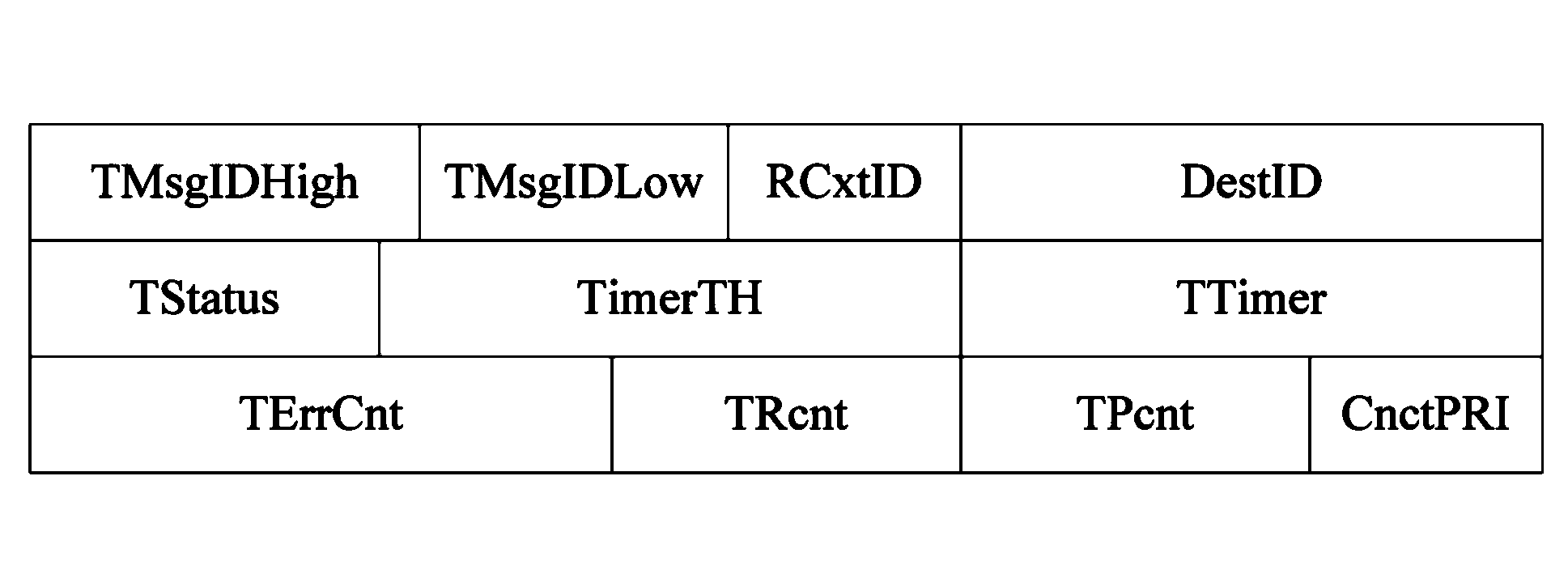
ActiveCN103248467AOvercoming Scalability IssuesImprove scalabilityError prevention/detection by using return channelExtensibilityInternal memory
The invention discloses an in-chip connection management-based RDMA (Remote Direct Memory Access) communication method, which comprises the following implementation steps: (1), building a context data transmitting structure and a context data receiving structure in a network interface card, building a descriptor queue, a short message receiving queue and a completion event queue in a host internal memory; (2), submitting RDMA written descriptor to the descriptor queue in the host internal memory by a source node host, and obtaining the descriptor to be processed by a source node network card; (3), checking that the current required descriptor is RDMA written descriptor by the source node network card, and building connection between the source node and an objective node network card chip; and (4), based on the connection, obtaining data from a local machine by the source node in a DMA manner, and then sending to the objective node network card. The method has the advantages of good extensibility, multi-channel transmission supporting, reliable data transmission, high multinuclear treatment efficiency, and low single-message message transmission delay.
Owner:NAT UNIV OF DEFENSE TECH
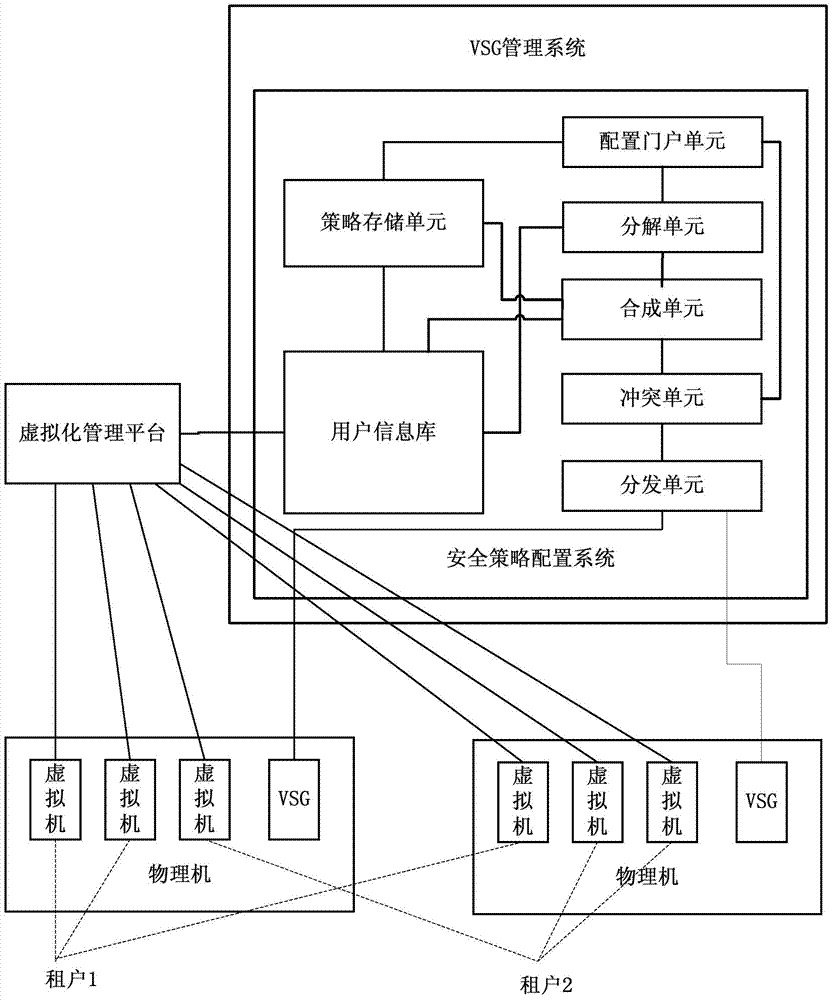
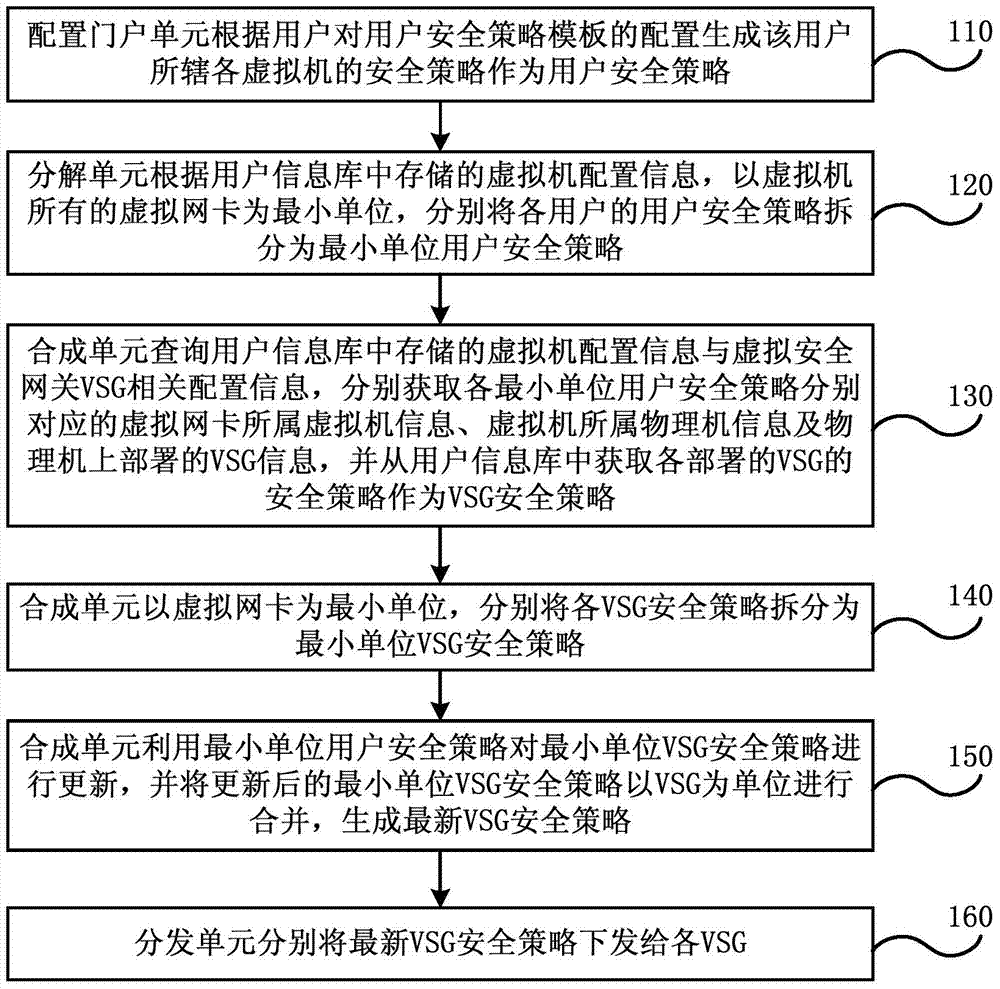
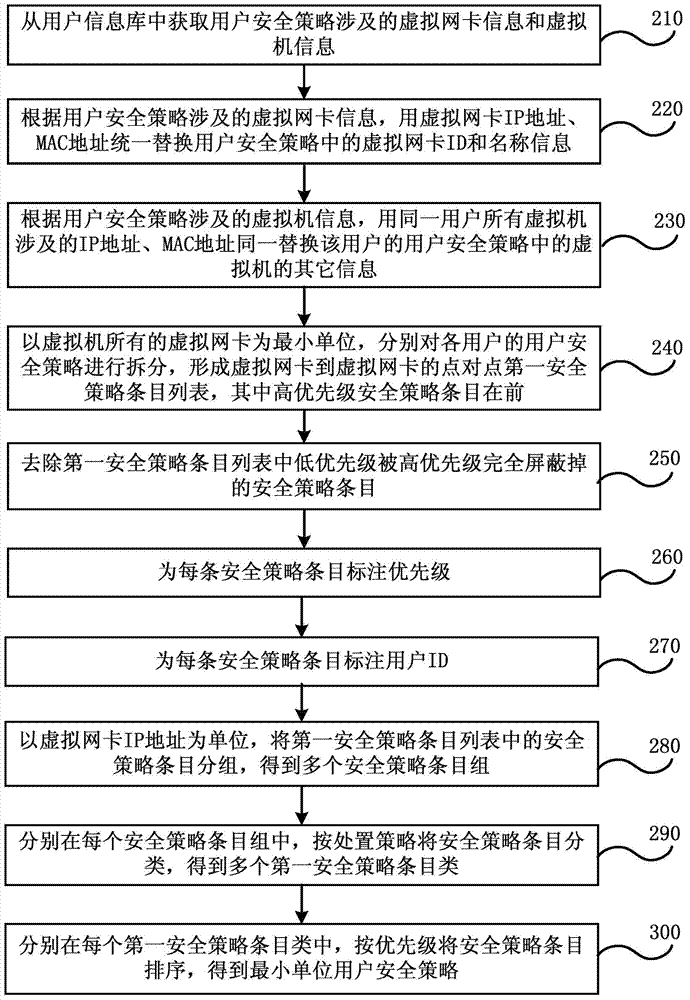
Security policy configuration system and method for virtual security gateway
The embodiment of the invention discloses a security policy configuration system and method for a virtual security gateway. The method comprises the steps that user security policies are generated according to user configuration; with virtual network interface cards as minimum units, the user security policies of all users are split into minimum unit user security policies respectively; a user information base is inquired for obtaining information of a virtual machine which the virtual network interface cards belong to, information of a physical machine which the virtual machine belongs to, and VSG information deployed on the physical machine, and obtaining VSG security policies from the user information base, wherein the information of the virtual machine, the information of the physical machine and the VSG information correspond to all the minimum unit user security policies respectively; with the virtual network interface cards as the minimum units, all the VSG security policies are split into minimum unit VSG security policies; the minimum unit user security policies are utilized for updating the minimum unit VSG security policies, the updated minimum unit VSG security policies are combined with VSGs as units to generate the latest VSG security policies, and the latest VSG security policies are issued to all the VSGs. According to the system and the method, the VSG security policies of a Hypervisor mode can be configured from user dimensionality.
Owner:CHINA TELECOM CORP LTD
Data message processing method from user mode to kernel mode
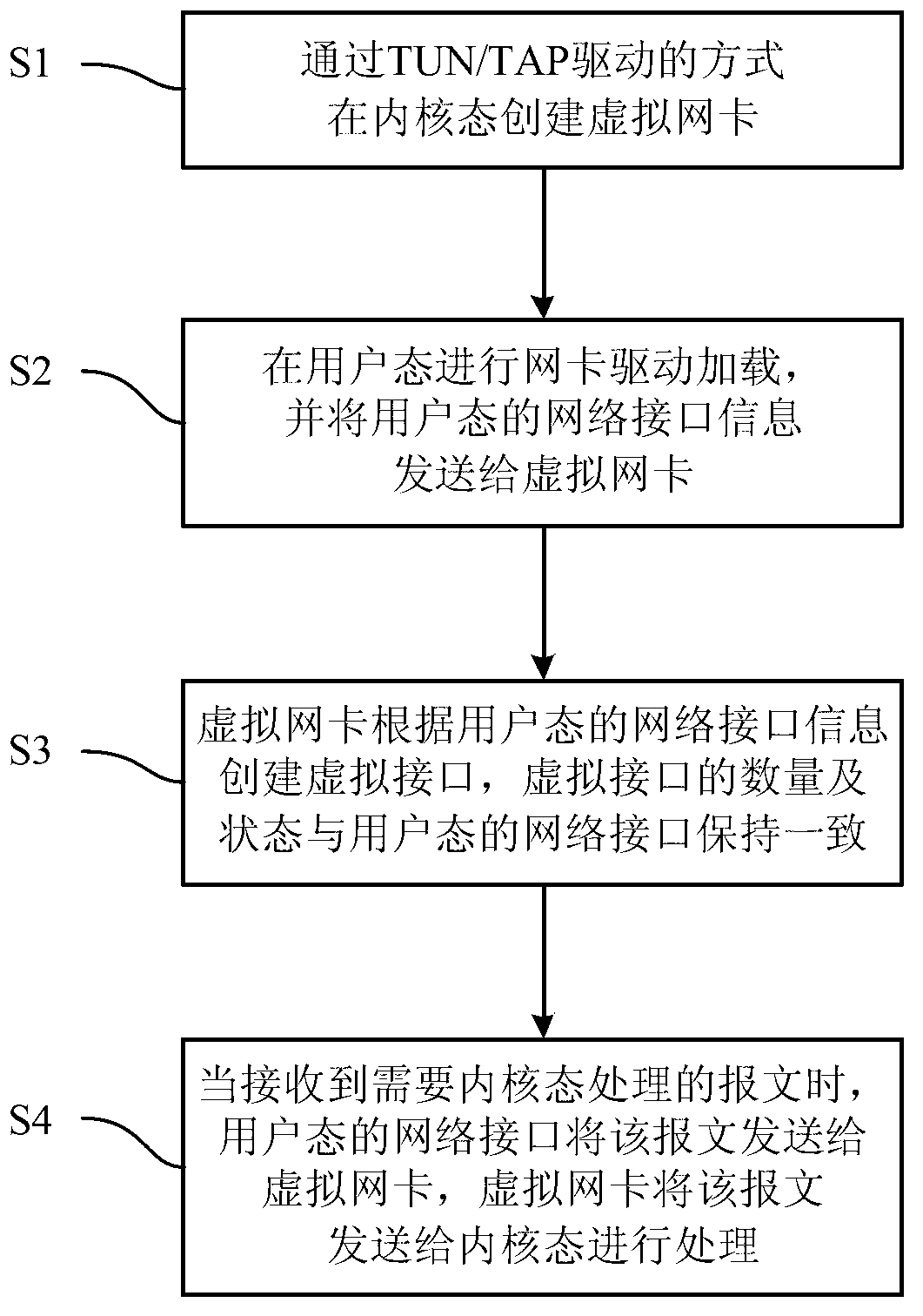
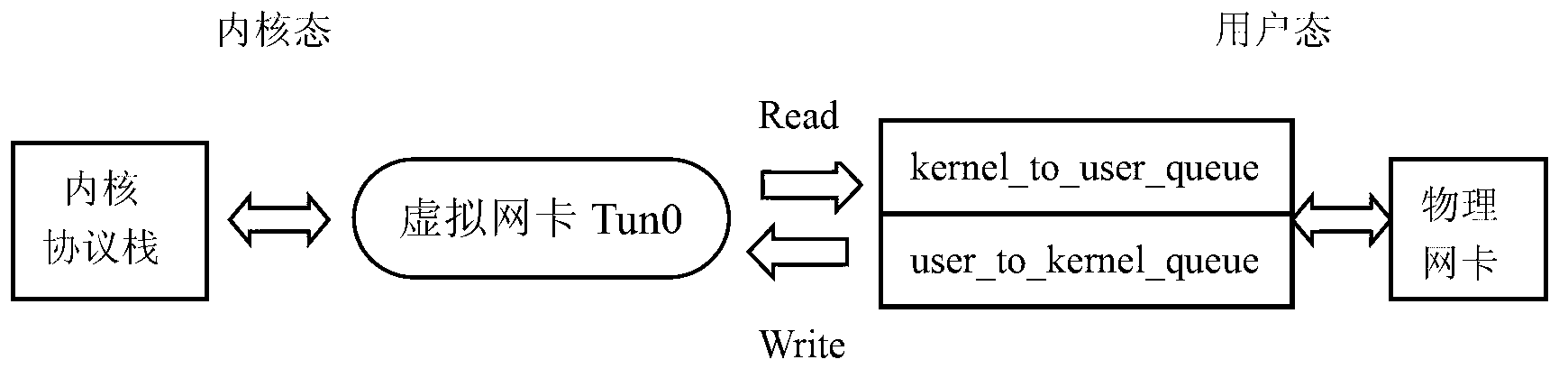
InactiveCN103312601ASatisfy perceived needsReduce performance lossData switching networksMessage processingTUN/TAP
The invention discloses a data message processing method from a user mode to a kernel mode. The method comprises the steps that S1, a virtual network card is created in the kernel mode through a TUN / TAP driving manner; S2, a network card drive is loaded in the user mode, and network interface information in the user mode is sent to the virtual network card; S3, the virtual network card creates virtual interfaces according to the network interface information in the user mode, wherein the number and the state of the virtual interfaces are kept consistent with those of a network interface in the user mode; S4, when receiving a message needing to be processed by the kernel mode, the network interface in the user mode sends the message needing to be processed by the kernel mode to the virtual network card, and the virtual network card sends the message needing to be processed by the kernel mode to the kernel mode for processing. The method can be used for eliminating performance loss caused by loading a kernel network card drive and enabling the kernel mode to perceive the states of an actual physical network and a network interface.
Owner:OPZOON TECH
Downlink flow, uplink flow and bidirectional flow limit method and device
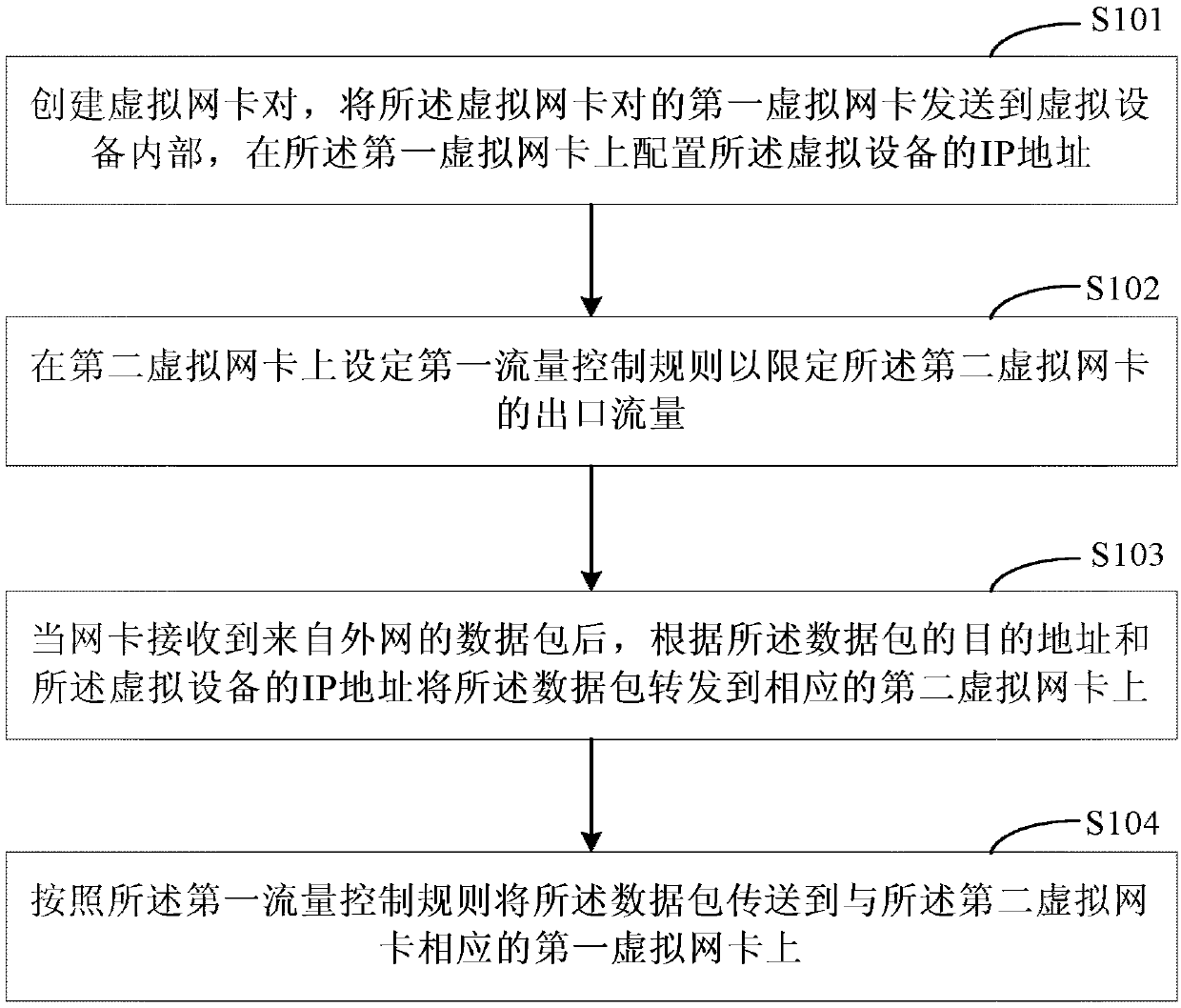
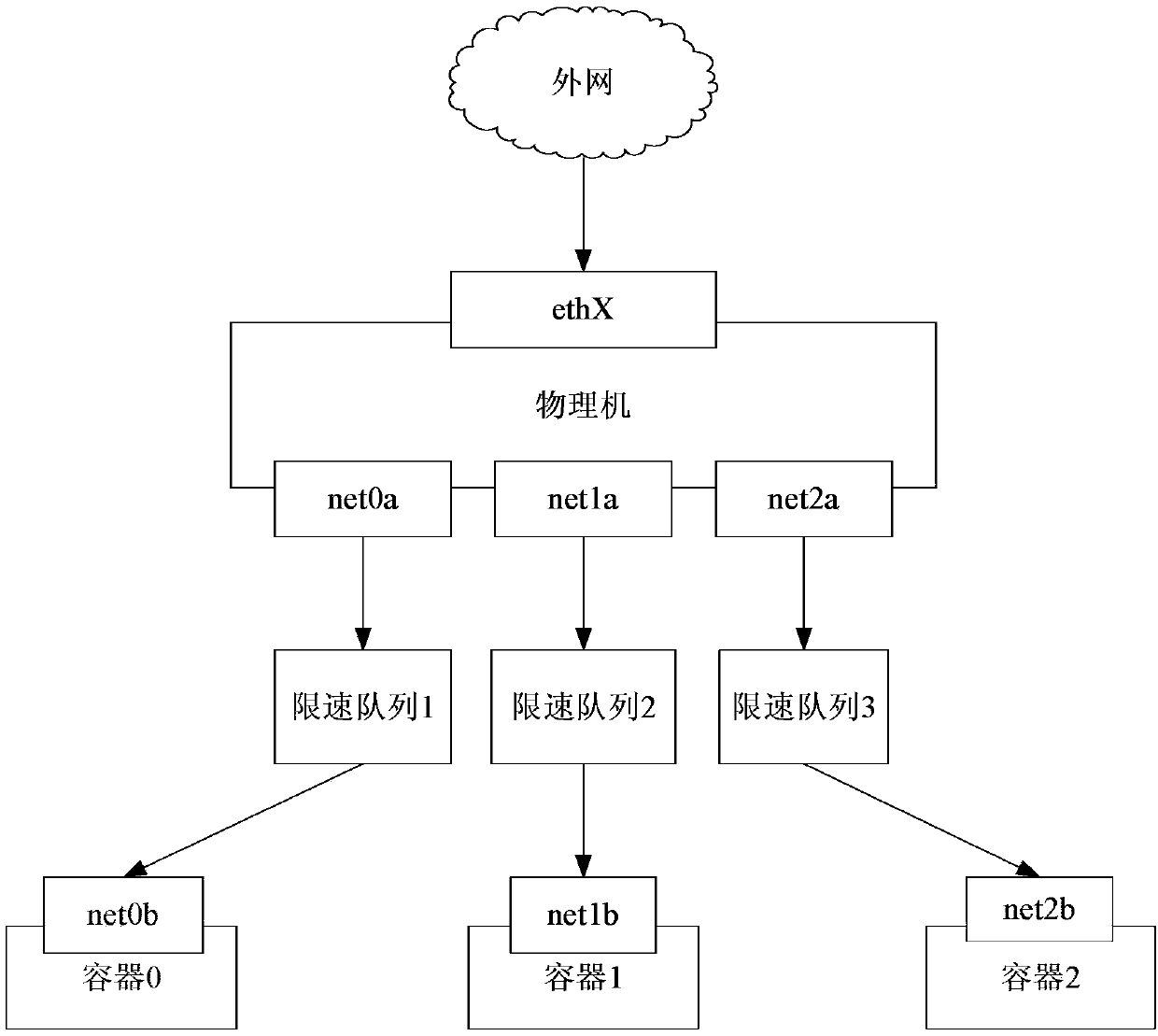
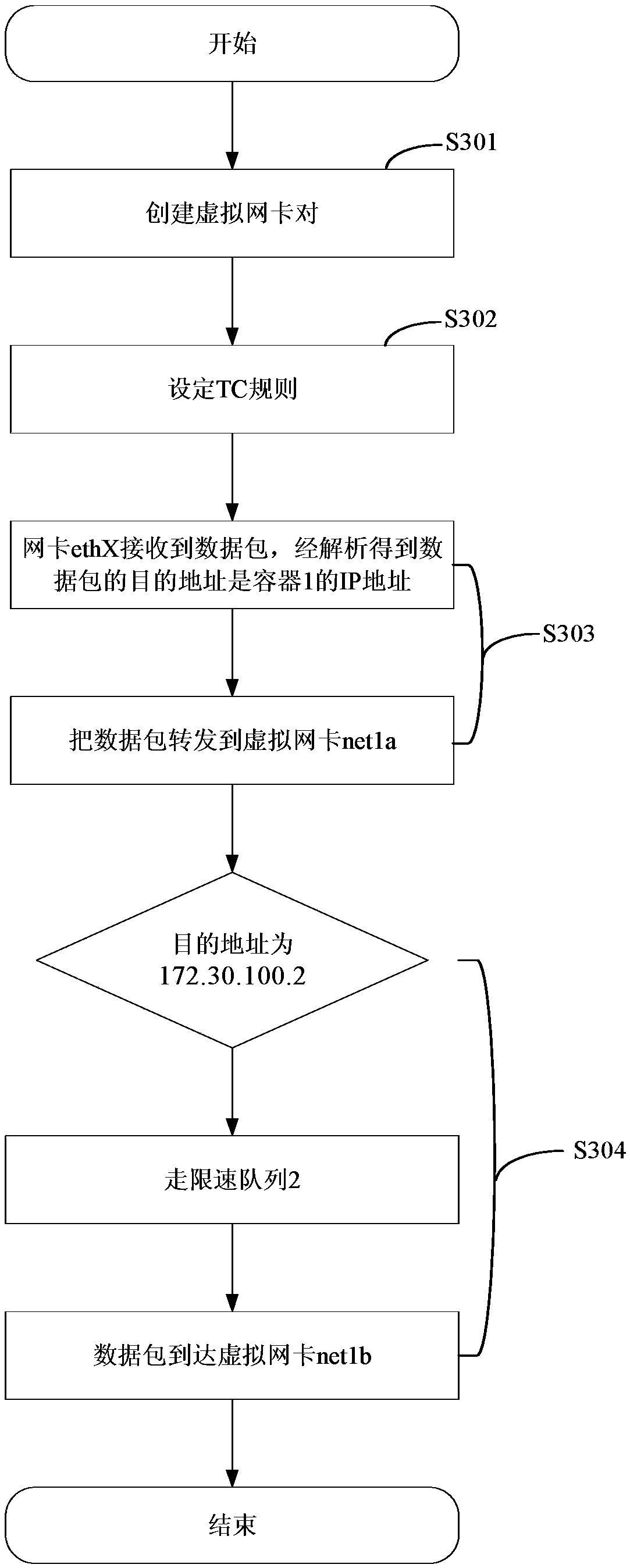
ActiveCN107666446AIncrease flexibilityTake advantage ofData switching networksTraffic capacityIp address
The invention further provides a downlink flow, uplink flow and bidirectional flow limit method and device and relates to the technical field of a computer. The method comprises steps that a virtual network interface card pair is created, a first virtual network interface card of the virtual network interface card pair is sent to an internal portion of virtual equipment, and an IP address of the virtual equipment is configured on the first virtual network interface card; first flow control rules are set on the second virtual network interface card; when a data packet from the external networkis received by the virtual network interface cards, the data packet is forwarded to the corresponding second virtual network interface card according to a destination address of the data packet and the IP address of the virtual equipment; the data packet is transmitted to the first virtual network interface card corresponding to the second virtual network interface card according to first flow control rules. The method is advantaged in that a physical machine and the virtual equipment are communicated through utilizing the virtual network interface cards, the outlet flow of the virtual networkinterface cards on the physical machine is limited through setting the first flow control rules, so the inlet flow of the virtual network interface cards of the virtual equipment is limited, and downlink flow limit is realized.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com