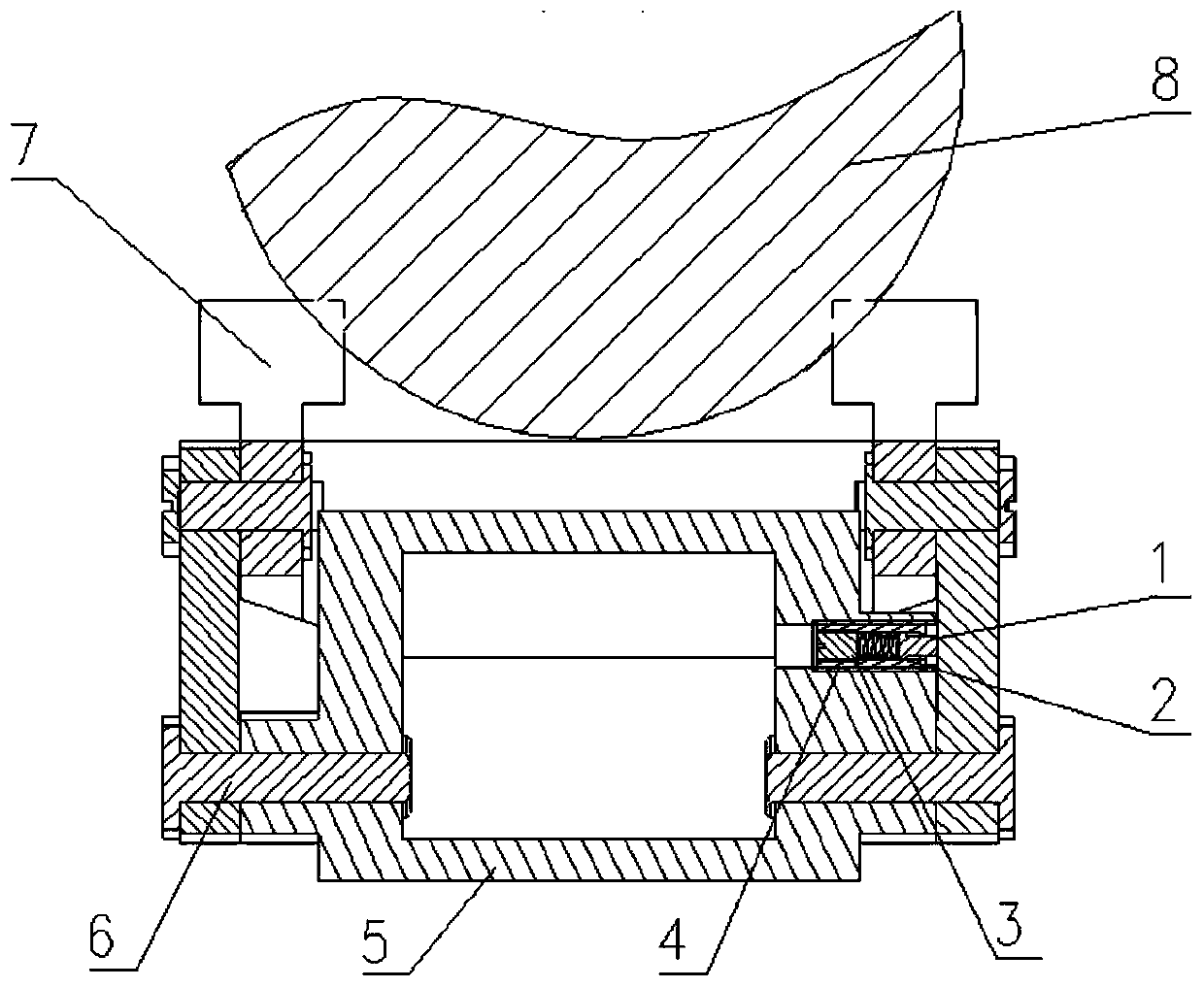
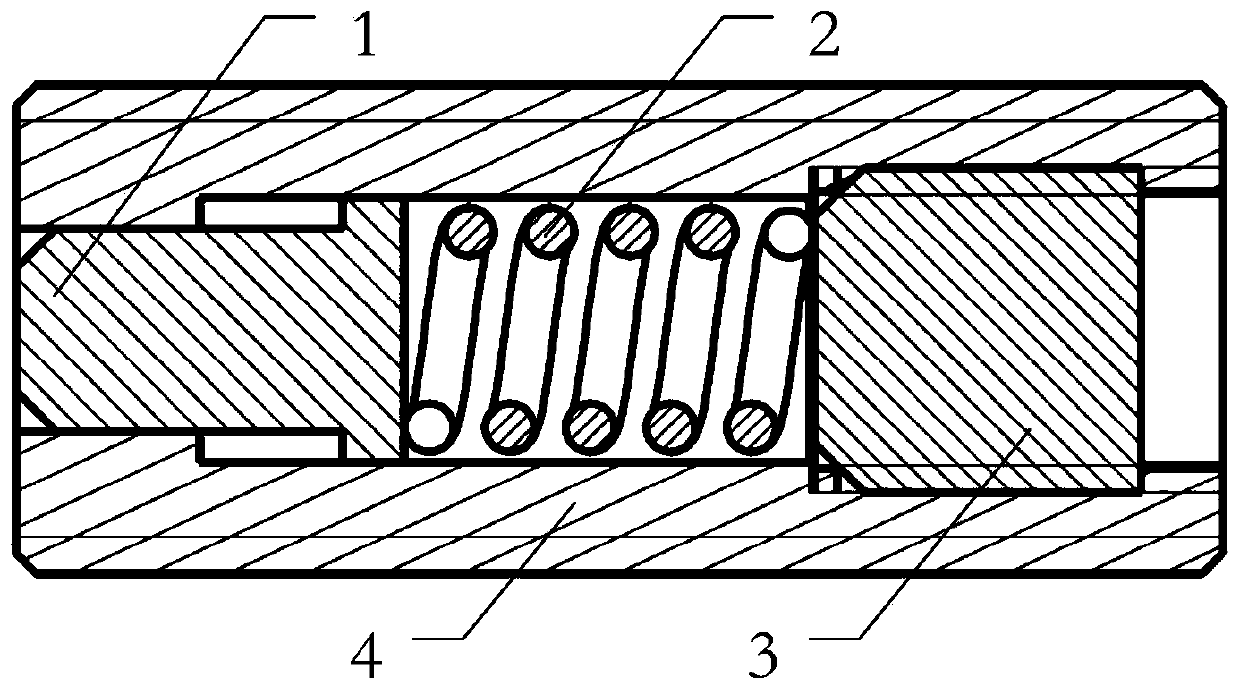
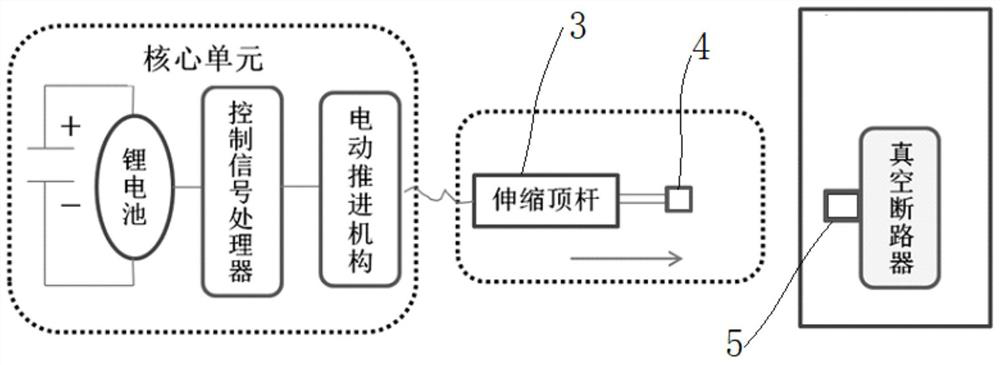
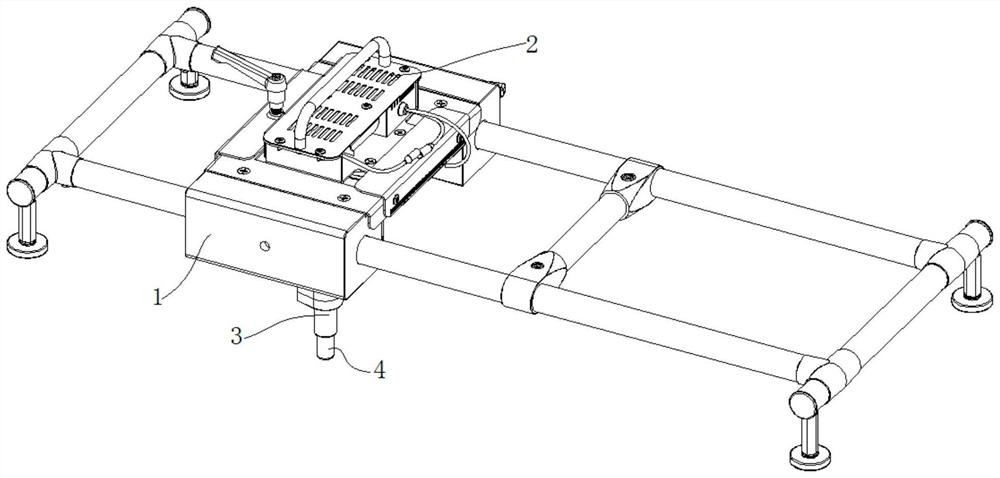
Patents
Literature
71results about How to "Solve insecurity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
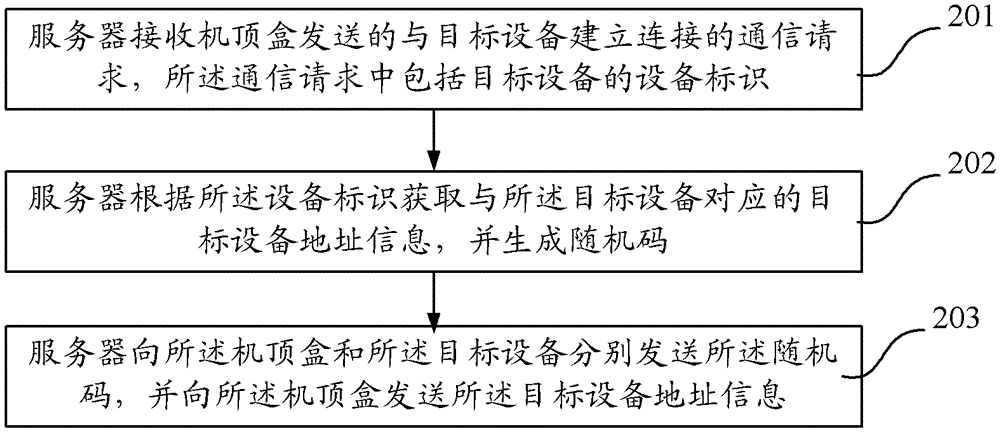
Load balancing method, server and system for virtual machine cluster
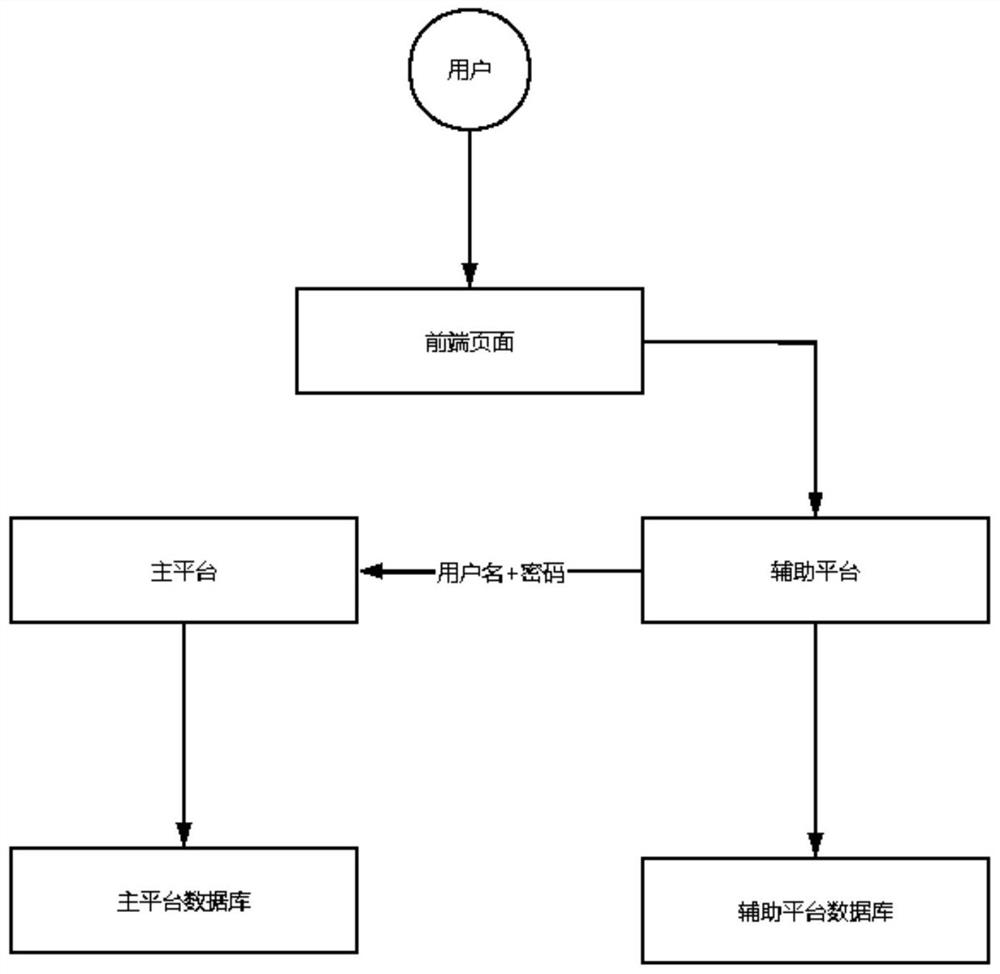
ActiveCN103384255ASolve insecurityData switching networksPhysical networkVirtual network interface card
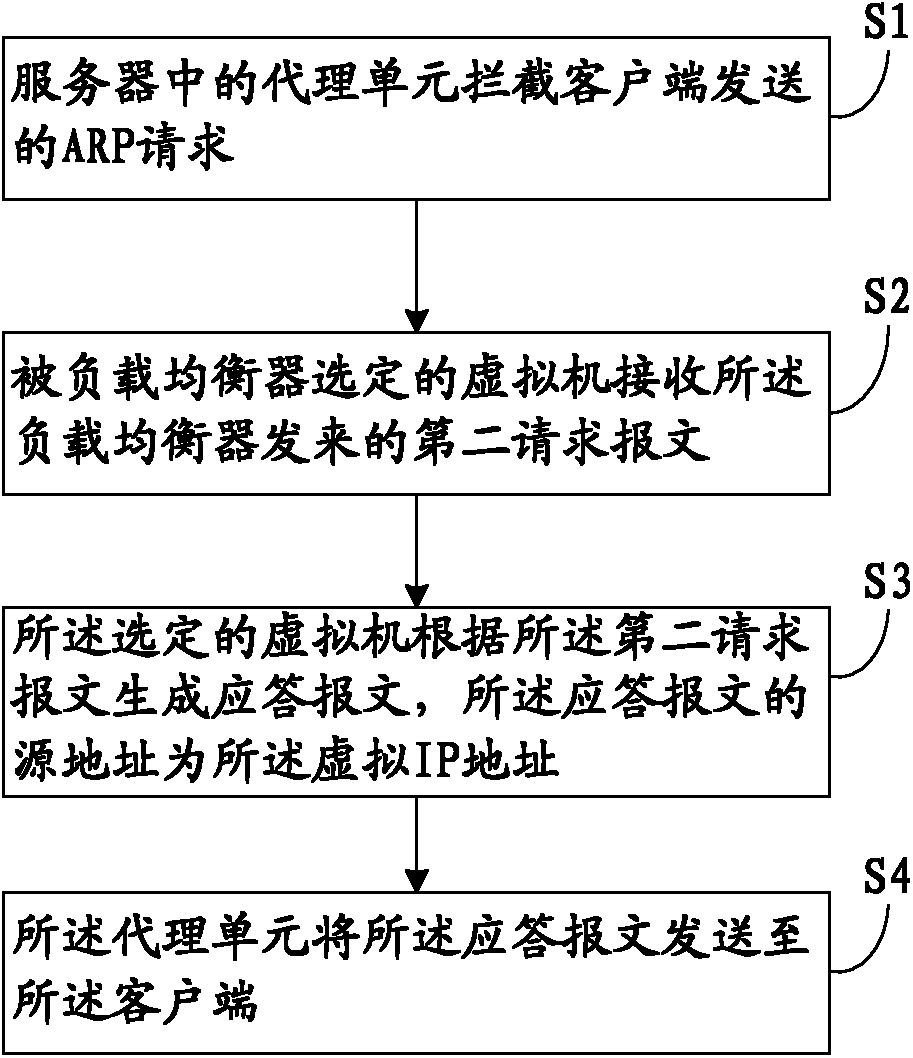
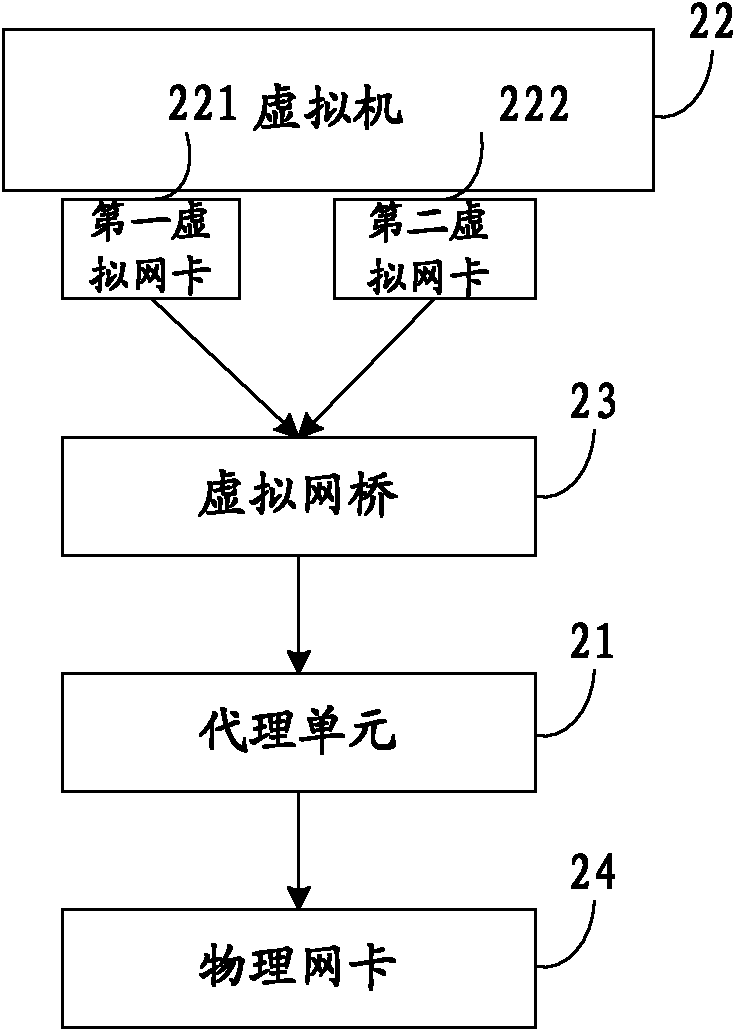
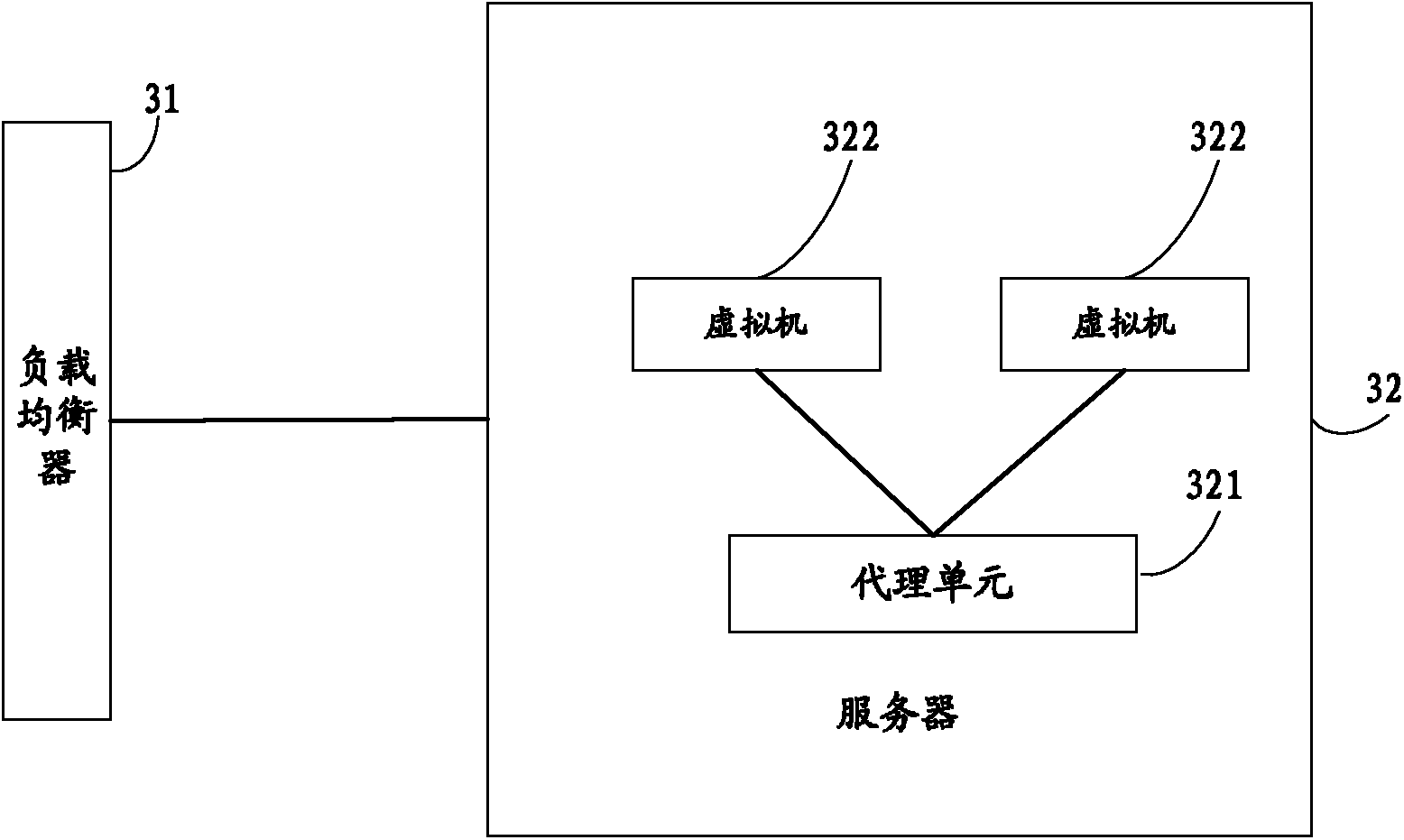
The invention discloses a load balancing method, server and system for a virtual machine cluster. The method is applied to a server where at least one virtual machine is established and comprises the steps that an agency unit which is arranged between a virtual network interface card of the virtual machine and a physical network interface card of the server in the server intercepts ARP requests sent by a client, the agency unit can configure a virtual IP address identical with the IP address of a load balancer for each virtual machine, the virtual machine chosen by the load balancer can receive second request message sent by the load balancer, the chosen virtual machine can generate response message according to the second request message, a source address of the response message is the virtual IP address, and the agency unit can send the response message to the client. By means of the load balancing method, load balance can be achieved without carrying out configuration in the virtual machine, and the safety of the system is improved.
Owner:CHENGDU HUAWEI TECH
Grouped multiple-key encryption method and grouped multiple-key encryption device
ActiveCN103716157ASolve potential safety hazardsGood for recoveryEncryption apparatus with shift registers/memoriesPublic key for secure communicationEncryptionData recovery
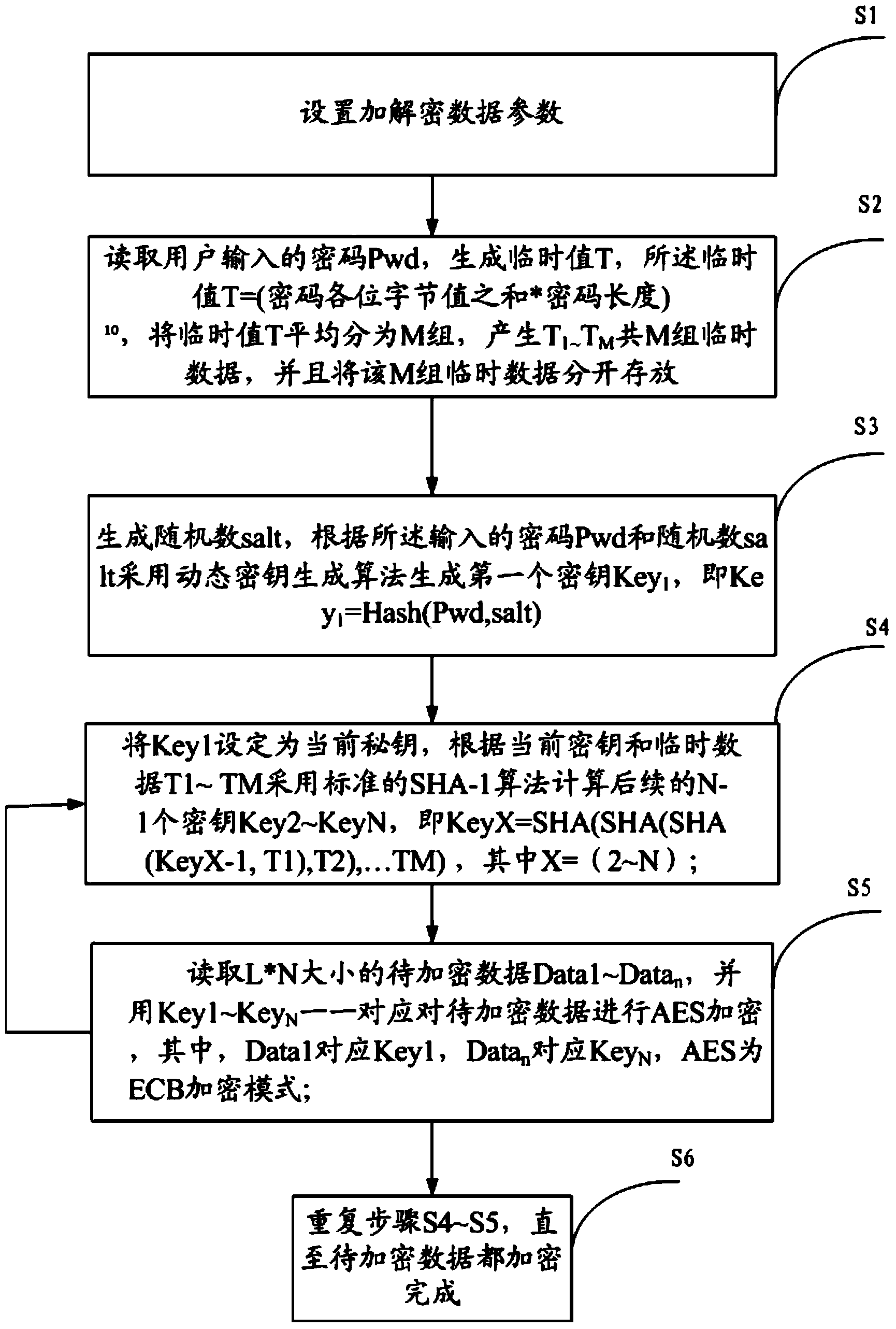
The invention provides a grouped multiple-key encryption method and a grouped multiple-key encryption device. A plurality of groups of different keys are generated, to-be-encrypted data is grouped and encryption and secondary encryption are carried out on the to-be-encrypted data with the use of the plurality of groups of different keys, thus greatly improving the security of the keys and the security of encrypted files. By the adoption of a multiple-key data-grouping encryption mechanism, the problem that all data is insecure once a key is acquired for an existing single-key encryption method is solved. As different keys are used, different encrypted data is generated after data of the same content is encrypted, thus solving the hidden safety problems of an ECB model. As an ECB model is adopted among blocks and encryption blocks are independent of each other, only data of the damaged blocks is affected and other data is not affected at all even if the encrypted data is damaged, which is conducive to data recovery and reduces the loss caused by data damage.
Owner:XIAMEN MEIYA PICO INFORMATION
Method for security authentication of smart TV software based on Android platform
InactiveCN102300065AImprove securityEnsure safetyTelevision system detailsColor television detailsSoftwareSecure authentication
The present invention relates to the technology of Android platform. The present invention solves the problem that the existing smart TV software based on the Android platform is insecure, and provides a method for security authentication of the smart TV software based on the Android platform. The certification body of the company releases verified software, and the smart TV verifies the software before installing the software, and only the verified software can be installed and run. The invention has the beneficial effects of improving the security of the smart TV software based on the Android platform, and being suitable for the smart TV software based on the Android platform.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
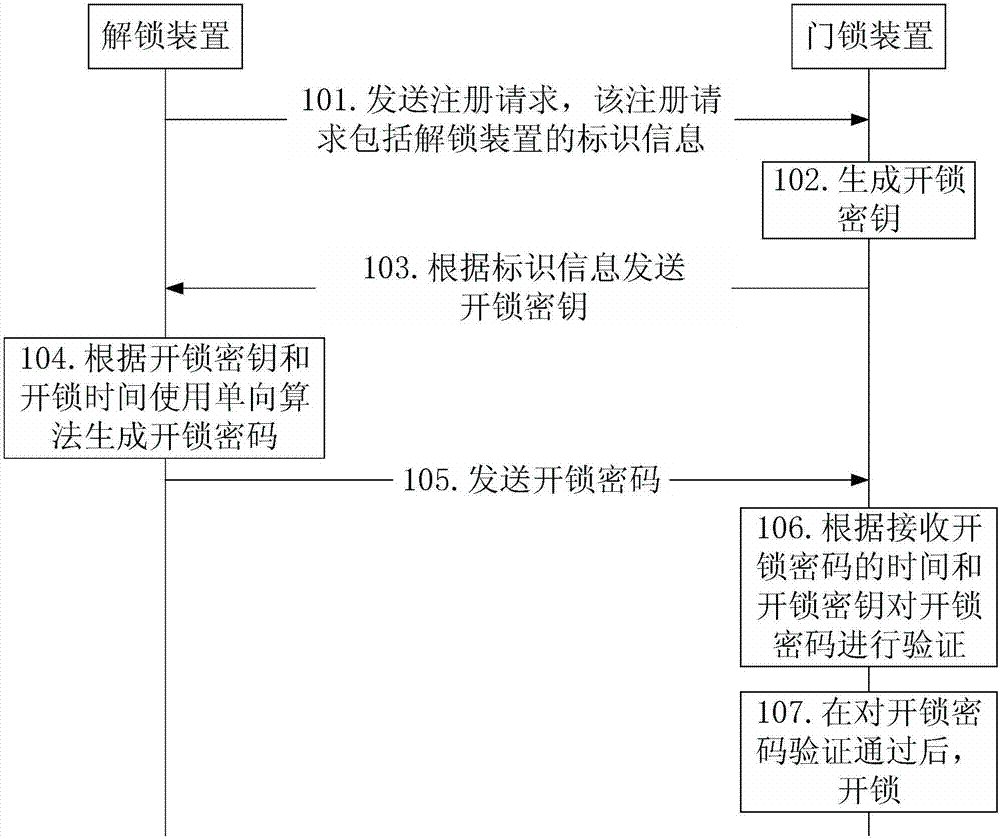
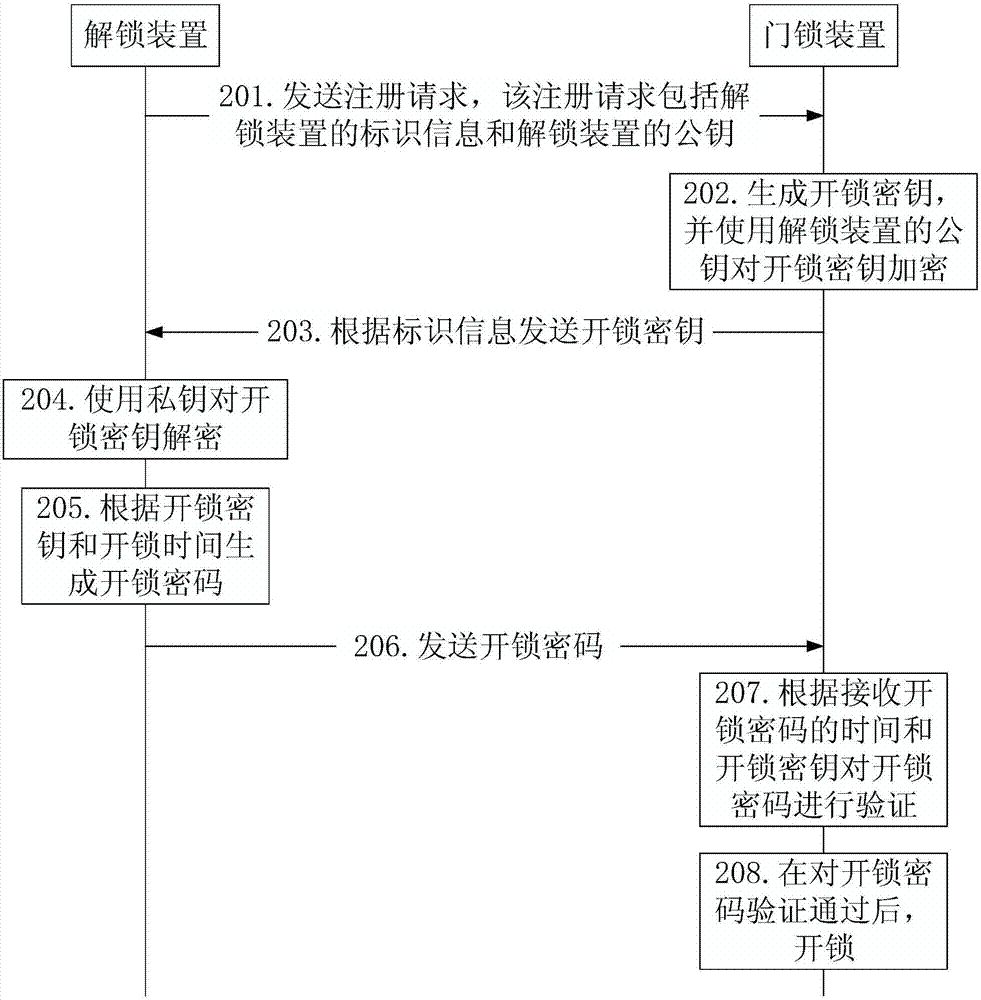
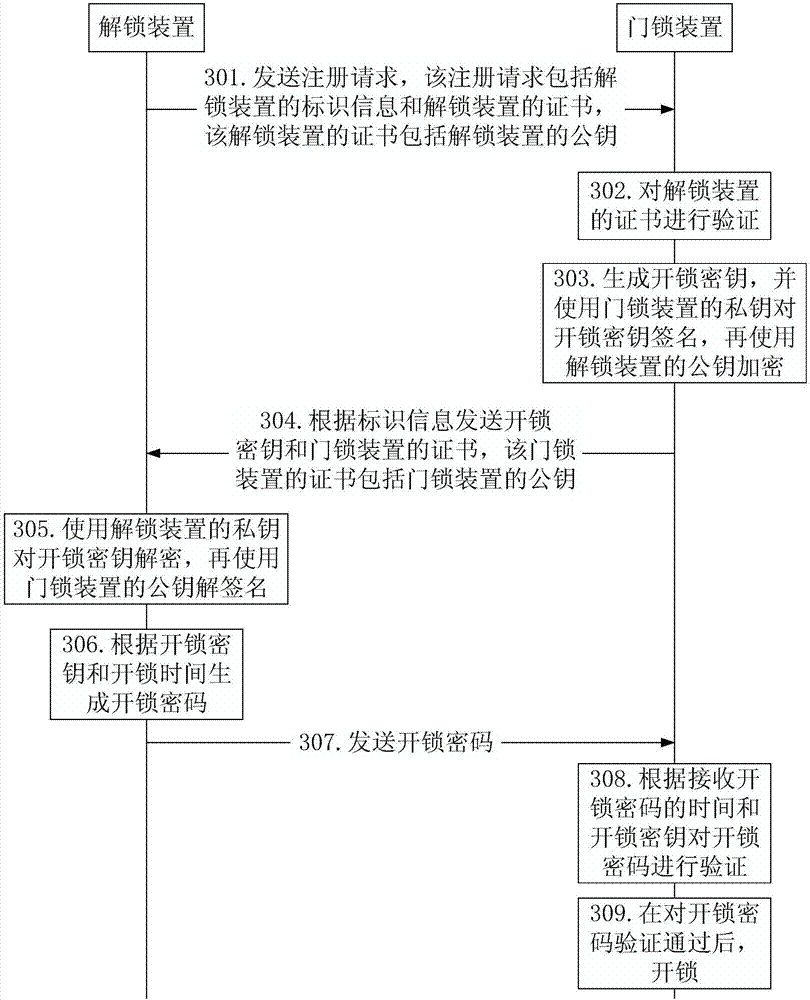
Method, device and system for unlocking by password
ActiveCN107978047AEasy to manageSolve insecurityIndividual entry/exit registersPasswordAuthorization
The invention discloses a method, a device and a system for unlocking by a password. The method for unlocking by a password is suitable for a process that an object which needs to unlock a door lock device through an unlocking device. The method comprises the following steps: the unlocking device generates an unlocking password according to an unlocking secret keys and unlocking time by a one-wayalgorithm; the unlocking device transmits the unlocking password to the door lock device to enable the door lock device to verify the unlocking password and unlock after verification is qualified. According to the method, the problem of insecurity since a temporary unlocking object takes unlocking authorization is solved, and an effect that the unlocking password is convenient in management is achieved.
Owner:BEIJING SENSESHIELD TECH
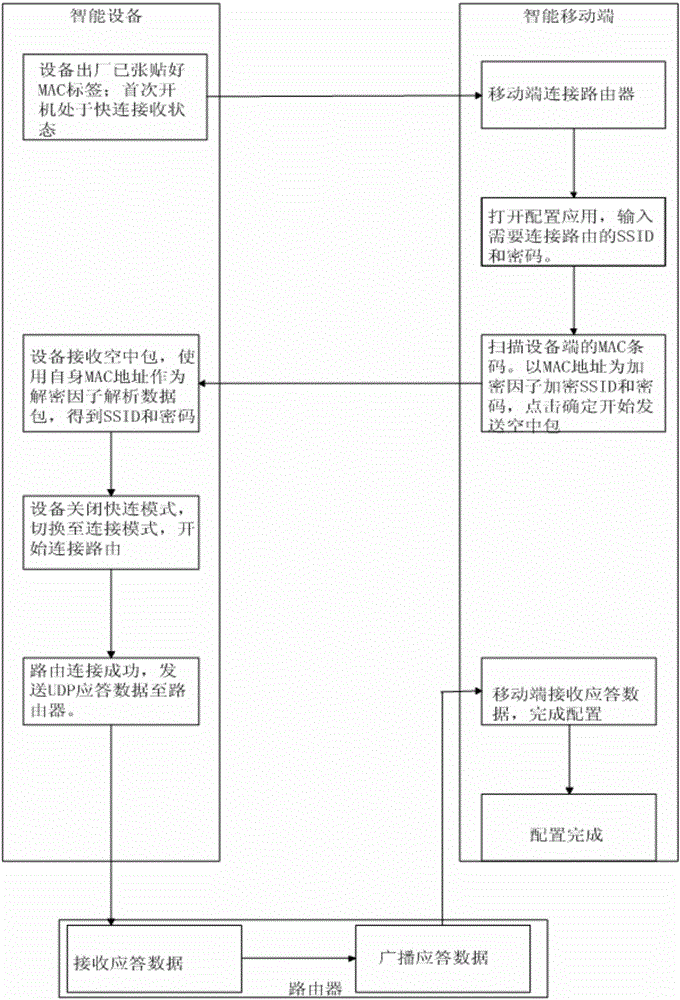
Method for rapidly configuring intelligent device network connection based on quick connection protocol
ActiveCN105142135AQuickly configure Internet accessSolve insecurityAssess restrictionSecurity arrangementData securityElectricity
The invention relates to an intelligent device network setting technology, discloses a method for rapidly configuring intelligent device network connection based on a quick connection protocol and aims at solving the problems of complex operations and poor data security and effectiveness of intelligent device network configuration in the traditional technology. After an intelligent device leaves the factory, the intelligent device is powered on for the first time to be in a quick-connection receiving state; a mobile terminal connects to a network to which the intelligent device needs to connect; after successful connection, an installed configuration application is started; the SSID and the password of the connected network are input, and the MAC bar code of the device is scanned to obtain an MAC address; the MAC address is taken as an encryption factor to encrypt the SSID and the password; the mobile terminal starts to send an air packet and obtains the SSID and the password by analyzing using the own MAC address; a mode is switched to reboot the connected network; after the network is connected, a UDP reply packet is sent, and the configuration is completed after the intelligent mobile terminal receives the reply packet. The method is suitable for network connection of an embedded device in an open environment.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
E-coupon generation method and device
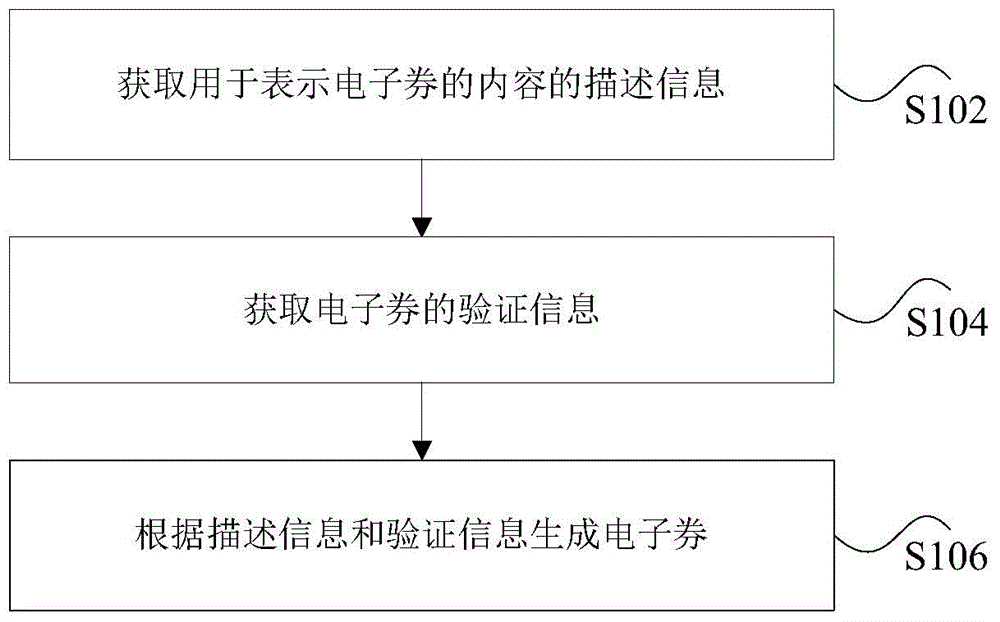
InactiveCN104573442AEasy transferConsumer safetyDigital data protectionPayment architectureComputer engineering
The invention discloses an e-coupon generation method and device. The e-coupon generation method includes: acquiring description information used for representing content of e-coupons; acquiring verification information of the e-coupons, wherein the verification information is used for verifying effectiveness of the e-coupons and identity information of e-coupons holders; generating the e-coupons according to the description information and the verification information, wherein the description information is used as plaintext parts of the e-coupons and the verification information is used as ciphertext parts of the e-coupons. Through the method and device, the problem that the e-coupons are unsafe in the circulation process in the prior art is solved, and safe circulation of the e-coupons is guaranteed.
Owner:BEIJING NETQIN TECH
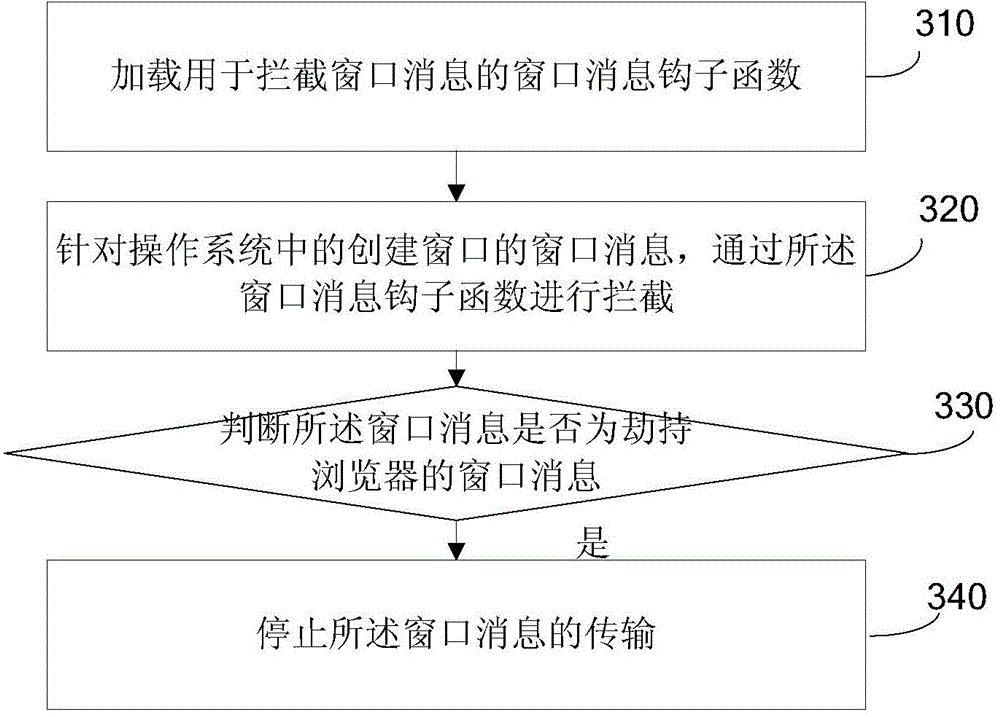
Anti-injection method for browser, browser client and device
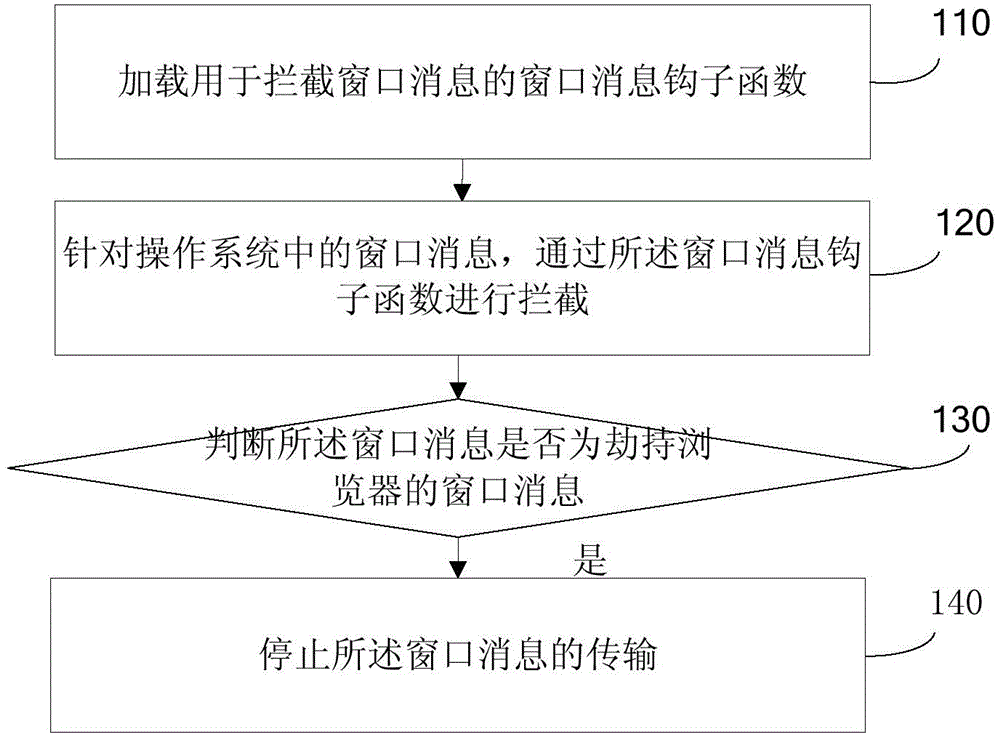
ActiveCN104539584ASolve insecurityImprove securitySecuring communicationComputer hardwareBrowser security
The invention discloses an anti-injection method for a browser, and relates to the technical field of browsers. The method comprises the following steps: loading a window message hook function for intercepting a window message; intercepting a window message in an operating system through the window message hook function; judging whether the window message is a browser-hijacking window message or not; and if the window message is the browser-hijacking window message, stopping transmission of the window message. According to the anti-injection method for the browser disclosed by the invention, the window message in the operating system can be intercepted by loading a global window message hook function, and a judgment on whether the window message is the browser-hijacking window message or not is made, so that the problem of unsafety of the browser due to the injection of dll into the browser through other applications is solved, and the beneficial effects of preventing the other applications from hijacking the browser by injecting unsafe dll into the browser and enhancing the safety of the browser are achieved.
Owner:BEIJING QIHOO TECH CO LTD +1
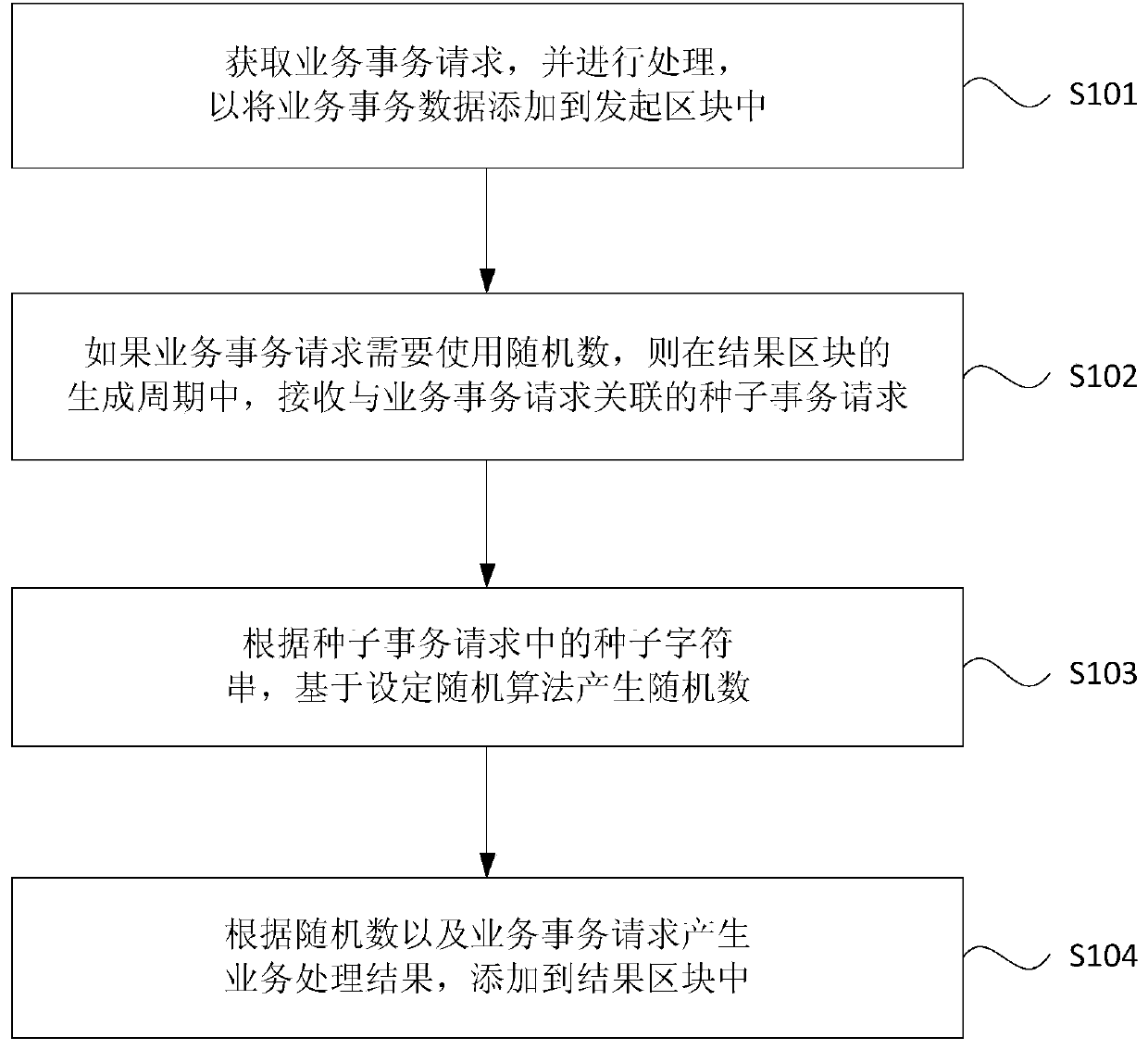
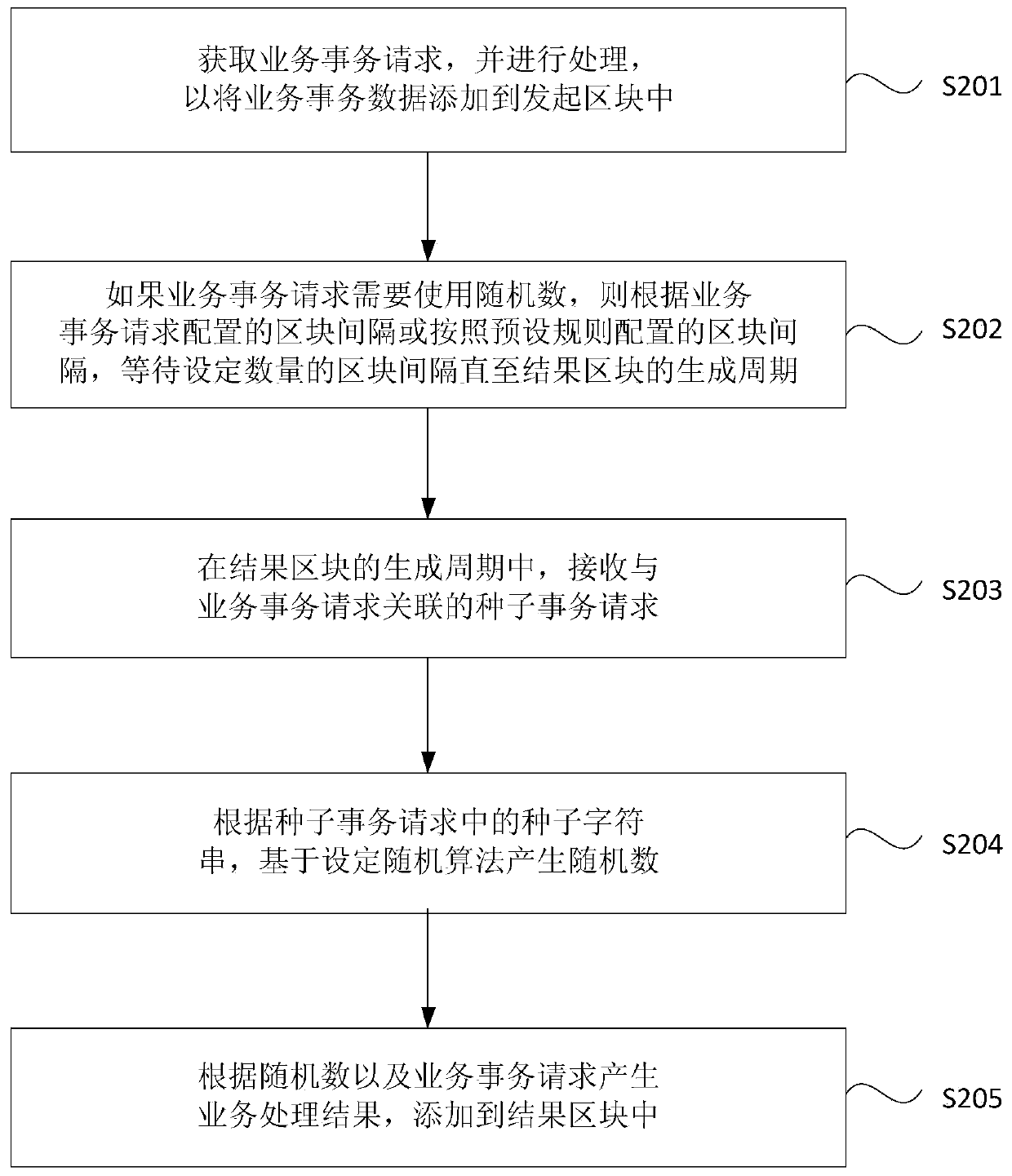
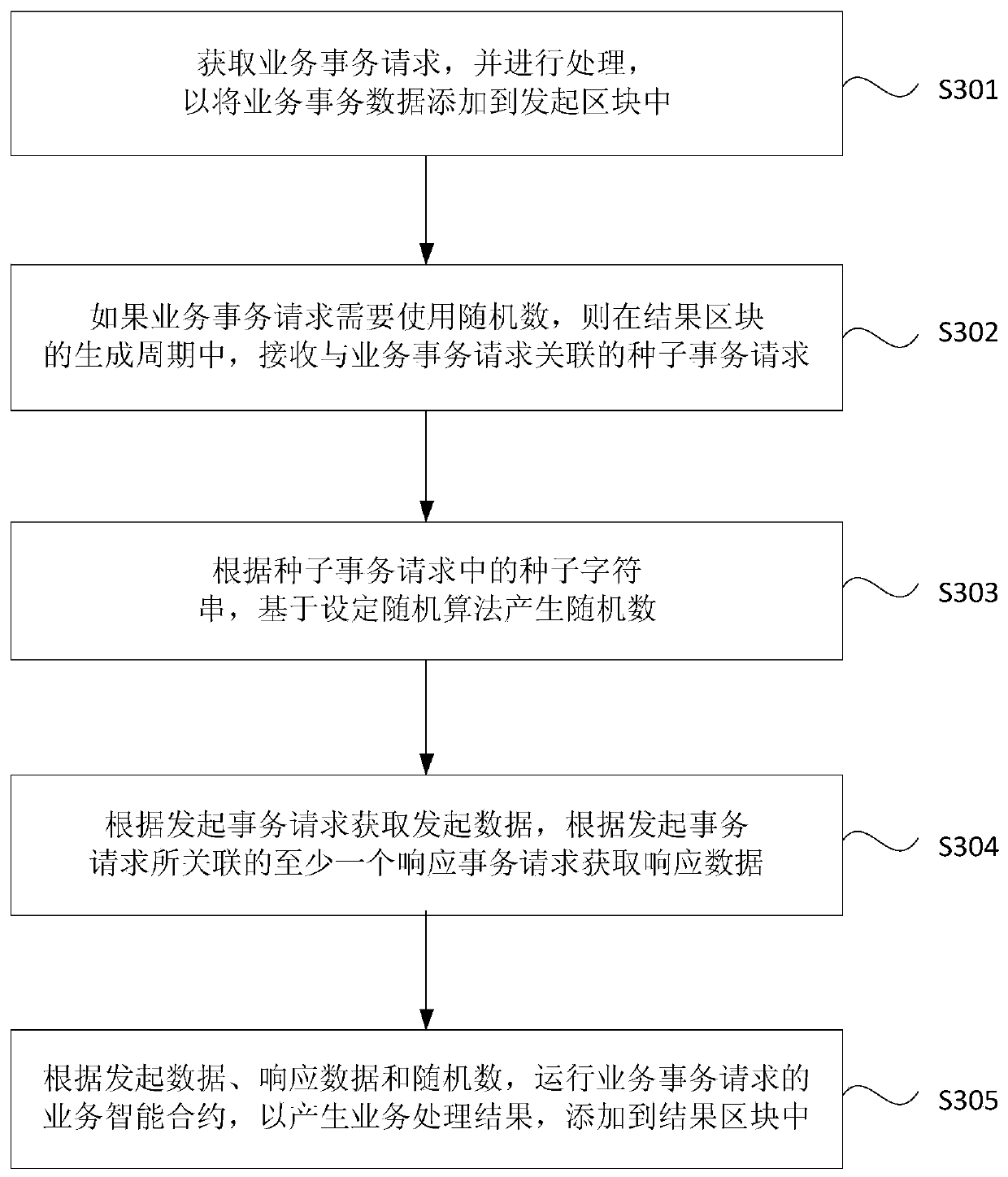
Random number generation method and device for block chain, equipment and storage medium
ActiveCN109753269ASolve insecurityIncrease credibilityRandom number generatorsMultiprogramming arrangementsComputer scienceOperating system
Embodiments of the invention disclose a random number generation method and device for a block chain, equipment and a storage medium. When the method is executed by a block chain node, the method cancomprise the following steps: obtaining a business transaction request, and processing the business transaction request to add business transaction data into an initiating block; if the service transaction request needs to use a random number, receiving a seed transaction request associated with the service transaction request in a generation period of a result block; wherein the result block is asubsequent block of an initiating block, and the seed transaction request is provided by a service participant of the service transaction request; generating a random number based on a set random algorithm according to a seed character string in the seed transaction request; and generating a service processing result according to the random number and the service transaction request, and adding the service processing result to the result block. According to the technical scheme provided by the embodiment of the invention, the credibility of generating the block chain random number is improved, and the security of the random number is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Identity authentication method and device of equipment and computer storage medium
ActiveCN109446788AReduce security threatsImprove efficiency and safetyDigital data authenticationInformation transmissionInformation transfer
The invention discloses an identity authentication method and device of equipment and a computer storage medium. The method comprises that in response to an inquiry instruction sent by a management platform, the device calculates a first hash value according to the device identity information and a received random number, and sends the first hash value to the management platform; the device sendsthe first hash value to the management platform according to the first hash value; the random number is generated by the management platform after the device joins the network; in response to a queryresponse instruction sent by the device, the management platform calculates the received first hash value, obtains a second hash value and sends it to the server; the server performs legitimacy authentication on the device according to the first hash value, obtains authentication information corresponding to the device and returns the authentication information to the management platform, so thatthe management platform calculates a third hash value according to the authentication information; according to the received third hash value, the device authenticates the validity of the management platform, which can effectively improve the efficiency and security of identity authentication, and effectively improve the efficiency and security and reliability of equipment information transmission.
Owner:GCI SCI & TECH
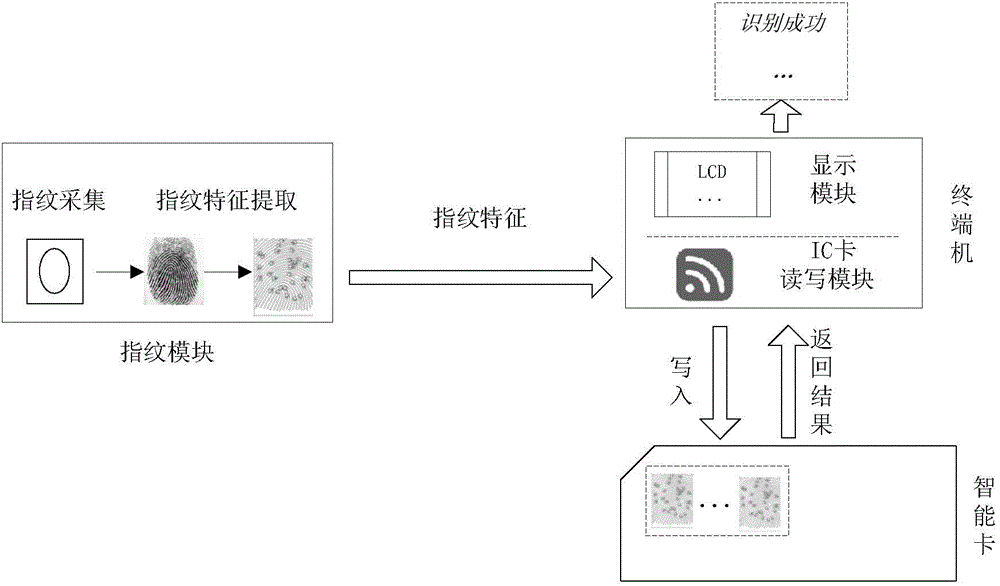
Fingerprint data processing method and device
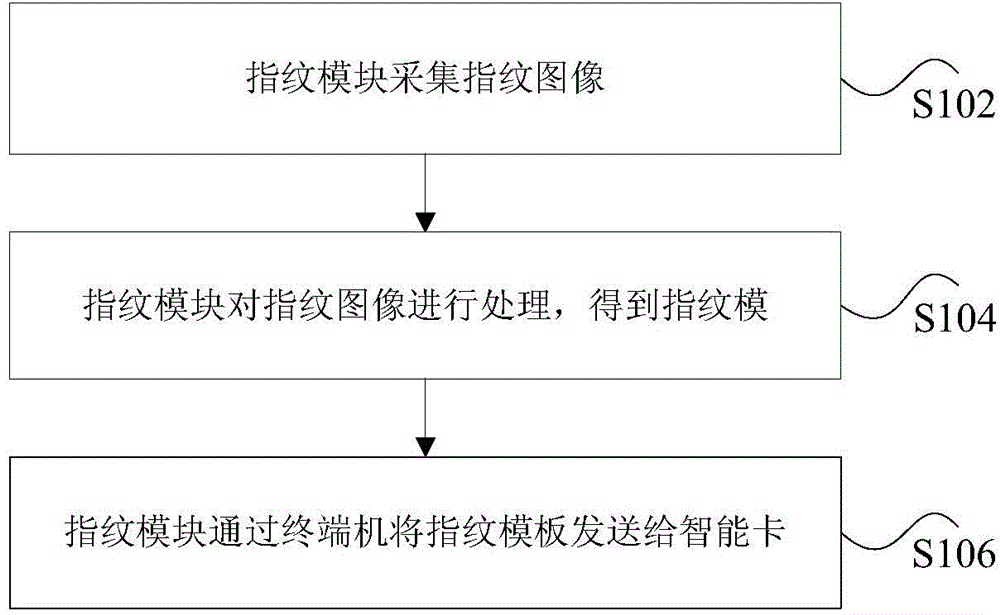
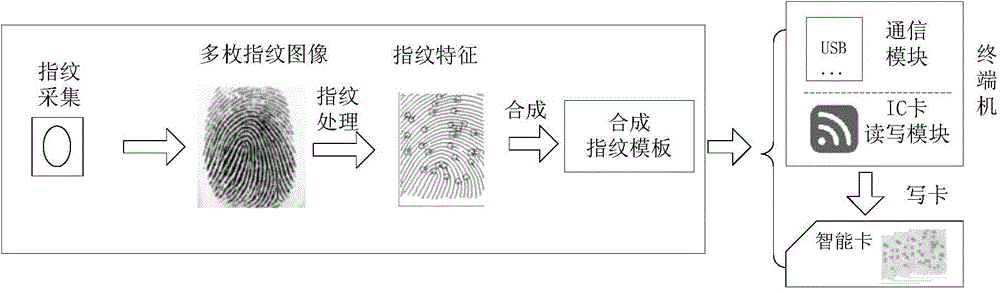
InactiveCN104573661APrevent leakageImprove securityCharacter and pattern recognitionSmart cardFingerprint image
The invention discloses a fingerprint data processing method and device. The fingerprint data processing method comprises the steps that a fingerprint image is collected by a fingerprint module; the fingerprint module processes the fingerprint image to obtain a fingerprint template; the fingerprint module sends the fingerprint template to a smart card through a terminal, and fingerprint comparison is conducted by the smart card according to the fingerprint template. By means of the fingerprint data processing method and device, the problem of insecurity of the smart card caused by fingerprint identification is solved, and the effect of improving the security of the smart card is achieved.
Owner:BEIJING TECHSHINO TECH
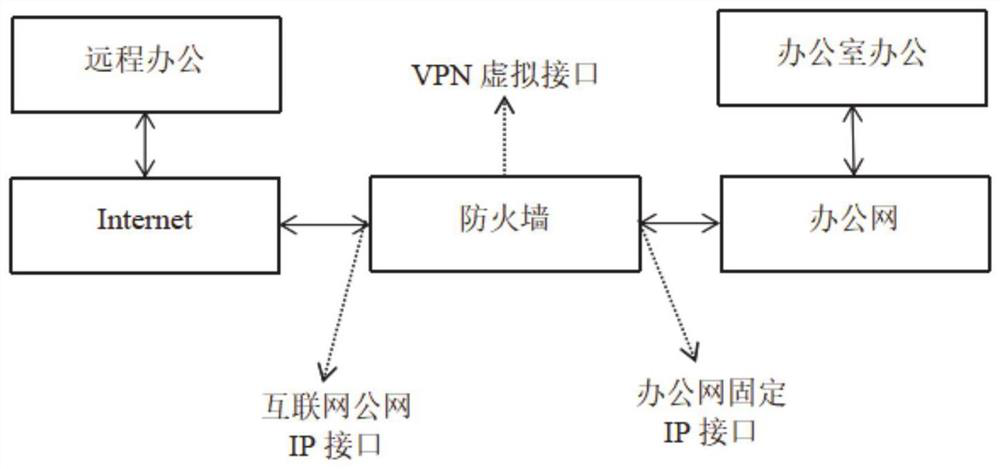
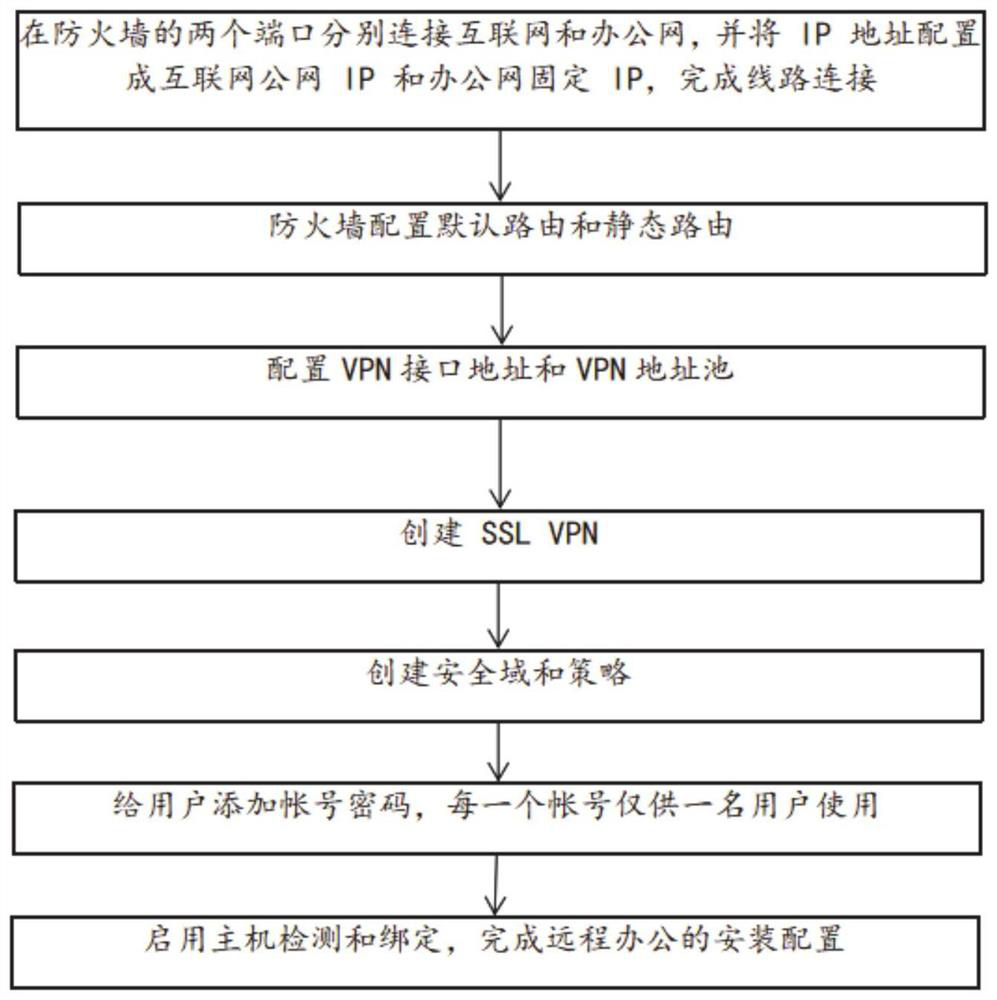
Remote office system based on data security
ActiveCN113395272AImprove securityImprove experiencePlatform integrity maintainanceTransmissionPrivate networkNetwork connection
Owner:GUANGDONG URBAN & RURAL PLANNING & DESIGN INST
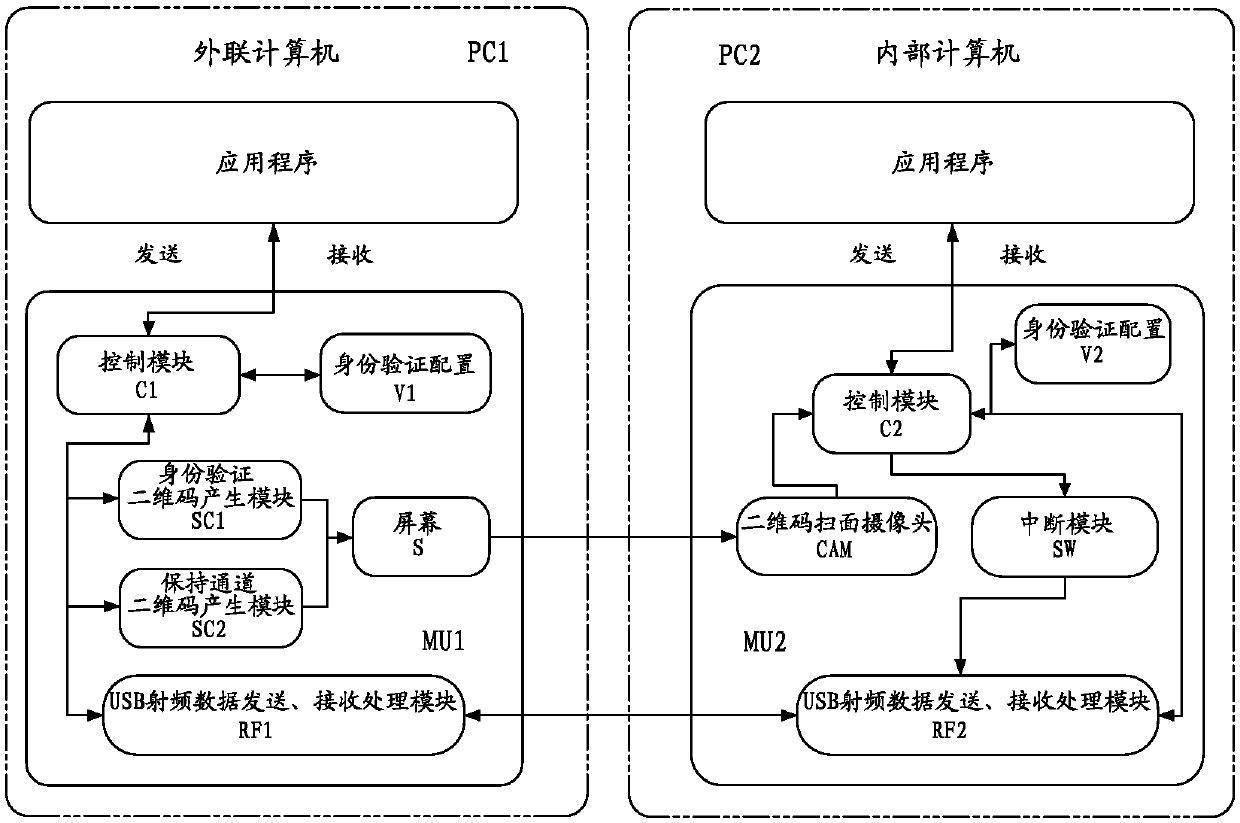
Network invasion preventing safe data transmission system and network invasion preventing safe data transmission method
The invention provides a network invasion preventing safe data transmission system and a network invasion preventing safe data transmission method. On condition that a network is physically isolated, data transmission between an internal-network computer and an external-network computer is realized through an RF communication module. In view of low safety in RF communication data transmission, identity authentication is performed between the internal-network computer and the external-network computer. Furthermore a data transmission manner with discontinuous RF communication intervals is used for frequently confirming the validity of the computer which transmits and receives data. Only under a precondition that the identity of the computer is valid, data transmission can be finished, thereby settling a problem of low safety in RF communication data transmission. Because high identity validity confirmation speed is realized in a two-dimensional code manner, speed and safety in data transmission are greatly improved. Data transmission speed in the network invasion preventing safe data transmission system and the network invasion preventing safe data transmission method is far higher than that of data transmission mode in which the two-dimensional code is utilized.
Owner:GREEN NET WORLD FUJIAN NETWORK TECH
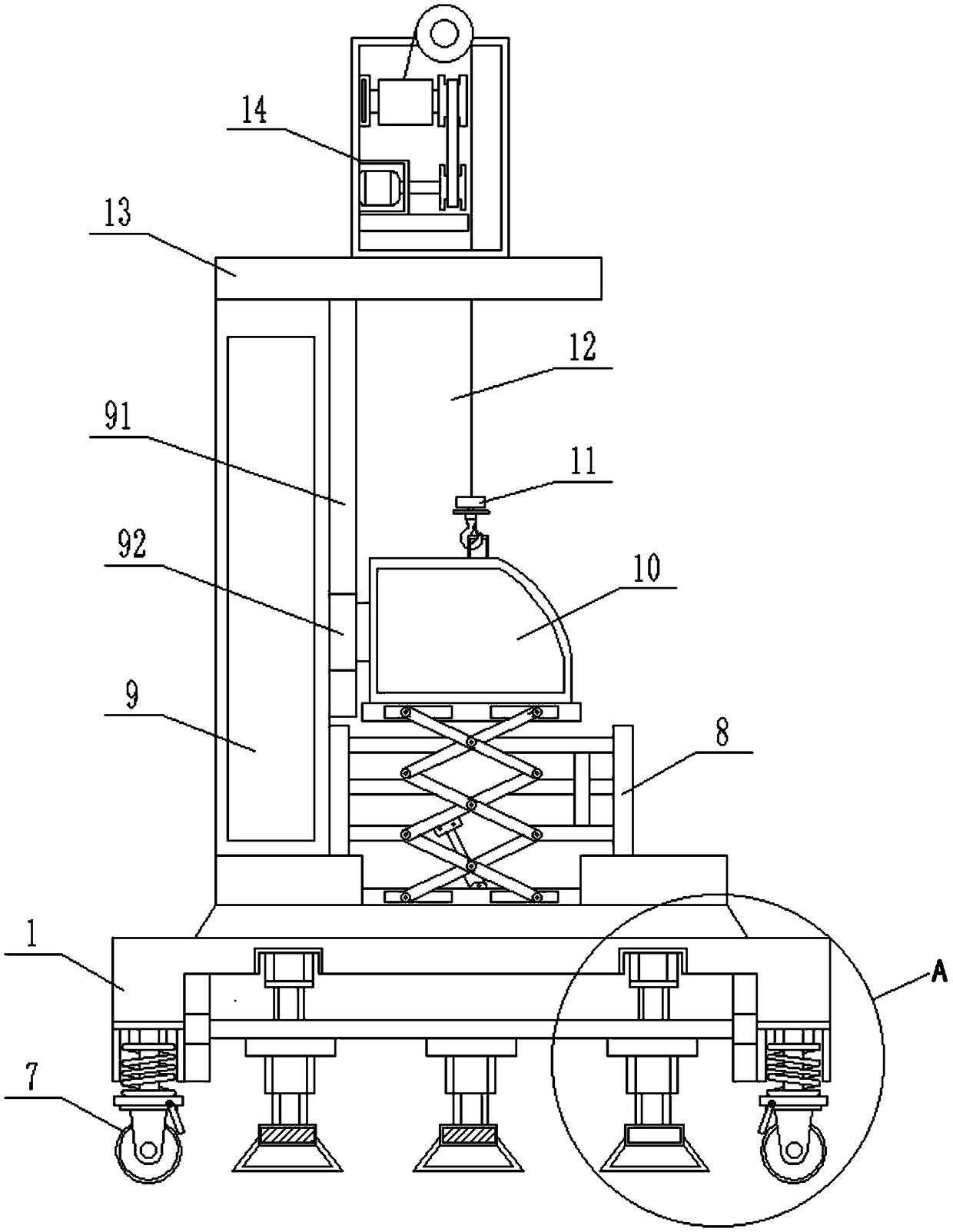
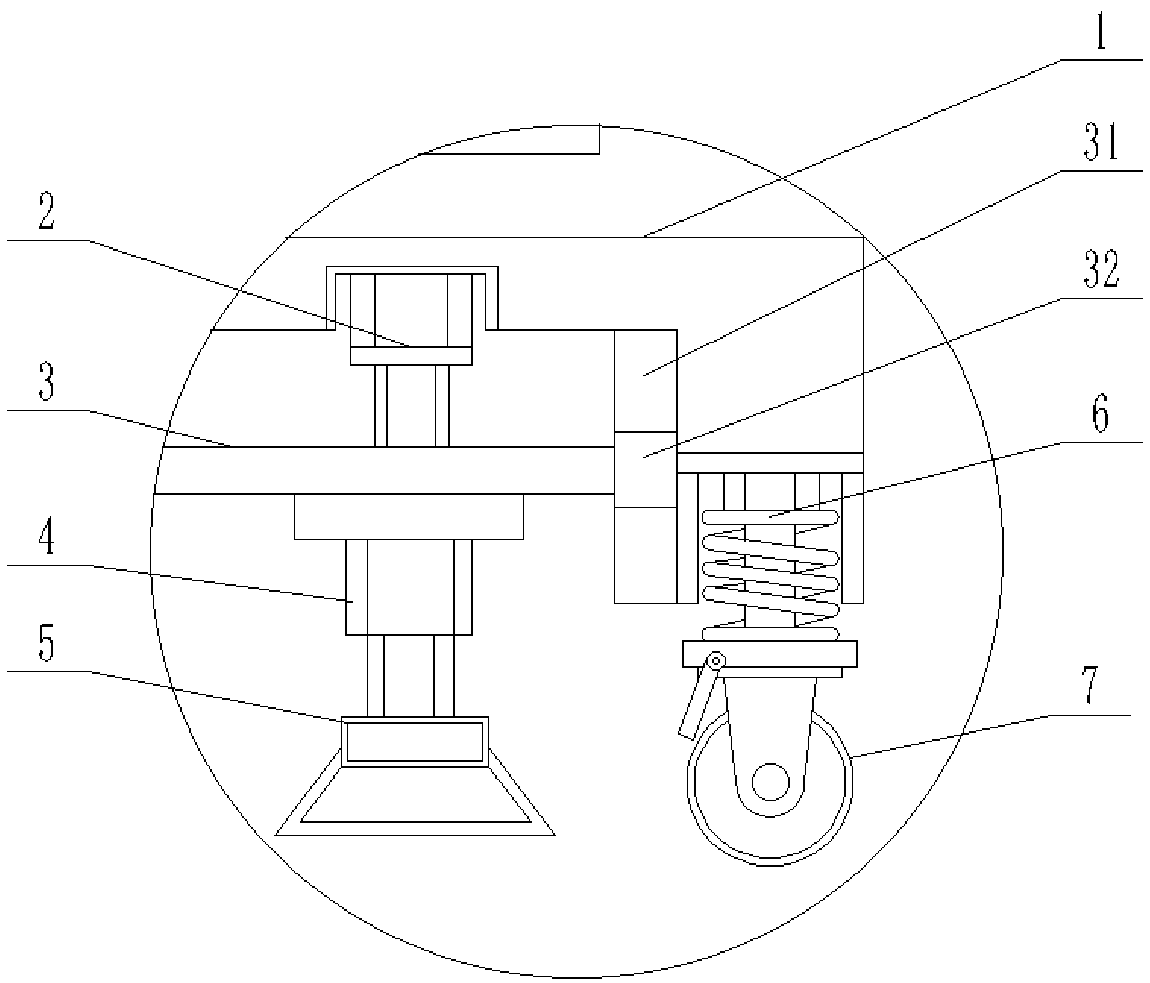
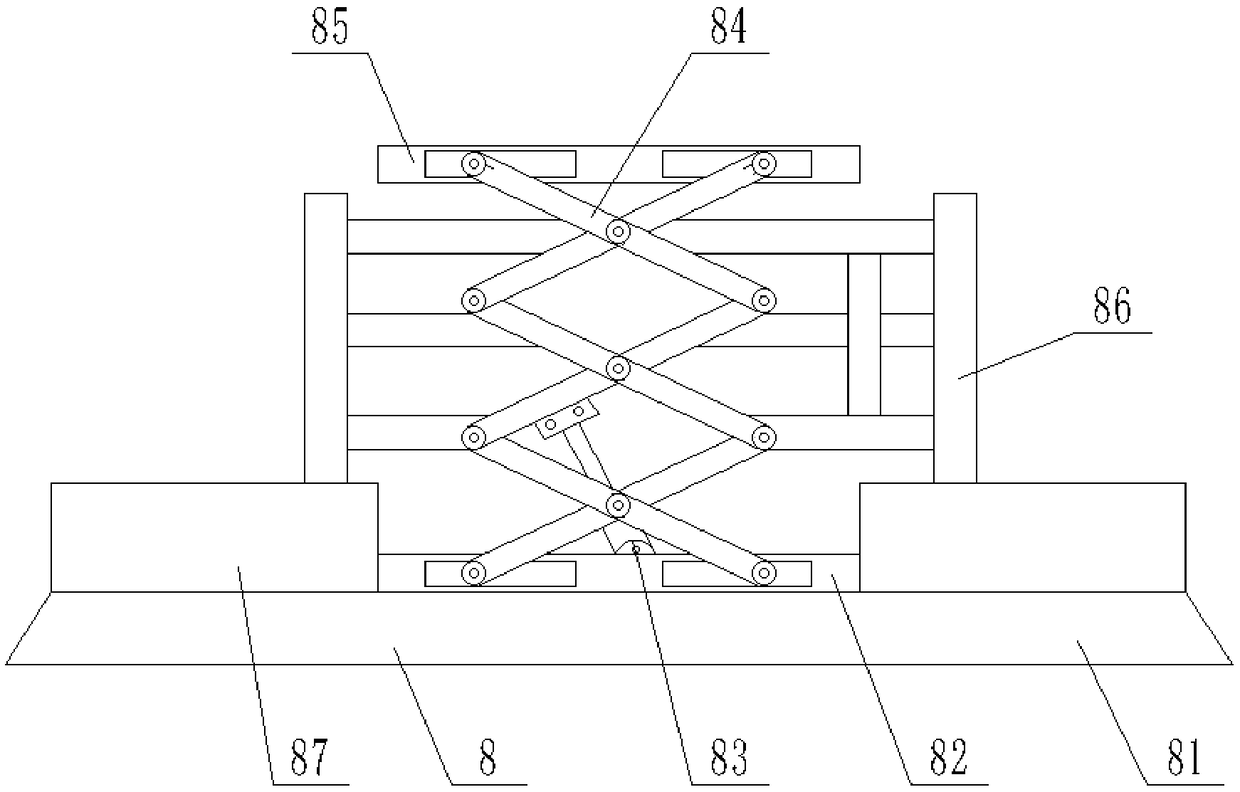
Fall preventing device for aerial operation
The invention discloses a fall preventing device for aerial operation. The device comprises a base plate; a first hydraulic cylinder is arranged at the bottom of the base plate; an output end of the first hydraulic cylinder is fixedly connected with a sliding plate; first slide blocks are fixedly connected to two sides of the sliding plate, and are slidingly connected to first chutes formed in thebase plate; a support rod is fixedly connected to the bottom of the sliding plate; the bottom of the support rod is fixedly connected with a support base; damping springs are arranged at four cornersof the bottom of the base plate; and universal wheels are fixedly mounted at the bottoms of the damping springs. The fall preventing device for aerial operation is provided with a lifting base; and workers sit in the lifting base, and are protected through matching and clamping between son buckles and mother buckles, so that the operation safety of the workers on a working platform is improved, the fall phenomenon of the workers during working is prevented, and the safety is improved.
Owner:JINAN LICHENG POWER SUPPLY CO OF STATE GRID SHANDONG ELECTRIC POWER CO +1
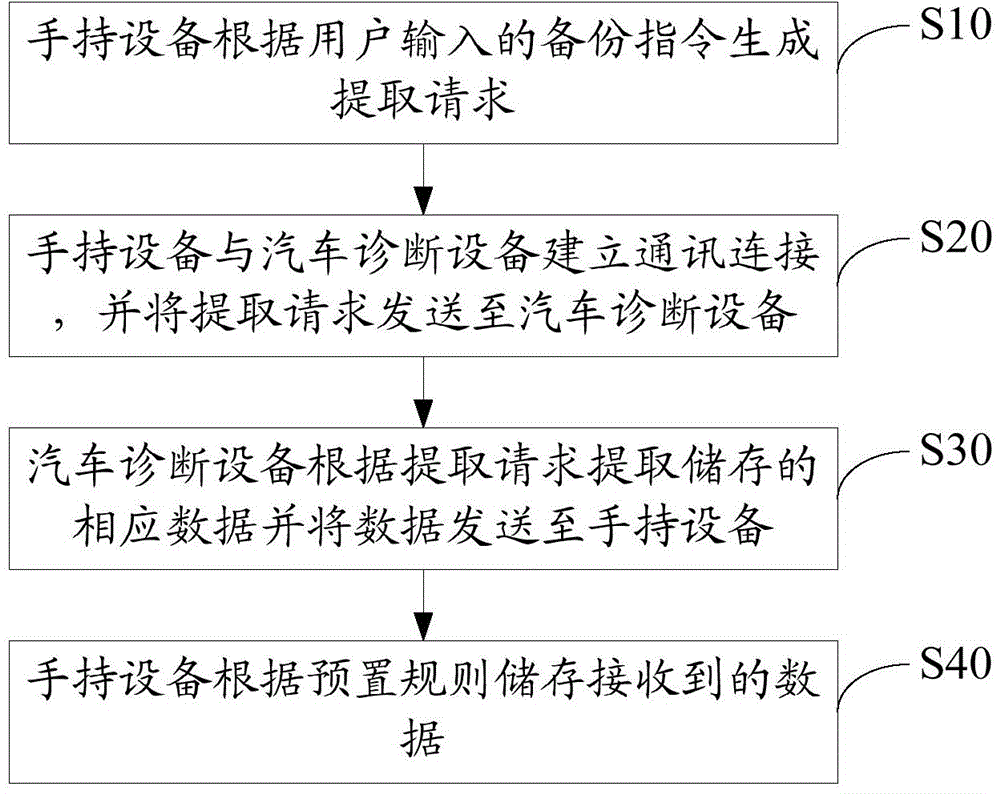
Method and system for backing up data of automobile diagnostic equipment
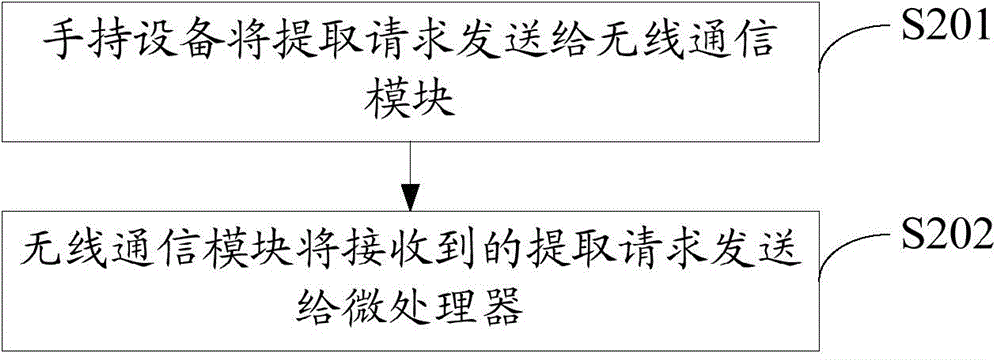
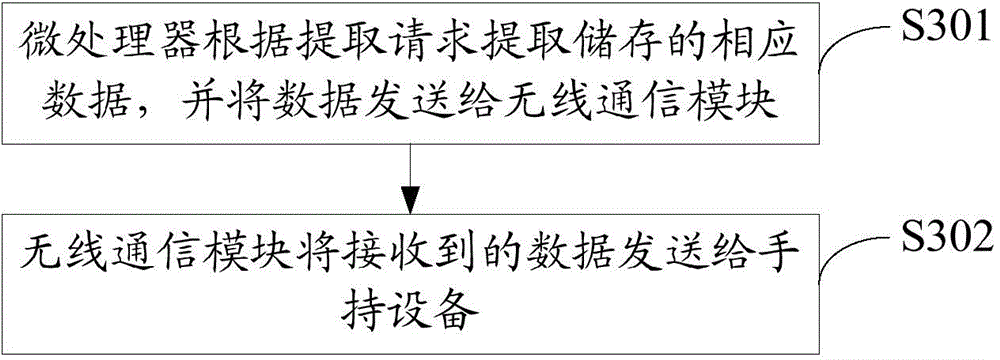
ActiveCN104656637ASolve insecurityEasy to carryElectric testing/monitoringUser inputComputer science
The invention discloses a method for backing up data of automobile diagnostic equipment. The method comprises the following steps: a handheld device generates an extract request according to a backup command input by a user; the handheld device communicates with the automobile diagnostic equipment and sends the extract request to the automobile diagnostic equipment; the automobile diagnostic equipment extracts the stored corresponding data according to the extract request and sends the data to the handheld device; the handheld device stores the received data according to a pre-setting rule. The invention further discloses a system for backing up the data of the automobile diagnostic equipment. The method and the system solve the problem that the data of the automobile diagnostic equipment is unsafe when stored in the local storage space.
Owner:LAUNCH SOFTWARE DEV
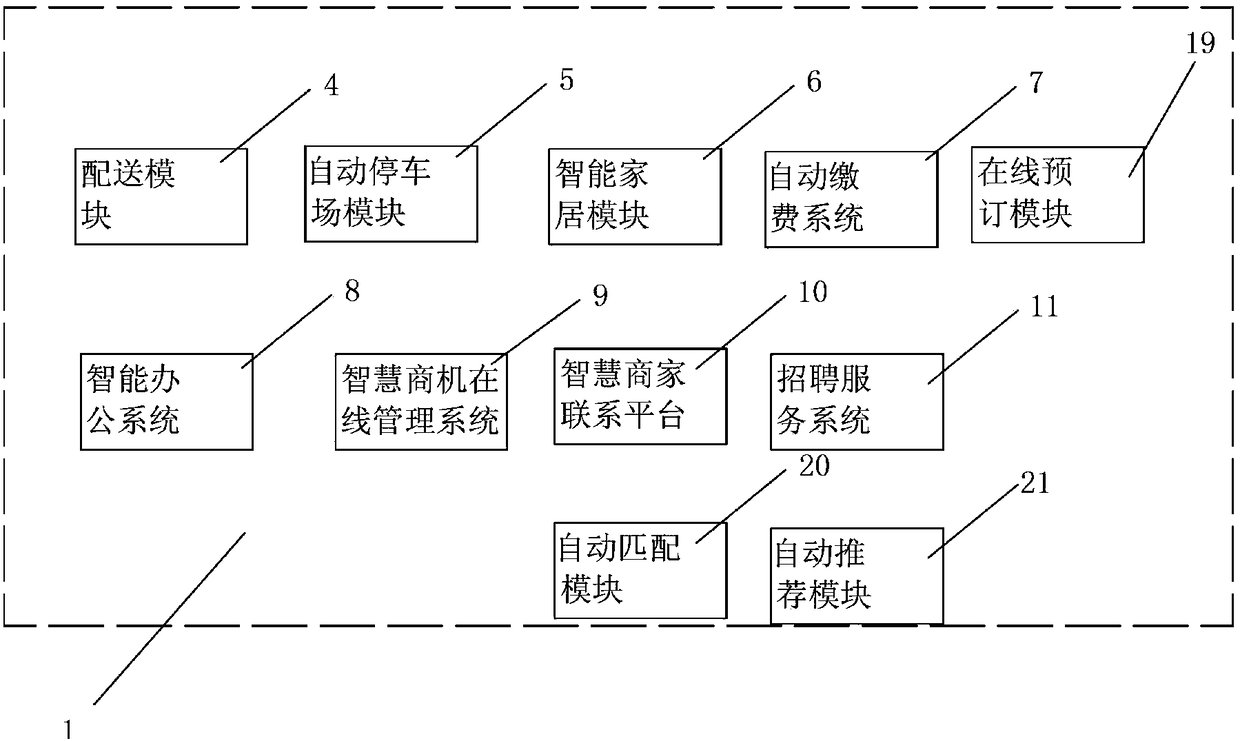
Smart city platform and method thereof
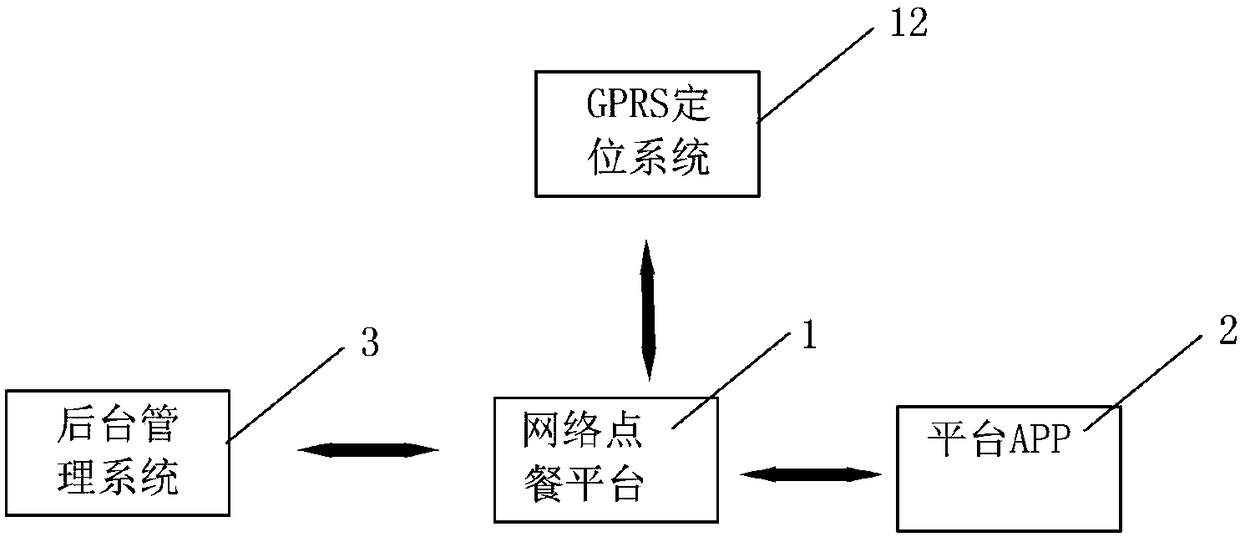
InactiveCN108133439ANo manual operationExact searchReservationsBuying/selling/leasing transactionsOnline bookingGps positioning system
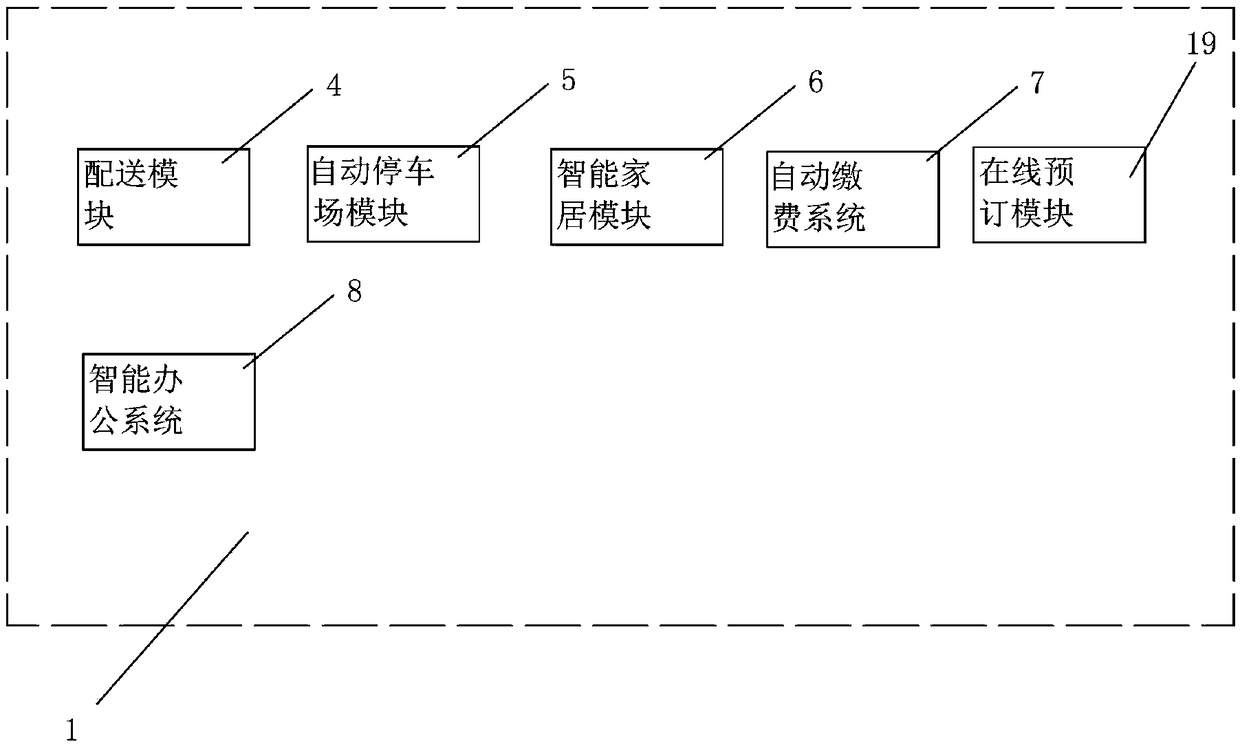
The present invention discloses a smart city platform and a method thereof. The smart city platform comprises an online shopping platform, a platform APP, a background management system and a GPS positioning system that are connected through the Internet. The online shopping platform comprises an online booking module capable of online booking of a merchant store service, a delivery module capableof delivering orders in an online manner, an automatic parking module capable of obtaining parking condition of the parking lot by connecting to the merchant parking plot through the network, and carrying out parking space reservation and automatic parking, a smart home system for implementing network control with the smart home system, an automatic payment system capable of implementing automatic life payment, and a smart office system that connects with the government public sector to implement online public appointment service. The method disclosed by the present invention can solve the problem of download of too many APPs; the problem of insecure personal information in the memory card caused by that an account will be registered for each download of an APP; the problem of the over stuck phone; and the problem of difficult sales or inability to attract customers.
Owner:广州掌里通网络科技有限公司
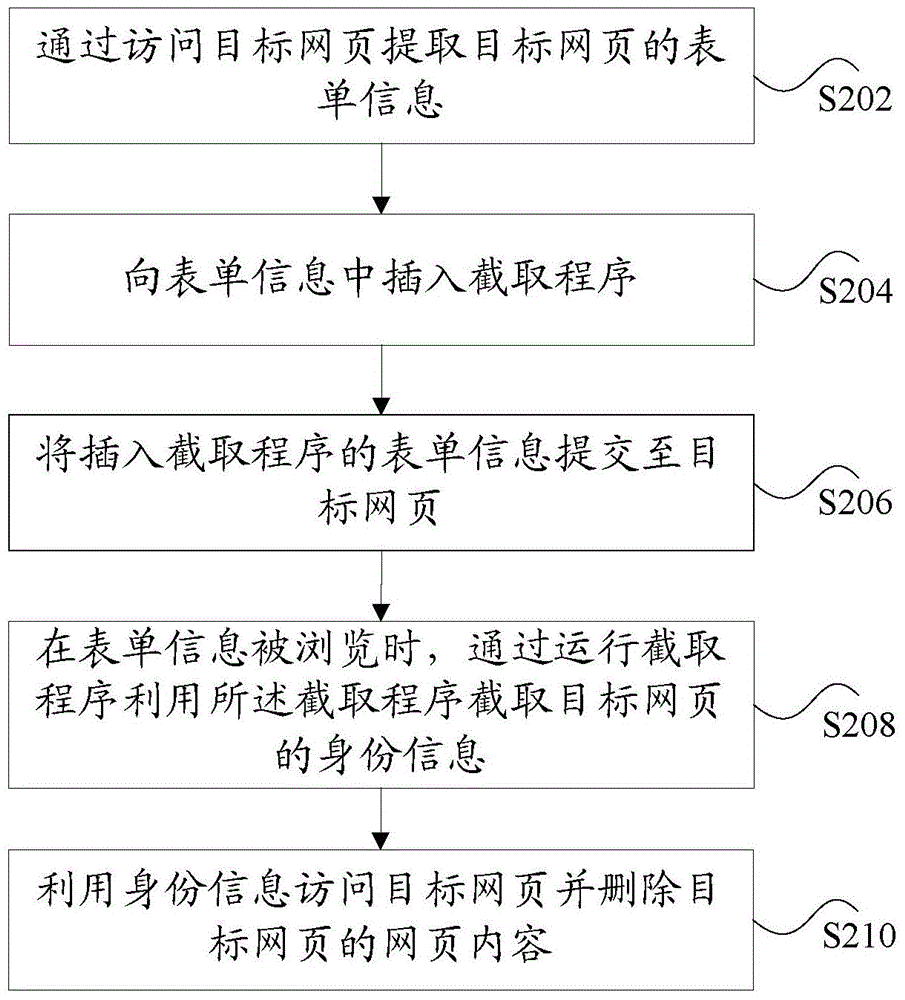
Webpage processing method and device
InactiveCN105095309ASolve insecurityImprove securityTransmissionSpecial data processing applicationsWeb pageDatabase
The invention discloses a webpage processing method and device. The webpage processing method comprises the following steps: accessing a target webpage to extract the form information of the target webpage; inserting an interception program into the form information, wherein the interception program is used for intercepting the identity information of the target webpage; submitting the form information which is inserted into the interception program to the target webpage; when the form information is browsed, intercepting the identity information of the target webpage through the running of the interception program; and utilizing the identity information to access the target webpage, and deleting the webpage content of the target webpage, wherein the webpage content corresponds to the form information. The problem of insecure user information since the user information is lost is solved so as to achieve an effect that the safety of the user information is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
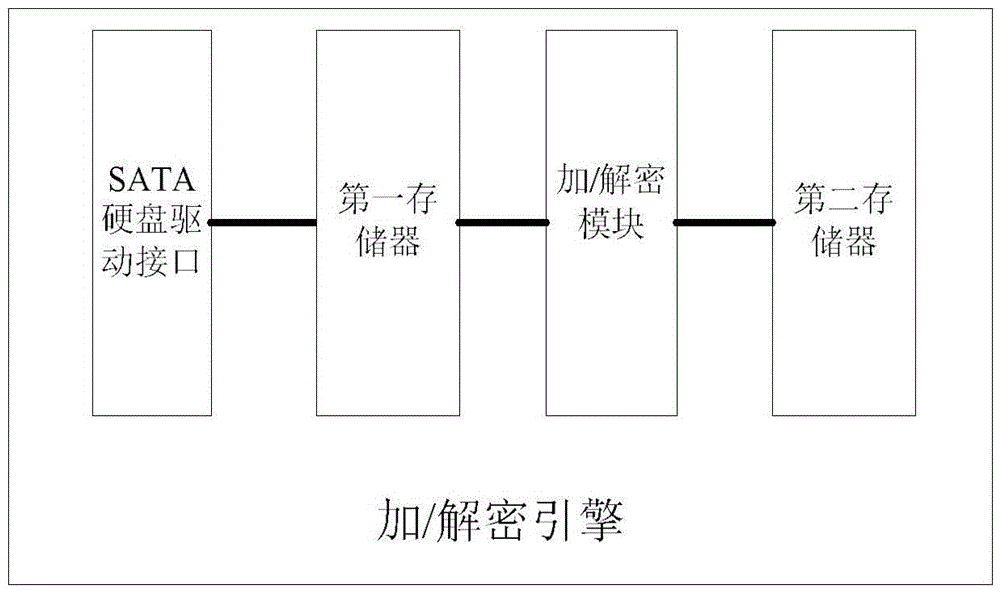
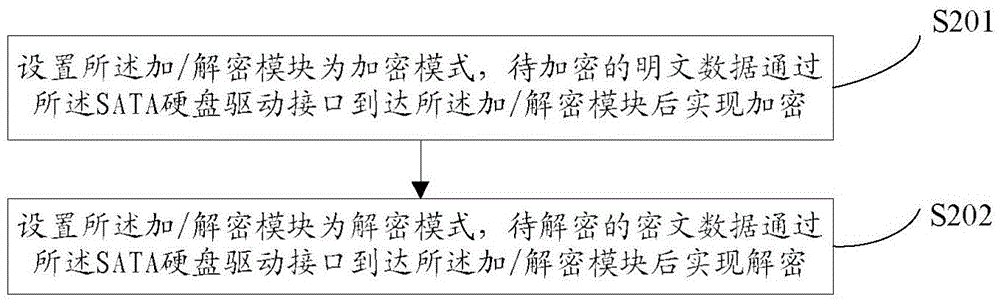
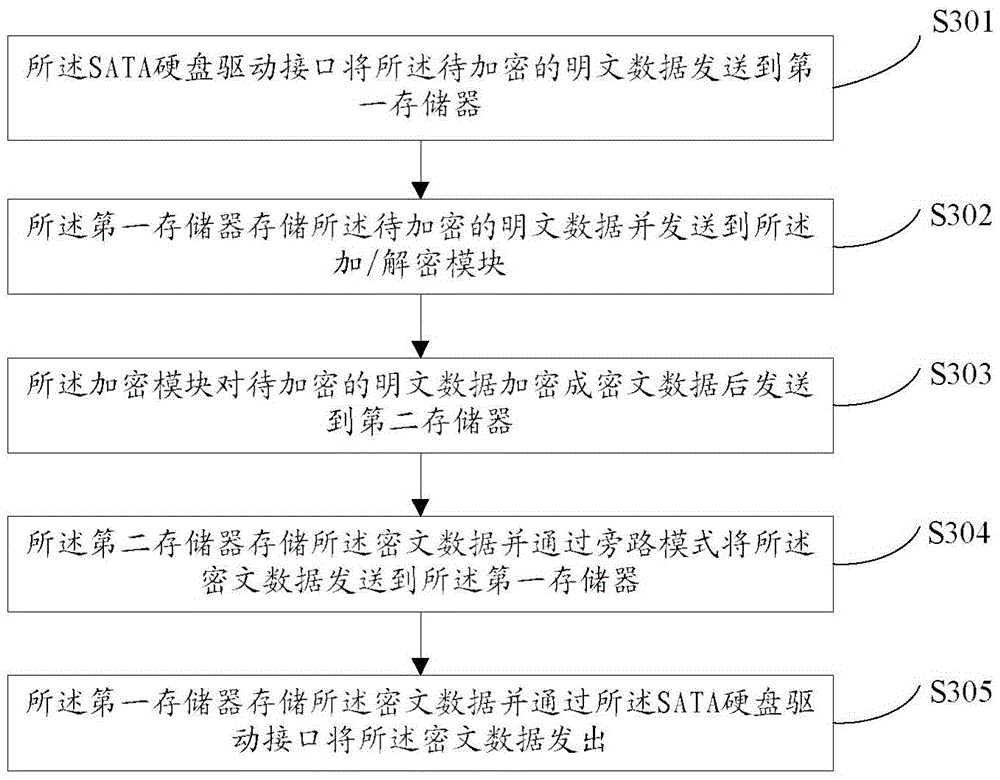
Encryption/decryption engine and implementation method thereof
InactiveCN105550605AImprove compatibilitySolve insecurityInternal/peripheral component protectionHard disk drive interfaceSoftware engineering
The embodiment of the invention discloses an encryption / decryption engine and an implementation method thereof and is applied to the technical field of information safety. The encryption / decryption engine can specifically comprise a first memory, a second memory, an encryption / decryption module and an SATA (Serial Advanced Technology Attachment) hard disk drive interface, wherein one end of the first memory is connected with the SATA hard disk drive interface and the other end of the first memory is connected with the encryption / decryption module; the second memory is connected with the encryption / decryption module; one end of the encryption / decryption module is connected with the first memory and the other end of the encryption / decryption module is connected with the second memory; and one end of the SATA hard disk drive interface is connected with the first memory and the other end of the SATA hard disk drive interface is connected with an SATA host interface of a mainboard. By means of the implementation method of the encryption / decryption engine, provided by the embodiment of the invention, the encryption / decryption module which is safer, more reliable, higher in performance and better in compatibility can be provided for information safety service providers.
Owner:BEIJING HUAHONG INTEGRATED CIRCUIT DESIGN
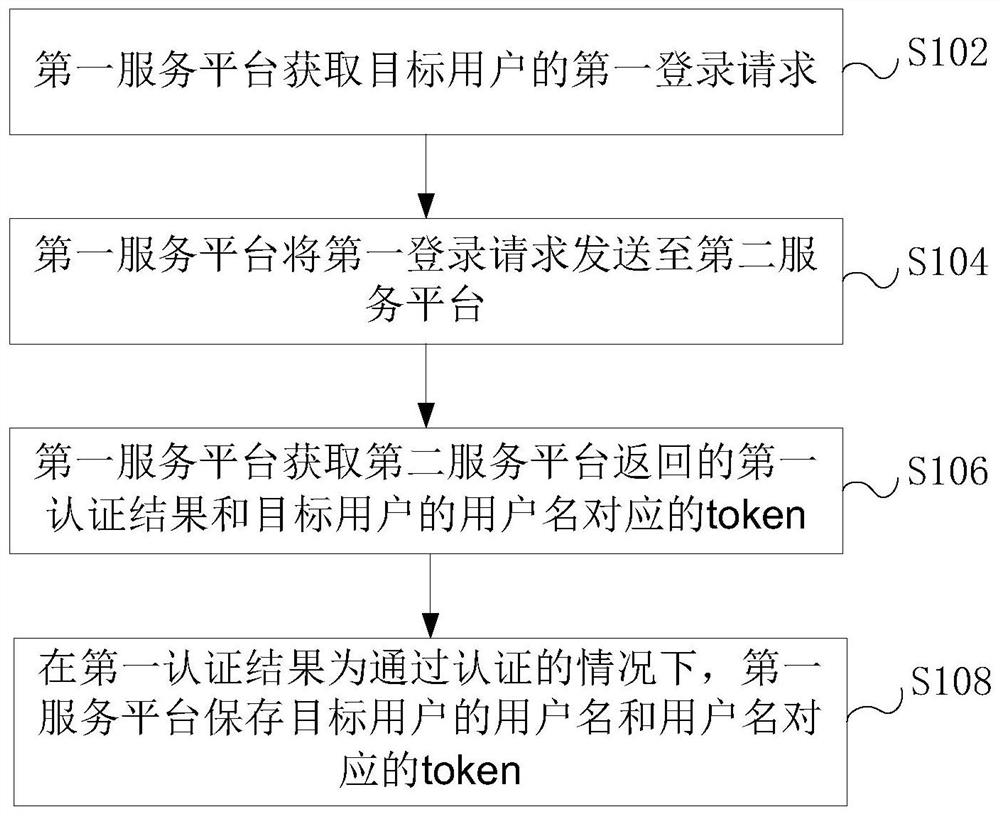
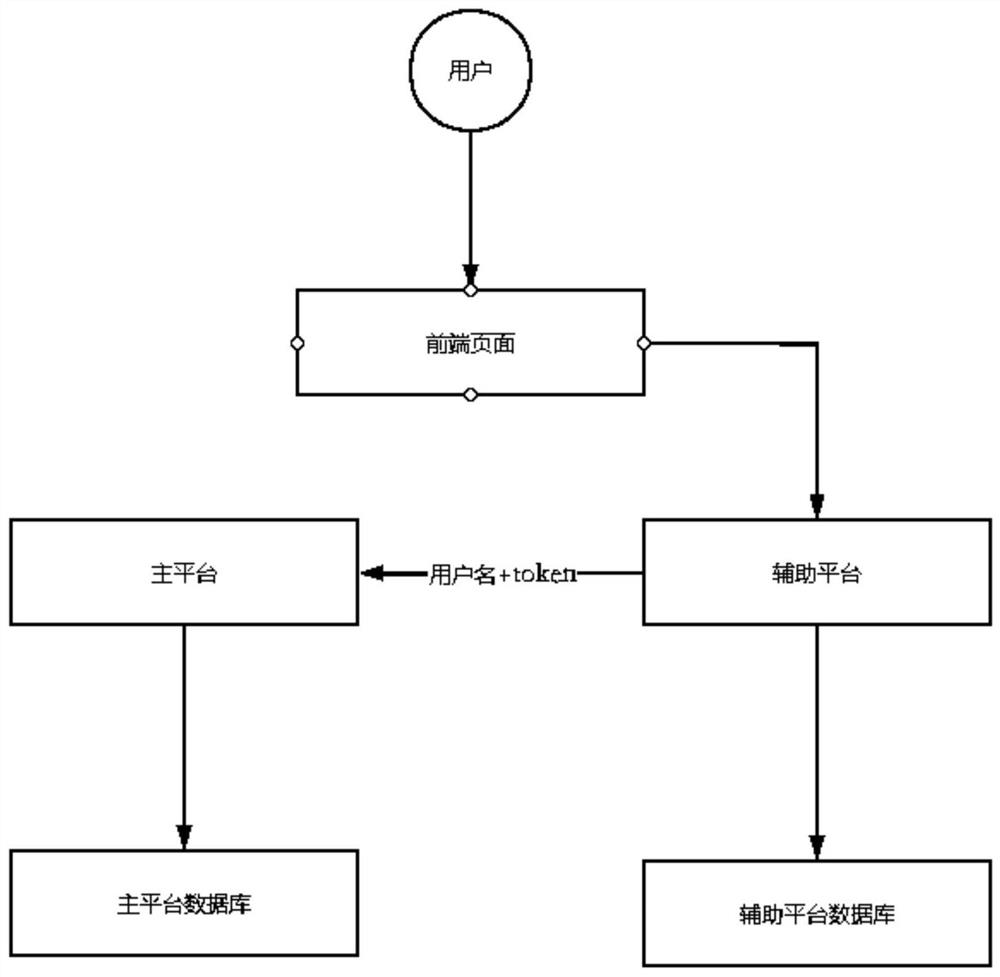
Token-based authentication method and device, storage medium and electronic device
InactiveCN113055185ASolve insecurityProtection securityUser identity/authority verificationPasswordEngineering
The embodiment of the invention provides a token-based authentication method and device, a storage medium and an electronic device, and the method comprises the steps that a first service platform obtains a first login request of a target user, wherein the first login request comprises a user name and a login password of the target user; the first service platform sends the first login request to a second service platform, instructs the second service platform to perform login authentication on a target user, stores a user name and a login password of the target user, and generates a token corresponding to the user name; the first service platform obtains a first authentication result returned by the second service platform and a token corresponding to the user name of the target user; and when the first authentication result is that authentication is passed, the first service platform stores the user name of the target user and the token corresponding to the user name. The problem that in the related technology, when a user logs in a service platform through a user name and a password, the service platform needs to access a database storing the password, and consequently user information is not safe is solved.
Owner:的卢技术有限公司
Breaker test line hitching rod
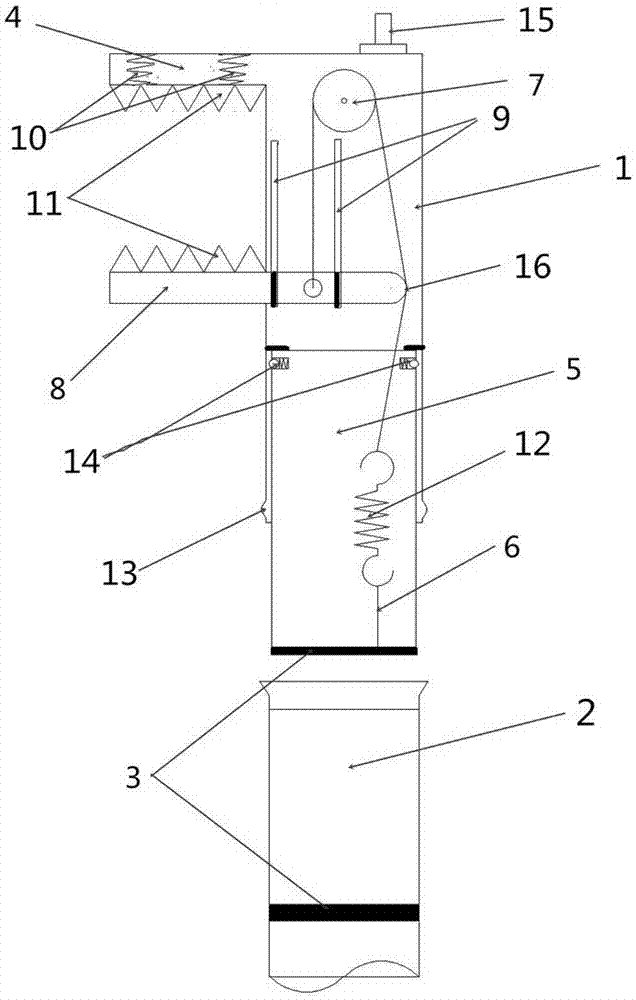
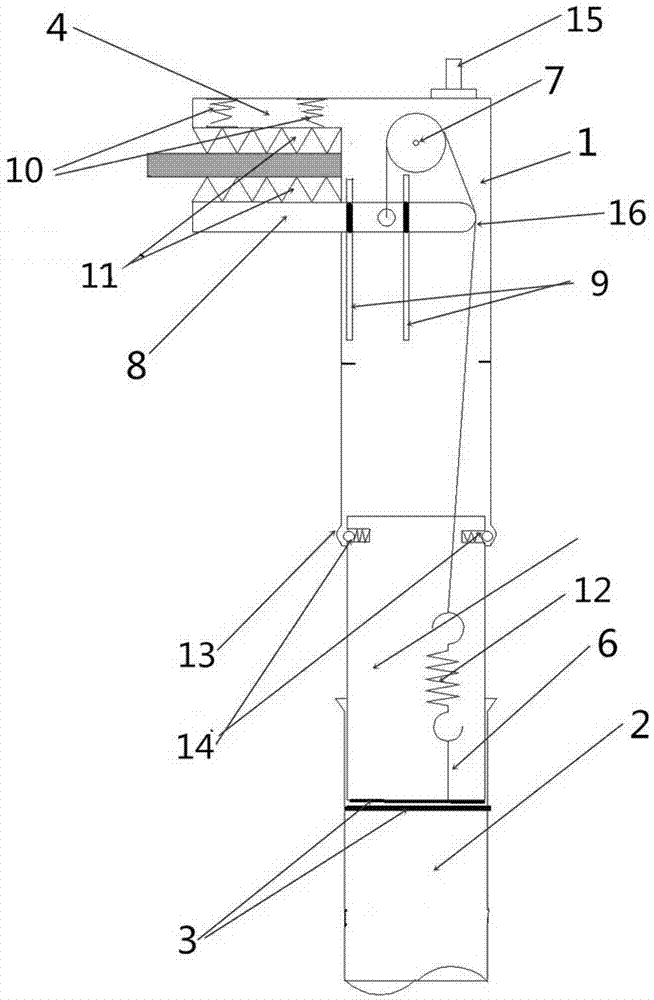
ActiveCN107064574AWon't fall offEasy to useMeasurement instrument housingFriction forceCircuit breaker
The invention relates to a breaker test line hitching rod. The breaker test line hitching rod comprises a clamping head and an operation rod, and the clamping head is inserted into an insertion hole in an upper part of the operation rod; the clamping head comprises a fixed clamping head, a moving clamping head and a movable guide rod; and the overall fixed clamping head is 7-shaped, the bottom of the fixed clamping head is connected with the movable guide rod, the moving clamping head is installed at the middle part of the fixed clamping head and is disposed in a manner that the moving clamping head is parallel to the top of the fixed clamping head, a fixed pulley is installed on the fixed clamping head, one end of a transmission steel wire rope is connected to the moving clamping head, and the other end of the transmission steel wire rope bypasses the fixed pulley and then is connected to the movable guide rod. A breaker wire plate is clamped through cooperation between the fixed clamping head and the moving clamping head performing upward movement, and the clamping head keeps in a clamped state by utilizing a friction force between the steel wire rope and the moving clamping head. The breaker test line hitching rod ahs the advantages of the light weight, firm structure and convenient assembling and disassembling; no vibration can enable the clamping head to fall off after the clamping head is clamped tightly; and the problem of test line hitching unsafety when a breaker characteristic test is performed is solved completely.
Owner:TIELING POWER SUPPLY COMPANY OF STATE GRID LIAONING ELECTRIC POWER COMPANY +1
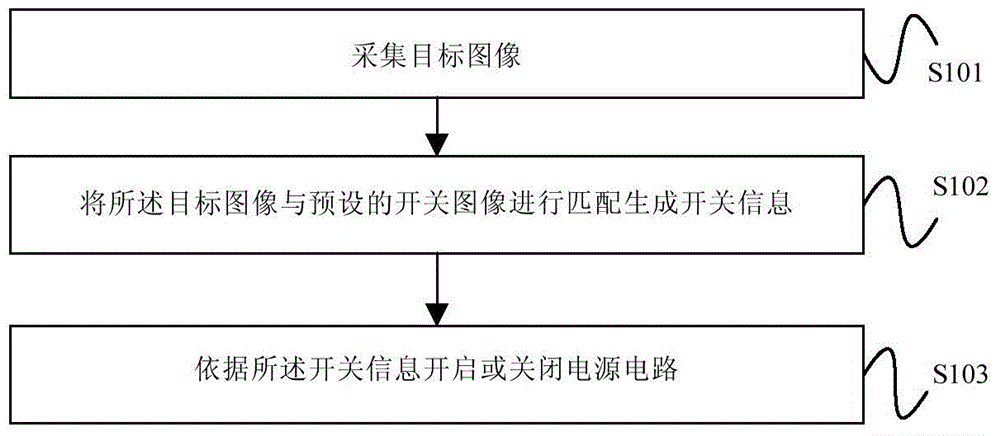
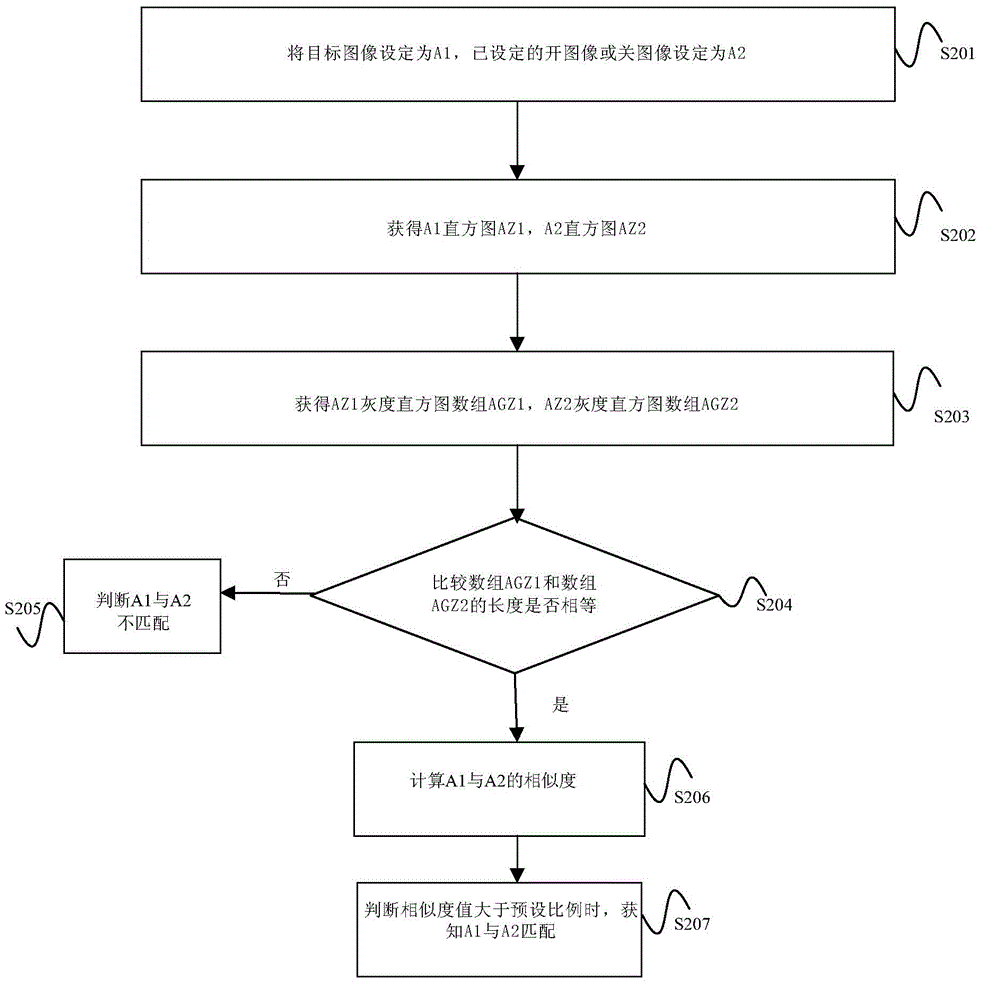
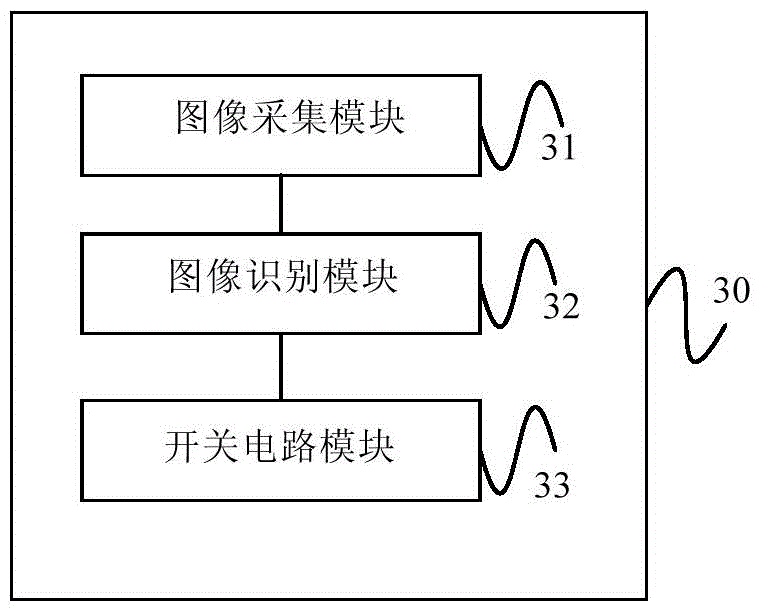
Power circuit control method and device
InactiveCN105334765ASolve insecurityProgramme controlComputer controlInformation controlContact type
The invention provides a power circuit control method and device. The method comprises that an object image is collected; the object image is coupled with a preset switching image to generate switching information; and a power circuit is switched on or off according to the switching information. Thus, the power circuit can be controlled needless of touching a switch by fingers, and the problem that a contact type control switch is unsafe is solved.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
Anti-rebound device suitable for bomb fixing mechanism of cluster bomb separating device
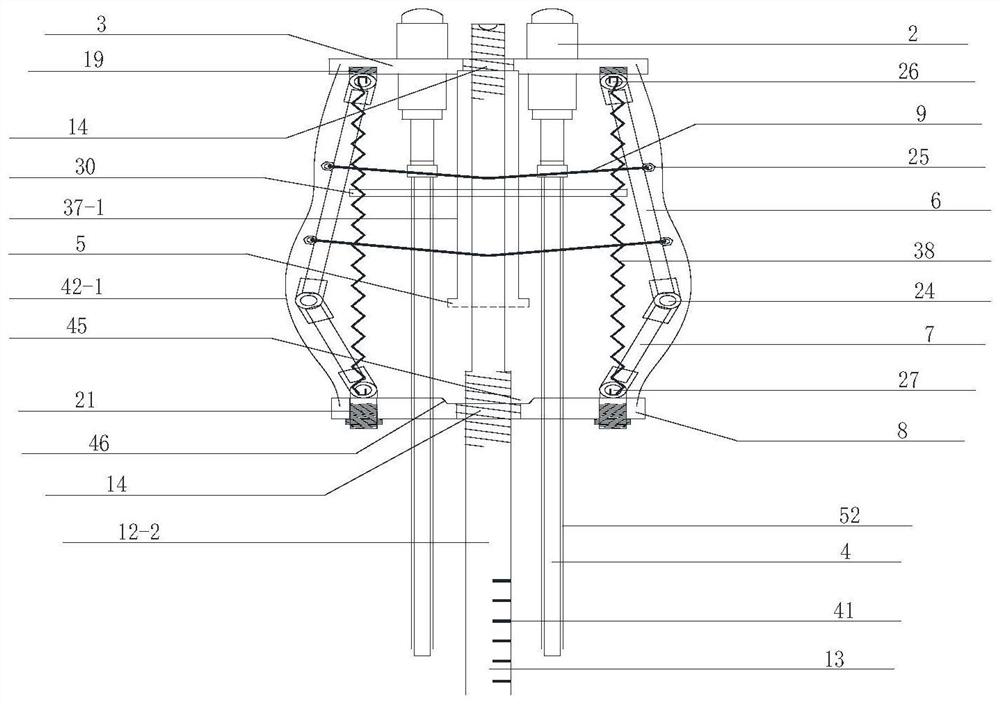
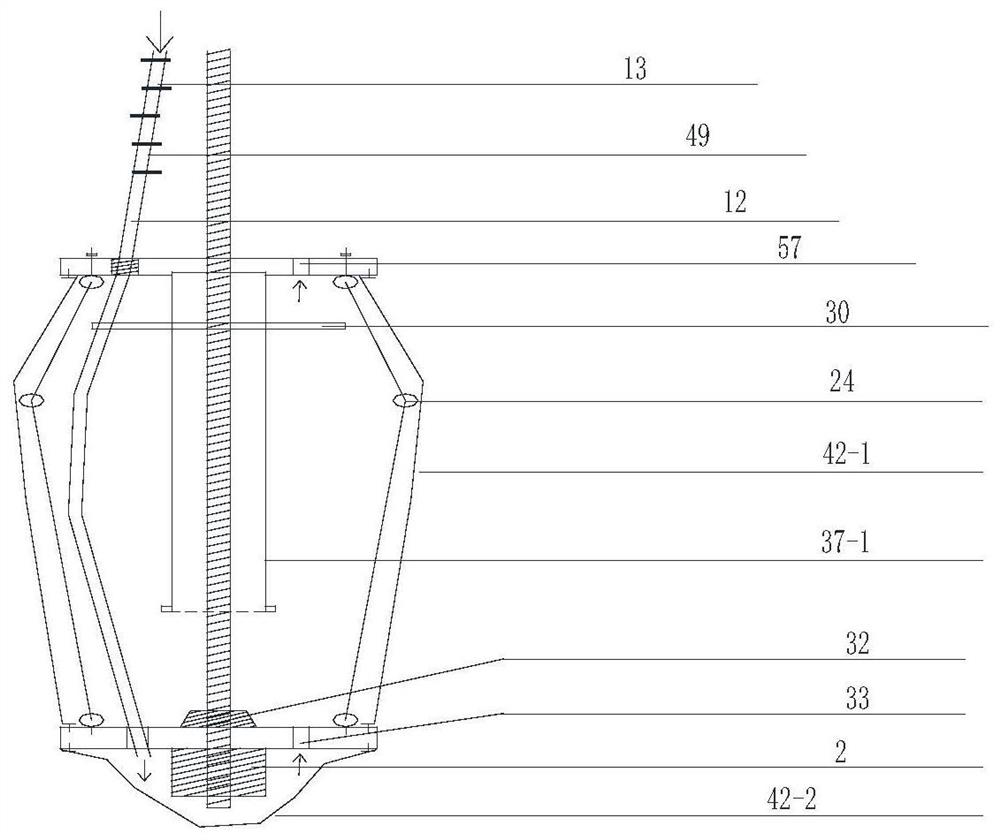
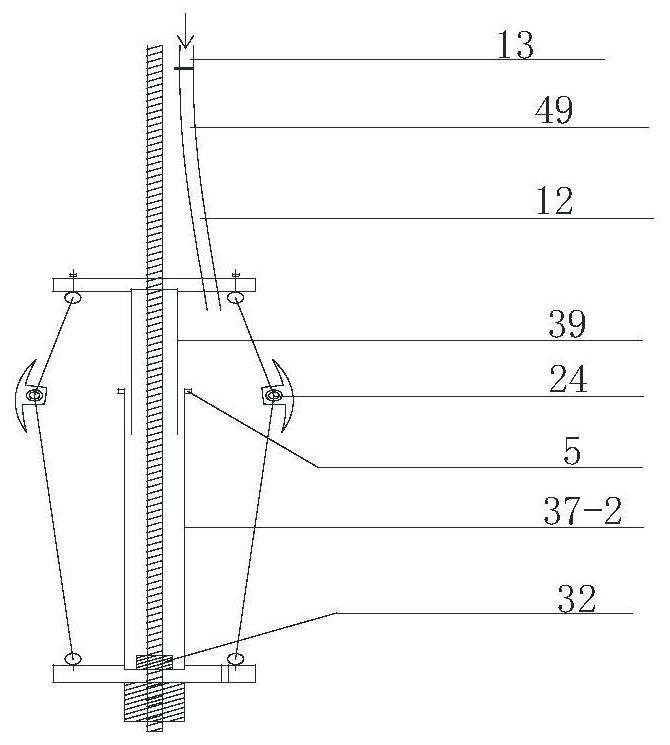
ActiveCN111412784ASolve insecurityRebound blockSafety arrangementLaunching weaponsCrankStructural engineering
The invention provides an anti-rebound device suitable for a bomb fixing mechanism of a cluster bomb separating device. The anti-rebound device comprises a crank seat, an anti-rebound assembly and a four-connecting-rod mechanism, the crank seat is provided with a first accommodating space, the anti-rebound assembly is installed in the first accommodating space, the anti-rebound assembly is provided with a stop pin, and when a missile is launched, the four-connecting-rod mechanism rotates around a fixed rotating shaft from an initial position to achieve missile unlocking and expose the shieldedanti-rebound assembly, and the stop pin is ejected out of the anti-rebound assembly and extends to the outer portion of the crank base so as to limit the four-connecting-rod mechanism to return to the initial position. According to the anti-rebound device suitable for the bomb fixing mechanism of the cluster bomb separating device, the anti-rebound assembly is installed on the crank base, the stop pin can be automatically ejected out by combining the spring, the problem that in the prior art, a tension spring or a rubber pad cannot completely restrain rebound of the bomb fixing mechanism, andconsequently the missile is unsafe is solved, rigid anti-rebound blocking is achieved through rebound of the four-connecting-rod mechanism, and the anti-rebound device is simple in structure, safe and reliable.
Owner:SHANGHAI INST OF ELECTROMECHANICAL ENG
Remote control breaker opening mechanism
PendingCN111933484ASolve insecurityReduce restrictionsHigh-tension/heavy-dress switchesAir-break switchesWireless transmissionRemote control
The invention discloses a remote control circuit breaker opening mechanism. The mechanism comprises a main body and a remote controller. The main body comprises a top head, a driving unit, a control unit and a wireless signal receiver. After a control button of the remote controller is pressed, a switching-off signal can be sent to the wireless signal receiver in a wireless mode through the wireless signal transmitter. And the control unit can control the driving unit to drive the top head to move after the wireless signal receiver receives the opening signal so as to push an emergency openingtripping button of the circuit breaker. According to the remote control circuit breaker opening mechanism, the remote controller is arranged, the wireless signal transmitter and the wireless signal receiver are arranged, wireless signal transmission is conducted between the remote controller and the controller through the wireless signal transmitter and the wireless signal receiver, an operator can execute operation after retreating to a safe position according to needs, due to wireless transmission, limitation on the operator is small, and operation is easy and convenient.
Owner:STATE GRID ZHEJIANG HANGZHOU YUHANG POWER SUPPLY +2
Energy-saving combined window capable of sliding, flat-opening and rotating in 360 degree
InactiveCN100439646CAdjust the opening area at willEasy to cleanSealing arrangementsWing arrangementsEngineeringEnergy analysis
Owner:东营威辰节能技术开发有限公司
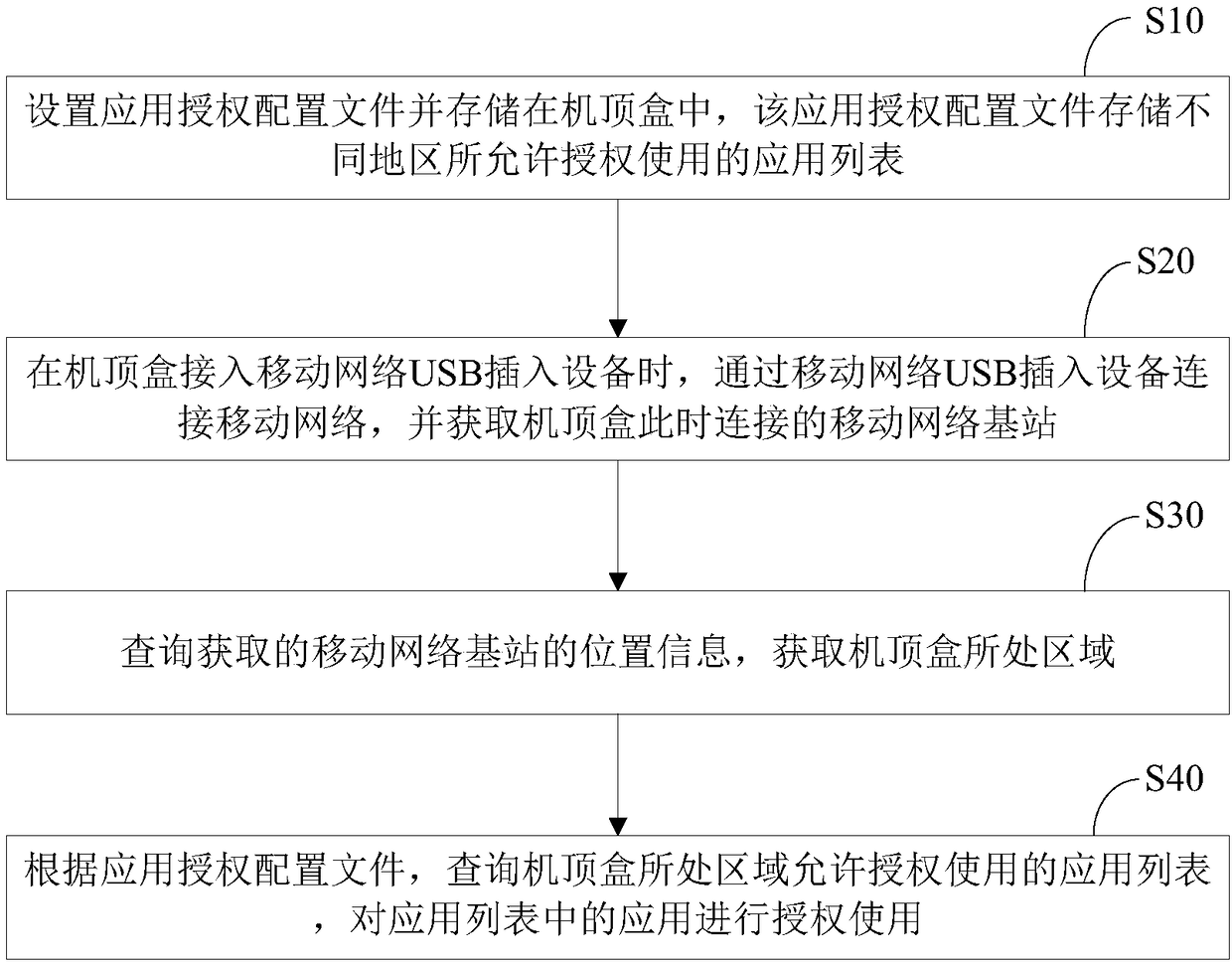
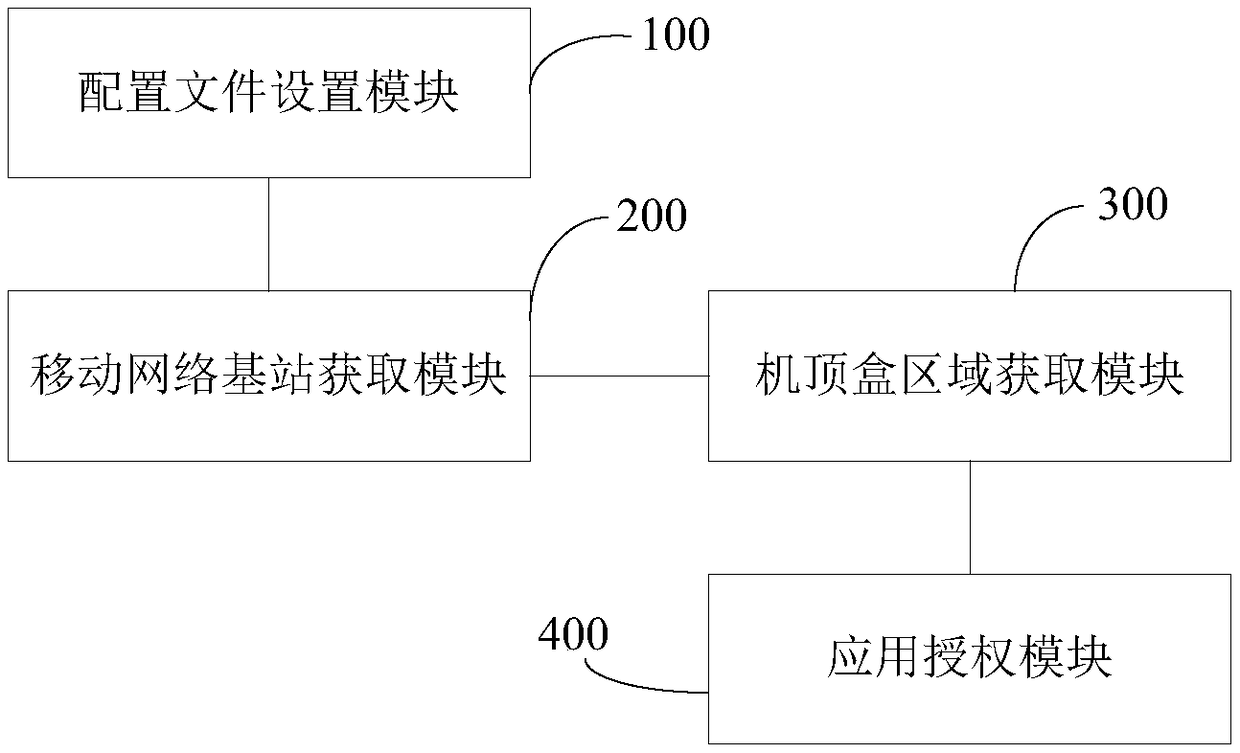
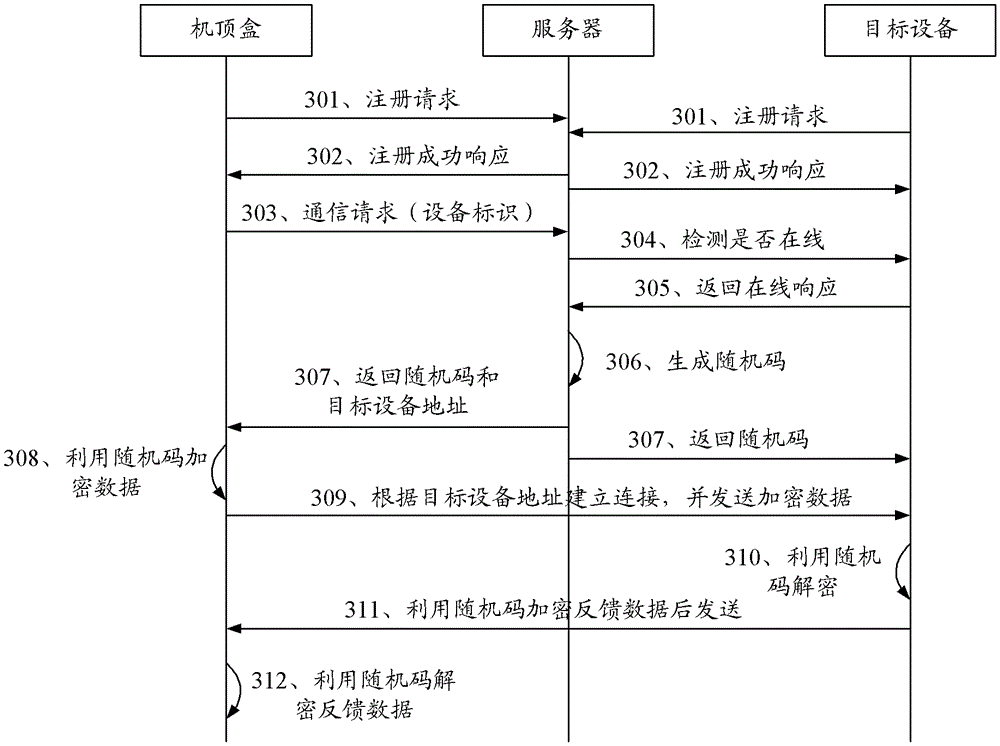
Set top box application authorization application method and system
ActiveCN108650530AEffective protectionSolve insecuritySelective content distributionPasswordSecret code
The invention relates to a set top box application authorization application method and system. According to the method, a function of a set top box supporting a USB plug-in device of a mobile networkis used for obtaining location information of a connected mobile network base station when the set top box accesses the mobile network, and determining an area where the set top box is located, thereby, according to the application authorization profile stored in the set top box, querying the application in the area allowed for authorization. The set top box application authorization applicationmethod and system in the invention do not require a user to verify the account password on the Internet again, thereby solving the problem that the user account password is leaked and the user information is not safe, and effectively protecting the user information.
Owner:SHENZHEN JIUZHOU ELECTRIC
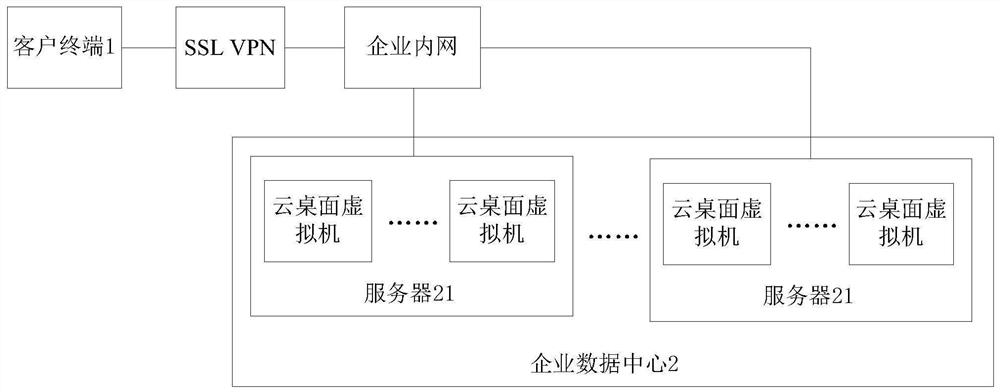
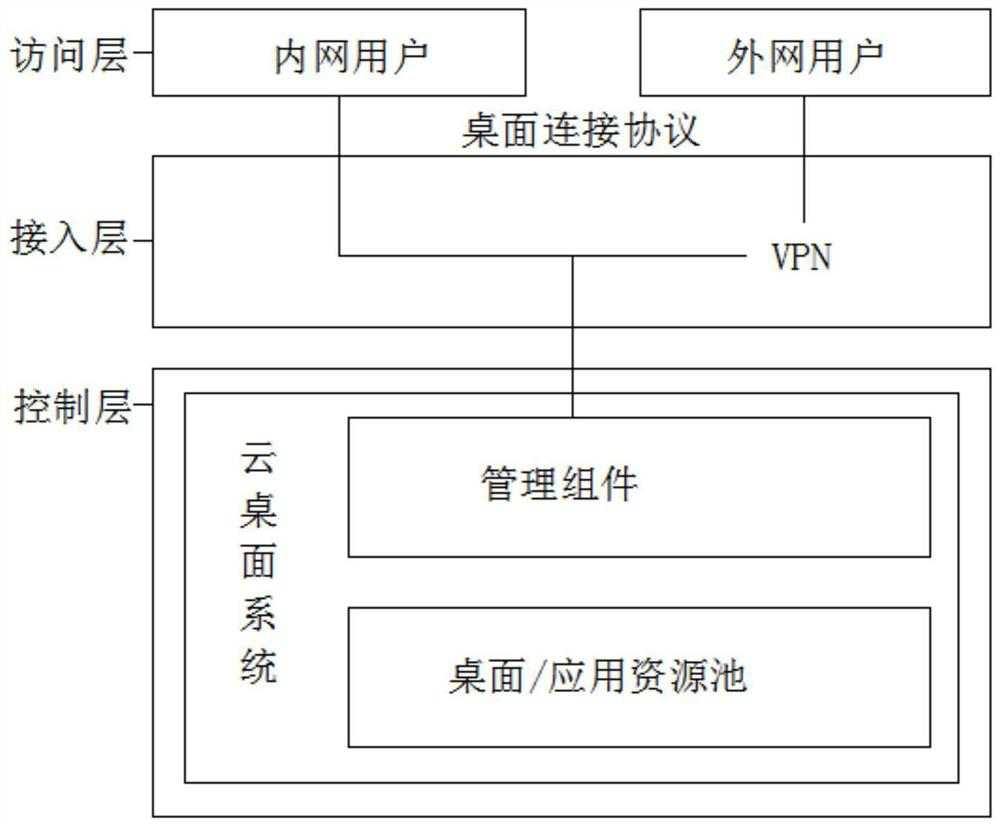
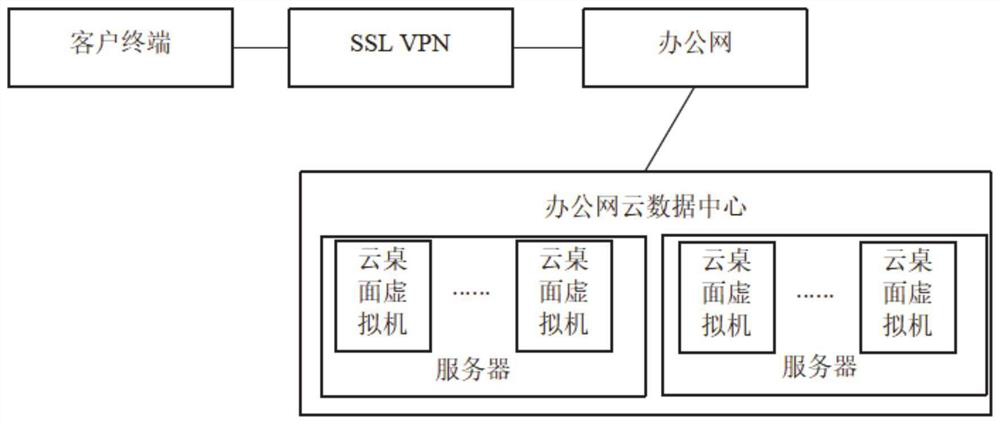
Remote office implementation system and method based on cloud desktop
PendingCN114244651ARealization of telecommutingImprove securityNetworks interconnectionSoftware simulation/interpretation/emulationPrivate networkBusiness enterprise
The invention discloses a remote office implementation system and method based on a cloud desktop. The system comprises a client terminal and an office network cloud data center, the client terminal is connected to an office network through a VPN (Virtual Private Network), a plurality of servers are deployed in a cloud data center of the office network, each server is accessed to the office network, a plurality of desktop virtual machines are virtualized on each server, cloud desktop connection software is arranged on the client terminal, and the cloud desktop connection software is connected with the office network. And the client terminal transmits a desktop image through the cloud desktop connection software and maps local equipment on the client terminal to the cloud desktop virtual machine. According to the method, the cloud desktop virtual machine and the office network cloud data center are used, the problem that traditional data office is not safe is solved, data cannot fall to the ground and are all in an enterprise in the mode, the safety and experience effect of the data are improved, and the application safety audit fine degree of the network is improved.
Owner:浪潮数字(山东)科技有限公司
Blasting fuse of high-safety firecracker and preparation method thereof
InactiveCN101270015BStable chemical propertiesLow mechanical sensitivityInorganic oxygen-halogen salt explosive compositionsFuse detonationYarnDecomposition
Owner:醴陵神马花炮有限公司
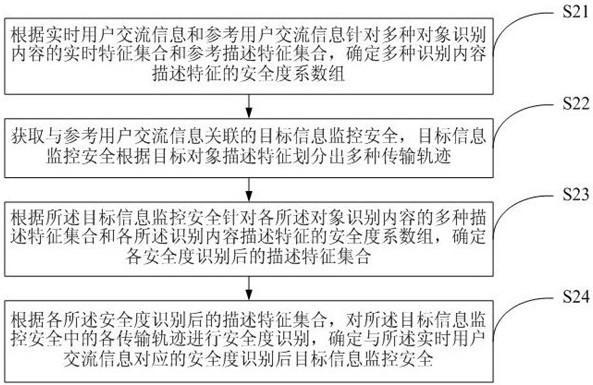
Big data-based information security monitoring method and system and cloud platform
InactiveCN113360729ASolve insecurityDigital data protectionOther databases queryingInformation transmissionRelevant information
Disclosed are a big data-based information security monitoring method and system and a cloud platform. The method comprises the steps of determining a security coefficient group of various identification content description features for a real-time feature set and a reference description feature set of various object identification contents through real-time user communication information and reference user communication information, acquiring target information monitoring security associated with exchange information of a reference user, determining description feature sets after security identification according to various description feature sets of target information monitoring security for the object identification contents and the security coefficient group of the description features of the identification contents, and according to the description feature sets after security identification, performing safety degree identification on each transmission track in the target information monitoring security, and determining the target information monitoring security after the security degree identification, thereby solving the problem that related information is not secure in information transmission of the target information.
Owner:广州云博互联网技术有限公司
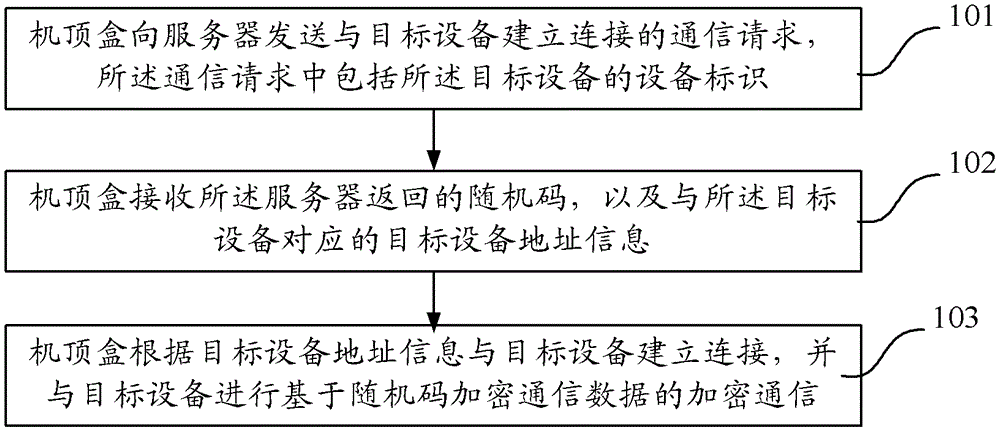
Set-top box communication method, device and system
ActiveCN103024599BSolve insecurityGuaranteed legalitySelective content distributionCommunications securityCommunications system
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
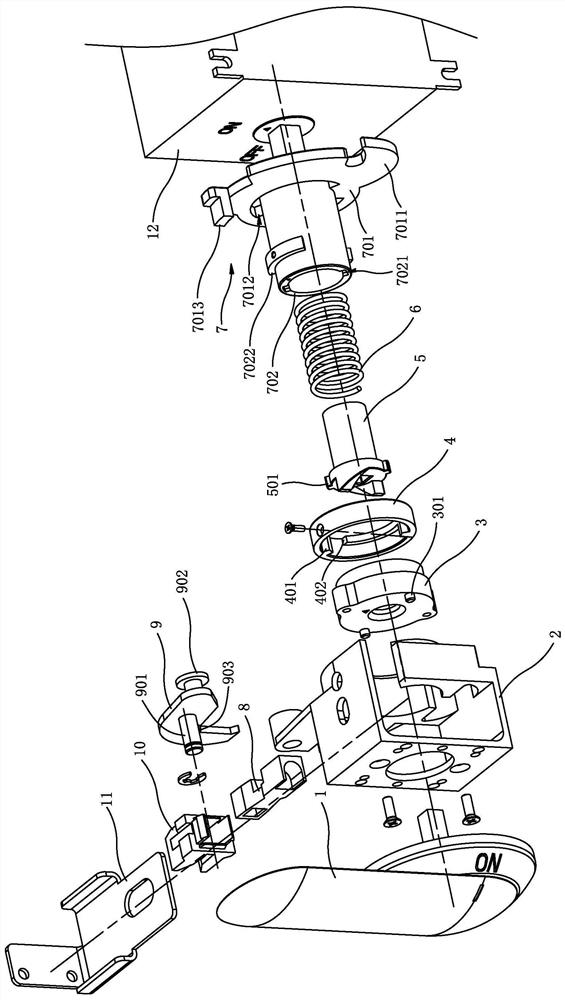
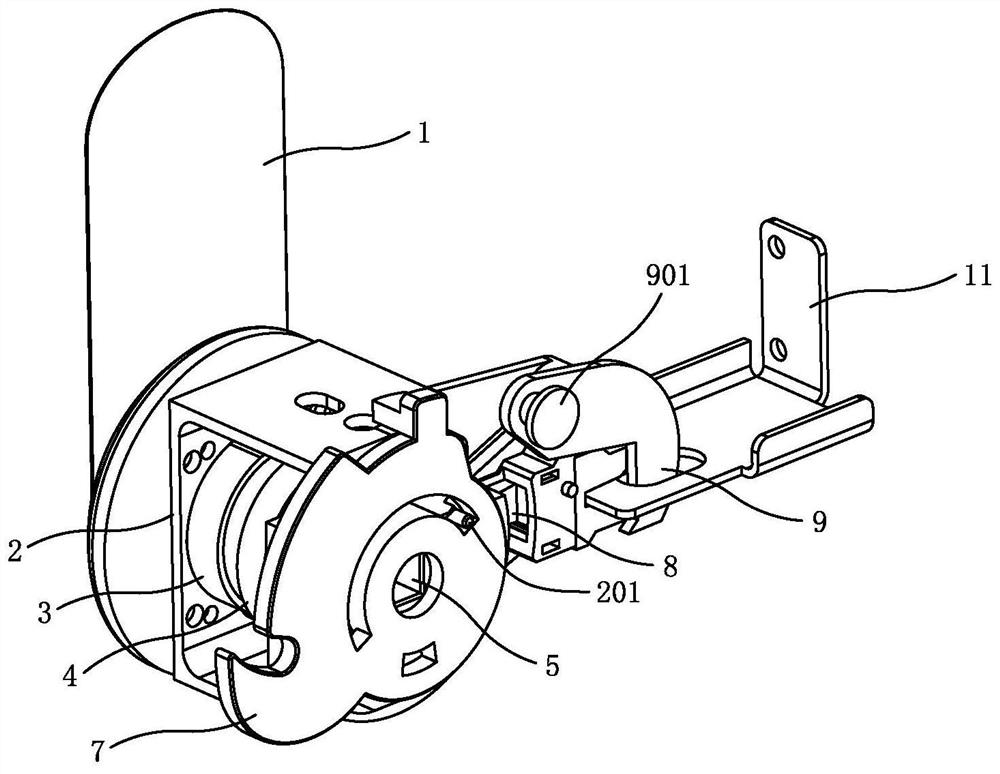
Telescopic rotary unlocking device of power distribution cabinet
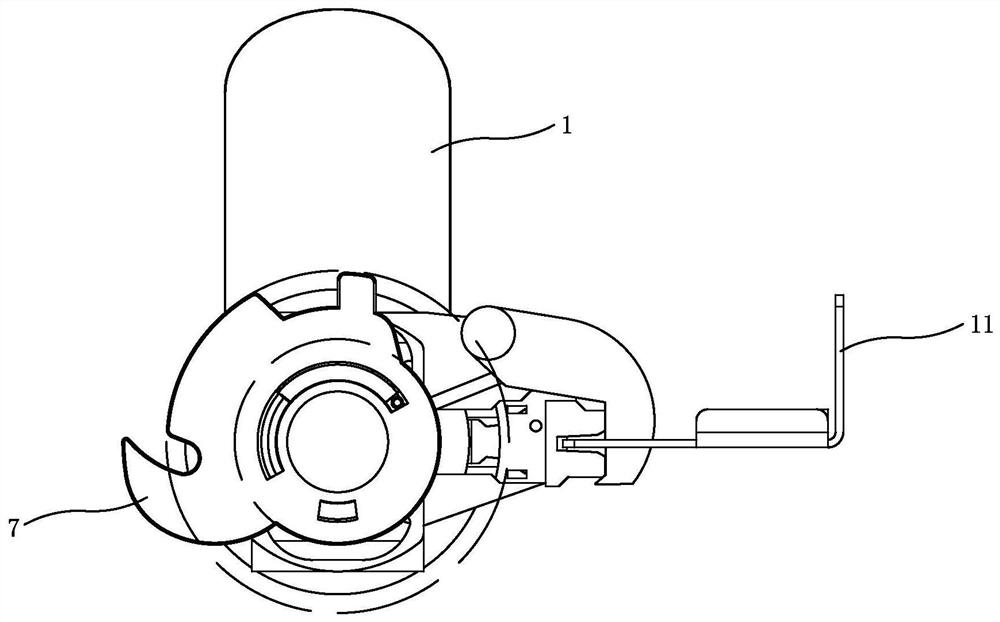
ActiveCN112696098ASolve insecurityReasonable structural designSwitchgear arrangementsWing handlesEngineeringCam
The invention relates to a telescopic rotary unlocking device of a power distribution cabinet, which is designed for solving the technical problems of poor cam structure stability and reset effect, inconvenience in production and assembly and poor universality of the existing similar products. The unlocking device comprises a transmission mechanism and an unlocking mechanism. The unlocking device is characterized in that a cam of the transmission mechanism is fixed in a fixing seat; a cylindrical section of a rotating shaft is sleeved with a sleeve of a shifting piece; meanwhile, a spring is arranged on the outer diameter of the cylindrical section of the rotating shaft in the sleeve; a protruding sickle head is arranged on one side of the outer diameter of a rotating disc of the shifting piece; a tilted introducing port is formed in one side of the end portion of the sickle head; one end of a connecting piece of the unlocking mechanism is fixed in a square groove in one side of a fixing seat; a spring bolt is arranged on one side of an opening of a lock nozzle in the square groove; a hook hole is formed in the spring bolt at the lock nozzle; a hook is arranged on the fixing seat above the hook hole; the hook is bent in an L shape; the bent position of the hook is fixed to the fixing seat through a clamp spring on a third small cylinder to swing; a hook head at one end of the hook is inserted into the hook hole of the spring bolt; and the hook head of the hook is inserted into the hook hole of the spring bolt.
Owner:宁波生久科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com