Network invasion preventing safe data transmission system and network invasion preventing safe data transmission method
A data transmission and data security technology, which is applied in the field of data security transmission system, can solve the problem that the data speed cannot be accelerated, and achieve the effect of fast speed, improved speed and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
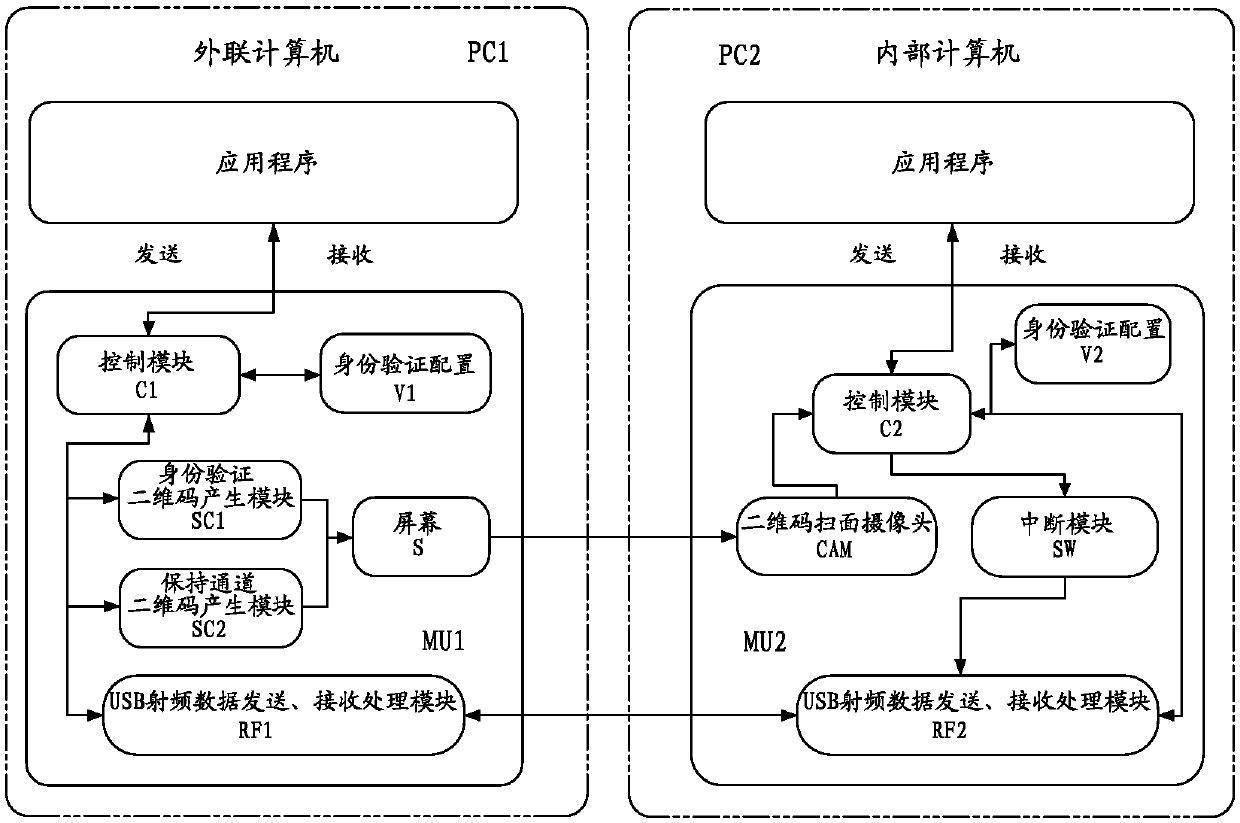
[0026] Such as figure 1 As shown, a data security transmission system for preventing network intrusion in the present invention includes a first data transmission receiving module MU1 set on an external network computer and a second data transmission receiving module MU2 set on an intranet computer; wherein, the first The data transmission receiving module MU1 includes a first control module C1, two-dimensional code generation modules SC1, SC2, a display screen S and a first radio frequency communication module RF1; the second data transmission receiving module MU2 includes a second control module C2, facing the display screen The QR code scanning camera CAM, interrupt module SW and second radio frequency communication module RF2 set by S;
[0027] The first control module C1 performs data interaction with the application program of the external network computer, including accepting user instructions to start the data transmission process, controlling the two-dimensional code ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com