Anti-injection method for browser, browser client and device
A browser client, browser technology, applied in secure communication devices, digital transmission systems, electrical components, etc., can solve problems such as inability to change, browser insecurity, and insecurity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
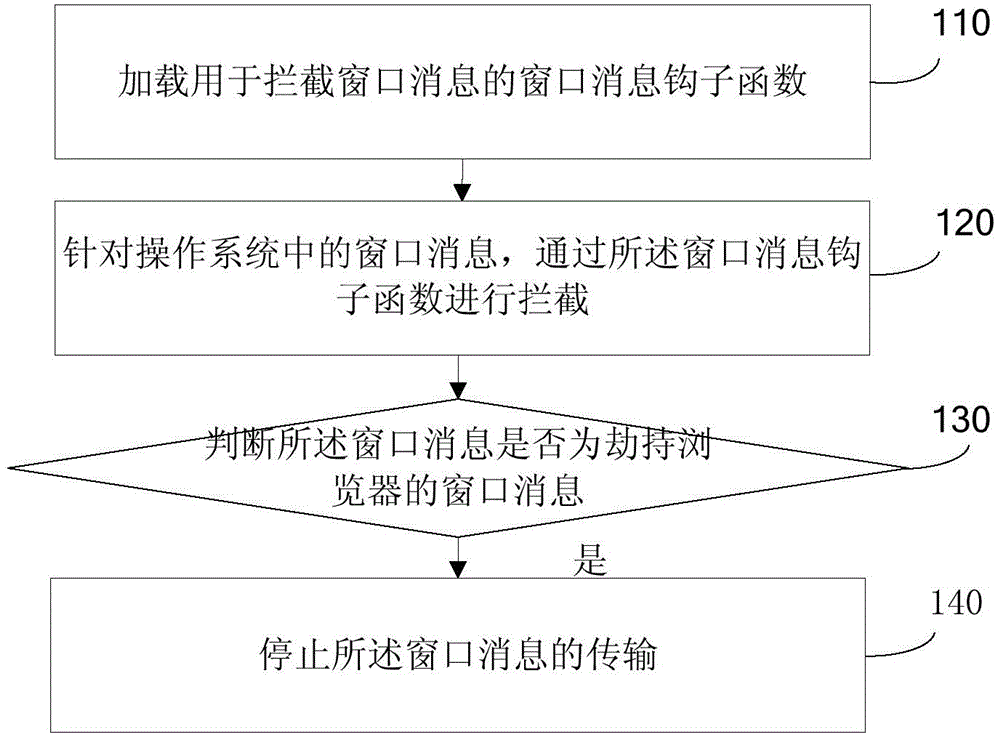
[0125] refer to figure 1 , which shows a schematic flowchart of a method for preventing injection of a browser according to the present invention, which may specifically include:
[0126] Step 110, loading a window message hook function for intercepting window messages;
[0127] In the embodiment of the present invention, the CBT hook function WH_CBT is loaded, and the window messages of the WH_CBT hook function can be intercepted through the WH_CBT when the windows window is activated, created, released (closed), minimized, maximized or changed. The present invention can load the above-mentioned CBT hook function.
[0128] Preferably, the loading of the window message hook function for intercepting window messages includes:
[0129] Sub-step 112, calling the dynamic link library loading function to load the dynamic link library where the window message hook function is located, so as to load the window message hook function.
[0130] WH_CBT needs to be installed through th...
Embodiment 2
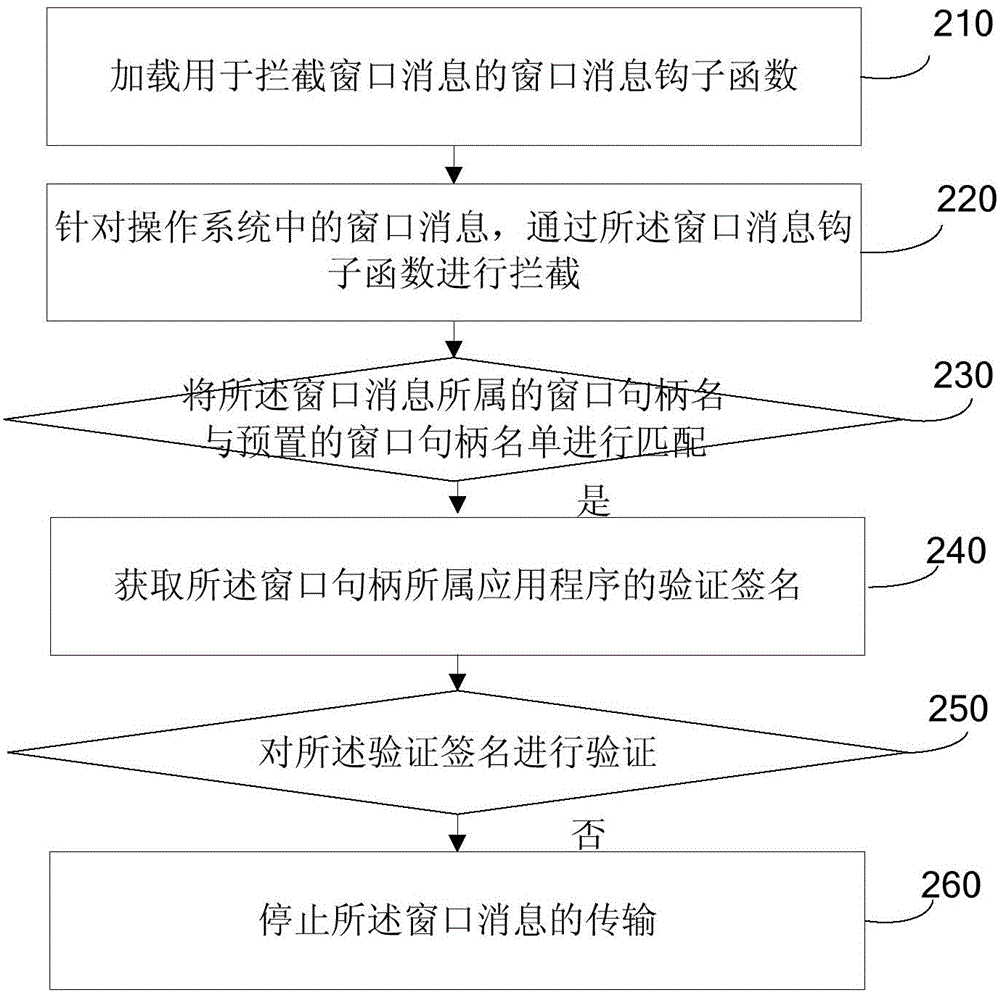
[0158] refer to figure 2 , which shows a schematic flowchart of a method for preventing injection of a browser according to the present invention, which may specifically include:
[0159] Step 210, loading a window message hook function for intercepting window messages;
[0160] Step 220, intercepting the window message in the operating system through the window message hook function;
[0161] Step 230, match the window handle name to which the window message belongs with a preset window handle list; if the window handle matches, then enter step 240;
[0162] If the window handle does not match, the window message is released.
[0163] Step 240, obtaining the verification signature of the application to which the window handle belongs;
[0164] Step 250, verify the verification signature; if the verification fails, determine that the window message is a browser hijacking window message, and enter step 260;
[0165] If the verification is successful, the window message is ...
Embodiment 3
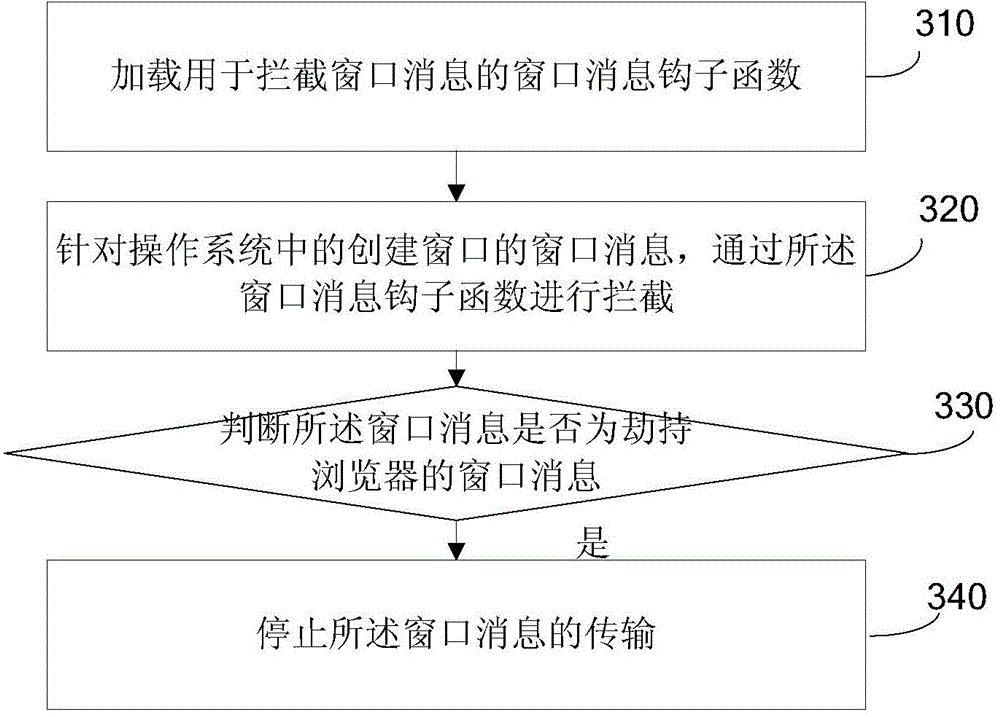
[0171] refer to image 3 , which shows a schematic flowchart of a method for preventing injection of a browser according to the present invention, which may specifically include:
[0172] Step 310, loading a window message hook function for intercepting window messages;
[0173] Step 320, for the window message of the created window in the operating system, intercepted by the window message hook function;
[0174] In the embodiment of the present invention, it can be understood that when an application program wants to inject a dll into a browser, it needs to perform an installation process, and the installation process needs to create a window for installation first in the Windows system. In the embodiment of the present invention, only To intercept the window message of the created window, the embodiment of the present invention can only intercept the window message of the created window, and can determine whether it is the window message of the application program that inj...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com