Grouped multiple-key encryption method and grouped multiple-key encryption device
An encryption method and technology of an encryption device, applied in the field of data encryption and decryption, can solve problems such as affecting data security, encrypted data being decrypted, etc., and achieve the effects of reducing losses, facilitating recovery, and solving security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
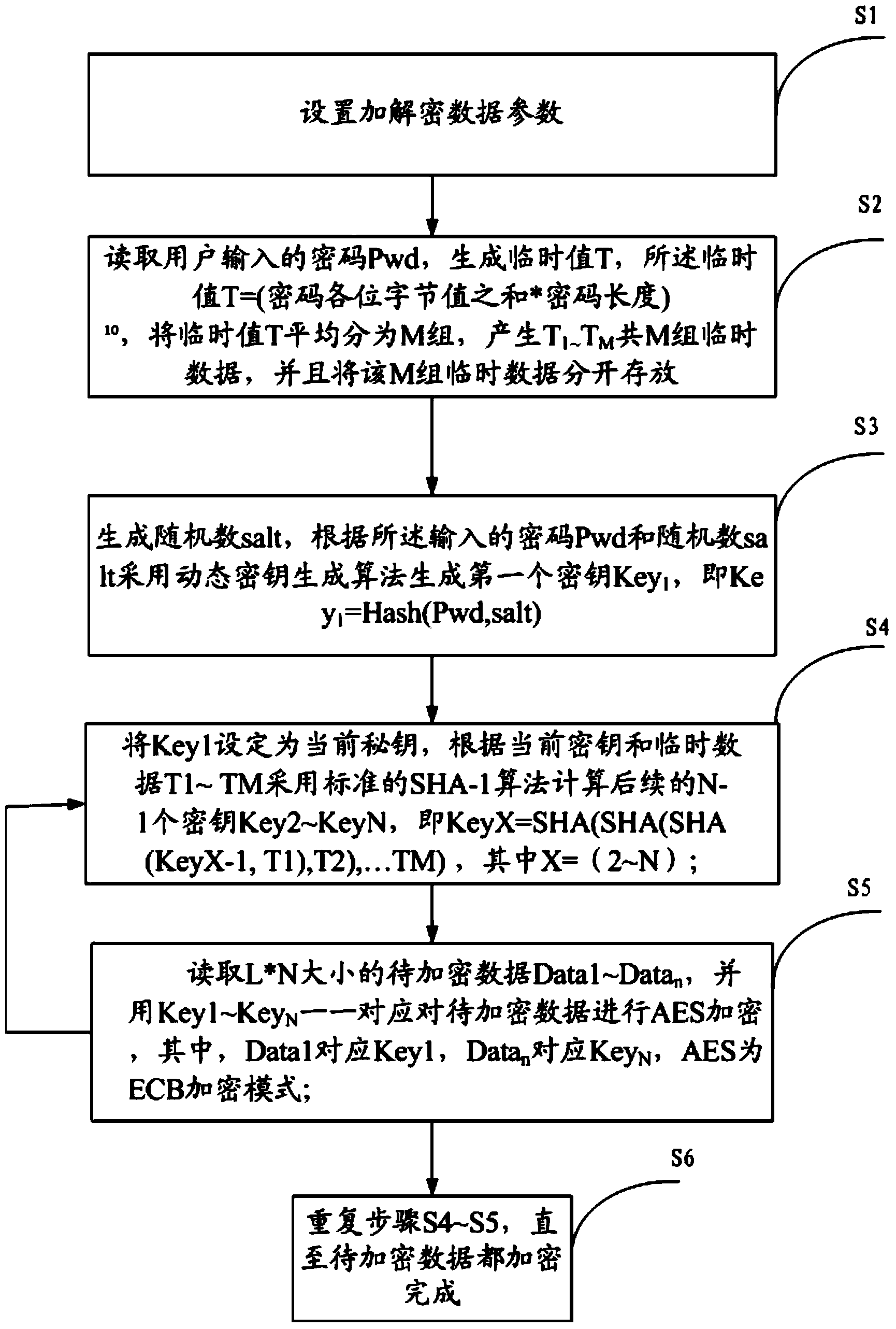
[0020] like figure 1 Shown is the flow chart that the present invention implements grouping multi-key encryption method, and this grouping multi-key algorithm comprises steps:
[0021] S1. Set encryption and decryption data parameters: encryption and decryption data block size L: indicates the length of data encrypted and decrypted by a key; number of packets N: indicates the number of packets processed in parallel for one encryption and decryption; number of hash algorithm cycles M: indicates calculation The cycle calculation rounds of the hash algorithm used for the key;
[0022] S2. Read the password Pwd entered by the user and generate a temporary value T according to the password and the calculation formula of the temporary value, and then divide the temporary value T into M groups on average to generate M groups of temporary data from T1 to TM, and store the M groups of temporary data separately , the formula for calculating the temporary value is: T=(the sum of each by...
Embodiment 2
[0037] This embodiment provides a group multi-key encryption device, which includes:
[0038] Encryption and decryption parameter setting module: used to set the encryption and decryption data block size L, the number of packets N, and the number of cycles of the hash algorithm M, where the encryption and decryption data block size L: indicates the length of data encrypted and decrypted by a key; the number of packets N : Indicates the number of packets processed in parallel for one encryption and decryption; Hash algorithm cycle times M: Indicates the hash algorithm cycle calculation rounds used when calculating the key; Temporary data T1~TM generation module: used to read the password input by the user Pwd, generate a temporary value T, the temporary value T=(the sum of each byte value of the password*password length)10, divide the temporary value T into M groups on average (same as the number of cycles of the algorithm), and generate a total of M from T1 to TM group of temp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com