Method for logging in online game through mobile equipment
A mobile device and online game technology, applied in the field of online game login, can solve problems such as difficult to guarantee theft, and achieve the effect of solving the problem of account theft and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
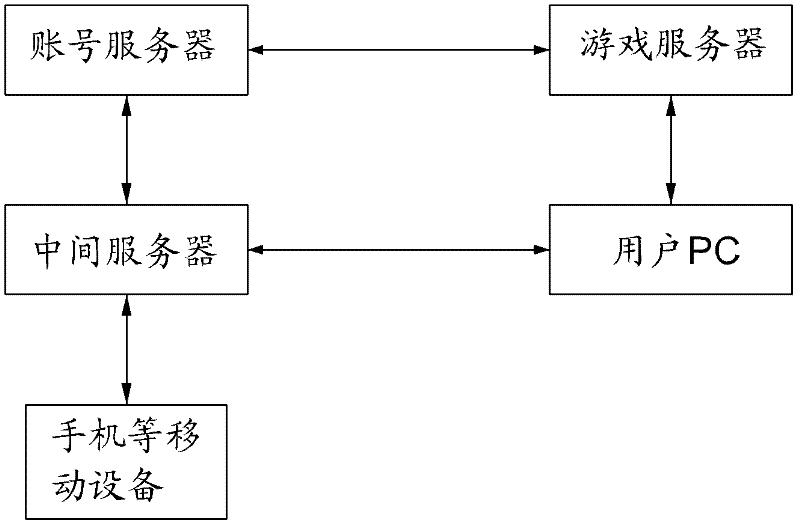
[0022] The present invention is a method for logging in online games through mobile devices, such as figure 1 , the present invention includes a mobile device, an intermediate server, an account server, a user PC, and a game server.
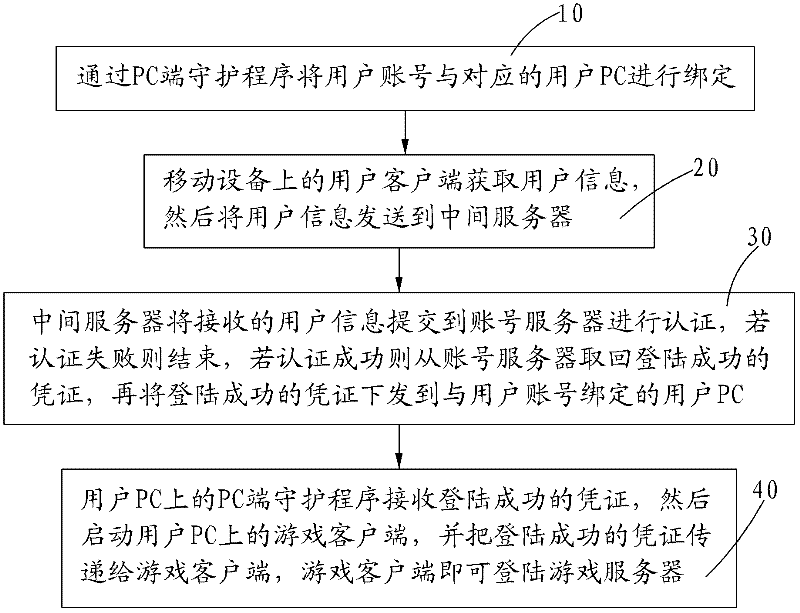
[0023] combine figure 2 , which includes the following specific steps:
[0024] Step 10, install the user client on the mobile device, the mobile device can be a mobile phone, etc., install the PC-side daemon program on the user PC, and bind the user account with the corresponding user PC through the PC-side daemon program;
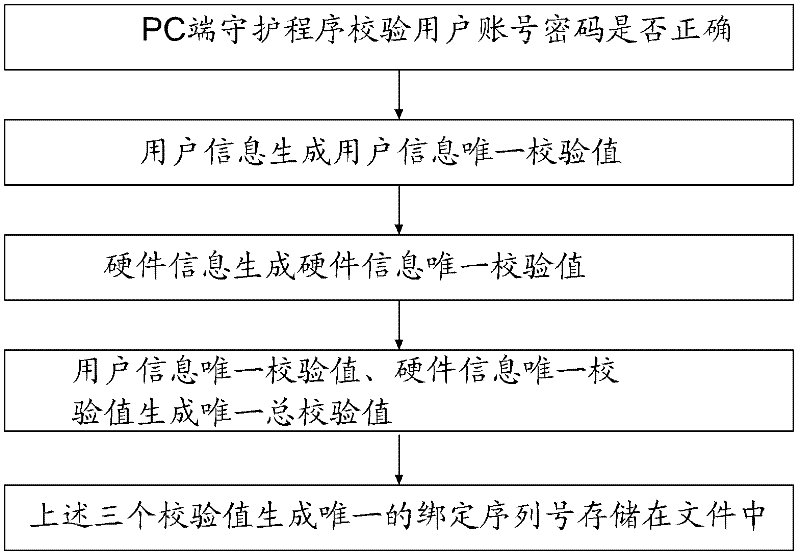
[0025] Such as image 3 , the PC-side daemon program is bound like this: the user inputs user information (such as user account number, password, and game item selection), and after the PC-side daemon program confirms that the user account number and password are correct, the PC-side daemon program generates The unique check value of the user information, the hardware information on the user PC generates the unique check...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com