Profile switching method, signal intensity detection method and equipment
A technology of signal detection and user equipment, applied in the field of communication, can solve the problem of unreasonable and effective profile switching
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
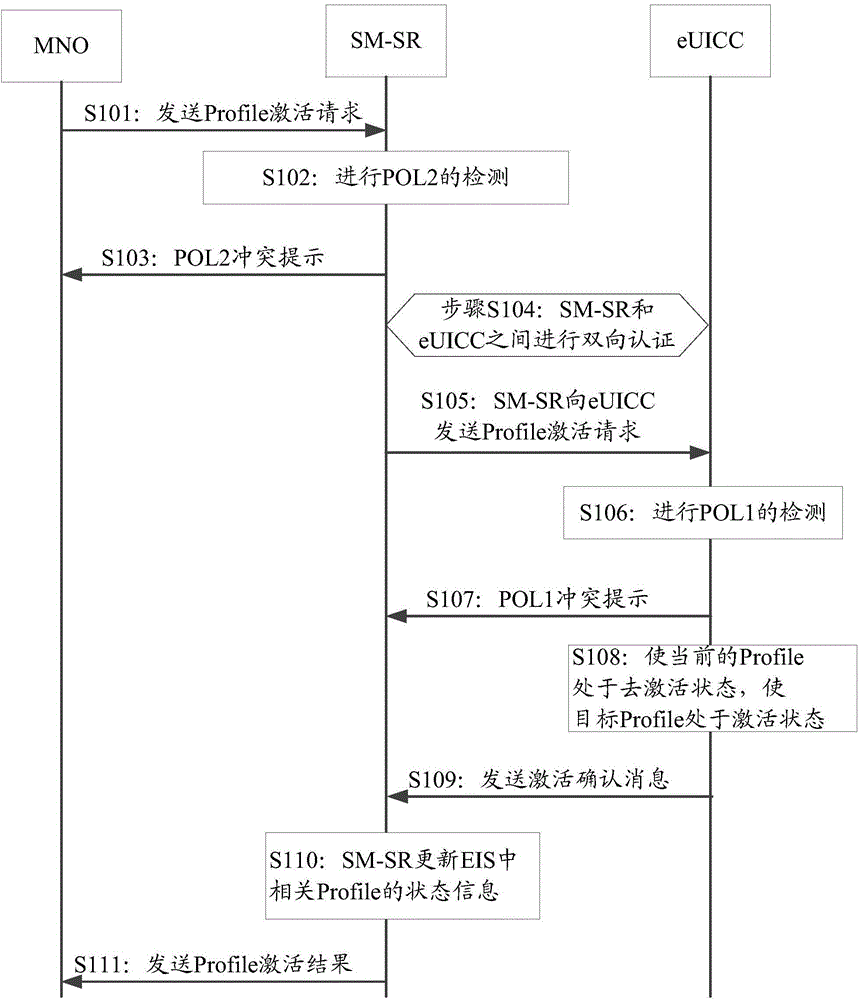
[0237] In this embodiment, the Profile switching method and the signal detection method in the embodiment of the present invention are introduced with the Profile switching process initiated by the MNO, please refer to Figure 12 , including the following steps:
[0238] Step S1201: The MNO sends a Profile activation request to the SM-SR, wherein the MNO can directly send a Profile activation request to the SM-SR, or send a Profile activation request to the SM-SR through the SM-DP, and the Profile activation request carries EID, target Profile ICCID and profile switching policy.
[0239] Step S1202: According to the EID and ICCID, the SM-SR performs POL2 policy detection on the currently activated Profile and the to-be-activated Profile on the target eUICC. POL2 is also POLicy2, which means the policy on the SM-SR.
[0240] The policy detection content of POL2 includes one or more of the following detection content:
[0241] 1) disabled not allowed (deactivation is not allow...
Embodiment 2
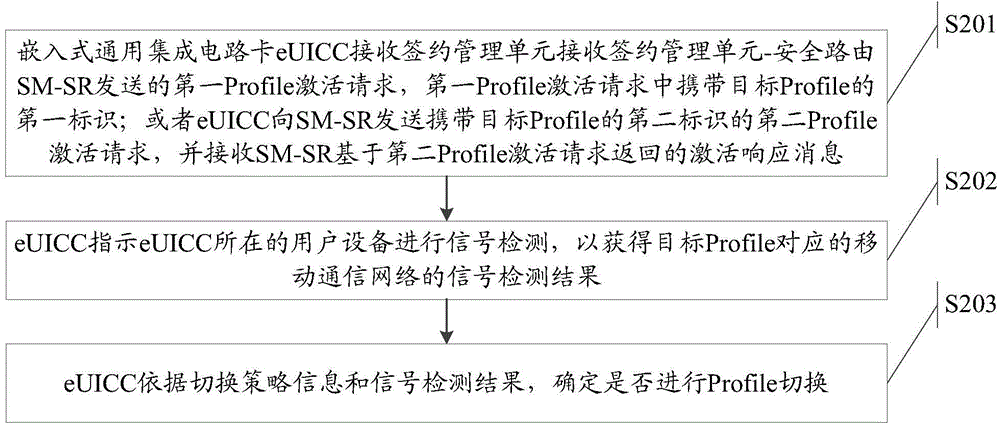
[0279] In this embodiment, the Profile switching process initiated by the eUICC is taken as an example to introduce the Profile switching method and signal detection method in the embodiment of the present invention. Please refer to Figure 13 , including the following steps:
[0280] Step S1300: Profile switching on the eUICC is triggered, including but not limited to the following situations: 1) The user initiates a Profile switching request through the user equipment; 2) The trigger conditions set on the eUICC (can be based on time, location, etc.) are satisfied; 3) Other situations ;
[0281] Step S1301: The eUICC performs POL1 policy detection on the currently activated Profile and the target Profile to be activated;
[0282] Step S1302a: If the POL1 policy detection in step S1302 passes, use PKI certificate or symmetric key for mutual authentication between eUICC and SM-SR;
[0283] Step S1302b: Negotiation between eUICC and SM-SR generates two sets of keys, namely: ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com