Mobile phone access control system based on encrypted two-dimensional code
An access control system and two-dimensional code technology, which can be applied to instruments, time registers, and individual input/output registers, etc., which can solve the problems of inconvenient management, poor security, and high cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
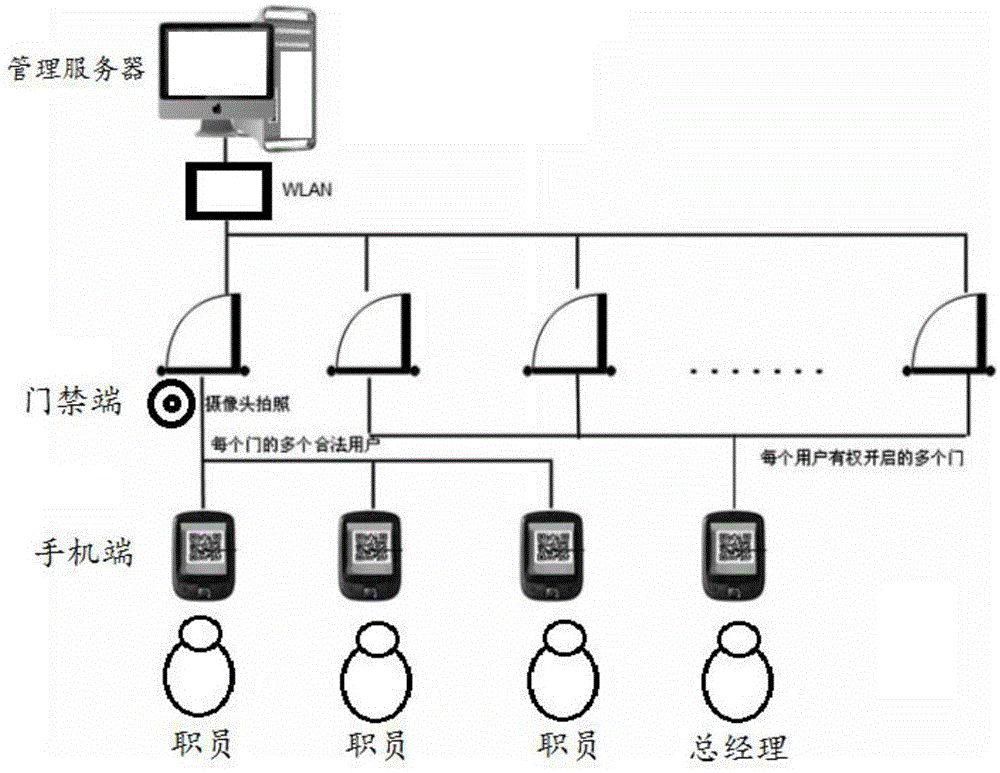
[0075] see figure 1 , the present invention discloses a mobile phone access control system based on an encrypted two-dimensional code, the system mainly consists of three parts: a mobile phone terminal, an access control terminal and a management server;
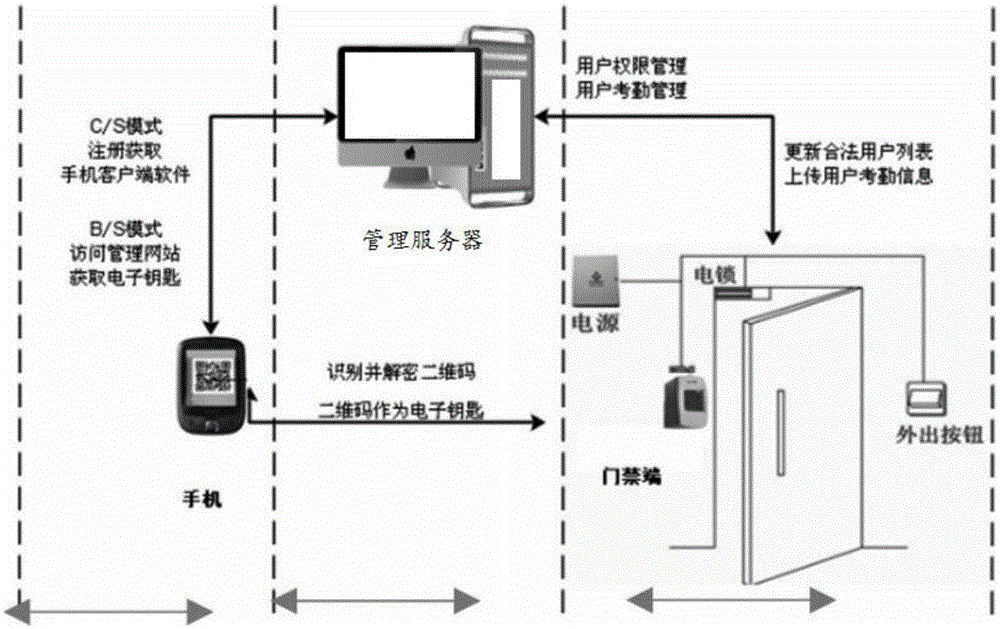
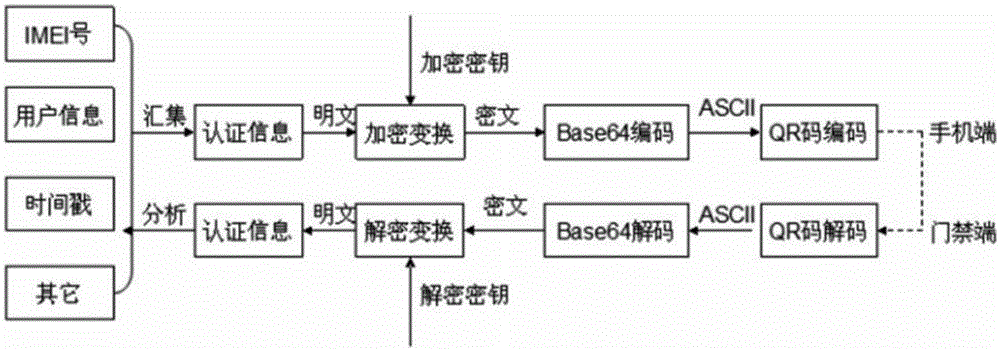
[0076] In this system, the soft key carrying identity information is generated by the software on the mobile phone in the form of a two-dimensional code, and has a time limit and a limit on the number of times. When in use, the mobile client software first generates a soft key and displays it on the screen of the mobile phone. The access control terminal software drives the camera to obtain the image of the soft key on the mobile phone screen and decrypts and verifies the soft key through the identity verification module integrated in the access control terminal. The rear drive electric control switch opens the door lock.
[0077] The whole system is mainly composed of three parts: mobile terminal, access control terminal a...
Embodiment 2
[0106] A mobile phone access control system based on an encrypted two-dimensional code, the system includes: a mobile phone terminal, an access control terminal and a management server; the mobile terminal generates a soft key and displays it on the mobile phone screen, and the access control terminal drives a camera to obtain the soft key on the mobile phone screen image, and decrypt and verify the soft key through the identity verification module integrated in the access control terminal, and drive the electric control switch to open the door lock after passing the identity verification.
[0107] Described mobile terminal mainly comprises a software, is responsible for generating or obtains the soft key image that comprises encrypted two-dimensional code image from server; soft key image and decide whether to open the door lock according to the verification result; the management server is responsible for key issuance and authority management, and realizes the distributed man...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com