Method and system for malware network behavior detection based on access router
A malicious software and router technology, applied in transmission systems, electrical components, etc., can solve problems at the technical level, achieve the effect of enhancing detection capabilities and solving deployment difficulties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] The present invention is described in detail below in conjunction with accompanying drawing:
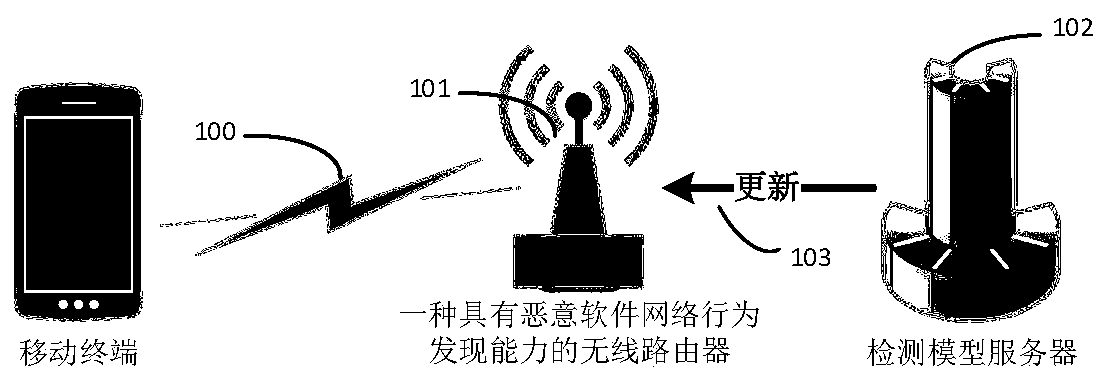
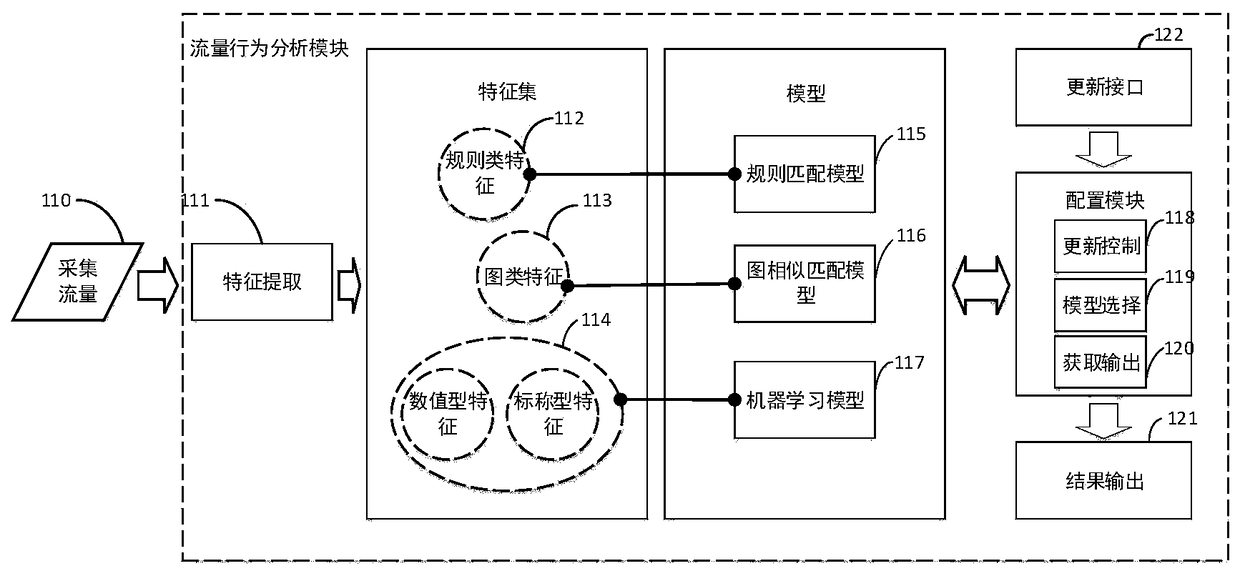
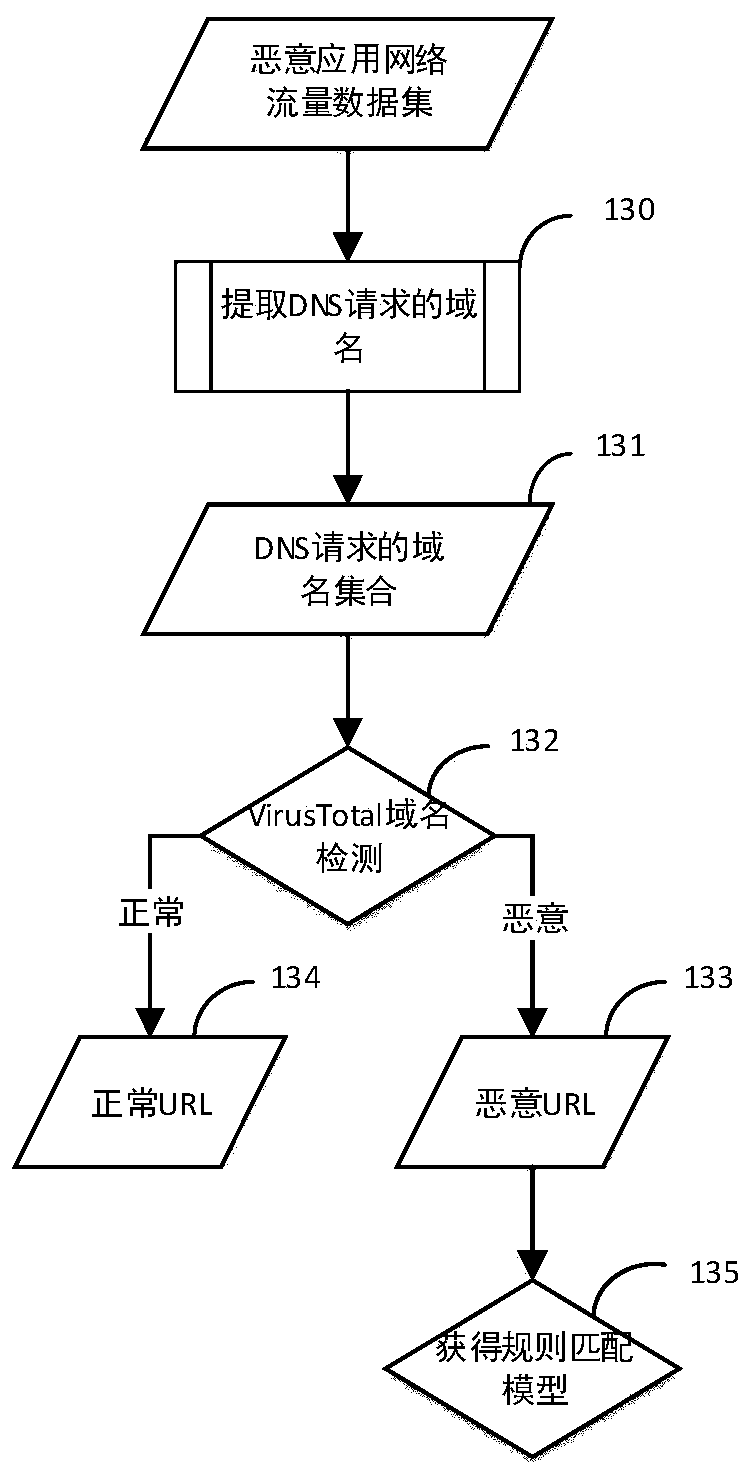
[0070] Based on the existing wireless router with malware network behavior discovery capability, the present invention deploys the novel router in a local area network environment, and realizes detection of malware by using network flow of a mobile terminal. First, the user connects wirelessly to a wireless router with malware network behavior detection capabilities, and passes the security verification; second, when the user's mobile terminal accesses the external network through the router, the tcpdump tool installed in the router system collects The interactive traffic between the user's mobile terminal device and the external network; then, the router's behavior analysis module reads and analyzes the collected network traffic. If malicious traffic is detected and analyzed, it means that malicious applications are installed on the user's mobile terminal device , feedback th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com