Memory leak detection device and method and terminal
A technology of memory leak and detection device
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
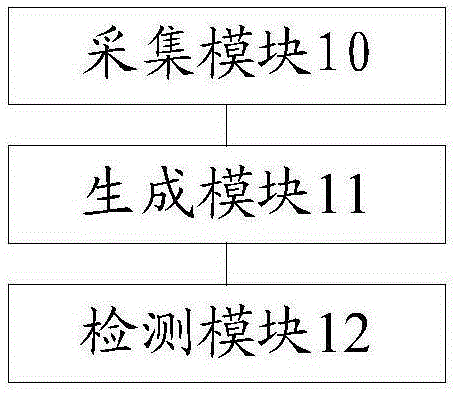
[0096] Based on the first embodiment of the above-mentioned memory leak detection device, the device also includes: an acquisition module 13, which is used to acquire a test script, and the test script is a shell script;
[0097] The collection module 10 is also used to run a shell script to collect memory sampling information of the process under test.
[0098] The acquisition module 13 can be directly read from the memory of the terminal where the process under test is located, and can also obtain the test script through other terminals that are wired or wirelessly connected to the terminal where the process under test is located. In one embodiment, If the terminal where the tested process is located is an Android mobile phone, the terminal connected to the Android mobile phone is a tablet computer, and a test script for memory leak detection is stored on the tablet computer, and the acquisition module 13 obtains the test script from the tablet computer , and save the test s...
no. 2 example
[0135] Based on the first embodiment or the second embodiment of the above memory leak detection method, the method further includes:
[0136] S14. When the process under test has a memory leak, locate the object or code segment where the process under test has a memory leak according to the change trend of the memory usage value of the process under test.
[0137] When there is a memory leak in the process under test, it may only be caused by a certain part of the code segment or object of the process under test that causes the memory leak during runtime. In this step, locate the Objects or code segments that have memory leaks in the measured process, for example, find the time point when the memory usage value is increasing from the change trend of the memory usage value of the measured process, and then find that at this time point, the user performed some What operation, and then find the corresponding object or code segment, that is, find the object or code segment that h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com