Automatic detection method for malicious software
A technology for automatic detection and malware, applied in the fields of instruments, digital data processing, platform integrity maintenance, etc., can solve problems such as threats to user privacy and information security, and achieve the effect of protecting privacy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] Below in conjunction with accompanying drawing and specific embodiment, the present invention will be further described:
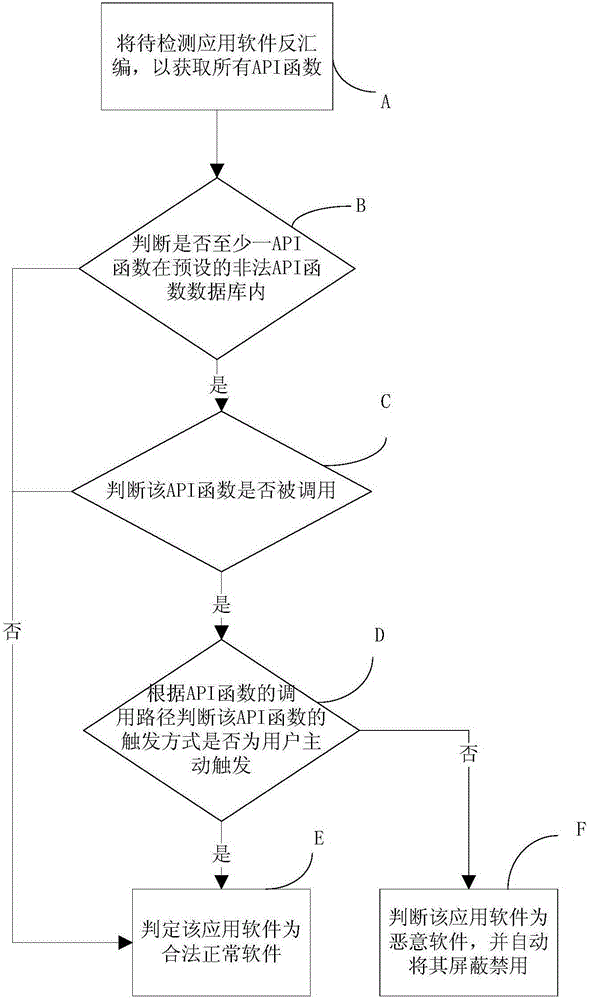
[0016] See figure 1 , the present invention relates to a kind of malware automatic detection method, and its preferred embodiment comprises the following steps:
[0017] Step A: Disassemble the application software to be detected to obtain all API (Application Programming Interface, Application Programming Interface) functions;
[0018] Step B: judging whether at least one API function is in the preset illegal API function database, if yes, execute step C; if not, execute step E;
[0019] Step C: Determine whether the API function is called, if so, execute step D; if not, execute step E;
[0020] Step D: According to the call path of the API function, it is judged whether the trigger mode of the API function is triggered by the user, if so, execute step E; if not, execute step F;
[0021] Step E: determine that the application software is legal a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com