Method and device for account risk assessment
A risk assessment and account technology, applied in the field of computer systems, can solve problems such as reducing the security of computer systems, and achieve the effect of improving the security of use and facilitating management and monitoring.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
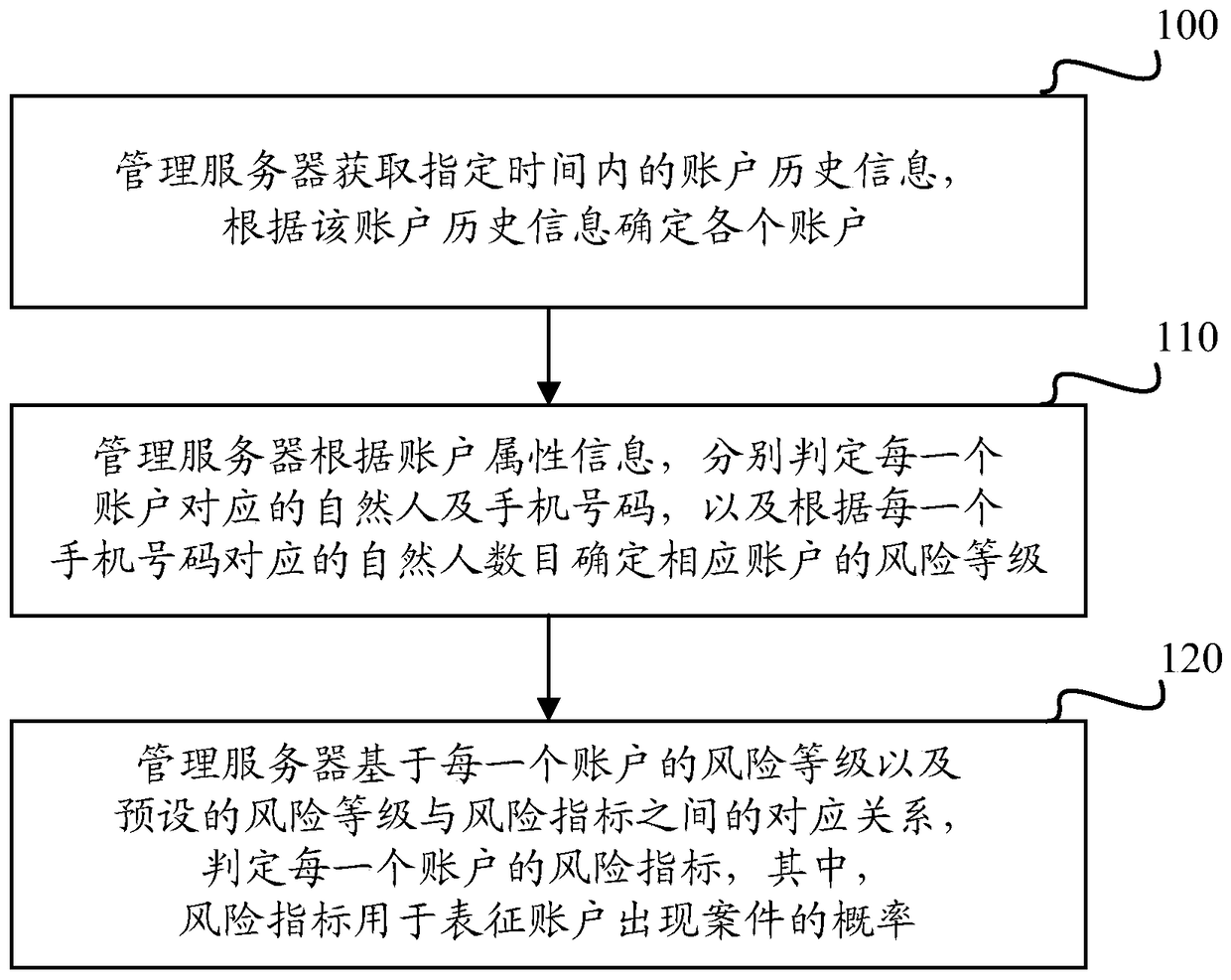
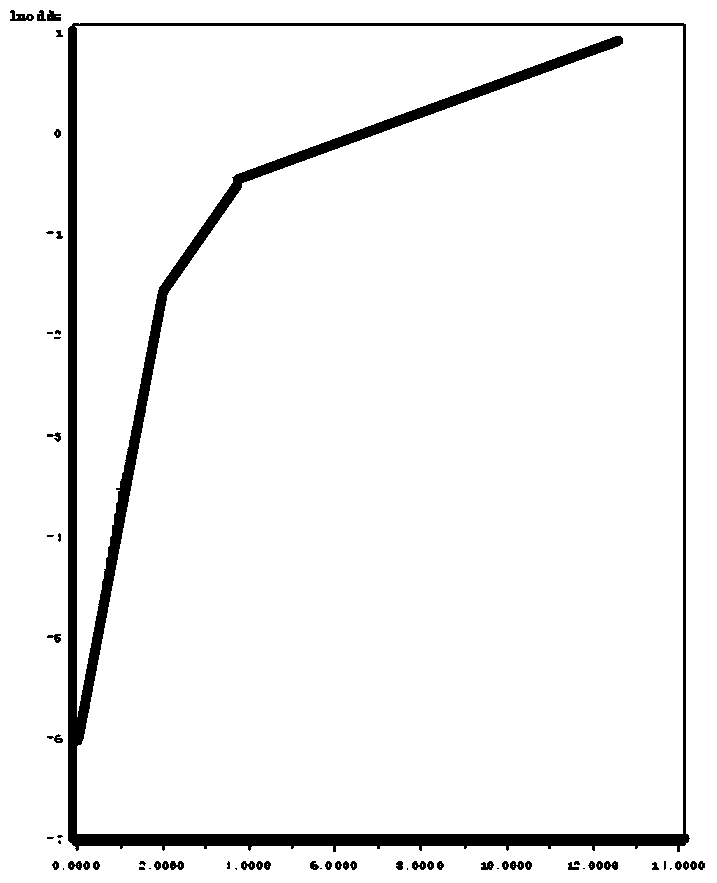
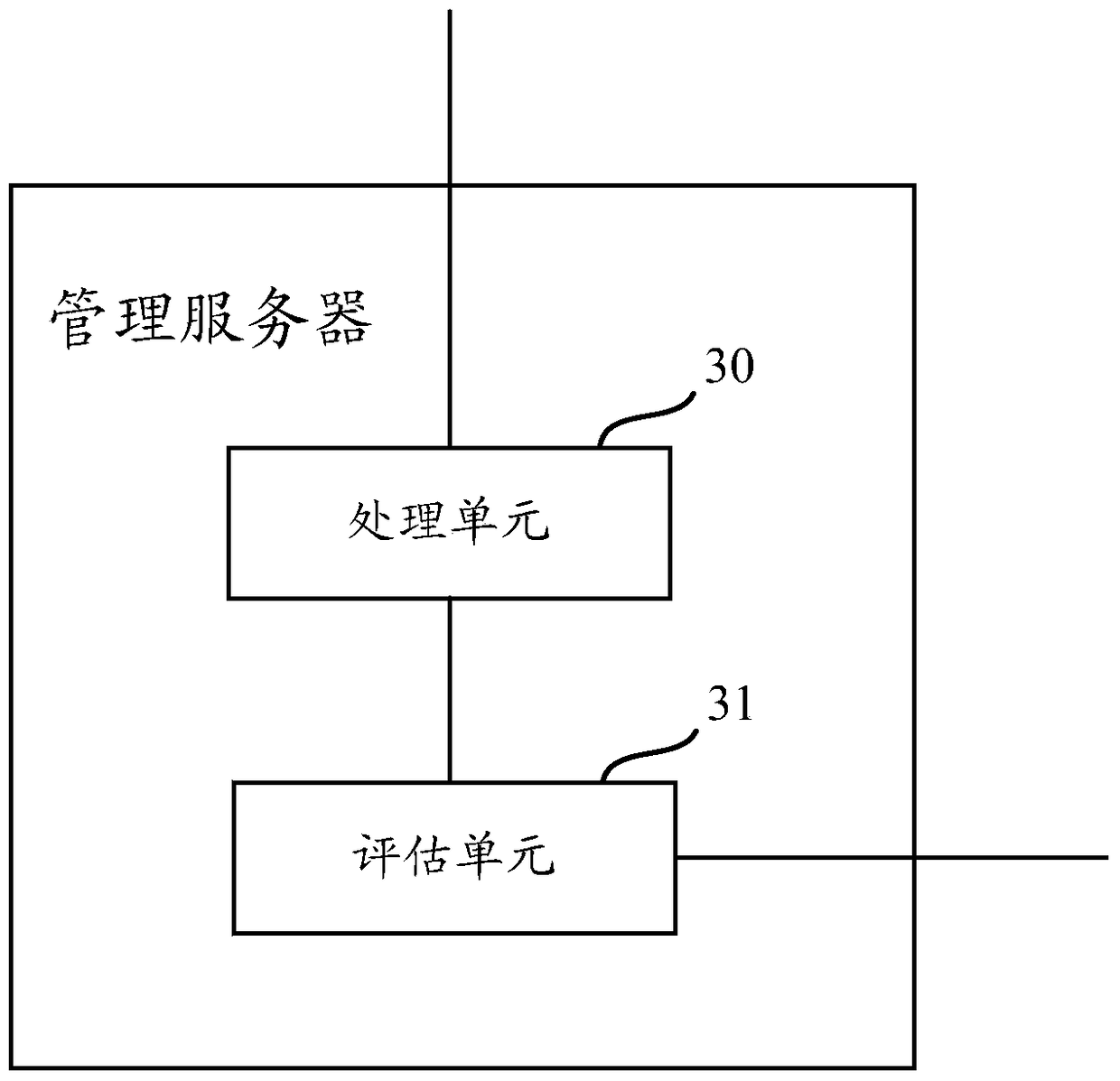
[0041] In order to effectively identify illegal accounts and improve system security, in the embodiment of this application, the risk index of the account is evaluated based on the number of natural persons corresponding to the mobile phone number bound to the account, so as to accurately screen out abnormal accounts that pose a threat to system security .
[0042] Preferred implementations of the present application will be described in detail below in conjunction with the accompanying drawings.
[0043] In practical applications, many hacking gangs in e-commerce systems will sell stolen goods by setting up multiple seller accounts, and in order to facilitate management and control, hacking gangs usually bind these multiple seller accounts to the same or fix several mobile phones Number. Through the sampling and analysis of massive data, an obvious rule was discovered: the number of different natural persons bound to a mobile phone number can be used as the basis for determi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com