Abnormal traffic detection method
A technology of abnormal traffic and detection methods, applied in the field of computer systems, can solve the problems of network paralysis, inability to detect attacks, and missed judgments, and achieve the effect of reducing the false positive rate and the false negative rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
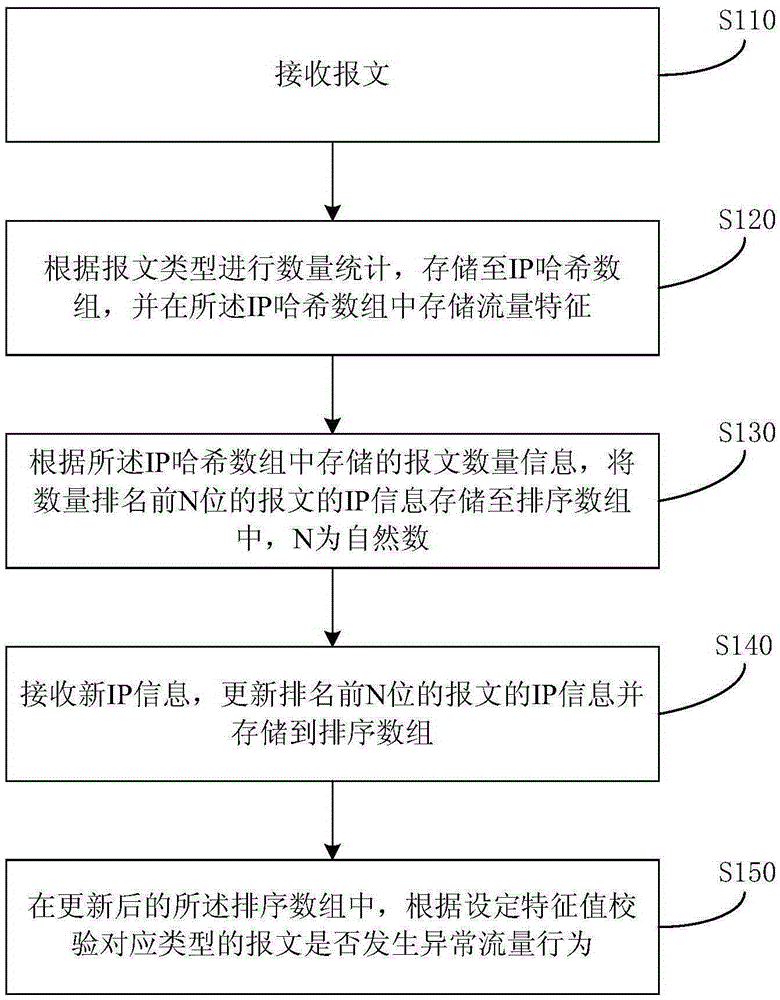
[0022] figure 1 It is a flowchart of a method for detecting abnormal traffic in Embodiment 1 of the present invention. This embodiment provides a method for detecting abnormal traffic. The method can be executed by any device that performs traffic detection. The device can use software and / or hardware implementation. Such as figure 1 As shown, the method includes:
[0023] S110. Receive a message;
[0024] S120. Perform quantity statistics according to the message type, store in the IP hash array, and store traffic characteristics in the IP hash array;
[0025] Exemplarily, a global IP hash array (HASH) is established to count information such as IP traffic, and the IP hash array may contain different variables to count information such as IP traffic. Preferably, the IP hash array can count the message information contained in the IP traffic, for example: the IP hash array can include variables SYN, ICMP and UDP, which are used to count synchronous messages (syn messages) ...
Embodiment 2
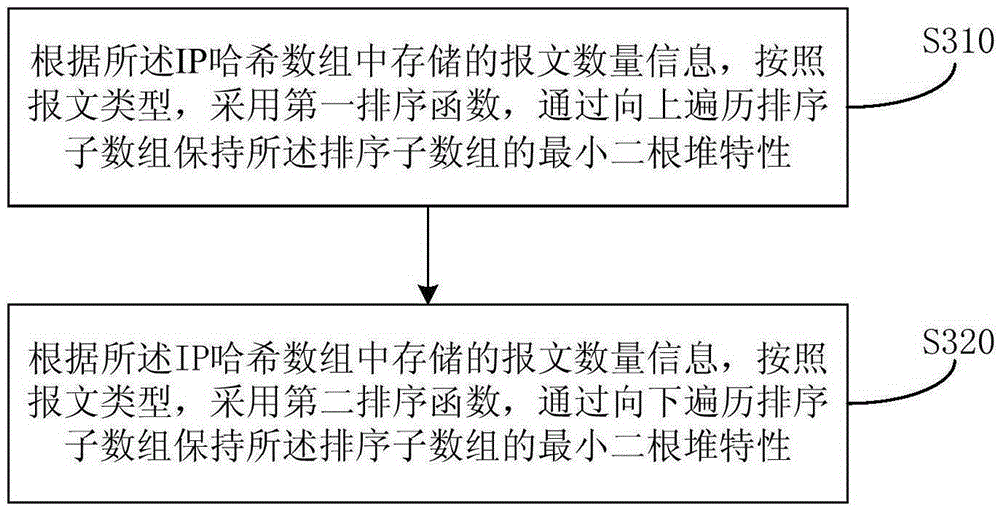
[0040] image 3 It is a flowchart of an abnormal flow detection method in Embodiment 2 of the present invention. The technical solution of this embodiment is based on the above-mentioned Embodiment 1, and is further optimized on the basis of Embodiment 1.
[0041] Further, according to the message quantity information stored in the IP hash array, according to the message type, store the IP information of the top N-bit messages in the form of the least binary heap in each sorted sub-array including :
[0042]S310. According to the message quantity information stored in the IP hash array, and according to the message type, adopt the first sorting function, and maintain the minimum binary heap characteristic of the sorting sub-array by traversing the sorting sub-array upwards;
[0043] S320. According to the message quantity information stored in the IP hash array and according to the message type, use a second sorting function to traverse the sorted sub-array downwards to maint...
Embodiment 3
[0052] Figure 4 It is a flow chart of an abnormal flow detection method in Embodiment 3 of the present invention. The technical solution of this embodiment is based on the above embodiments, and further optimizations are made on the basis of the above embodiments.
[0053] Further, receiving new IP information, updating the IP information of the top N packets and storing them in a sorted array includes:
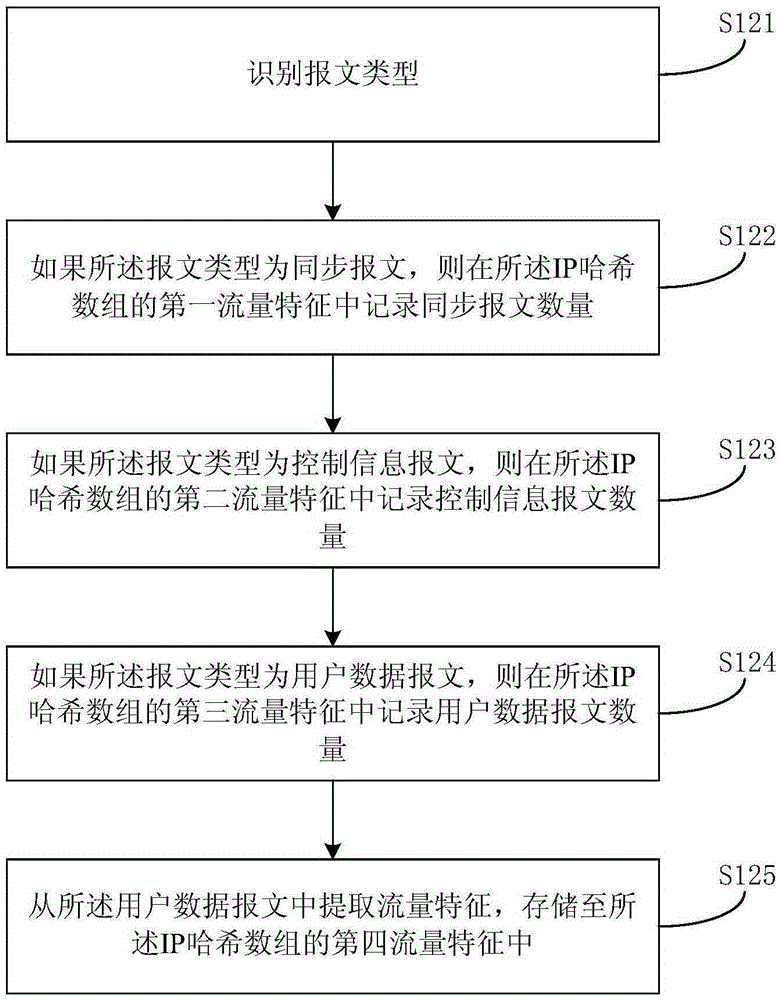
[0054] S410. Create two threads;
[0055] S420, the first thread is responsible for extracting the IP address and message type (TYPE) from the incoming and outgoing messages, and storing them in the IP hash array;
[0056] Exemplarily, if the packet type is a synchronous packet, then HASH[IP]→SYN+1, that is, add 1 to the number of synchronous packets in the IP hash array;
[0057] Otherwise, if the packet type is a control information packet, then HASH[IP]→ICMP+1, that is, add 1 to the number of control information packets in the IP hash array;
[0058] Otherwise, if the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com