Method for selecting IDA (intrusion detection agent) start strategies of wireless sensor network
A wireless sensor network, intrusion detection technology, applied in wireless communication, advanced technology, security devices, etc., can solve problems such as multiple computing and energy resources, shortening the life cycle of wireless sensor networks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
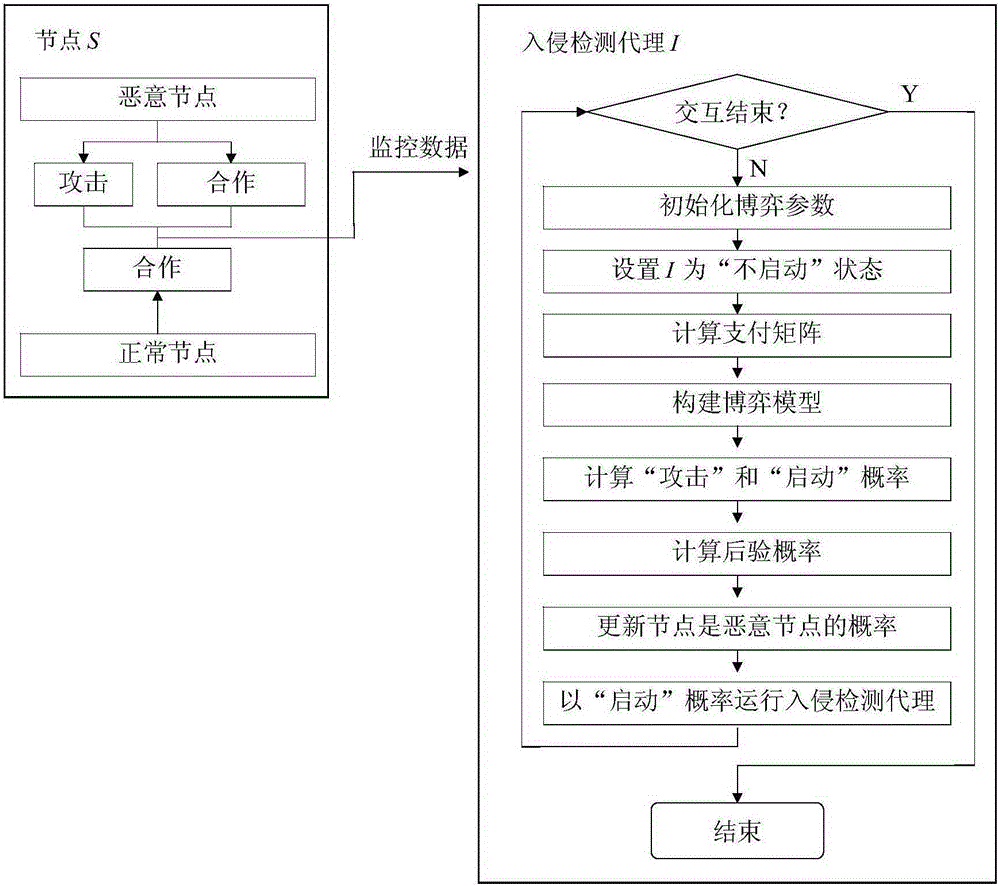
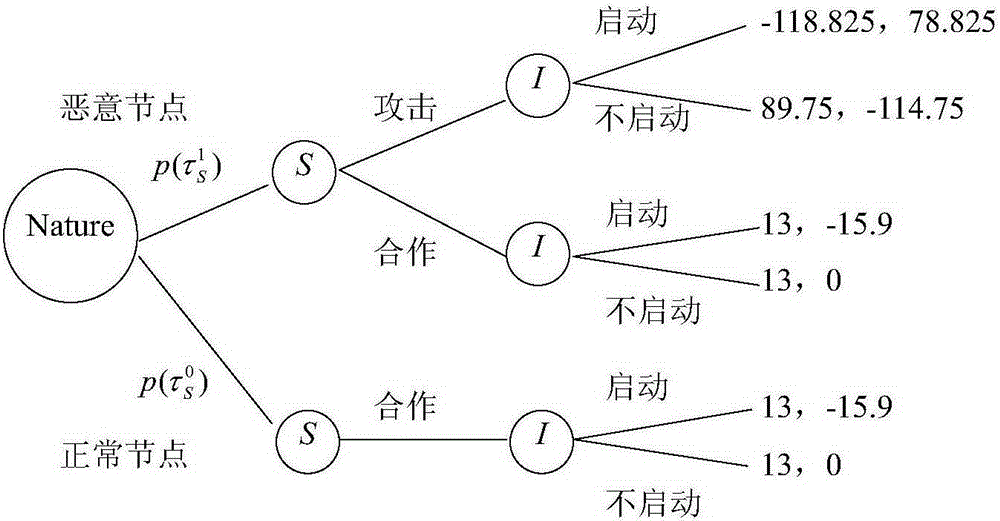
[0036] The present invention will be further elaborated below through specific embodiments. Examples will help to better understand the present invention, but the present invention is not limited only to the following examples.
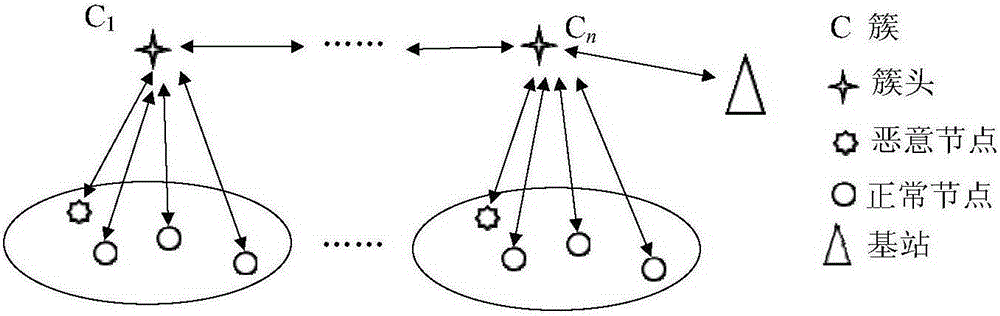
[0037] Such as figure 1 As shown, the present invention adopts a cluster structure to form an interconnected hierarchical wireless sensor network, which includes common nodes and cluster head nodes. All cluster-head nodes form high-level nodes in the hierarchy, while all common nodes form low-level nodes. In such a hierarchical structure, ordinary nodes gather data through their cluster head nodes and transmit data to the base station through other cluster heads. At the same time, because the intrusion detection agent has been pre-configured on the cluster head node, when the intrusion detection agent residing on the cluster head node is started, it will have the function of intrusion detection.
[0038] exist figure 1 In , legal sensor nodes inclu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com