A network communication method, an apparatus and a network attached storage apparatus
A network communication and communication party technology, applied in the field of network communication methods, equipment and network-attached storage devices, can solve problems such as complicated operation and waste of resources, and achieve the effect of saving system resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
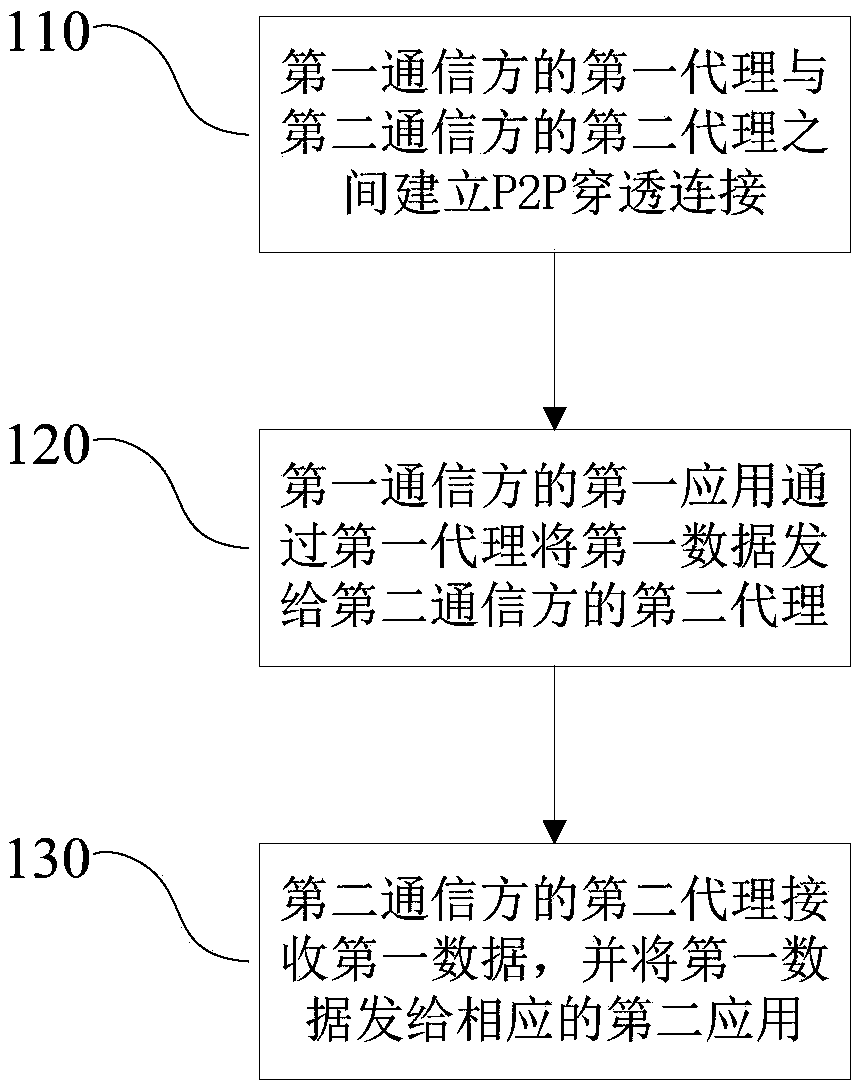
[0031] Such as figure 1 As shown, the first embodiment of the network communication method of the present invention includes:
[0032] S110, establishing a P2P penetration connection between the first agent of the first communication party and the second agent of the second communication party;
[0033] The first agent is independent of the first application, the second agent is independent of the second application, and both the first agent and the second agent are transparent to the corresponding first application and the second application.
[0034]Both the first agent and the second agent are programs that run independently, and are bridges and intermediaries for P2P penetration connections between various programs on the machine and other devices. Of course, they can also be understood as a communication interface. The programs of the first agent and the second agent can be designed according to requirements, local system environment, etc. The first agent and the second...
no. 2 example
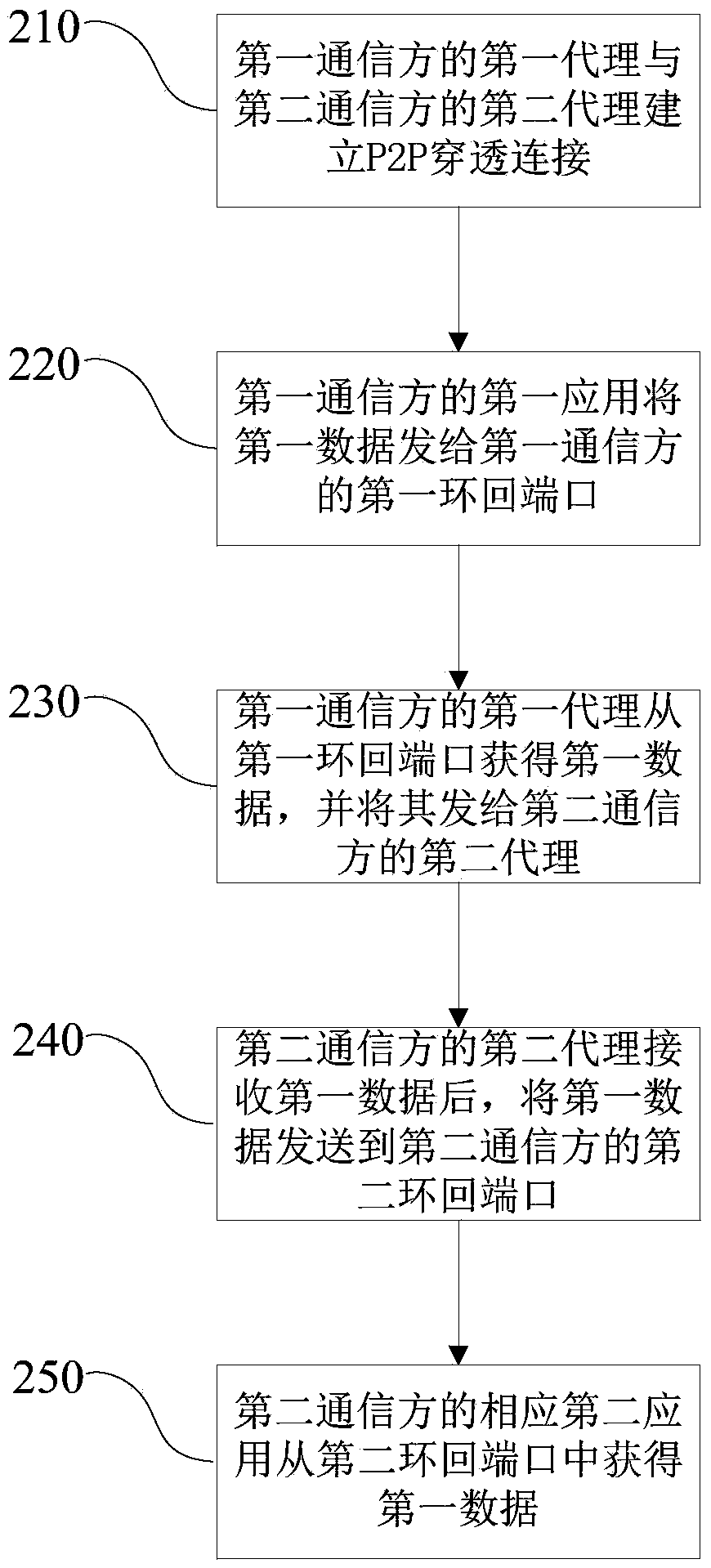
[0040] refer to figure 2 , the second embodiment of the network communication method of the present invention includes:
[0041] S210, the first agent of the first communication party establishes a P2P penetration connection with the second agent of the second communication party;
[0042] S220, the first application of the first communication party sends the first data to the first loopback port of the first communication party;
[0043] S230, the first agent of the first communication party obtains the first data from the first loopback port, and sends it to the second agent of the second communication party;
[0044] S240. After receiving the first data, the second proxy of the second communication party sends the first data to the second loopback port of the second communication party;
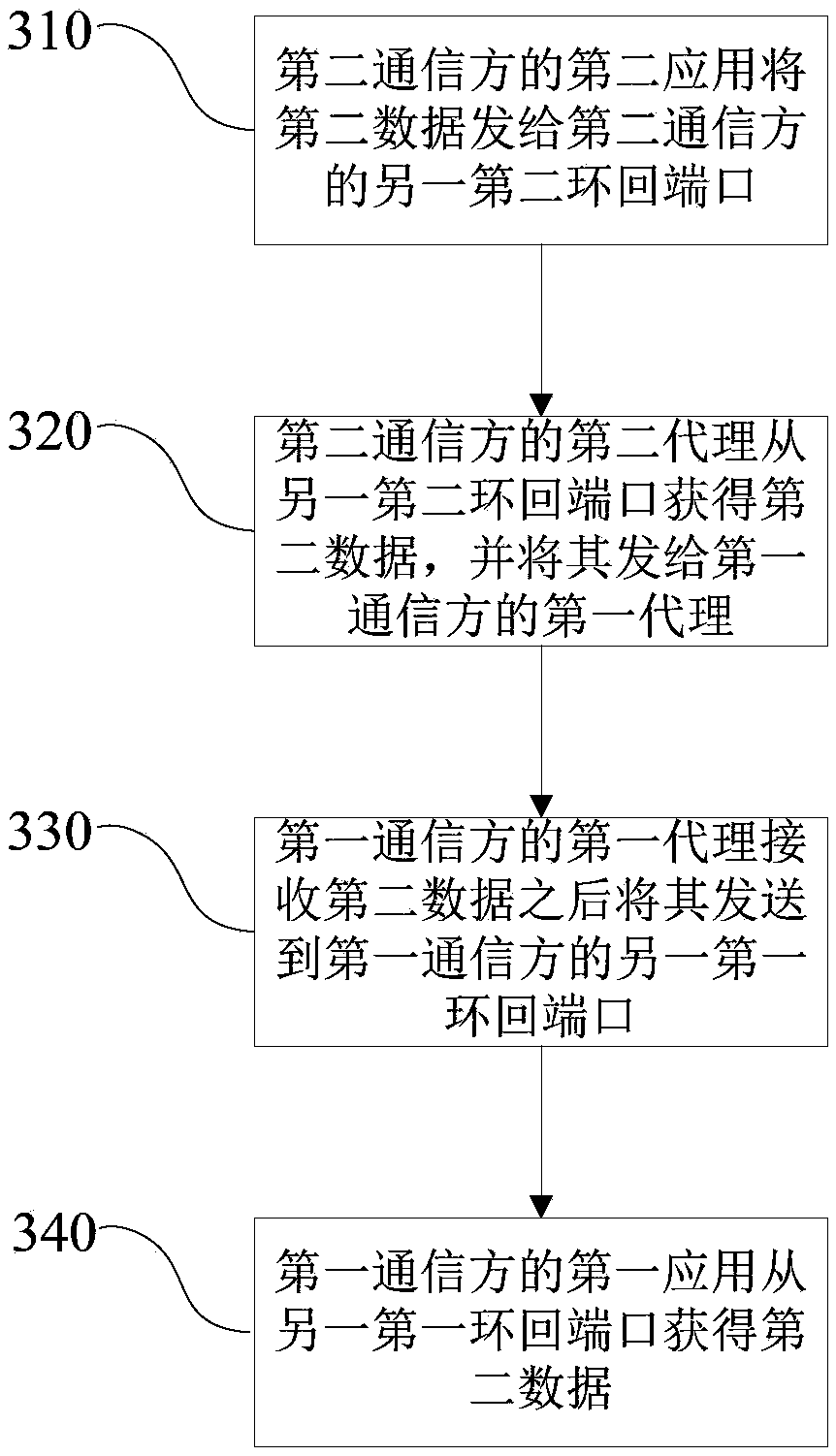
[0045] S250, the corresponding second application of the second communication party obtains the first data from the second loopback port, and completes sending the data from the first c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com