Incoming call processing method and device
A technology for incoming call processing and incoming calls, which is applied in the field of mobile communication to achieve the effects of avoiding harassment, realizing intelligent management, and preventing harassment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0099] When the user chooses to reject the harassing call by operating the answer option, after receiving the rejection instruction, the terminal can provide the user with a caller number management option through the display interface, and the caller number management option is used to prompt the user whether to choose to The caller number is added to the blacklist, and the user confirms whether to add the caller number of the harassing call to the blacklist by operating the caller number management option.
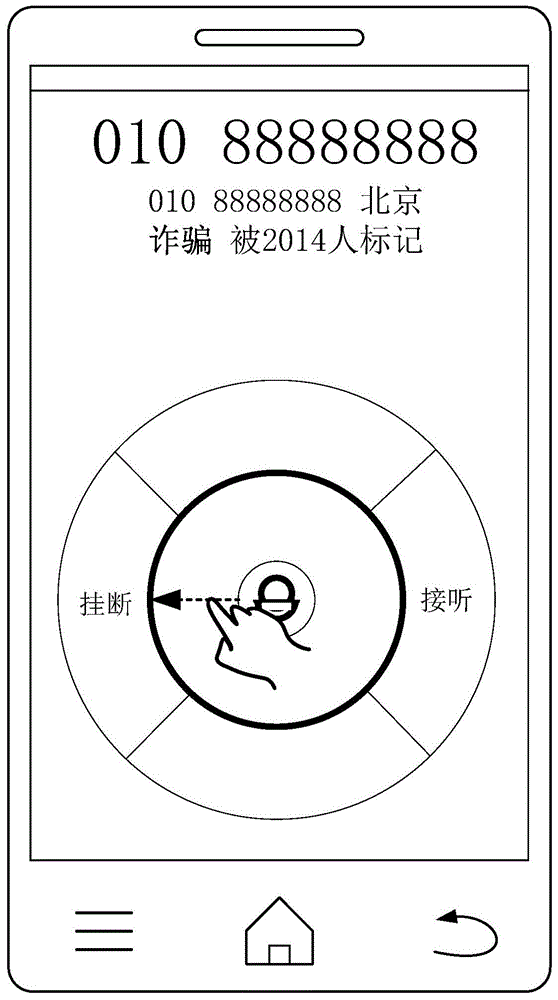
[0100] For example, see Figure 4 , the caller number management option may be a pop-up window presented by the terminal on the answering interface. When the terminal receives the rejection instruction, it can pop up a pop-up window for the user on the display interface, "whether to add this number to the blacklist", the pop-up window includes two user options of "yes" and "no"; when the user selects When "Yes", add the calling number to the blacklist.
Embodiment approach 2
[0102] When the user chooses to reject the harassing call by operating the answering option, the terminal automatically triggers adding the phone number of the harassing call to the blacklist after receiving the rejection instruction.
[0103] For example, see Figure 5 , which can be used as image 3 On the basis of the answering interface shown, there is an option of "reject and add to the blacklist". When the incoming call is marked as a nuisance call, the user can operate this option by sliding the finger down to hang up the nuisance call , and directly add the calling number of the harassing call to the blacklist.
Embodiment approach 3
[0105] Set the preset duration, when the user does not operate the answer option within the preset duration, that is, when the terminal does not receive a reject or answer command within the preset duration, the harassing call will be hung up and the harassing call will be automatically triggered to add the caller number to the blacklist. For example, the preset duration can be set to 30 seconds. When the user does not answer an unfamiliar call marked as a nuisance call for more than 30 seconds, the system will automatically hang up the call and add the caller number to the blacklist. Alternatively, when the terminal does not receive a reject or answer command within the preset time period, the user may leave or not carry the terminal with him at this time, so a message such as Figure 4 The pop-up window of "whether to add this number to the blacklist" shown, when the user sees the pop-up window again, the user can choose whether to add the caller number to the blacklist. Of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com