A method and system for redirecting file operations in a security sandbox
A file operation and security sandbox technology, applied in the direction of platform integrity maintenance, etc., to achieve the effect of ensuring integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
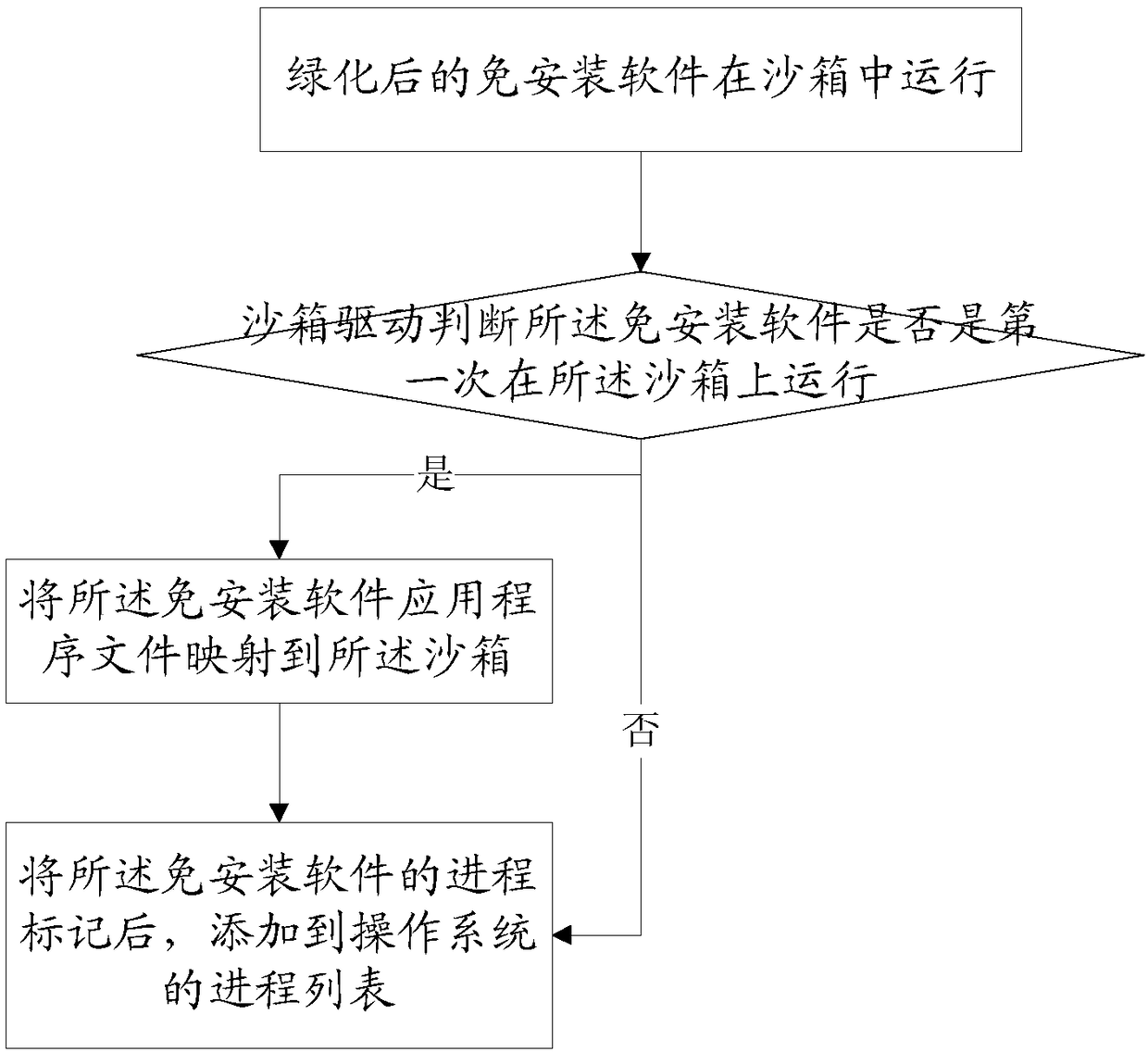
[0037] refer to figure 1 and image 3 , specific implementation mode 1, a method for redirecting file operations in a security sandbox,
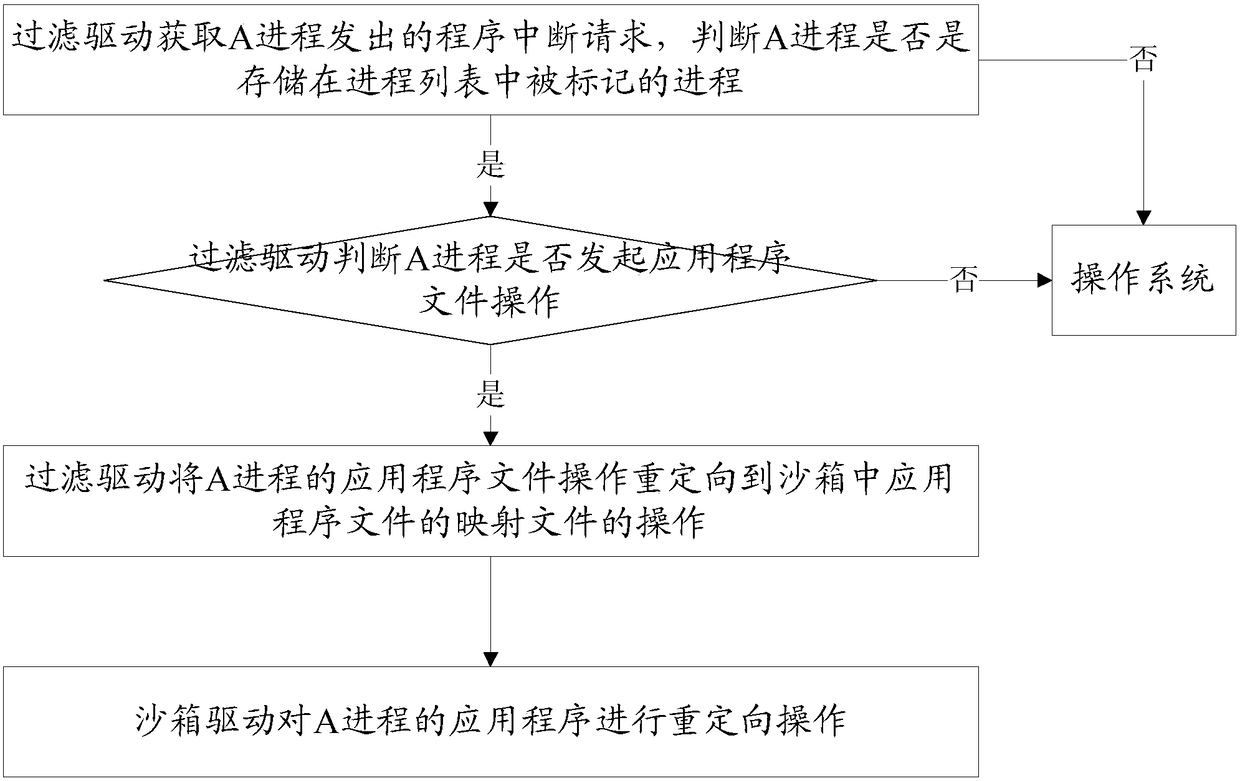
[0038] S1, the filter driver obtains the program interruption request sent by the A process, and judges whether the A process is a marked process stored in the process list, if yes, enters S2, if not, sends the program interruption request to the operating system;
[0039] S2, the filter driver judges whether the A process initiates the application program file operation, if yes, enters S3, if not, sends the judgment result to the operating system;
[0040] S3. The filter driver redirects the operation of the application file of the A process to the operation of the mapping file of the application file in the sandbox;
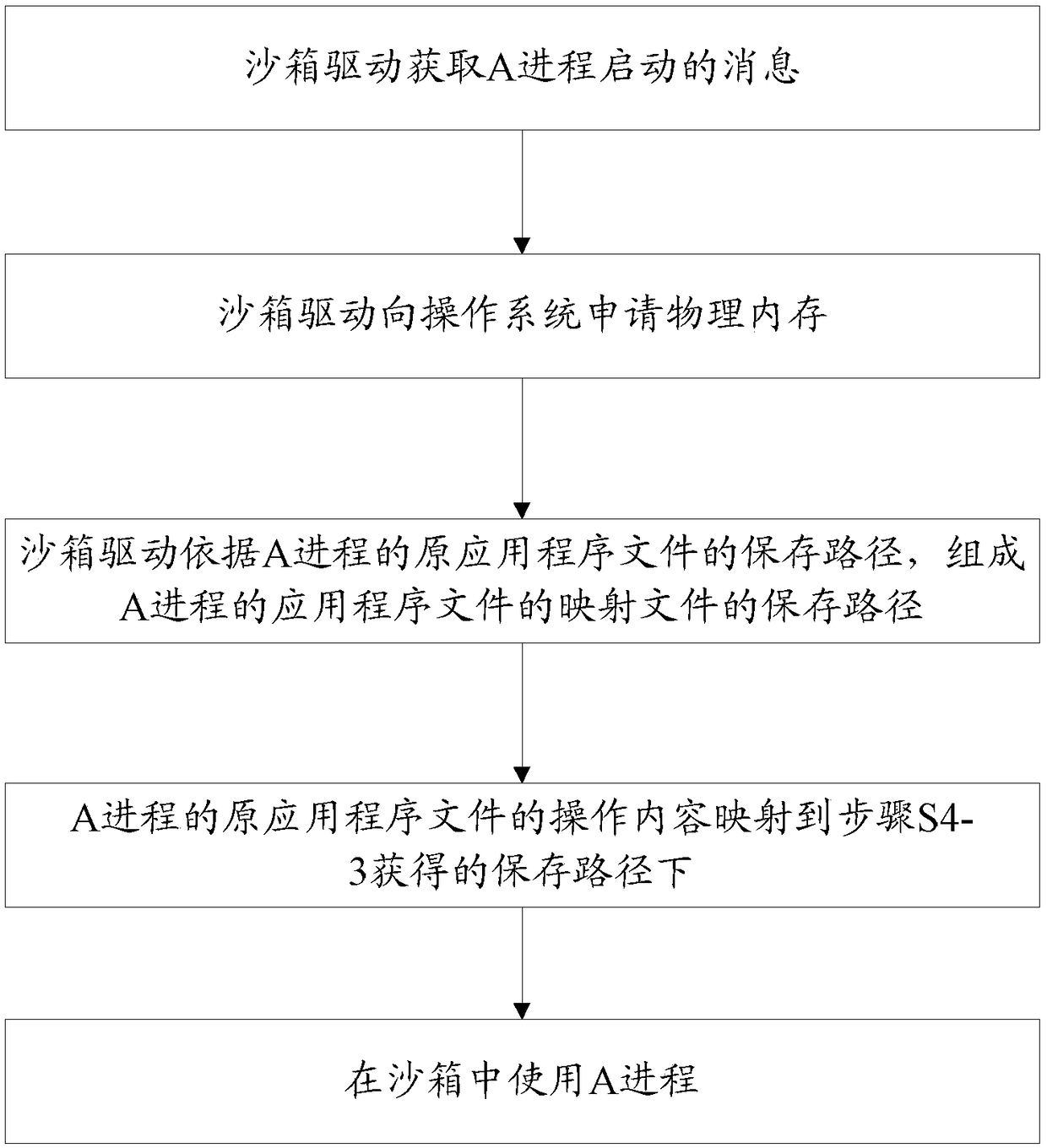
[0041] S4, the sandbox driver redirects the application program of the A process;
[0042] S4-1. The sandbox driver acquires the message that process A starts;
[0043] S4-2. The sandbox driver applies for physical memory...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com