Key managing method for trusted root server based virtual trusted platform module (VTPM)
A platform module and key management technology, applied in the field of information security, can solve the problem of not many trusted root servers, and achieve the effect of avoiding unauthorized use, ensuring security, and ensuring standardization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
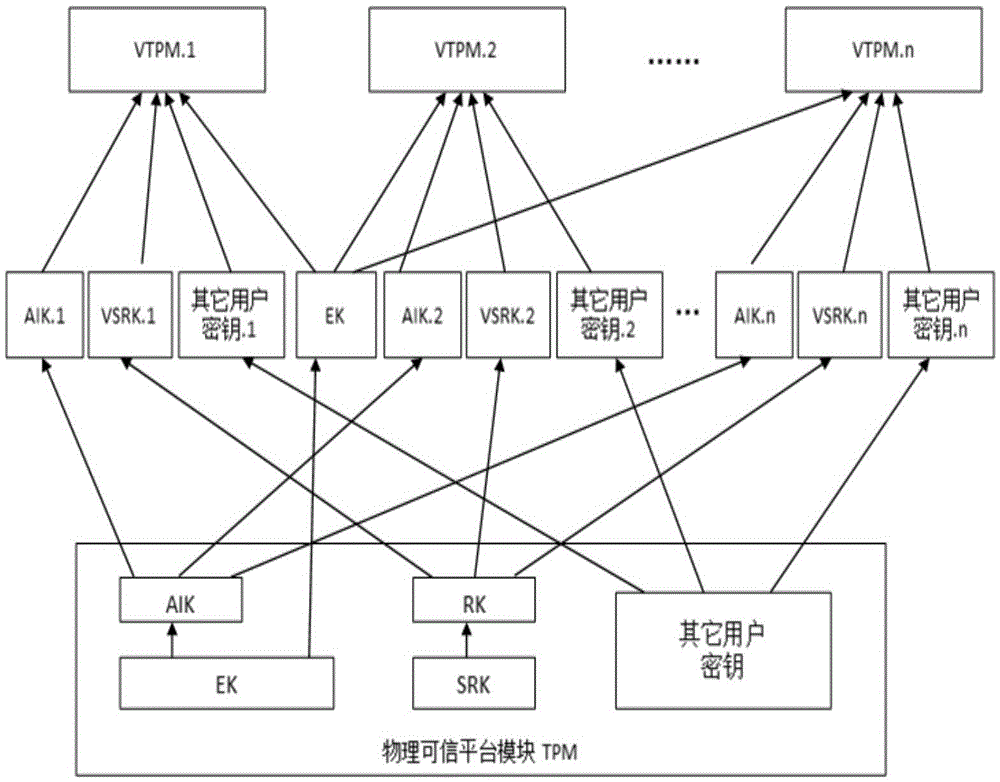
[0036] 1. Key generation mechanism
[0037] Such as figure 1 As shown, in the entire key derivation diagram, there are two special keys:
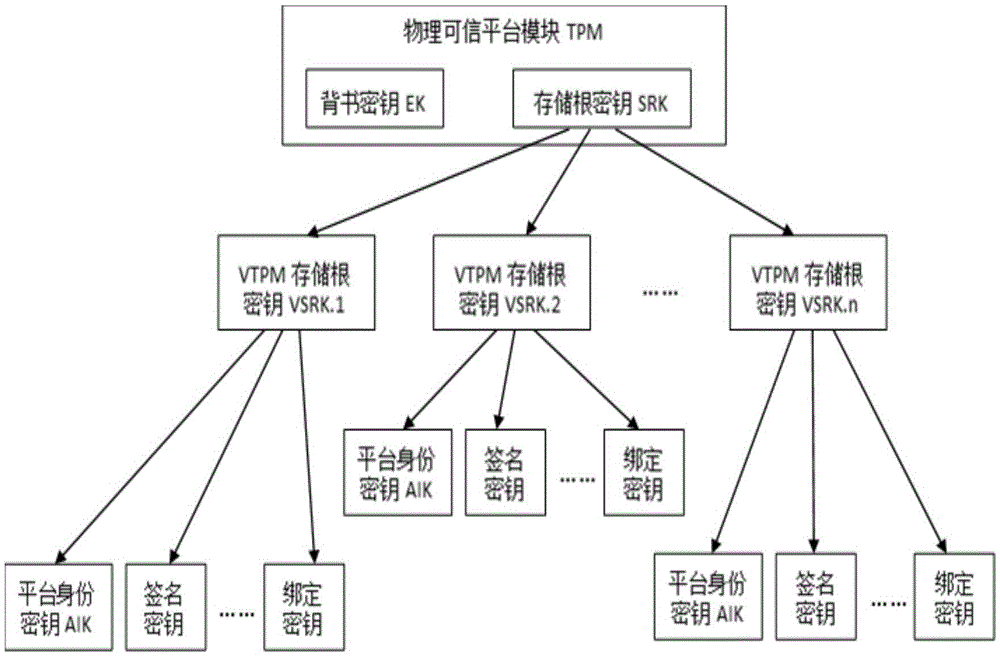
[0038] (1) Endorsement key EK. The endorsement key in the VTPM directly adopts the endorsement key in the physical TPM, and its generation method is similar to that of the physical TPM. There are two generation methods: one is to use the TPM command TPM_CreateEndorsementKeyPair Key "injection" technology, under the premise of trusting the manufacturer, is generated by the manufacturer and then injected into the TPM.
[0039] (2) Store the root key SRK. As the only user of the physical TPM, the VTPM manager stores the root key generated when the user is created, manages all key data of the user, and only serves the physical TPM.
[0040] Other keys:
[0041] (1) Virtual platform identity authentication key VAIK. The VAIK is actually the AIK of the physical TPM, and its generation requires the support of a trusted third-party PCA. PCA ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com