Information security equipment and its management method, management device and management system
A technology for information security and equipment management, applied in the field of information security, can solve problems such as time-consuming and labor-intensive, funds cannot be circulated in information security equipment, and the original version cannot be rolled back
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0085] In order to enable those skilled in the art to better understand the technical solution of the present invention, the information security equipment management method, information security equipment management device, information security equipment and information security equipment management system of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods describe.
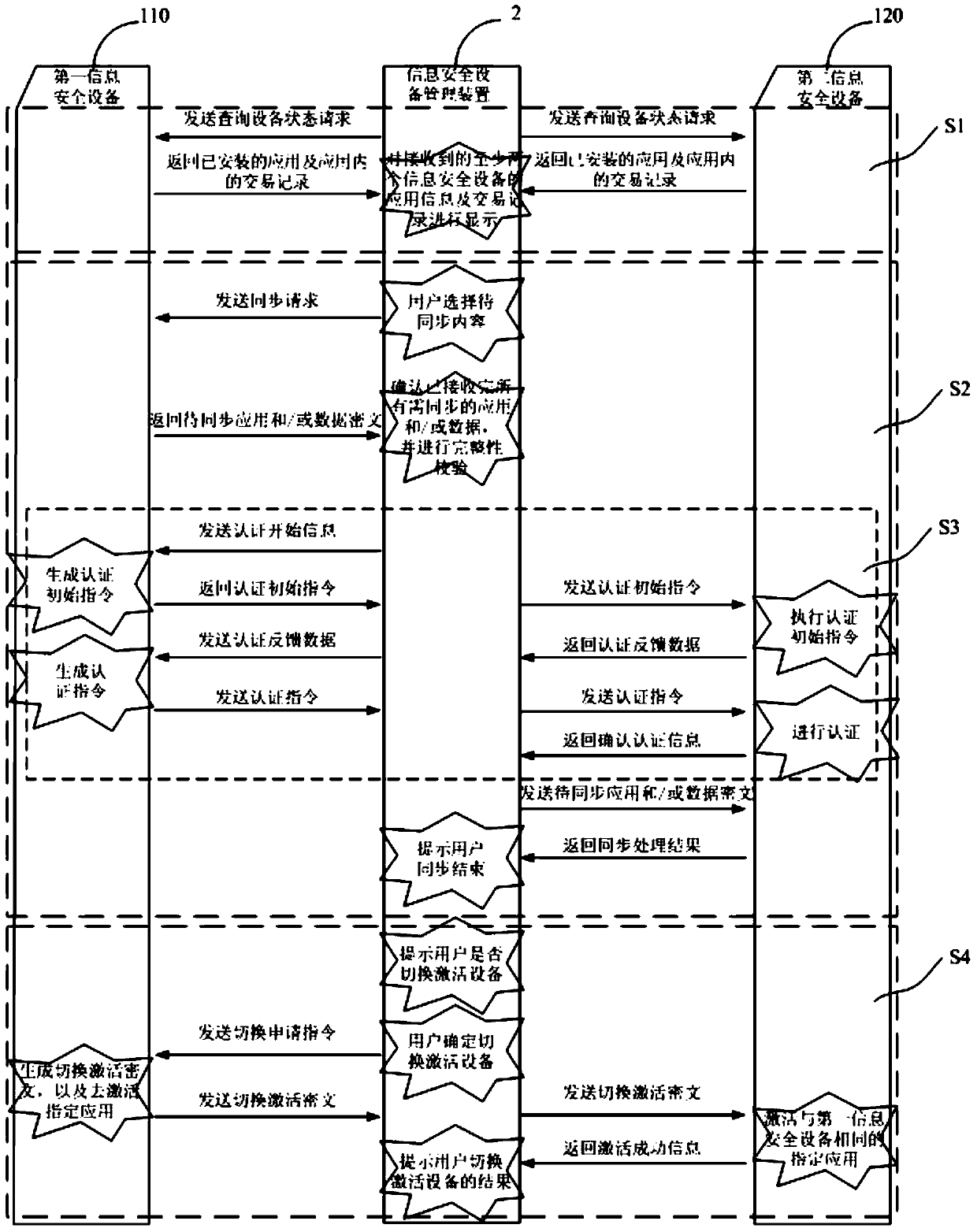
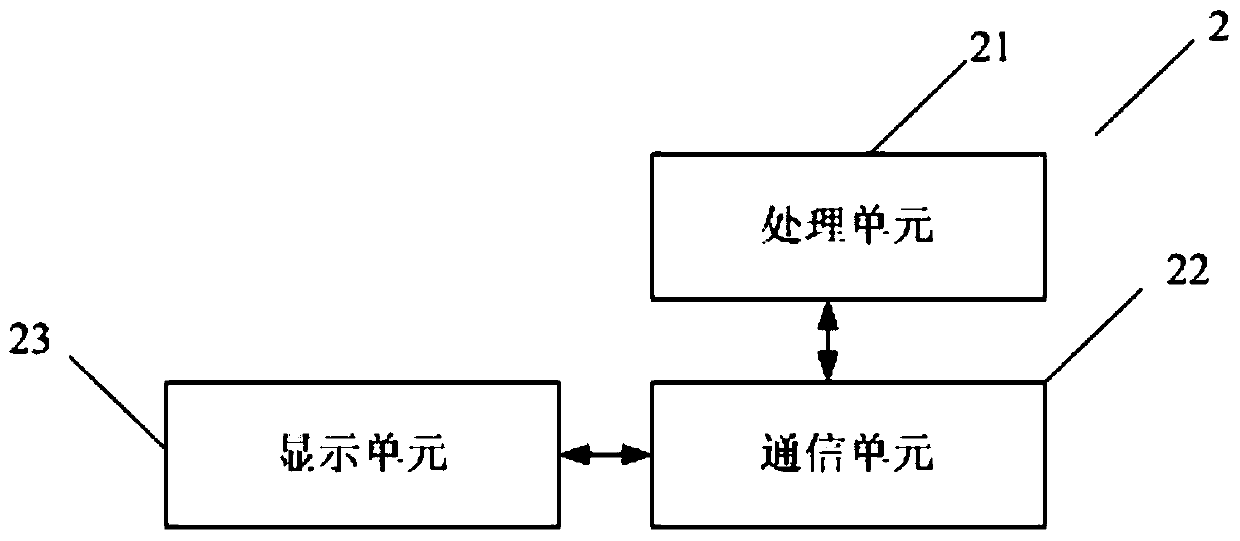
[0086] This embodiment provides an information security device and a management method for multiple information security devices. Through the information security device management method, multiple information security devices are managed through information sharing, which can easily realize the integration of personal funds. Function, but also has high security and convenience.
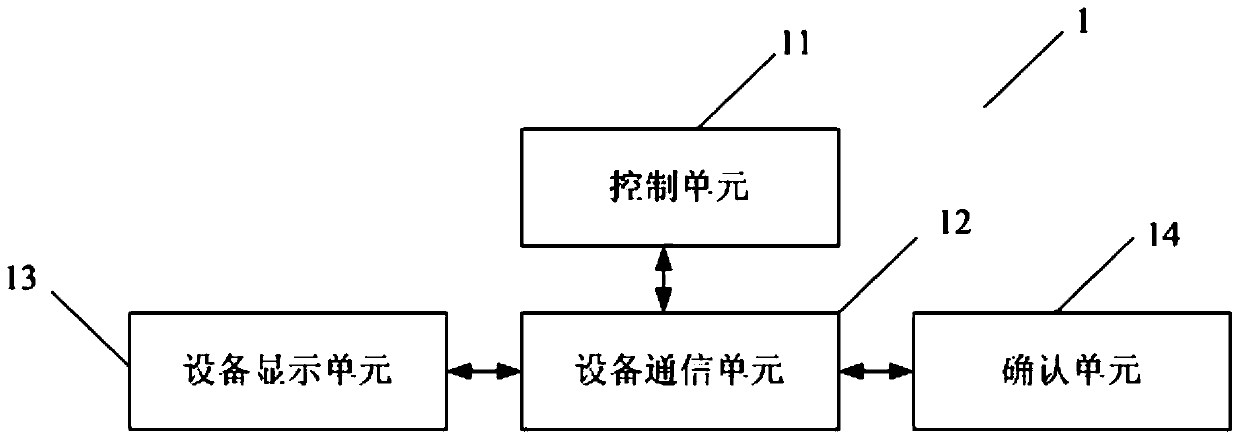
[0087] Such as figure 1 As shown, the information security device 1 includes a control unit 11, a device communication unit 12, a device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com