Graphic verification code generation method
A graphic verification code and verification code technology, applied in the field of computer information, can solve problems such as interfering with website business, consuming network bandwidth, occupying website resources, etc., to achieve the effect of enhancing the ability to resist attacks and increasing the difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The preferred modes of the present invention will be described in further detail below in conjunction with the examples.
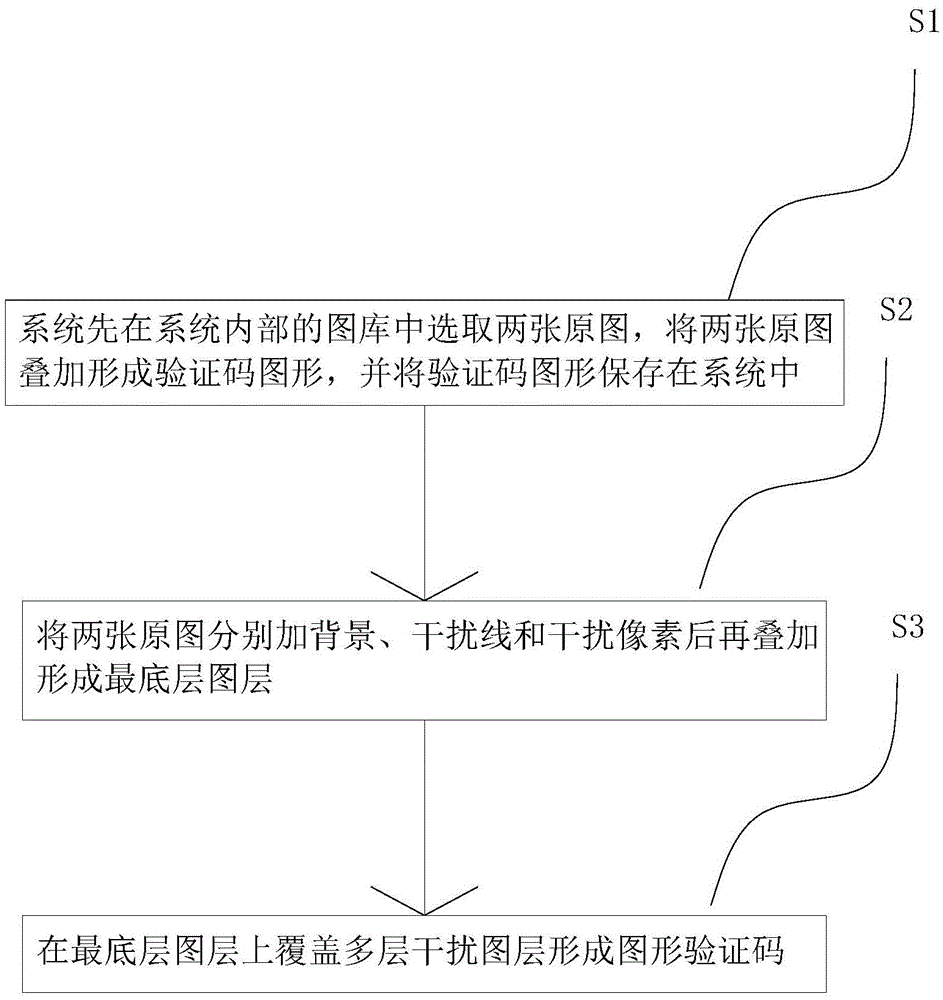
[0015] Such as figure 1 As shown, a method for generating a graphic verification code includes the following steps:
[0016] S1. The system first selects two original images containing numbers or letters from the gallery inside the system, superimposes the two original images to form a verification code graphic, and saves the verification code graphic in the system.
[0017] S2. Add the background, interference lines and interference pixels to the two original images respectively, and then superimpose them to form the bottom layer.
[0018] S3. Cover multiple layers of interfering layers including dynamic pictures on the lowest layer to form a graphic verification code.
[0019] The invention proposes a method for generating a graphic verification code. Compared with the existing method for generating a graphic verification code, this method super...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com