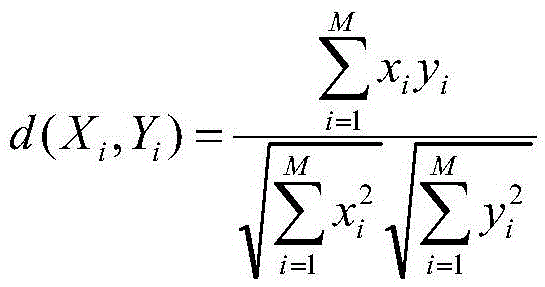Method for evaluating user behavior on the basis of position mining
A user and behavior technology, applied in data processing applications, instruments, resources, etc., can solve problems such as manual maintenance records, identifiable location restrictions, etc., to reduce deployment overhead and reduce illegal cheating.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
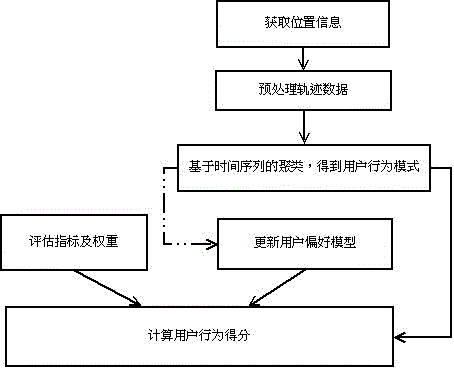
[0034] A user behavior evaluation method based on location mining is characterized in that: using trajectory data to mine user behavior patterns, analyzing user behavior rules, and evaluating user behavior.
[0035] Described method specifically comprises the steps:
[0036] a. Obtain location information to obtain trajectory data, and preprocess the trajectory data;
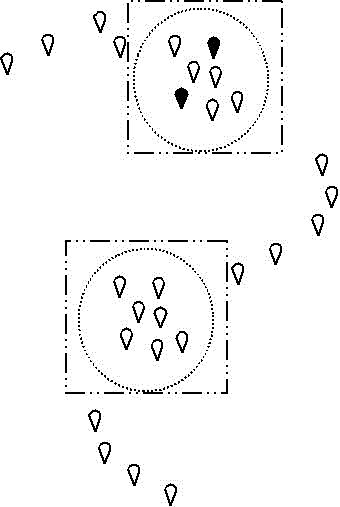
[0037] b. Obtain the time distribution of users in different places in different time periods through trajectory data, and obtain the user's behavior pattern;
[0038] c. Utilize the historical records of user behavior patterns to update the user preference model, judge whether it is an abnormal behavior according to the user preference model, and calculate the user behavior score.
[0039] In the step a, the mobile device reports the track data as L={l 1 , l 2 ,...,l n}, where l i =(lat i ,long i ,time i ) represents the latitude and longitude and time. Firstly, the repeated points in the trajectory dat...
Embodiment 2
[0055] A user behavior evaluation method based on location mining is applied to the management of security personnel in property companies. Security personnel need to check enough time in some designated locations every day, and need to patrol a certain number of times a day. Through this behavior evaluation method, the security guard's working conditions can be evaluated through the final score. The method includes the following steps:
[0056] a. Obtain location information through mobile devices such as smart phones carried by security guards to obtain trajectory data, and preprocess the trajectory data;
[0057] b. Obtain the time distribution of security guards at different locations in different time periods through trajectory data, and obtain the behavior patterns of security guards;
[0058] c. Utilize the historical records of security behavior patterns to update the user preference model, judge whether it is an abnormal behavior according to the user preference mode...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com