Security level determining method and device
A security level and determination method technology, applied in the Internet field, can solve problems such as inability to control business risks and inability to know equipment security, so as to achieve the effect of improving controllability and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
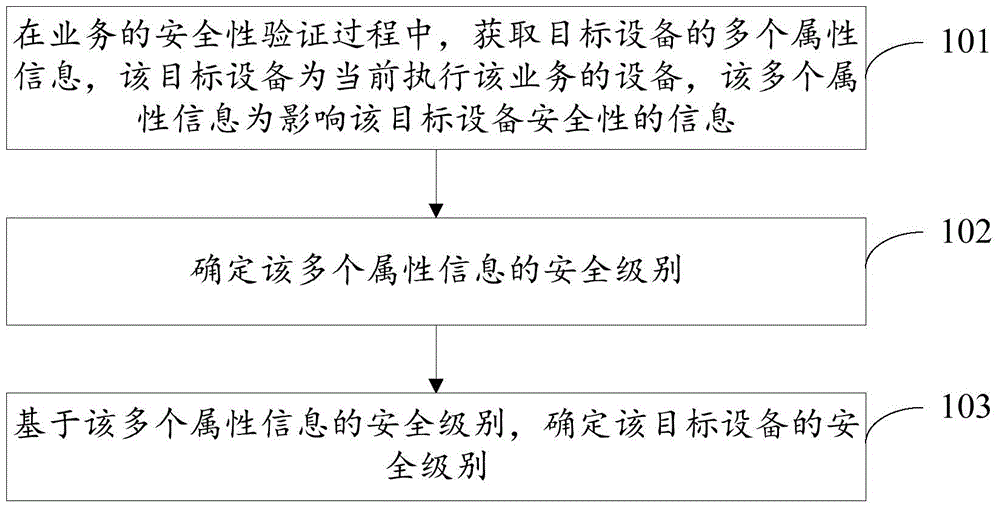
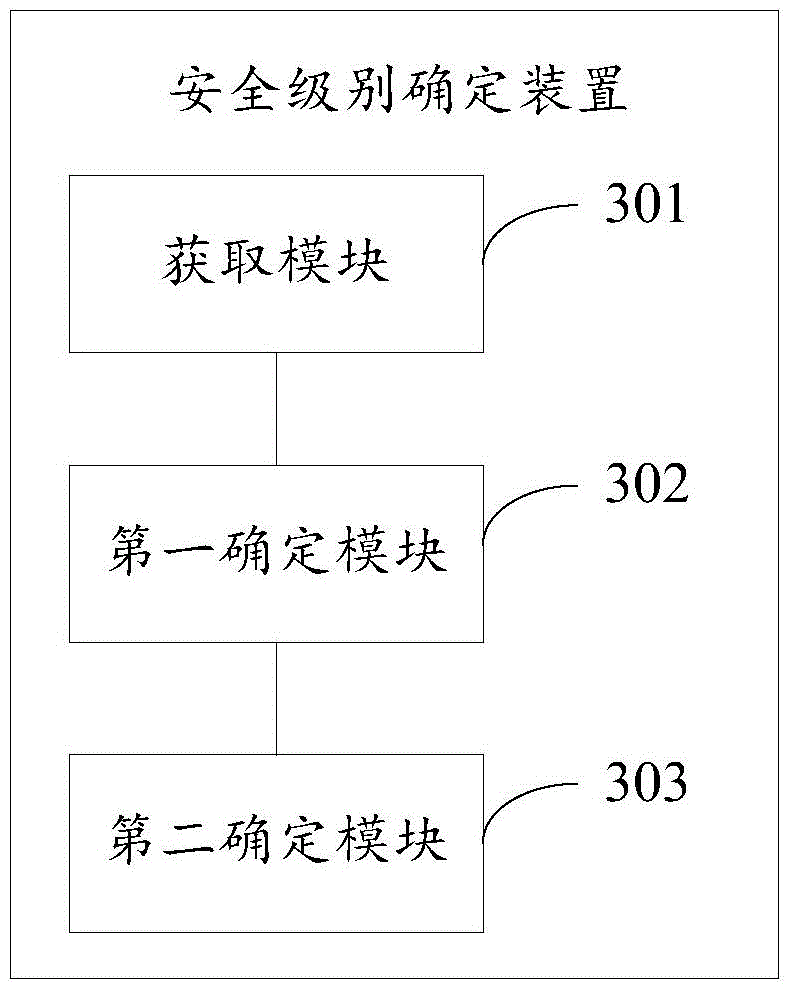
[0018] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0019] Before explaining and describing the embodiments of the present invention in detail, the application scenarios of the embodiments of the present invention are firstly introduced. Since some businesses completed on the device need to ensure security, such as payment services, at present, the risk of the business is basically reduced through some security logic in the application to ensure the security of the business, for example, in the application The security logic that can only pay a certain amount per day can be set in the program. That is to say, at present, the service provider basically controls the risk by itself, and when the device where the application is located has certain risks, the security of the device cannot be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com