Sandbox based two-dimensional code detection method and system
A two-dimensional code and sandbox technology, applied in the field of information security, can solve problems such as insufficient maintenance of two-dimensional code security, and achieve the effect of avoiding opening malicious two-dimensional codes, assisting judgment and decision-making, and accurate detection results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention provides a sandbox-based two-dimensional code detection method and system embodiments, in order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the above-mentioned purpose and characteristics of the present invention And advantage can be more obvious and easy to understand, below in conjunction with accompanying drawing technical scheme in the present invention is described in further detail:
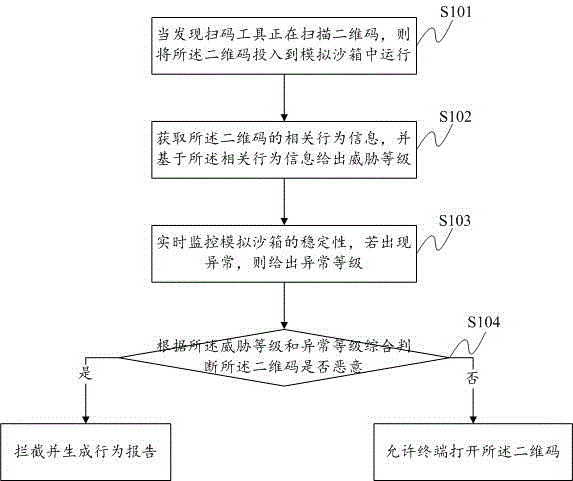
[0027] The present invention first provides an embodiment of a sandbox-based two-dimensional code detection method, such as figure 1 shown, including:
[0028] S101 When it is found that the code scanning tool is scanning the two-dimensional code, put the two-dimensional code into the simulation sandbox for operation;
[0029] Among them, use the simulated sandbox to open the QR code without worrying about endangering system security;
[0030] S102 Acquiring relevant b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com