Security protection management method and system based on face features and gait features
A technology of gait features and facial features, applied in the field of security management methods and systems based on facial features and gait features, can solve problems such as unavoidable photo deception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
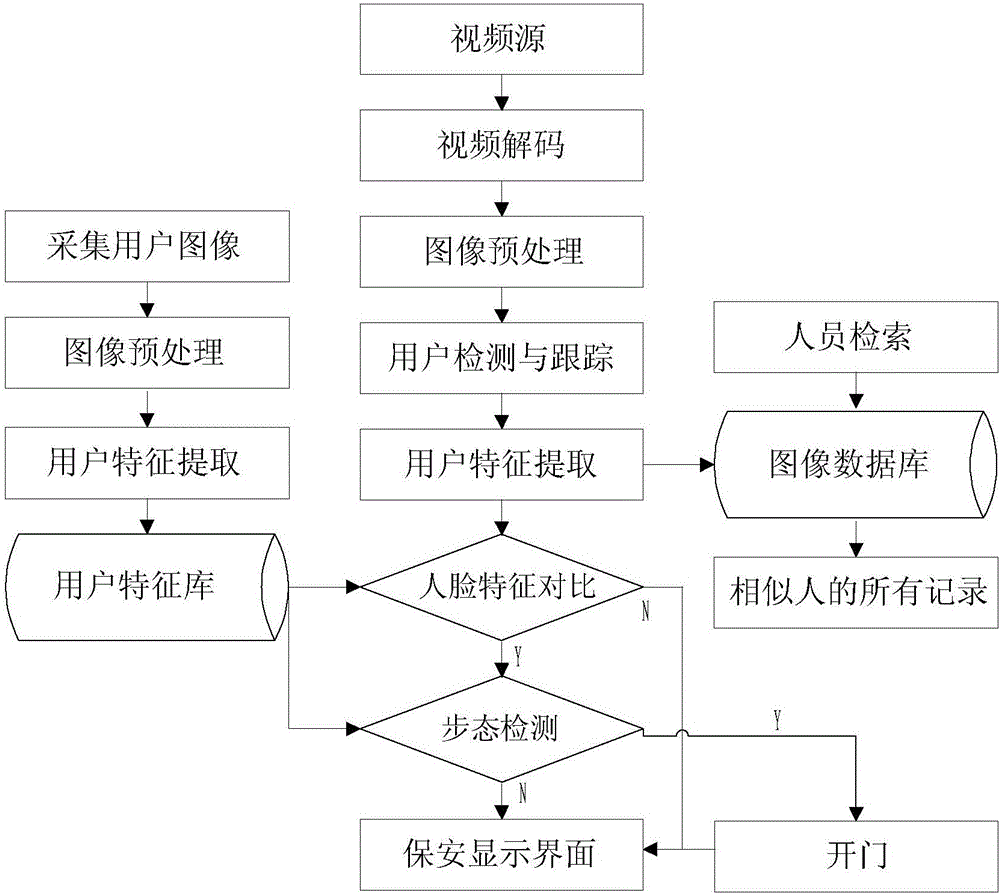
[0018] In a basic embodiment, a security management method based on facial features and gait features is provided, the method includes the following steps:
[0019] S100. Establish a user feature library: collect user information of legal users who are allowed to pass through the access control, the user information includes a face image, and extract the face features of the face image; collect the gait features of the corresponding user; , the gait feature and the user information are stored in the user feature library;
[0020] S200. Extracting the image data of the video frame: obtaining the real-time video from the camera within the scope of security management, decoding the video, and extracting the image data of the video frame;
[0021] S300. Extracting user features: performing user positioning on the image data of the video frame extracted in step S200, extracting facial features and corresponding gait features;
[0022] S400, judging whether it is a legitimate user:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com