Method and device for secure communication in Internet of Things
A technology for secure communication and the Internet of Things, applied in the field of secure communication methods and devices, can solve problems such as lack of identity verification, lack of security control mechanisms, and information leakage in smart devices, so as to ensure communication security and prevent devices from being counterfeited and peers. The effect of counterfeiting and ensuring communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
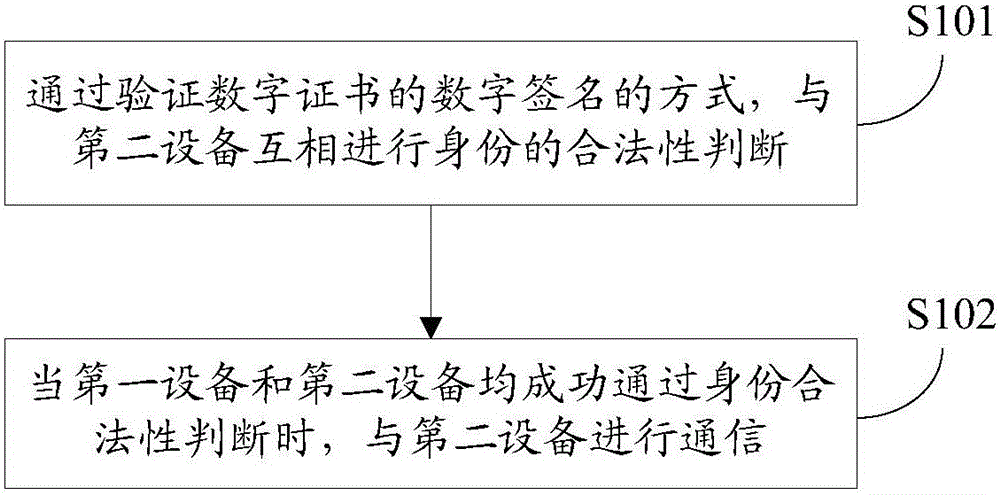
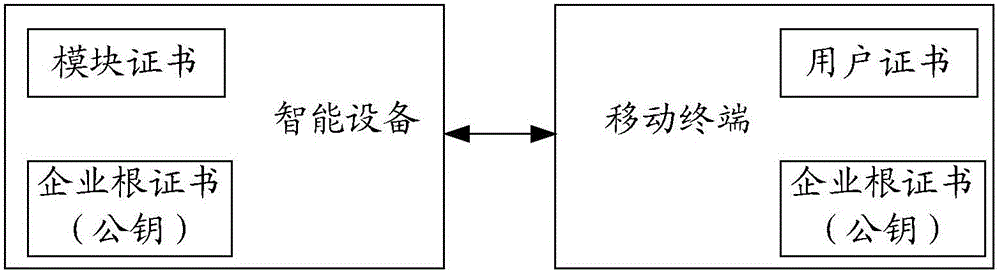
[0050] In the first embodiment of the present invention, a secure communication method in the Internet of Things, in the Internet of Things including cloud platform, smart device and mobile terminal three-party device interconnection, such as figure 1 As shown, for the communication between any two devices, assuming that any two devices are the first device and the second device, the steps performed by the first device include:
[0051] Step S101 , by verifying the digital signature of the digital certificate, judging the legitimacy of identity with the second device; wherein, the digital certificates and corresponding digital signatures of the three-party devices are all issued by the same CA center.
[0052] Specifically, step S101 includes:
[0053] Exchanging respective digital certificates with the second device for the second device to verify whether the digital signature of the digital certificate of the first device is legal, and,
[0054] The first device verifies wh...
no. 2 example
[0061] The second embodiment of the present invention is a secure communication method in the Internet of Things. The method described in this embodiment is substantially the same as that in the first embodiment. The difference is that step S101 of this embodiment specifically includes:
[0062] Exchanging respective digital certificates with the second device, so that the second device verifies whether the digital signature of the digital certificate of the first device and the attributes of the digital certificate are legal, and,
[0063] The first device verifies whether the digital signature of the digital certificate of the second device and the attributes of the digital certificate are legal, and if legal, determines that the second device has successfully passed the identity legality judgment; otherwise, determines that the second device cannot pass the identity legality judgment.
[0064] Further, the first device verifies whether the digital signature of the digital ce...
no. 3 example
[0067] The third embodiment of the present invention is a secure communication method in the Internet of Things. The method described in this embodiment is substantially the same as that in the first embodiment. The difference is that in step S102, the method described in this embodiment performs Communications, including:
[0068] The encryption mode negotiated with the second device is used to communicate with the second device.
[0069] Specifically, the process of negotiating with the second device to determine the encryption method includes:
[0070] After both the first device and the second device successfully pass the identity legality judgment, they negotiate with the second device to determine the encryption method; wherein, the messages exchanged during the negotiation process are encrypted and decrypted using an asymmetric encryption algorithm, and the negotiation determines the encryption method. The encryption method includes: a symmetric encryption algorithm su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com