MD5-based two-way encryption data protection method
A data protection and two-way encryption technology, applied in encryption devices with shift registers/memory, digital transmission systems, user identity/authority verification, etc., can solve problems such as high performance consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
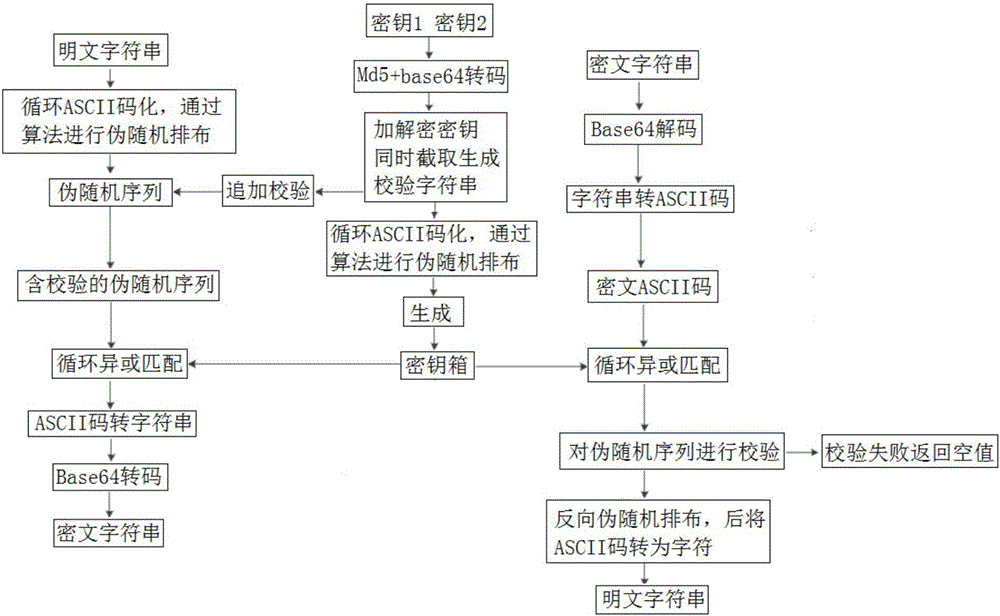
[0012] The present invention will be further described in detail below in conjunction with the accompanying drawings, so that those skilled in the art can implement it with reference to the description.
[0013] A two-way encrypted data protection method based on MD5, please refer to the attached figure 1 , including: key processing process, encryption process, decryption process, wherein,
[0014] The key processing process includes: performing md5 and base64 transcoding processing on the key to obtain the encryption and decryption special key; intercepting the above encryption and decryption special key to generate a fixed-digit check string for subsequent encryption and decryption processes The verification operation in is used; use the pseudo-random algorithm to process the above encryption and decryption private key, scramble its order again, and convert the string into ASCII code, that is, the key box, to be used in the subsequent encryption and decryption process;
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com