Encryption device and method
A technology of an encryption device and an encryption method, which is applied to a secure communication device and key distribution to achieve the effects of increasing difficulty and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
[0040] The invention provides an encryption device.
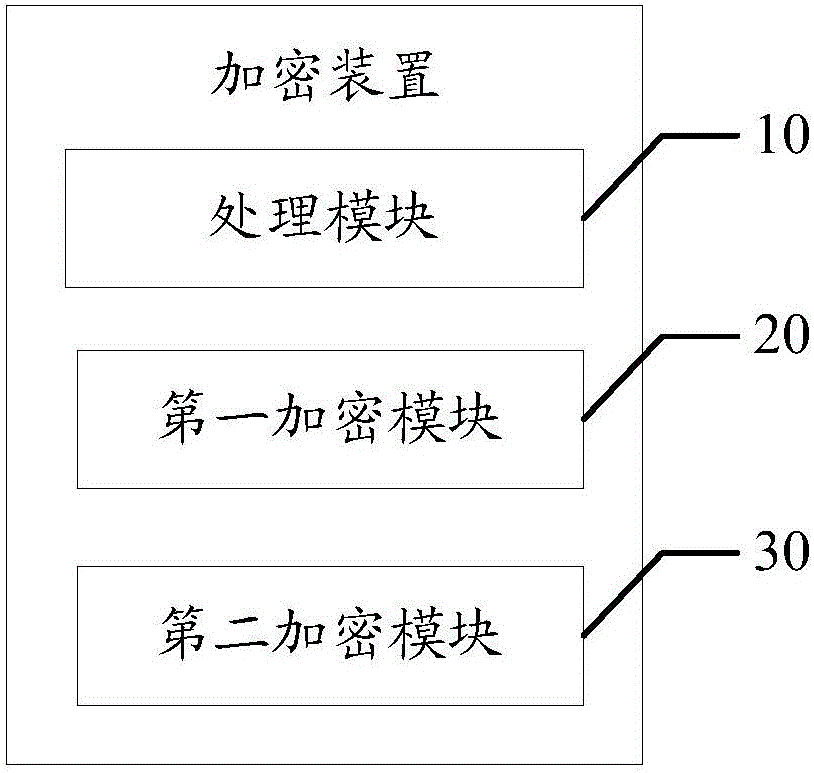
[0041] refer to figure 1 , figure 1 It is a functional block diagram of the first embodiment of the encryption device of the present invention.
[0042] In this embodiment, the encryption device includes:
[0043] The processing module 10 is configured to generate a license according to the license private key when the license private key is obtained;
[0044] When the production license is required, assign the corresponding MAC (MediaAccess Control, Media Access Control) address to the license to be generated, and then fill in the relevant information of the generated license on the license production page, such as filling in the MAC address corresponding to the license, and the license corresponds to identification number, etc. During the license production ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com