Key protection method
A key protection and key technology, which is applied to data and information that needs to be encrypted and backed up. Based on the field of key protection, it can solve problems such as key loss and information cannot be recovered, and achieve the effect of improving security and reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
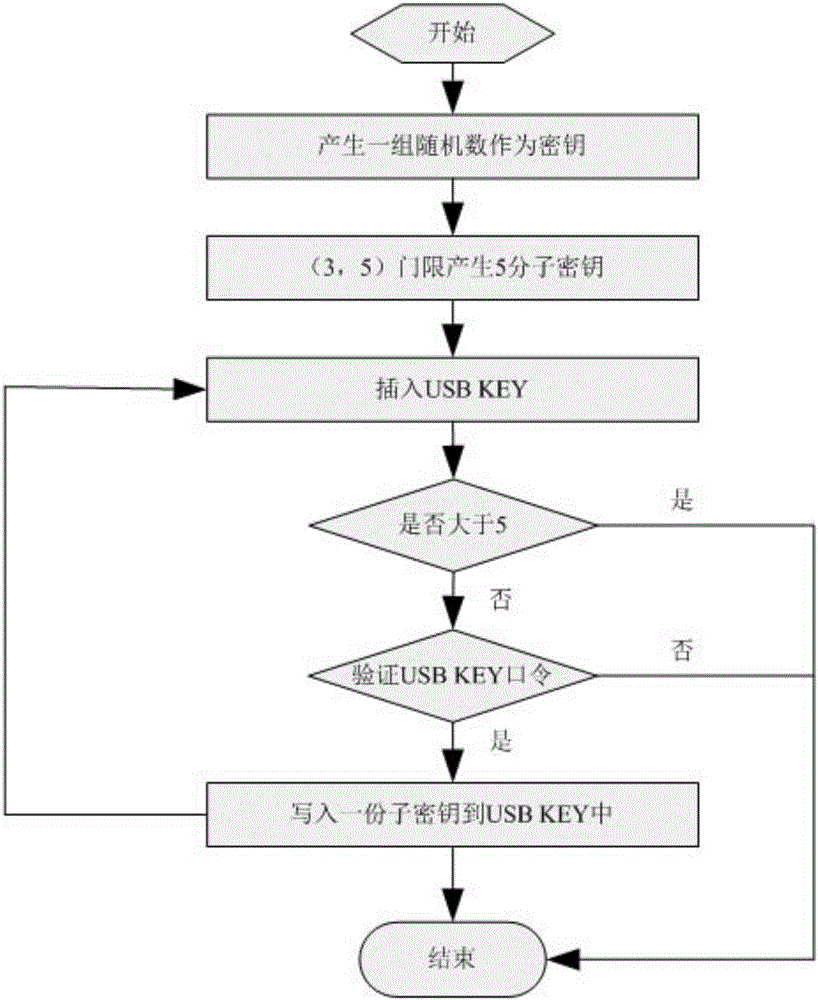
[0014] Encryption process:
[0015] Randomly generate a random number as the key to encrypt the plaintext.
[0016] Use this key to encrypt plaintext data to generate ciphertext.
[0017] Use the (3,5) threshold algorithm to split the key into 5 sub-keys.
[0018] Store the 5 sub-keys in 5 USB KEYs, and distribute the 5 USB KEYs to 5 different personnel for safekeeping.
[0019] USB KEY custodians set their own USB KEY passwords respectively.
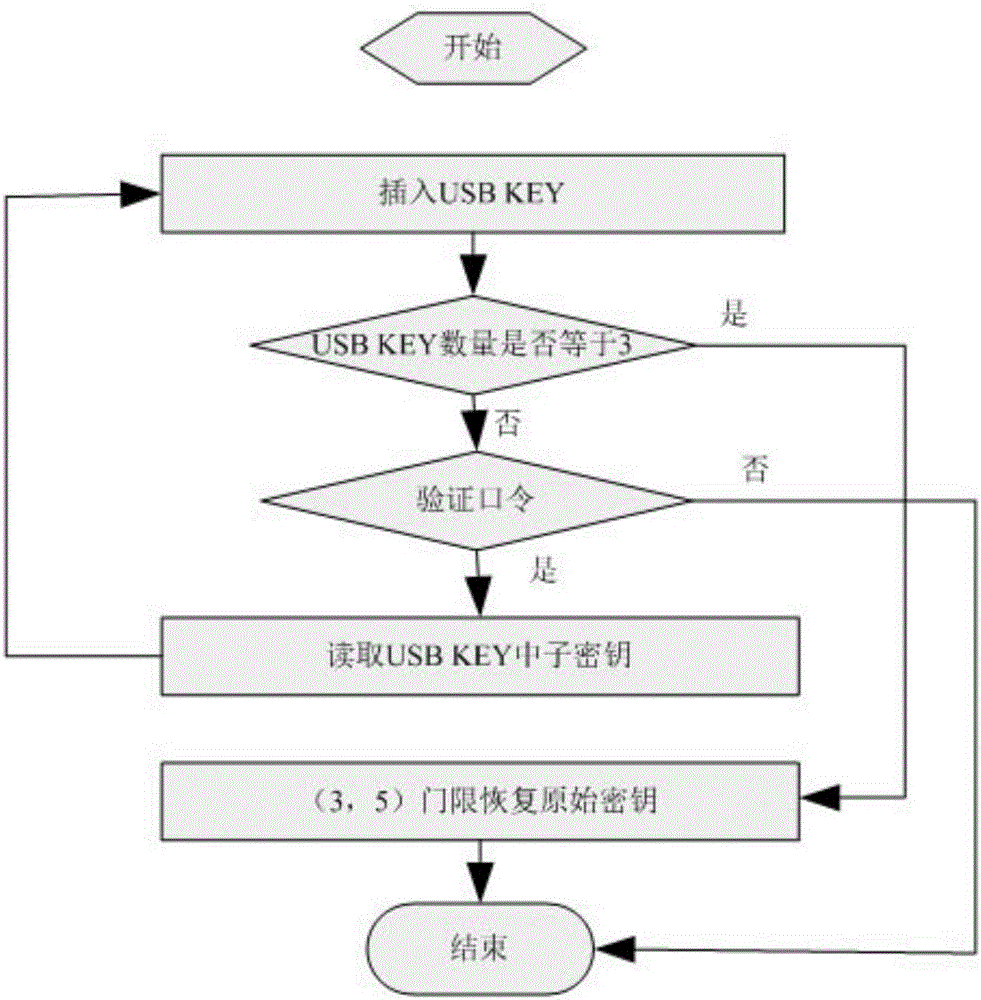
[0020] Decryption process:
[0021] Choose any three USB KEY managers, enter their own USB KEY including passwords, and take out three sub-keys.
[0022] Using the (3,5) threshold algorithm, the three-molecule key is restored to the original key.
[0023] Use the original key to decrypt the ciphertext data to obtain plaintext data.
[0024] The key is randomly generated in the above encryption process, and a random number generator can be used to generate a data string without any rules as the key.
[0025] Encrypt the plaintext: You can choose...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com