Method and device for code protection based on VEH
A protection device and code technology, applied in program/content distribution protection, electrical digital data processing, instruments, etc., can solve the problems of low safety factor, large resource occupation, weak anti-static analysis ability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to explain in detail the technical content, structural features, achieved goals and effects of the technical solution, the following will be described in detail in conjunction with specific embodiments and accompanying drawings.
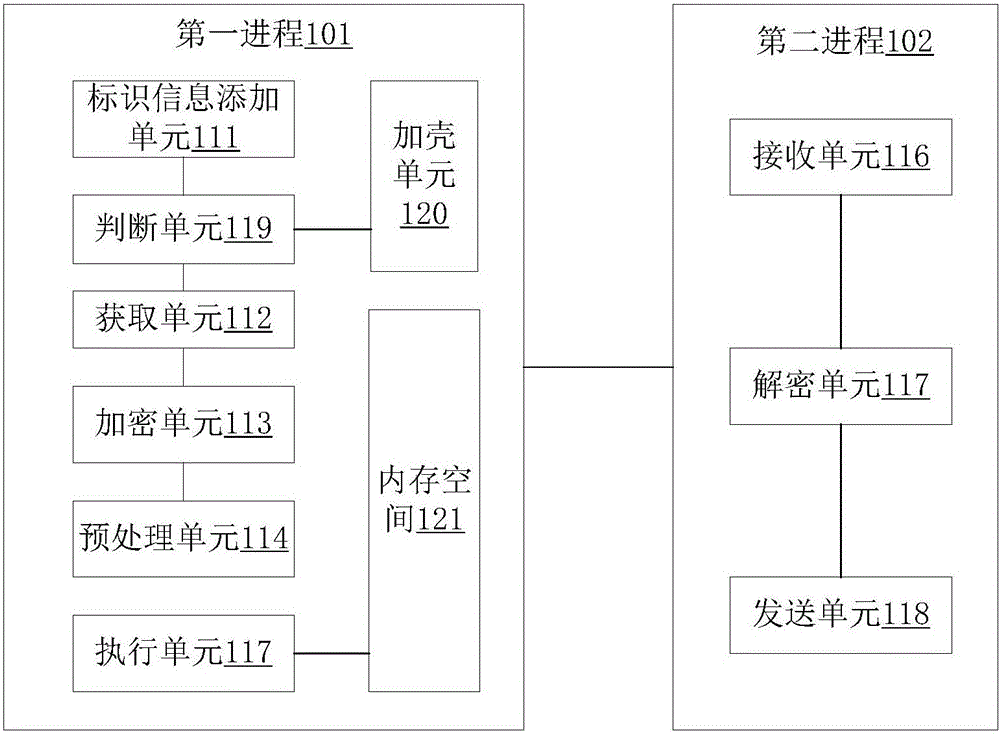
[0045] see figure 1 , is a flowchart of a VEH-based code protection method related to an embodiment of the present invention. The method can be applied to protect key software code segments and effectively improve the anti-static analysis capability of software codes. The method includes the following steps:
[0046] First enter step S101 to add identification information to the code segment to be protected in the first process. Specifically, two macros, ProtectBegin and ProtectEnd, may be added at the beginning and end of the code segment to be protected, representing the start of protection and the end of protection respectively. The identification information is an identification identifying the code to be protected, and in other...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com