Dalvik instruction abstraction-based Android malicious code detection method
A malicious code detection and abstraction technology, applied in the field of malicious code detection, can solve the problems of poor speed and low effectiveness, and achieve high detection rate, improved efficiency, and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described below in conjunction with the accompanying drawings.
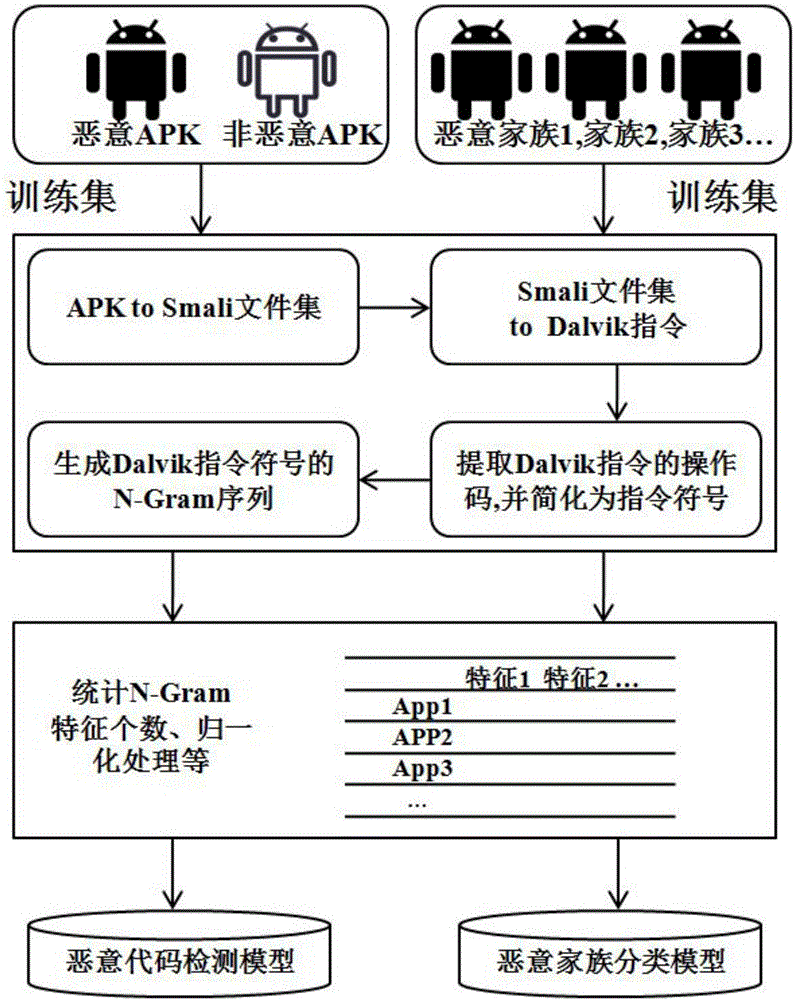
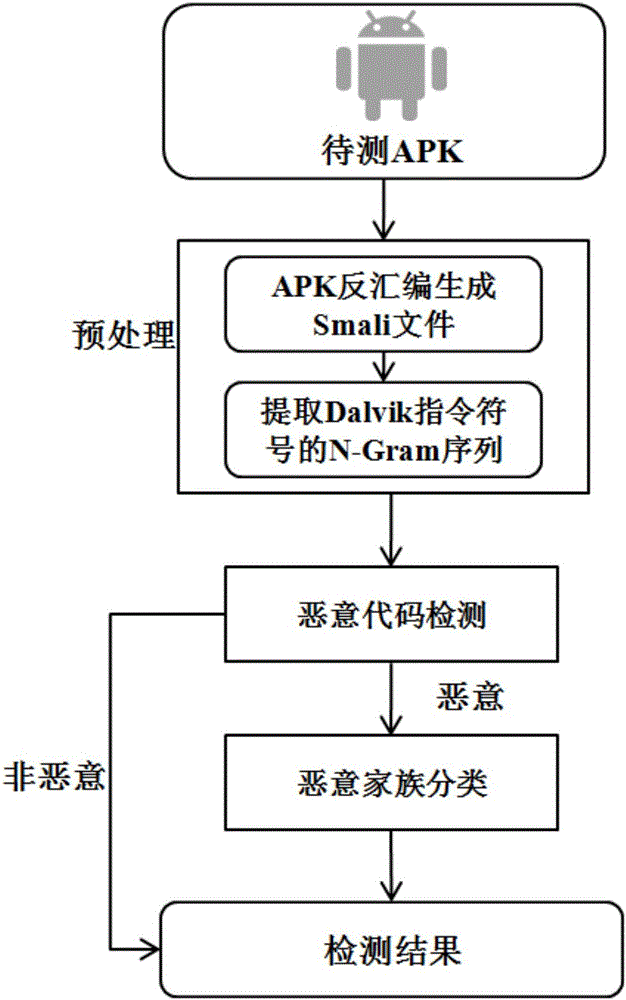
[0023] refer to figure 1 and figure 2 , a kind of Android malicious code detection method based on Dalvik instruction abstraction described detection method comprises the steps:
[0024] 1) Malicious code detection and classification model training, the process is as follows:
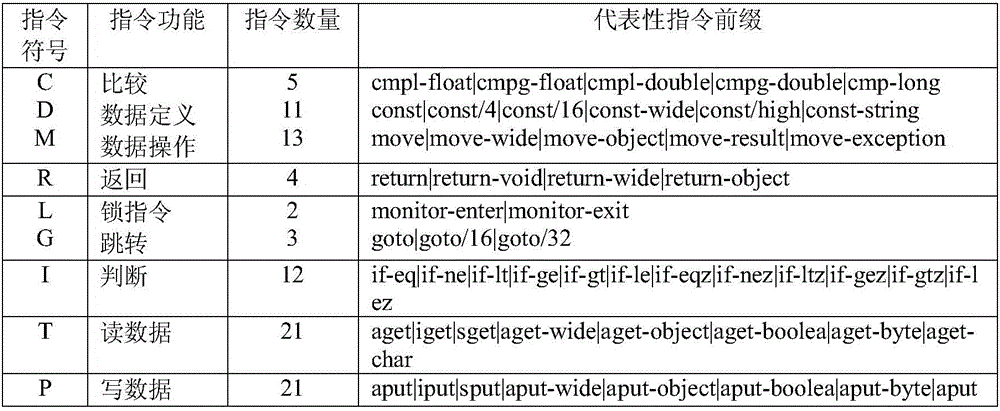
[0025] 1.1) Determine the training set for training the malicious code detection model. The training set is divided into two subsets, one is a collection of malicious APK samples, and the other is a collection of non-malicious sample APKs; the APK file format usually includes a classes.dex file, and the Dex file Encapsulate the Dalvik bytecode that can be executed by the Dalvik virtual machine, use the tool Apktool to disassemble the APK file, and you can get a file directory containing the smali source code. The smali directory structure corresponds to the src directory of the Java source co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com