Method and device for bidirectional forwarding detection authentication security switching
A two-way forwarding detection and security technology, applied in the field of communication, can solve problems such as traffic interruption and route deletion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
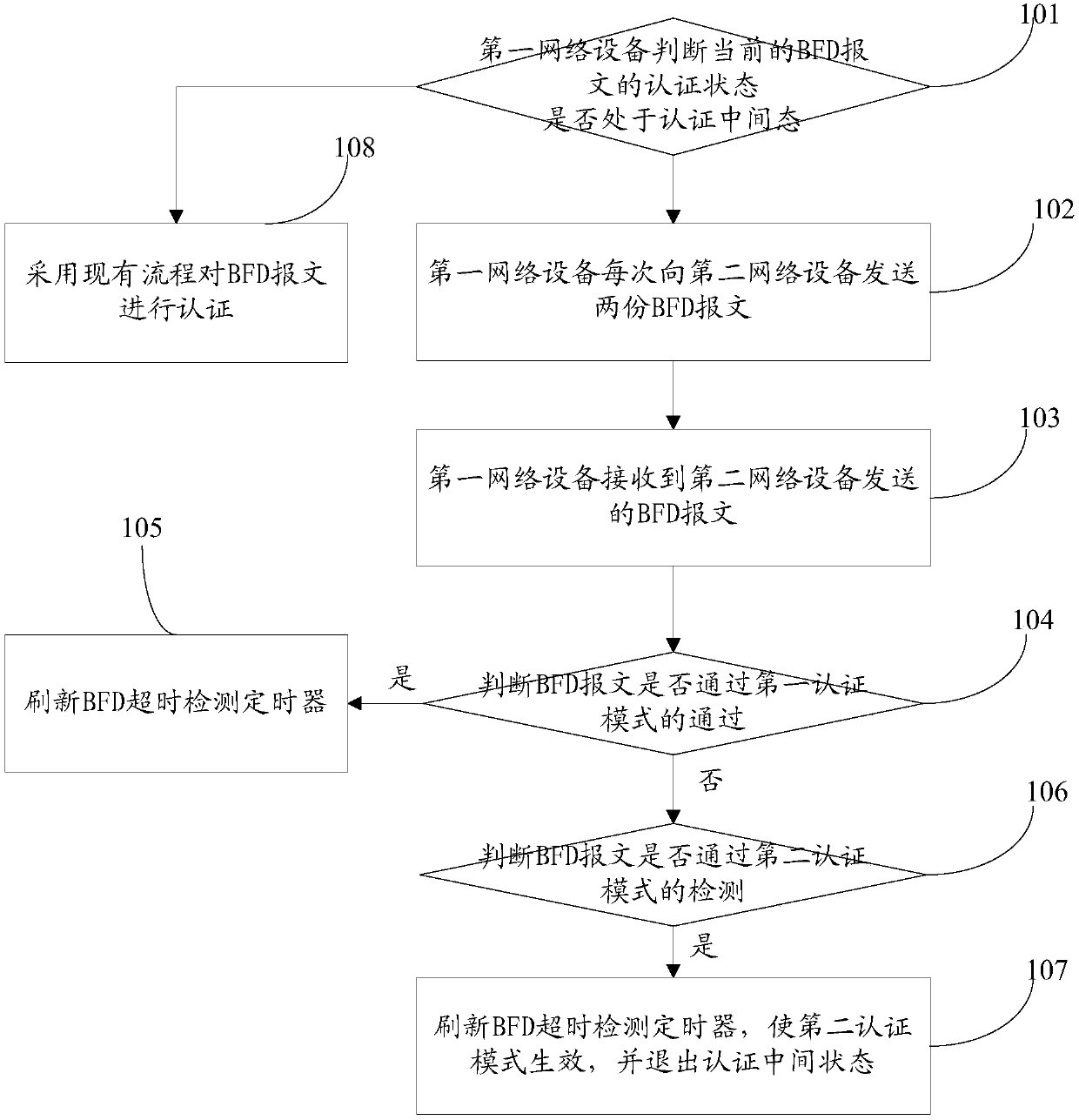
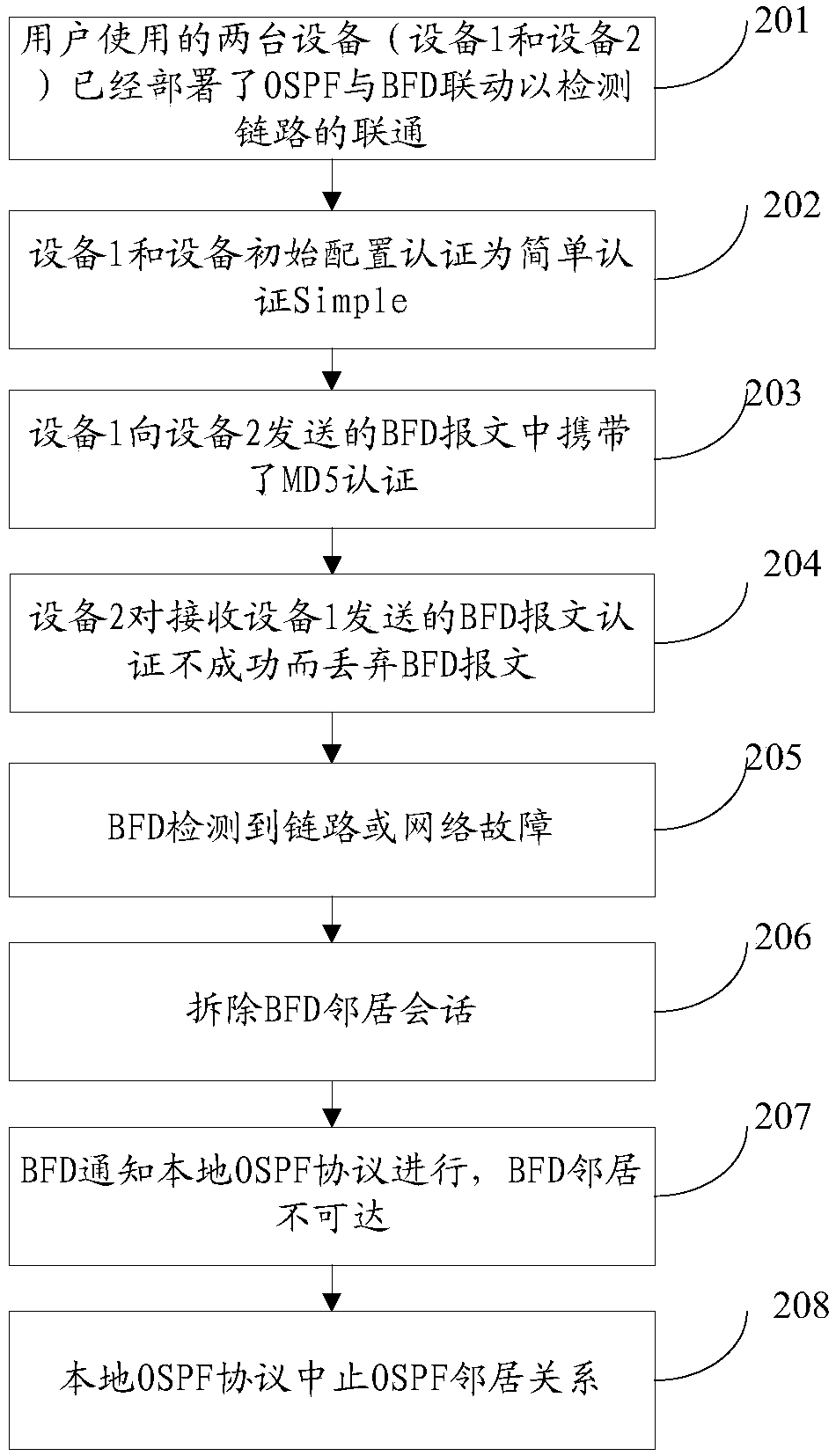
[0053] The basic idea of this application's two-way forwarding detection and authentication security switch is: after the first network device and the second network device establish a BFD session, they periodically send a two-way BFD message on the channel of the established session, and use the second network device to implement the second network device. In the detection of a network device, if the first network device does not receive the BFD message from the second network device within a certain period of time, it is considered that a certain part of the bidirectional channel has failed.
[0054]The first network device judges the authentication status of the current BFD message. If it is currently in the intermediate state of authentication, it sends two copies of the BFD message to the second network device each time. The first authentication mode is generated, and the second BFD packet is generated according to the second authentication mode after the modification of...
Embodiment 2
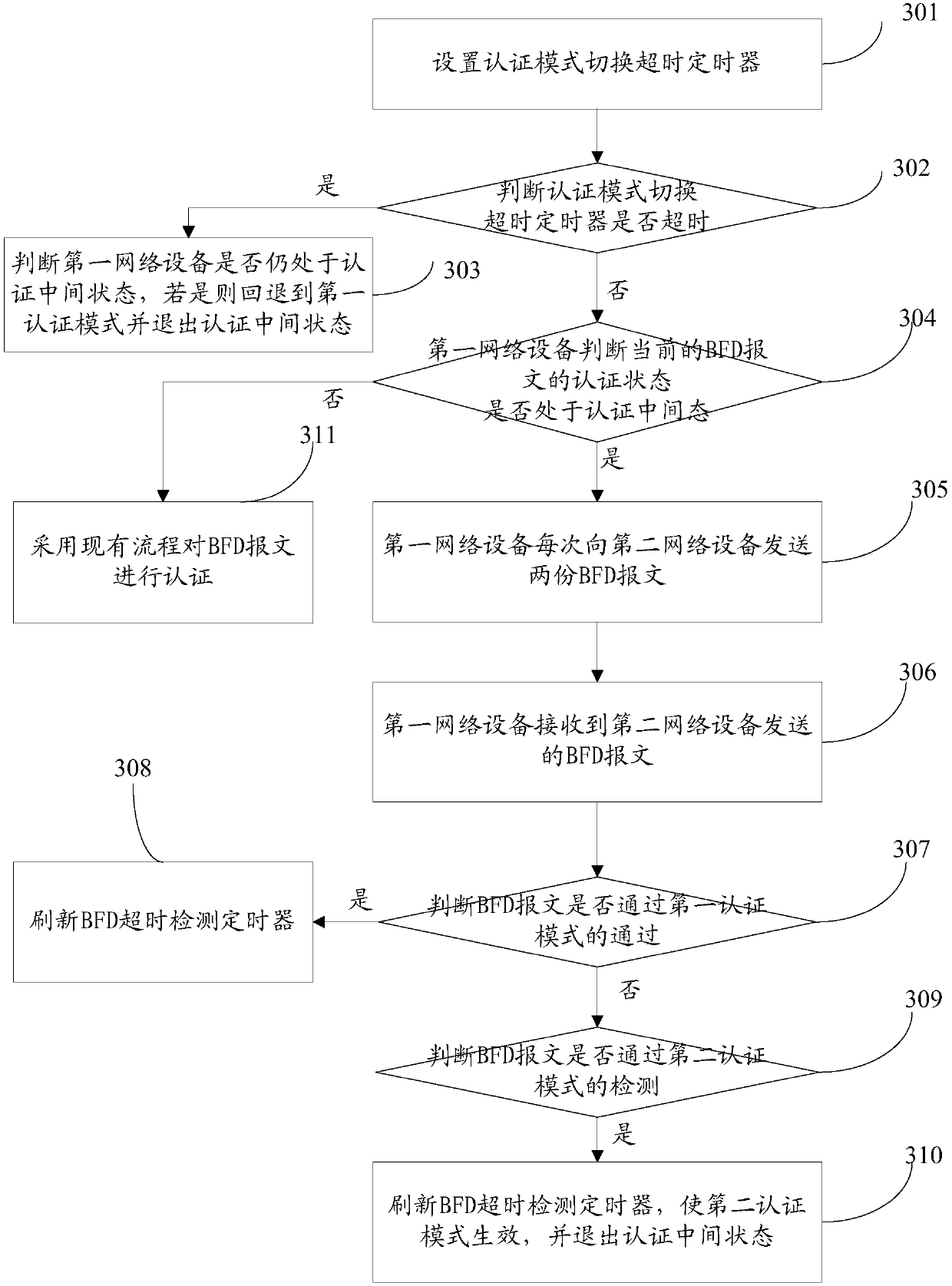
[0082] refer to image 3 , which shows a flow chart of a method for bidirectional forwarding detection and authentication security switchover described in Embodiment 2 of the present application, specifically including:
[0083] Step 301: Set an authentication mode switching timeout timer.
[0084] When the first network device enters the authentication intermediate state, start the authentication mode switching timeout timer.
[0085] Step 302: Judging whether the authentication mode switching timeout timer has expired, if it expires, execute step 303, if not, execute step 304.
[0086] Wherein, preferably, the authentication mode switching timeout timer timeout time can be set to 5 minutes, and can also be set in any appropriate way by those skilled in the art, such as the threshold can be set by manual experience, or set for the difference value of historical data The timeout period is not limited by this application.
[0087] Step 303: Determine whether the first networ...
Embodiment 3
[0142] refer to Figure 8 , which shows a structural diagram of a device for bidirectional forwarding detection and authentication security switching in Embodiment 3 of the present application. When the device is the first network device, it may specifically include:
[0143]The authentication status judging module 801 is used to judge the authentication status of the current BFD message. If the authentication status judging module judges that the current BFD message is in the authentication intermediate state, the sending module 802 is executed; otherwise, the authentication module 807 is executed.
[0144] Sending module 802: Send two BFD packets to the second network device each time.
[0145] Wherein, the first BFD message is generated according to the first authentication mode before the modification of the authentication mode, and the second BFD message is generated according to the second authentication mode after the modification of the authentication mode.
[0146] T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com