Service-orientated interface authentication method based on authorization certificate of operating system
A technology of authorization certificate and operating system, which is applied in the field of interface authentication, can solve the problems of OAuth2.0 interface authentication framework that cannot authorize certificate docking and cannot work normally, and achieve the effect of protecting commercial value, reducing research and development costs, and improving stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to better explain the present invention and facilitate understanding, the present invention will be further described below through specific embodiments in conjunction with the accompanying drawings.
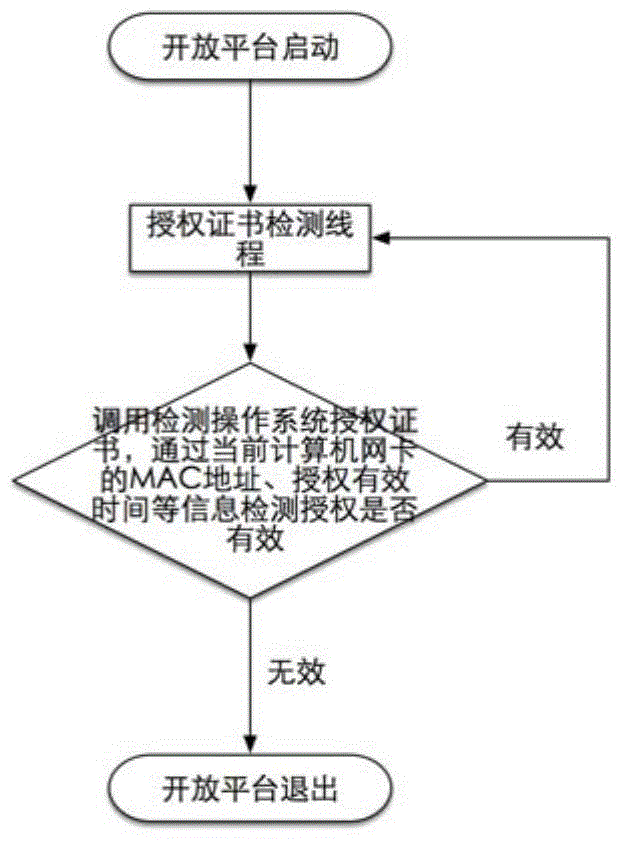
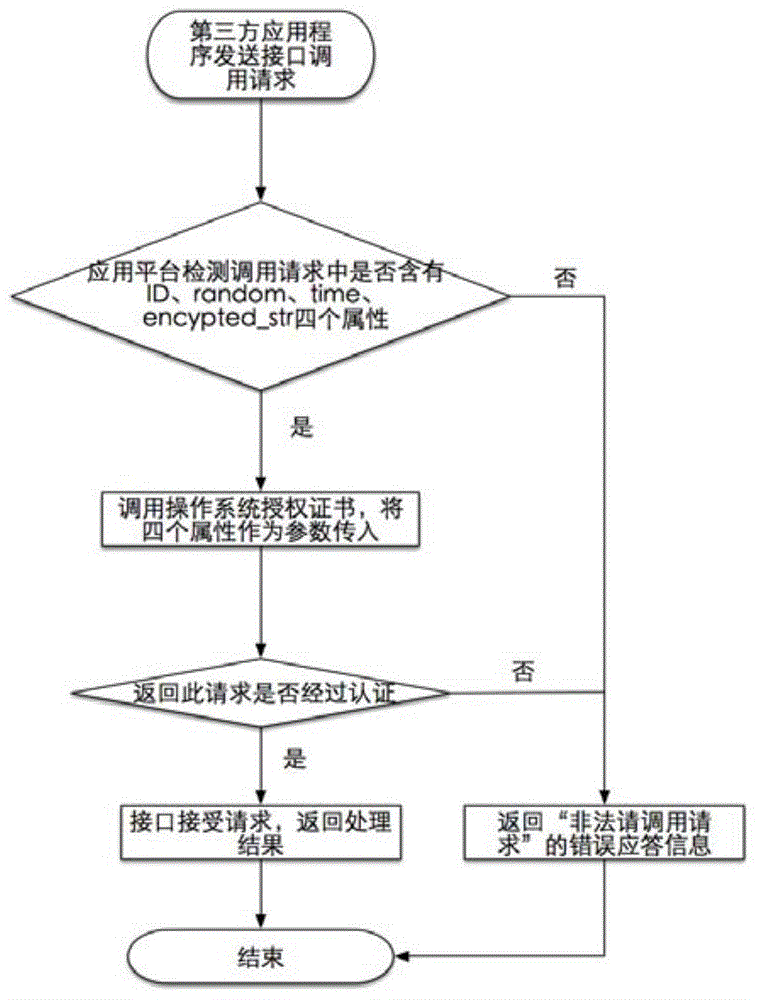
[0037] see Figure 1 to Figure 4 , a service-oriented interface authentication method based on an operating system authorization certificate according to an embodiment of the present invention, which mainly includes the following steps:
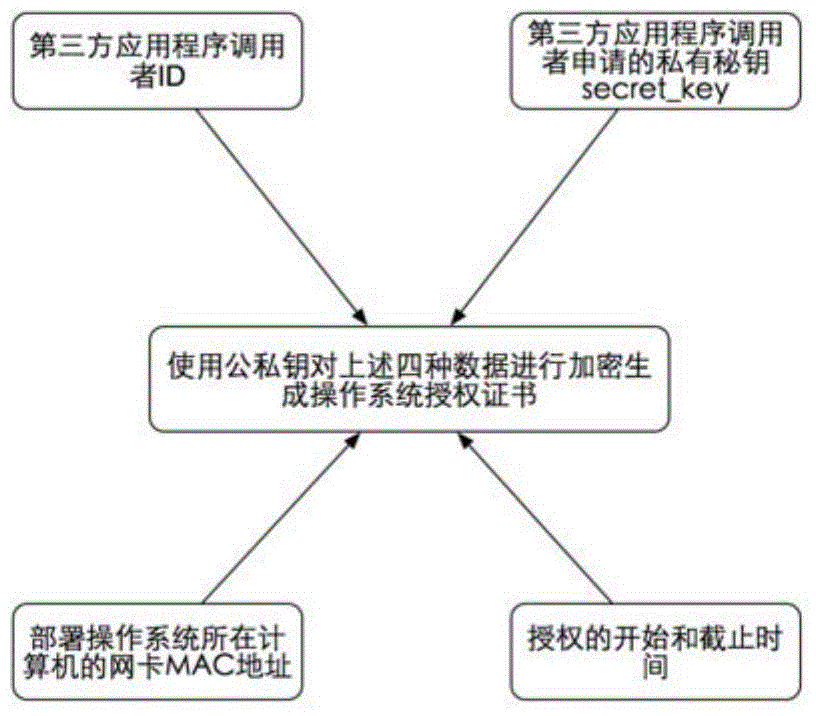
[0038] The first step is to assign a unique ID to the third-party application caller to identify the user, and assign a unique secret_key to represent the secret key of the user with the ID. At the same time, the ID and secret_key, as well as the MAC address of the network card of the computer where the third-party application caller wants to deploy the operating system, and the effective start and expiration time of the authorization are used as input data, and the authorization certificate is generated using the authorization ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com