Access control method based on identity and encryption in naming data network
A named data network, access control technology, applied in the usage of multiple keys/algorithms, electrical components, transmission systems, etc., can solve the problem of inability to obtain decryption keys, inability to decrypt, etc., to reduce network communication burden and enhance security. the effect of reducing encryption cost and system delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
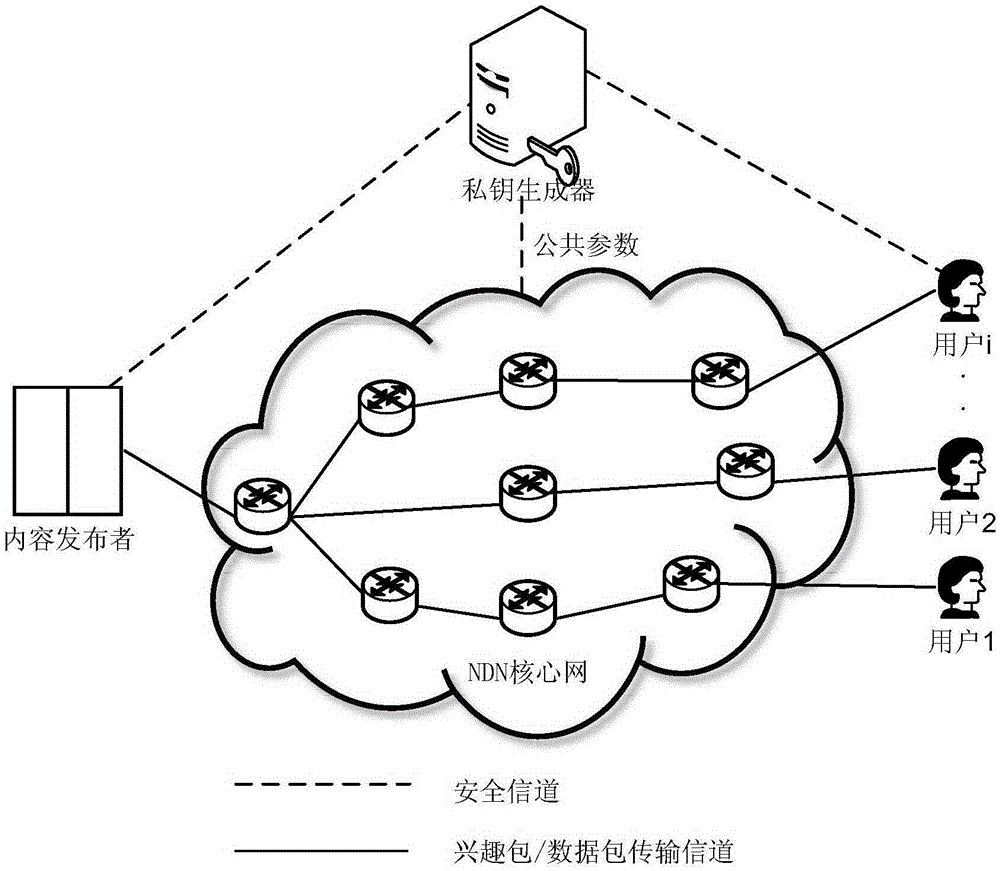
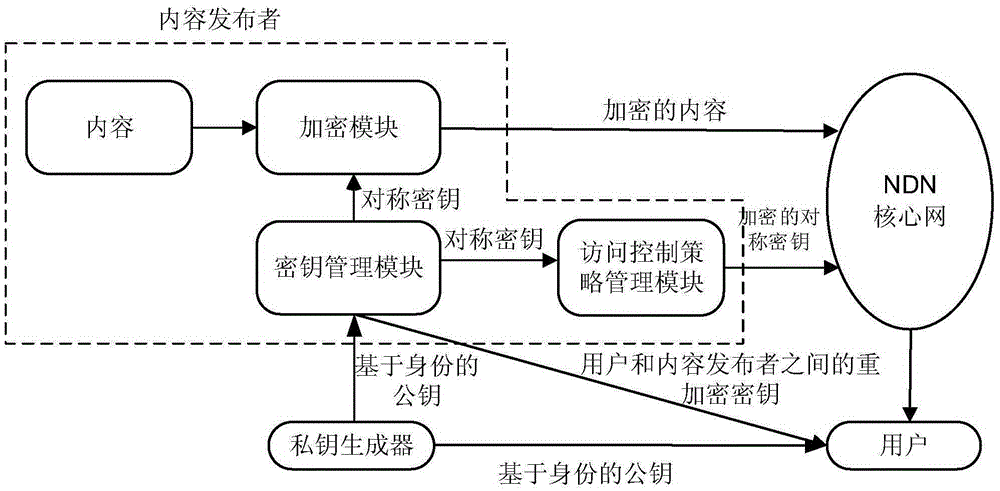
[0029] figure 1 is a schematic diagram of named data network access control, figure 2It is a flowchart of an access control method based on identity and encryption. In this embodiment, there are five entities: content publisher A, user B, user C, private key generator PKG, and NDN router. Content publisher A of a video website publishes popular movies to the Internet and forwards them to users through the router of the NDN core network. User B is a movie lover and becomes a member of the video website through registration, and user C is a non-member. Due to copyright issues, the newly released movies can only be accessed by registered members of the video site, and non-member users cannot watch the movies normally even if they download them locally. In order to realize such access control, the access control method based on identity and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com