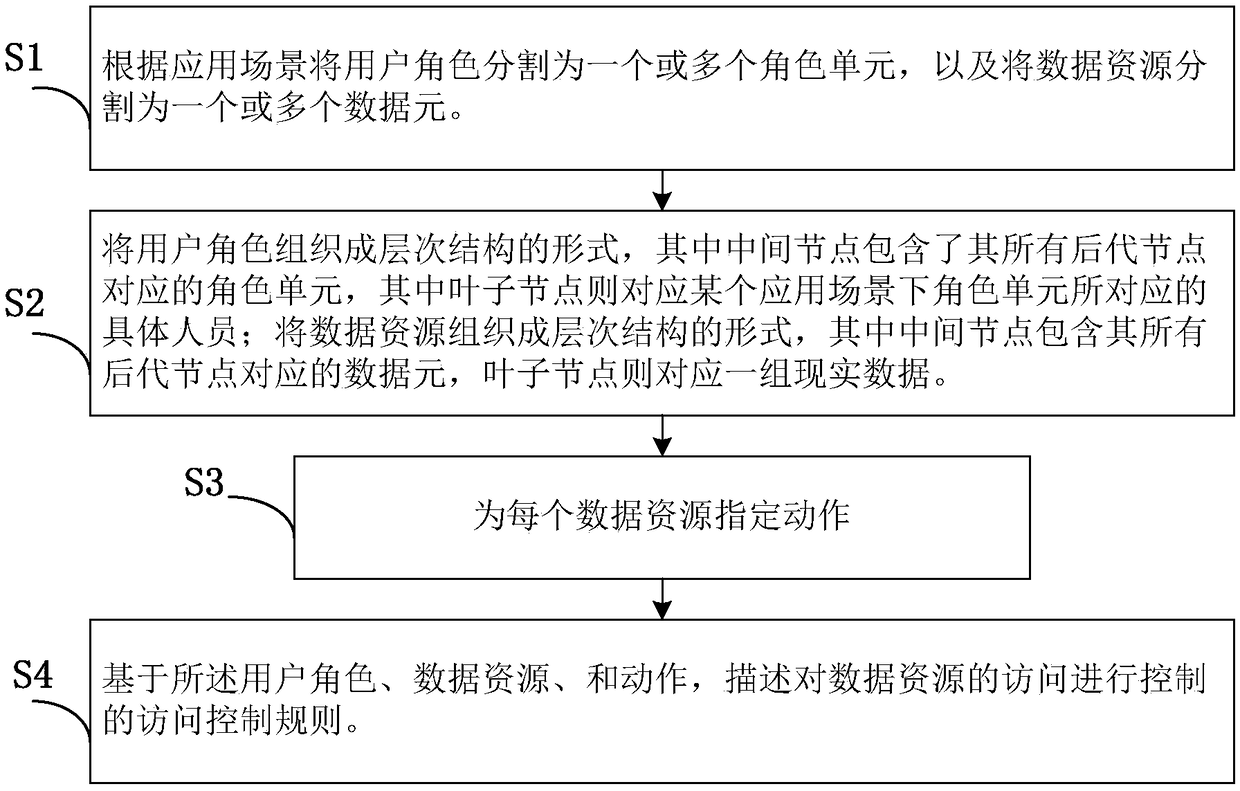
A method for describing access control rules for data analysis
An access control and data analysis technology, applied in digital data authentication, digital data protection, electronic digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0051] r1:Analyst exclude Marketing Analyst,[access Name]=>forbid
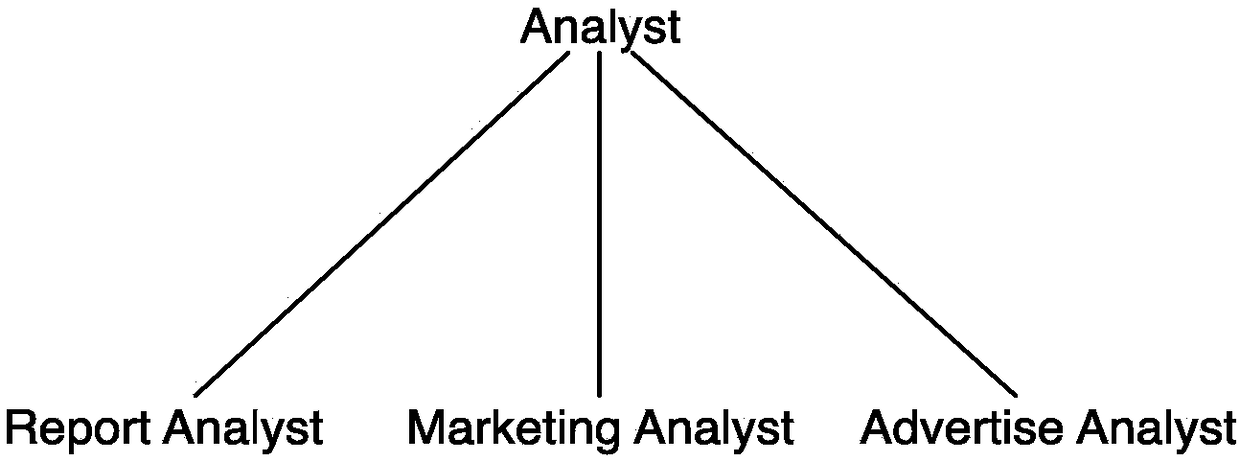
[0052] Access control rule r1 prohibits data analysts other than Marketing Analyst from accessing customer names, that is, only Marketing Analyst can access customer names.
example 2
[0054] r2:Analyst,[output Address,output Sale_Price]=>[{},{avg,sum,min,max}]
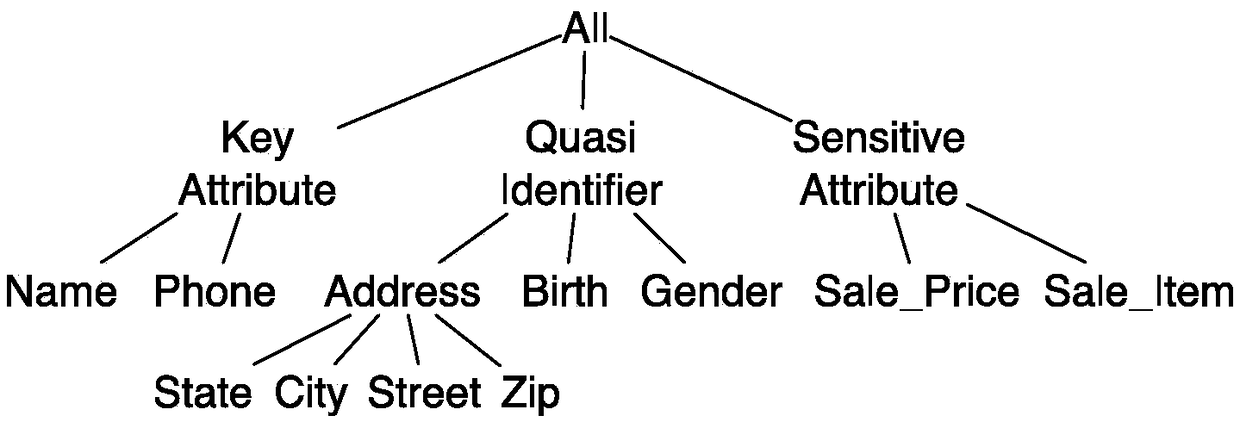
[0055] Access control rule r2 requires that when data analysts output Address and Sale_Price at the same time, they must perform avg, sum, min or max operations on Sale_Price, but there is no desensitization requirement on Address. Since Address further includes State, City, Street, and Zip in the data resource hierarchy, when one of them is output together with Sale_Price, the access control rule is also applicable. In addition, both Address and Sale_Price in the access control rule correspond to the output action. Therefore, when the Address or Sale_Price is not directly output but used for condition judgment, the access control rule will no longer apply.
example 3
[0057] r3: Analyst, [access State, access City, access Street] => forbid
[0058] Access control rule r3 prohibits data analysts from accessing State, City and Street at the same time. However, data analysts can independently access one or two of the three data resources, such as accessing State alone, or accessing State and City at the same time.
[0059] After the above description of the access control rule is completed, after the access control request for data analysis is received, the access control request is controlled based on the access control rule. The access control method specifically includes the following steps:
[0060] For each access control rule, first check whether the data access request triggers the access control rule; if triggered, then check whether the data access request meets the restrictions of the access control rule; if so, continue to traverse subsequent access control rules until the data The data resource request is authorized only when the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com