Data security exchange method based on black list and white list
A data security, black and white list technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of single judgment function, inflexible and inconvenient power system isolation technology, etc., to ensure security, enhance flexibility, and strong flexibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
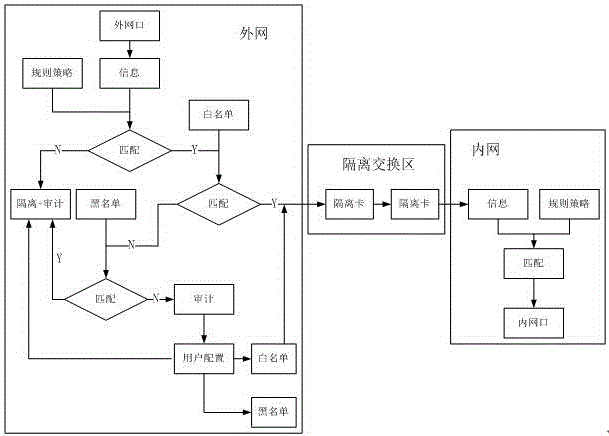
[0029] In the present invention, the external network is used as the network one, and the internal network is used as the network two. Assuming that the information is from the external network to the internal network, the "2+1" module structure design is adopted, that is, the external network host module, the internal network host module and the isolation switch module are included. The internal and external network host modules have independent computing units and storage units, which are respectively connected to the internal and external networks. The isolation switching module is implemented by a dedicated dual-channel isolation switching card, and the secure data exchange between the internal and external network host modules is completed through the embedded security chip. There is no network connection between the internal and external network host modules, so there is no data forwarding based on network protocols. The isolated switching module is the only channel for ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com