Safe transmission method in MIMO Y eavesdropping network based on real interference alignment
A technology for secure transmission and interference alignment, applied in the field of secure transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0082] The present invention will be further described below in conjunction with the drawings.
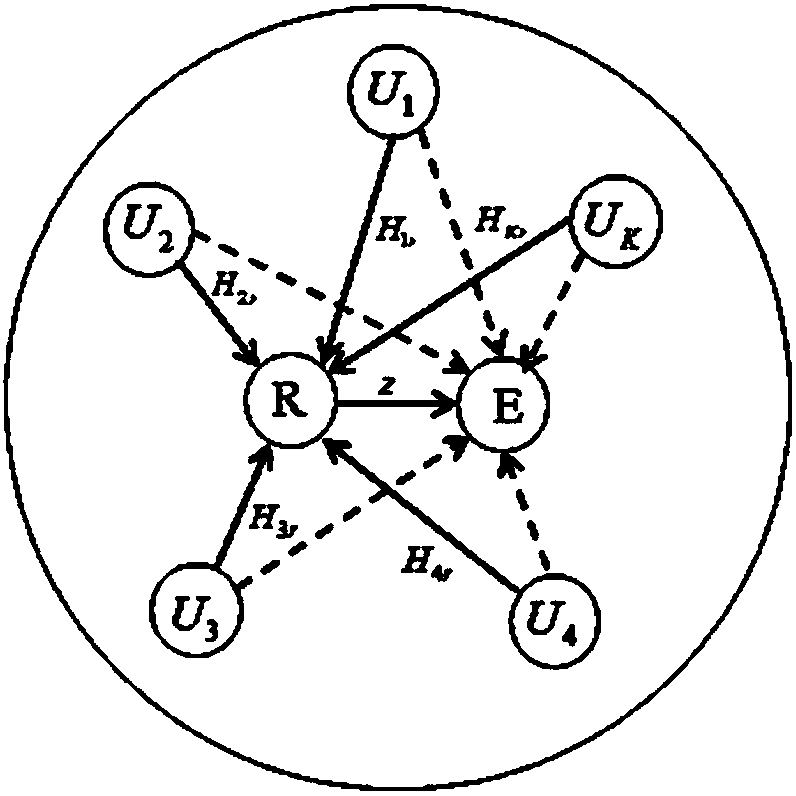
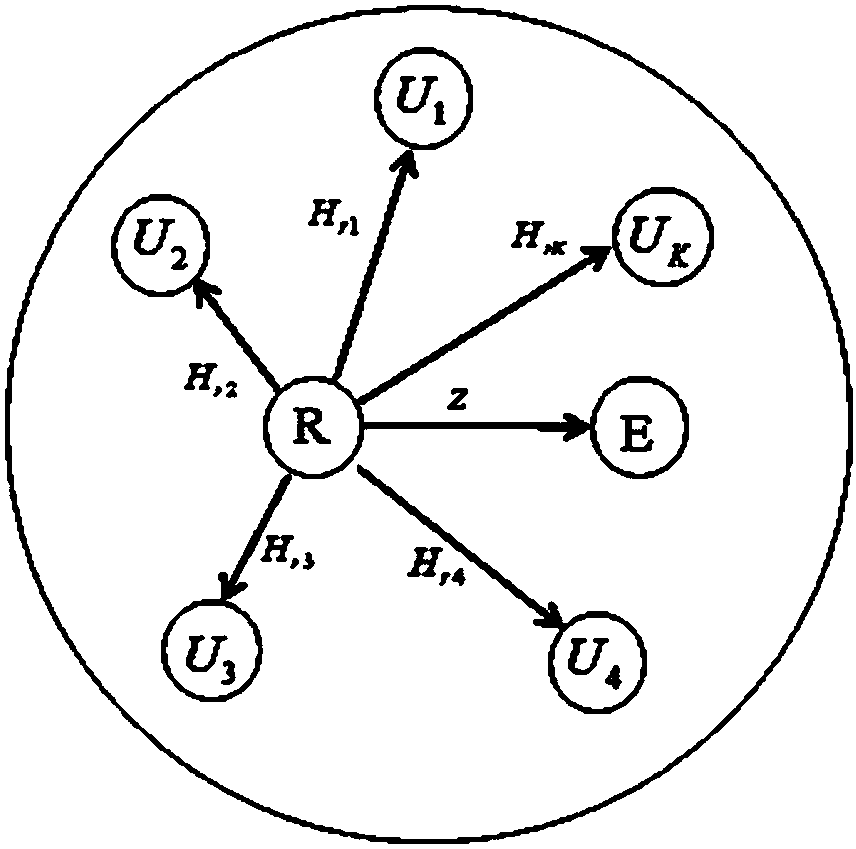
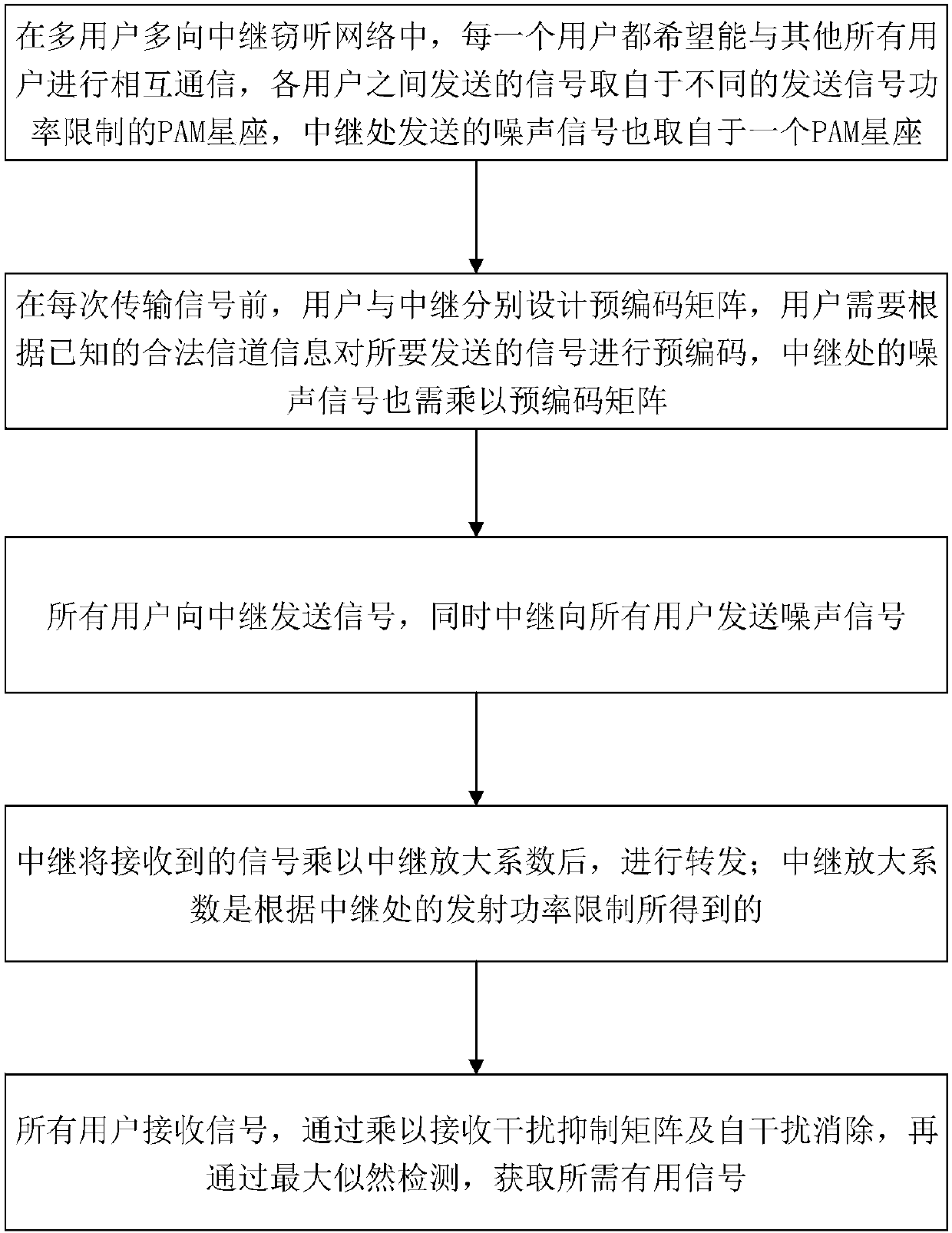
[0083] The present invention proposes a physical layer security scheme using real interference alignment technology and cooperative scrambling. The scheme adopts an amplifying and forwarding protocol, based on a multi-user-relay-multi-user physical channel, precoding is performed at the user, and the relay is Artificial noise is sent everywhere, which interferes with external eavesdropping nodes without disturbing users, and obtains all secure communication channels under the condition of power limitation of each user node.
[0084] The present invention considers a MIMO Y eavesdropping model, there are a total of K users, each user has M antennas, and there are N antennas at the relay. Multiple users communicate with each other through an AF relay, and the system includes an eavesdropping Node, the power of each user's signal is P i , The sum of the transmission power of all users is P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com